Analyze your supply chain security
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerThe Packages section within Inventory is designed to give you visibility into the dependencies used across all active repositories in a group, helping you monitor the status of these dependencies, regarding updates, security advisories and reachable vulnerabilities.
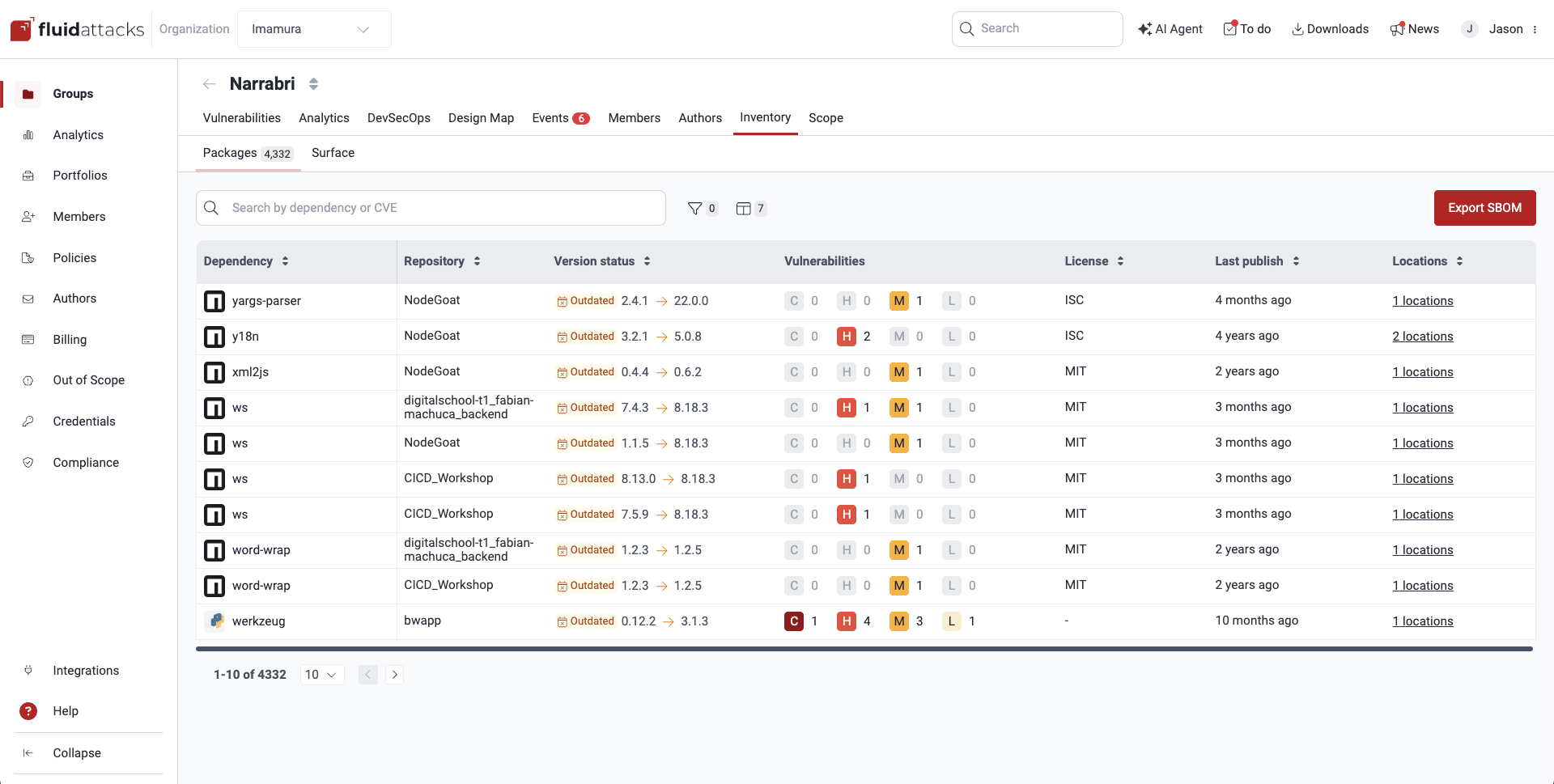
Views of Packages
Packages
The Packages section shows you all the third-party dependencies used across the code repositories of your group. This is the information provided by the table:
- Dependency: Name of the open-source component or dependency
- Repository: The nickname your organization has given to the repository where the dependency is used
- Version status: Indicates the version of the dependency currently in use by your project plus security-relevant status regarding the dependency version, where the following values are possible:
- Reachable: A vulnerable element of the dependency is effectively called by your application, thus generating the risk of the vulnerability being exploited in the context of your application.
- Vulnerable: Advisories have been issued for that dependency version.
- Outdated: A newer version of the dependency is available, in which case the column shows the suggested upgrade.
- Updated: The dependency is in its latest version.
- Malware: Malicious software was detected in that dependency version.
- Vulnerabilities: The number of detected vulnerabilities of each CVSS qualitative severity rating
- License: The license of the software package, like ISC or MIT, which defines how your project can legally use its code
- Last publish: Time since the latest version was released
- Locations: The number of files within the repo that contain, or correspond to, the dependency

Click on the link to enter the Package Imports section.
You can click on the columns button ( ) to open a window where you can reorder, show or hide columns.
) to open a window where you can reorder, show or hide columns.
You can filter the dependencies by variables that are visible in the table as well as the following: the Docker images containing them, the package manager used, and the stage in which your project depends on the third-party dependencies.

Filter dependencies

Apply filter by 'Version status'
Package Imports
In the Packages section, when you click on the links in the Locations column, you are taken to a table showing information of your files related to the selected third-party dependency.
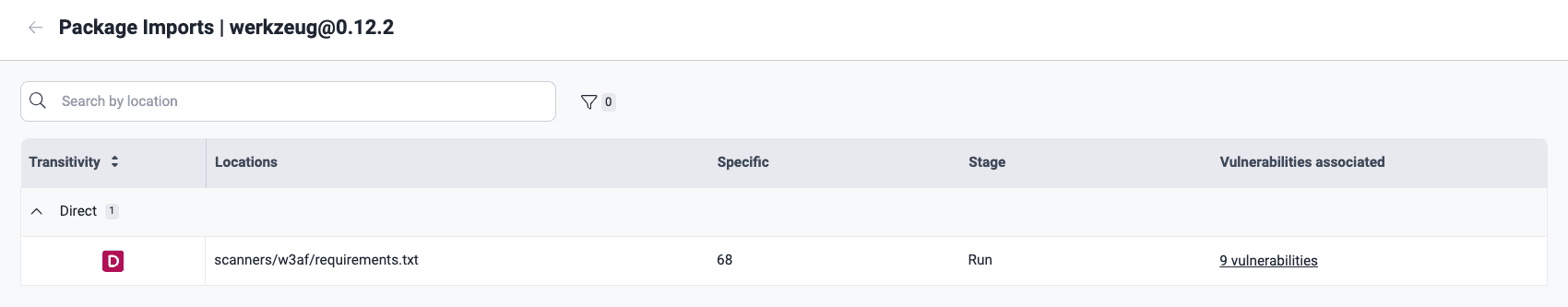 Use of the direct dependency in the production stage
Use of the direct dependency in the production stage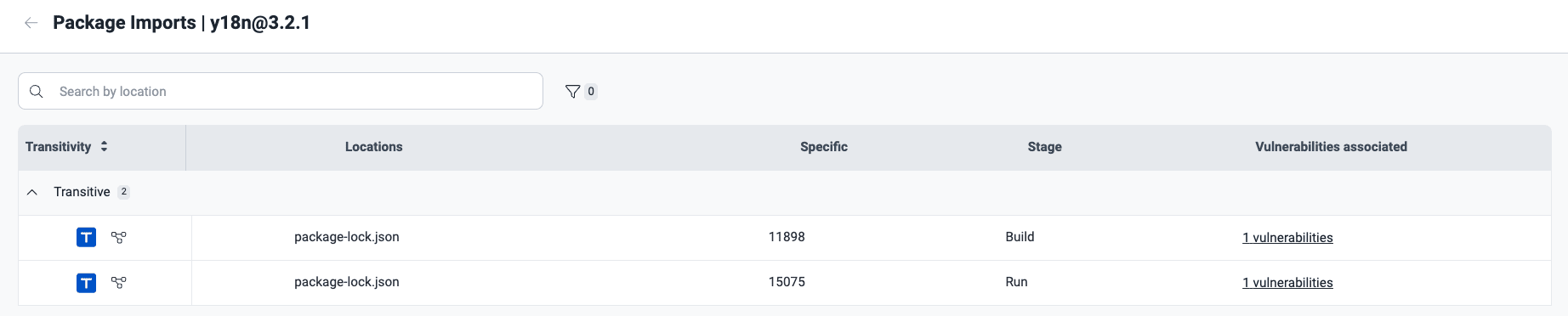 Use of the transitive dependency in the development and production stages
Use of the transitive dependency in the development and production stagesThe table columns provide the following information:
- Transitivity: Whether the listed vulnerable files in your software are directly or indirectly related to the third-party component in question:
- D: Short for 'Direct'; the file in your project explicitly imports and uses the third-party dependency
- T: Short for 'Transitive'; the third-party dependency is required by your direct dependencies, but not directly imported by the file in your project
- U: Short for 'Undeterminable'; for this file, it is impossible to determine whether the dependency is direct or transitive
- Locations: The file related to the third-party dependency
- Specific: The exact line of code that shows the relation with the third-party dependency stated in Transitivity
- Stage: The stage(s) in which your project depends on the third-party dependency:
- Build: Your file depends on the third-party component only in the software development stage
- Run: Your file depends on the third-party component in the live production environment
- Vulnerabilities associated: The number of vulnerabilities related to the third-party dependency
By clicking on the code branch icon next to the T in each of your transitive dependencies, you will find the dependency path that goes from the direct to the affected transitive dependency in question ("grunt-if" and "y18n," respectively, in the following example image):
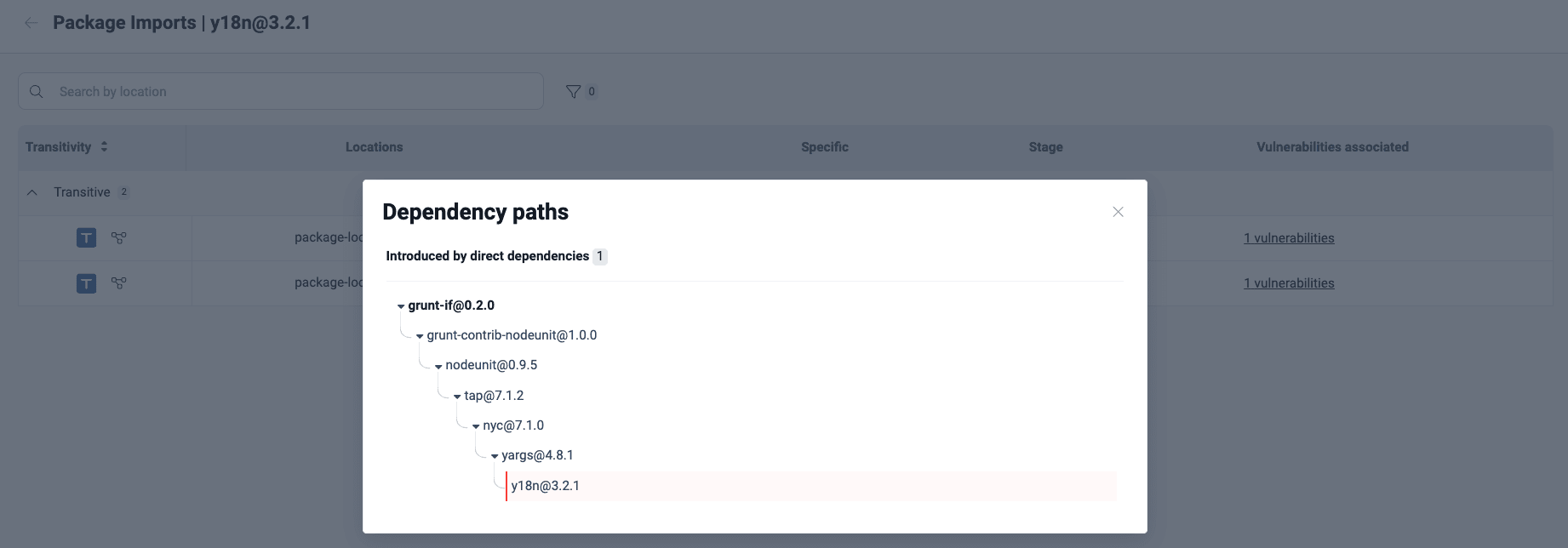 Example of a dependency path
Example of a dependency pathBy clicking on the vulnerabilities associated link, you get a pop-up window with the vulnerability details:
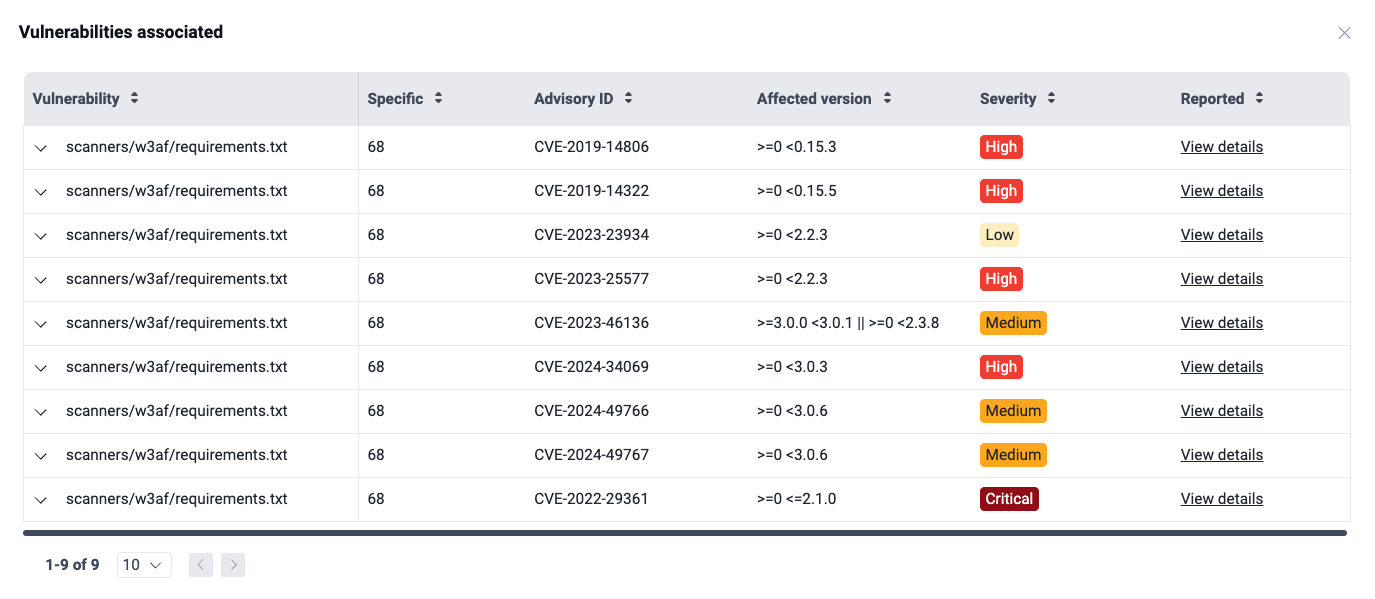
- Vulnerability: The file path where the vulnerability is found
- Specific: The exact line of code that shows the relation with the third-party dependency stated before in Transitivity
- Advisory ID: The identifier for the vulnerability advisory or Common Vulnerabilities and Exposures (CVE) entry
- Affected version: The dependency versions which are affected by the vulnerability
- Severity: The qualitative severity rating according to the Common Vulnerability Scoring System (CVSS)
- Reported: The link to the reported vulnerability on the platform
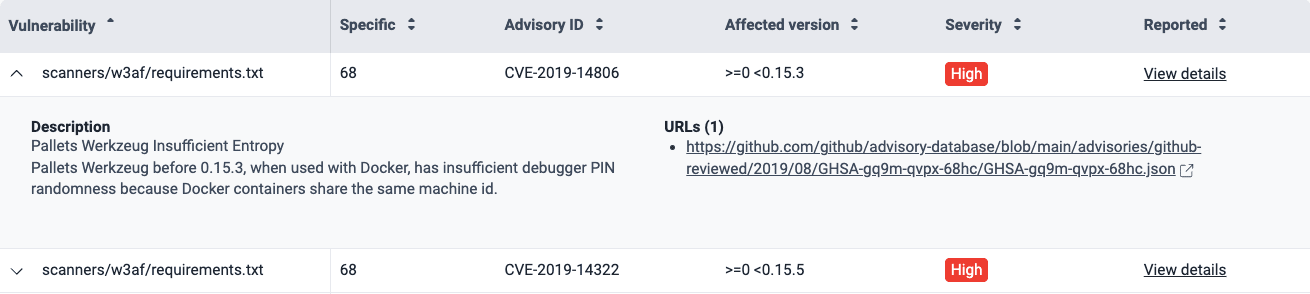
If you click on the downward-facing arrow, you can see a description taken from the advisory source and reference URLs.
Supported package managers
Currently, supply chain analysis is supported for the following package managers:
- Alpine Package Keeper (apk)
- APK (Android Package)
- Bundler (Ruby)
- Cargo (Rust)
- CocoaPods (Swift)
- Composer (PHP)
- Dart Pub (Dart)
- dpkg (Debian)
- Gradle (Java)
- Hex (Elixir)
- Maven (Java)
- NPM (JavaScript)
- NuGet (.NET)
- Pacman (Arch Linux and derivatives)
- PECL (PHP)
- Pip (Python)
- Pipenv (Python)
- PNPM (JavaScript)
- Poetry (Python)
- RPM (Redhat)
- Swift Package Manager (Swift)
- YARN (JavaScript)
Supported Docker images
Currently, supply chain analysis is supported for the following Docker images:
- Alpine Linux
- Arch Linux
- Distros based on Debian (Ubuntu, Debian)
- Distros based on Red Hat or Fedora

Excited to start using the platform? Explore Meet the platform to learn where to start and where everything is.
Export SBOM
The inventory of open-source software in your project is available on the platform in two different formats: CycloneDX and SPDX. Each of these formats follow a standard to show dependencies, vulnerabilities and license information in an organized way.
You can easily export a software bill of materials (SBOM) for your dependencies following these steps:
-
Within your group, navigate to Inventory > Packages.
- Click on the Export SBOM button.

- Select whether you want an SBOM for packages in your Git repository or Docker images.
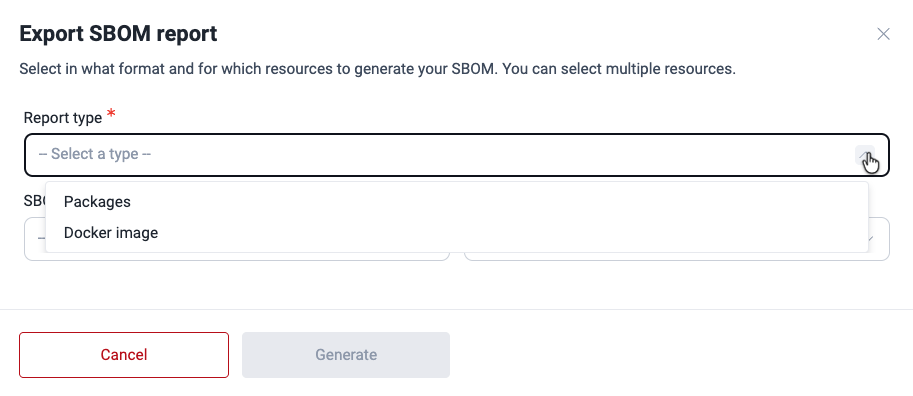
- Select in which format you want to download the inventory of software dependencies: CycloneDX or SPDX.
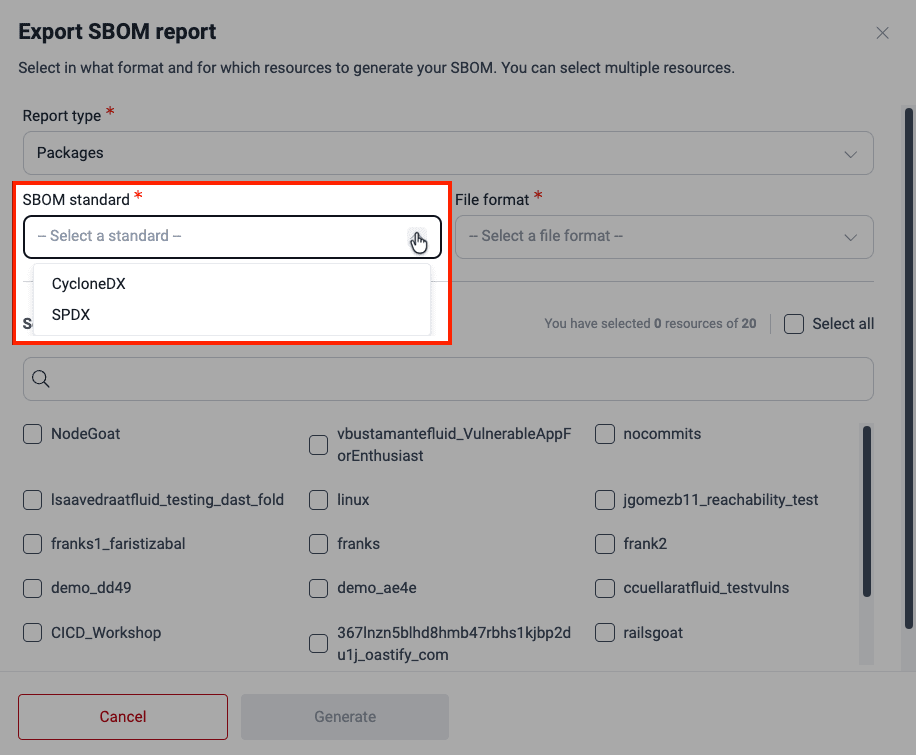
- Select the file type for your SBOM: JSON or XML.

- Select the resources (repos or Docker images) related to the project(s) of which you want to generate the SBOM. The window only shows active resources.
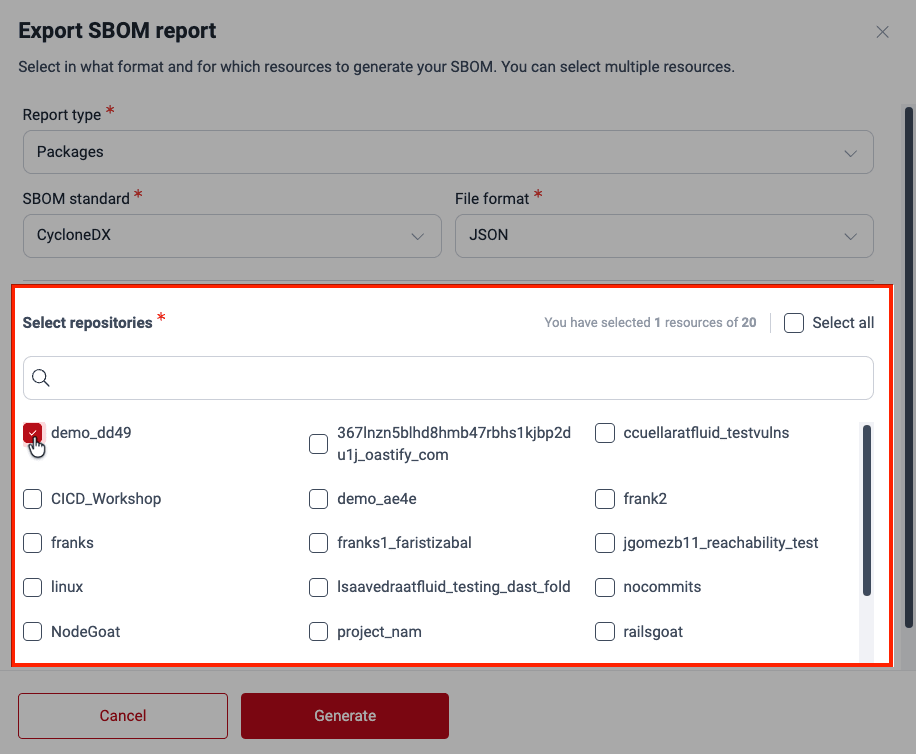
- Click on Generate.
- You then receive an email saying your SBOM is ready. Just go to the platform and click on Downloads to access the download option. If you chose more than one root, you receive a separate email for each root.

 Note: The SBOM may take up to 5 minutes to be ready for download. Keep in mind that the information provided may vary depending on the standard. The file may include the package name, version, location, license and dependency tree, which shows the primary and transitive dependencies.
Note: The SBOM may take up to 5 minutes to be ready for download. Keep in mind that the information provided may vary depending on the standard. The file may include the package name, version, location, license and dependency tree, which shows the primary and transitive dependencies.Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.