View analytics common to orgs, groups and portfolios

 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
Exposure management over time
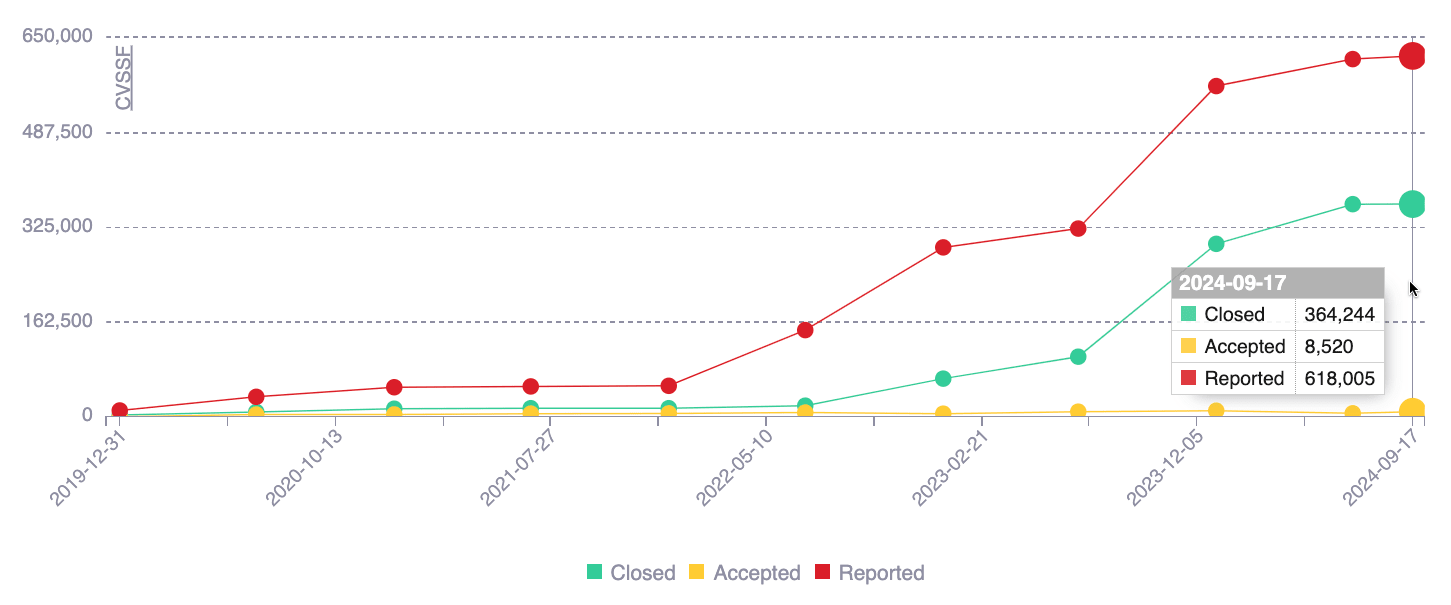
This chart presents the history of reported risk exposure (in CVSSF units), along with that of your actions addressing it. As this risk exposure is caused by the detected software vulnerabilities, the status of the latter, be it closed (remediated) or accepted, is by extension the status of risk exposure. With the help of this chart, you can identify gaps between known risk and managed risk.
- Hover over a data point to see the exact values
- Hover over a chart legend to highlight the corresponding line
- Click on a chart legend to hide the corresponding information from the visual comparison

 icon:
icon:- Exposure: Default view
- Vulns: See the number of vulnerabilities instead of risk exposure units
- 30: See data of the last 30 days
- 90: See data of the last 90 days
- All: See data since the creation of the organization
Sprint exposure increment
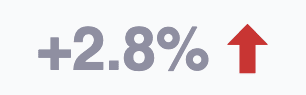
This figure is the percentage increase in risk exposure in the current sprint (i.e., the newly reported exposure value relative to the initial exposure value). The value is zero when no vulnerability has been reported in the period.
Sprint exposure decrement

This figure is the percentage decrease in risk exposure in the current sprint (i.e., the newly remediated exposure value relative to the initial exposure value). The value is zero when no vulnerability has been remediated in the period.
Sprint exposure change overall
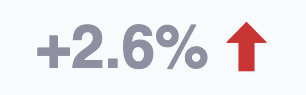
This figure is the resulting percentage change in risk exposure in the current sprint (i.e., the exposure decrement minus the exposure increment). A positive value means that more exposure was reported than remediated. A negative value means that more exposure was remediated than reported. A zero value means that as much exposure was remediated as reported.

Exposure management over time (%)

This chart shows how you have dealt with risk exposure (in CVSSF units) over time by correspondence with the statuses of vulnerabilities that cause it. Open vulnerabilities are those still present and unaccepted; whereas closed ones are those remediated. The information in this chart allows you to visualize the trends in your vulnerability management efforts, helping you identify areas where you are making progress and those that require more attention.
- Hover over a bar to see all the complete percentages information
- Hover over a chart legend to highlight the corresponding portion in the chart
- Click on a chart legend to hide the corresponding information from the visual comparison

 icon:
icon:- Exposure: Default view
- Vulns: See the percentages for number of vulnerabilities instead of risk exposure units
Exposure benchmark
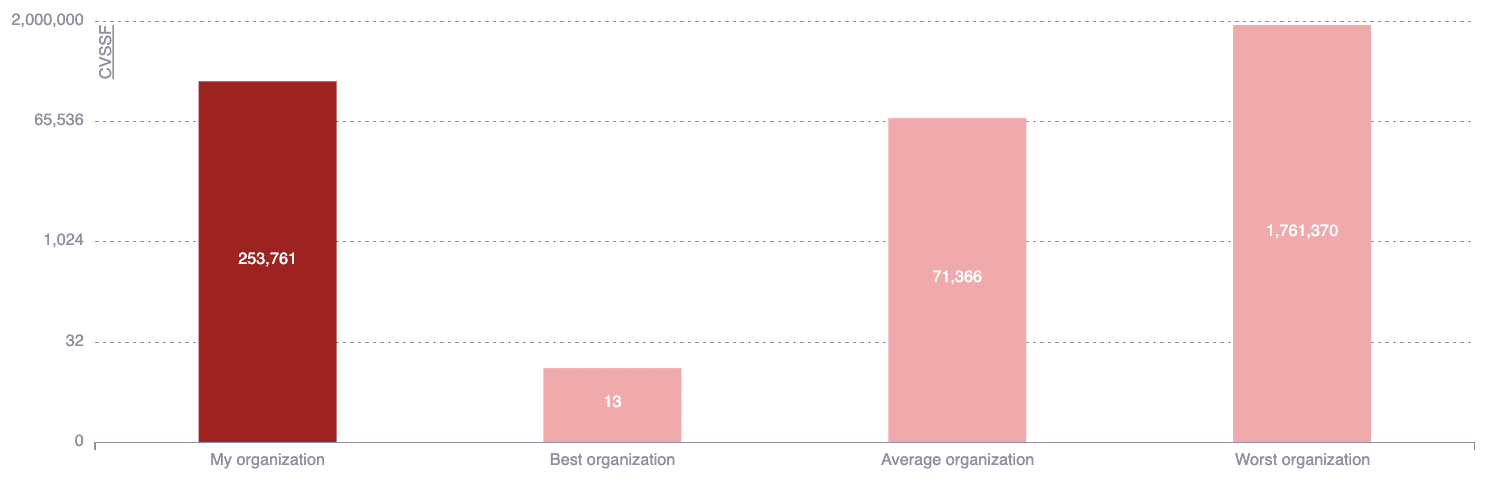
This chart shows your risk exposure level (CVSSF) that has not been remediated and allows you to compare it with that of other organizations, groups, or portfolios. Specifically, you can see how the best-performing and worse-performing at risk management are doing, as well as how many CVSSF units is the average. This benchmarking enables you to gauge your performance relative to your peers to ultimately set goals for reducing your risk exposure.
 Note: The benchmark for organizations excludes the ones with low activity (less than 100 reattacks on vulnerabilities within their groups) to ensure a fair comparison.
Note: The benchmark for organizations excludes the ones with low activity (less than 100 reattacks on vulnerabilities within their groups) to ensure a fair comparison.Exposure trends by vulnerability category
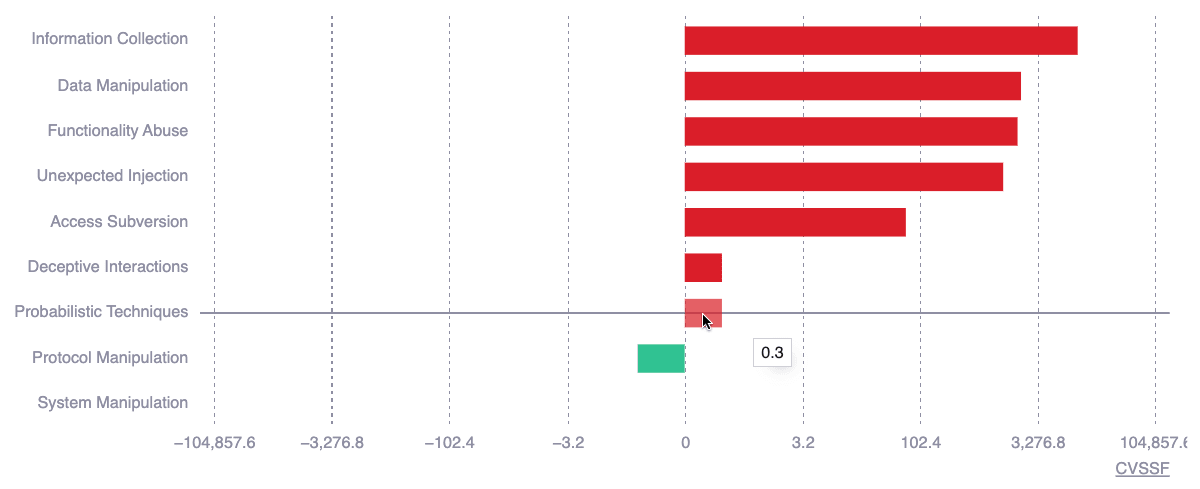
This chart shows you how risk exposure (in CVSSF units) has changed over time across the nine categories that group the types of vulnerabilities in Fluid Attacks' classification. This information helps you with an overview of the kinds of issues related to changes in your risk exposure.

- Types of vulnerabilities are categories into which detected security issues most likely fall. The chart shows a categorization at a higher level.
- This chart uses a logarithmic scale to effectively display exponential differences in a compact format.

 icon and then on a suitable option (30, 60, 90 or 180 days).
icon and then on a suitable option (30, 60, 90 or 180 days).Days since last remediation
This figure is the number of days since a code fix successfully remediated a vulnerability. This information may provide insight into the promptness with which your team addresses security issues.
Mean time to request reattacks
This figure is the average number of days it takes your team to request a reattack, i.e., a retest to verify the effectiveness of code fixes, after the vulnerability in question is reported. This information can serve as one factor to assess the responsiveness of your team to security issue reports.
Vulnerabilities being reattacked
This figure is the number of vulnerabilities for which currently a reattack has been requested and a response by Fluid Attacks is in the works. This may be one factor to assess your team's productivity.
Days until zero exposure
This figure is an estimated timeframe for fixing all vulnerabilities reported to date. It is calculated using the estimated remediation times for each weakness we have recorded in our database and the types and number of vulnerabilities reported in your groups. This information may help you set goals for your remediation efforts.
Mean time to remediate (MTTR) benchmark
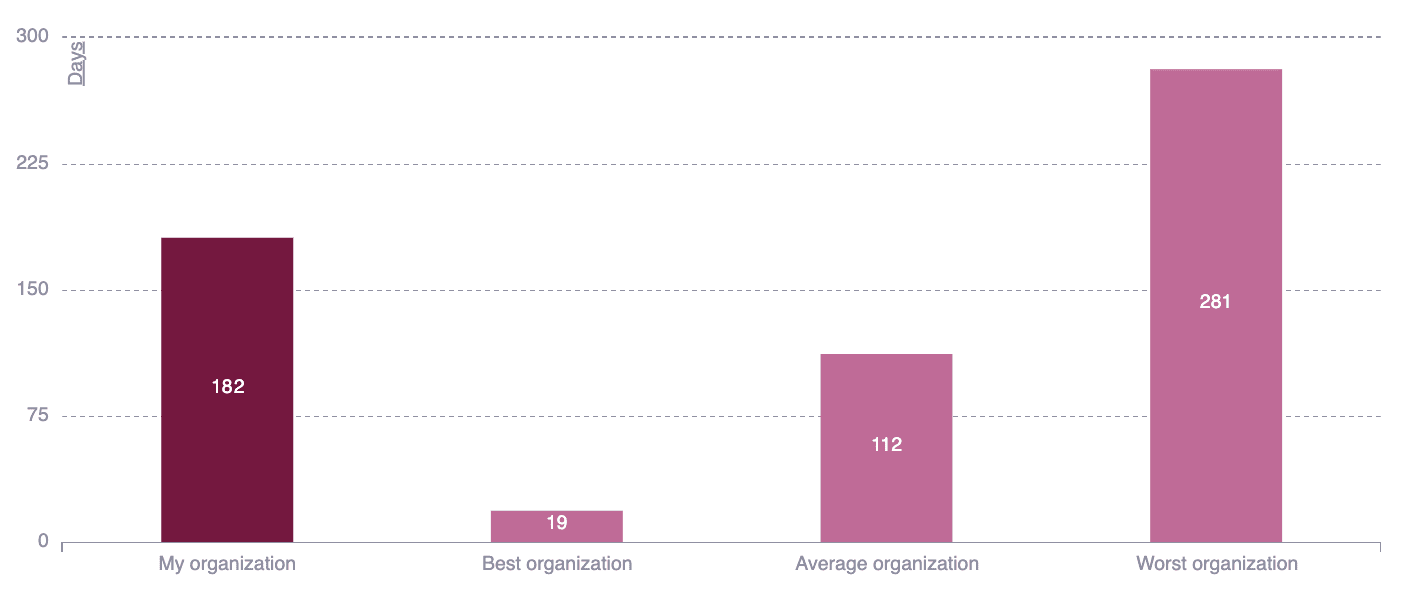
This chart displays the average number of days it takes your team to remediate a vulnerability weighted by risk exposure as measured using the CVSSF metric. Further, it allows comparing your performance against that of the best and worst performing organizations, groups or portfolios, as well as against the average value. This benchmark helps you to evaluate the efficiency of your remediation process compared to your peers and set goals.

 icon:
icon:- All: Default view (all vulnerabilities are included)
- No treatment: See only data for vulnerabilities whose Status was set to Safe as they were Untreated
- 30: See data of the last 30 days
- 90: See data of the last 90 days
- All: See data since the creation of the organization
Mean time to remediate (MTTR) by CVSS severity
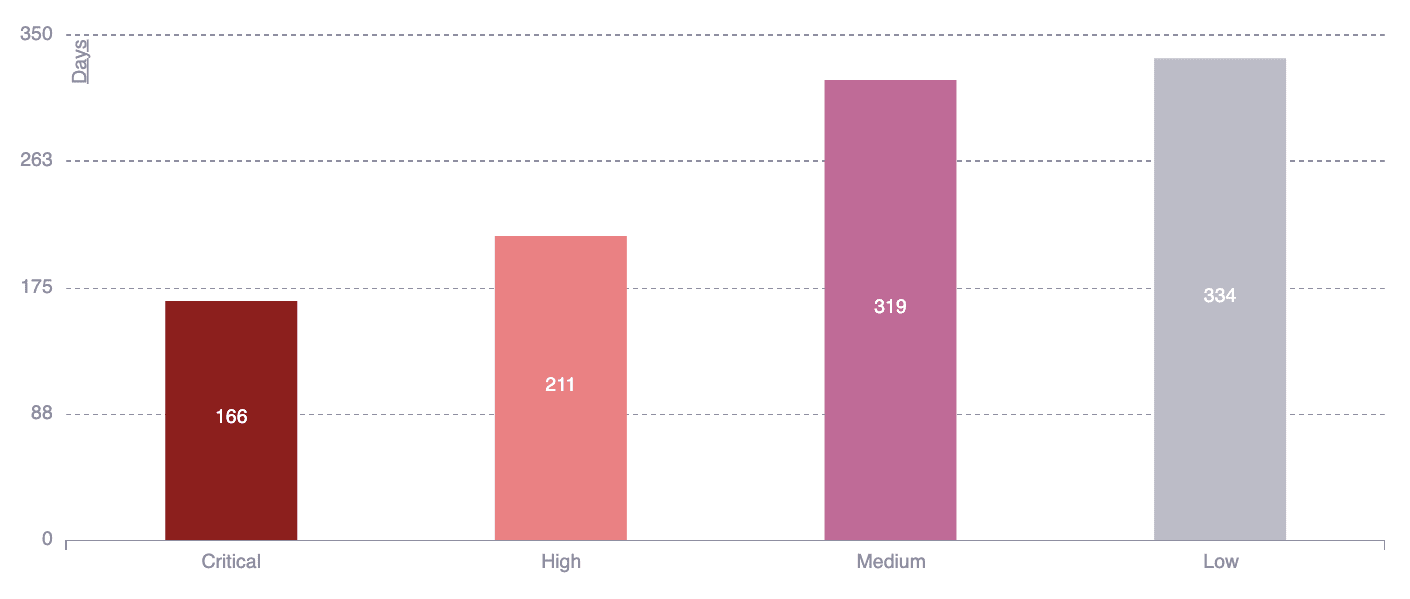
This chart shows the average time to remediate vulnerabilities weighted by risk exposure, differentiating by the qualitative severity rating. The qualitative rating groups CVSS scores as follows: Low = 0.1 - 3.9; medium = 4.0 - 6.9; high = 7.0 - 8.9; critical = 9.0 - 10.0. The information in this chart helps you understand how the severity of vulnerabilities impacts your remediation time.

 icon:
icon:- Vulns weighting by exposure: Default view
- Vulns (unweighted): See the unweighted mean time to remediate vulnerabilities
- Vulns (no treatment, weighted): See only data of remediation of risk exposure related to vulnerabilities whose Status was set to Safe as they were Untreated
- Vulns (no treatment, unweighted): See only data for vulnerabilities whose Status was set to Safe as they were Untreated
- 30: See data of the last 30 days
- 90: See data of the last 90 days
- All: See data since the creation of the organization
Accepted vulnerabilities by CVSS severity
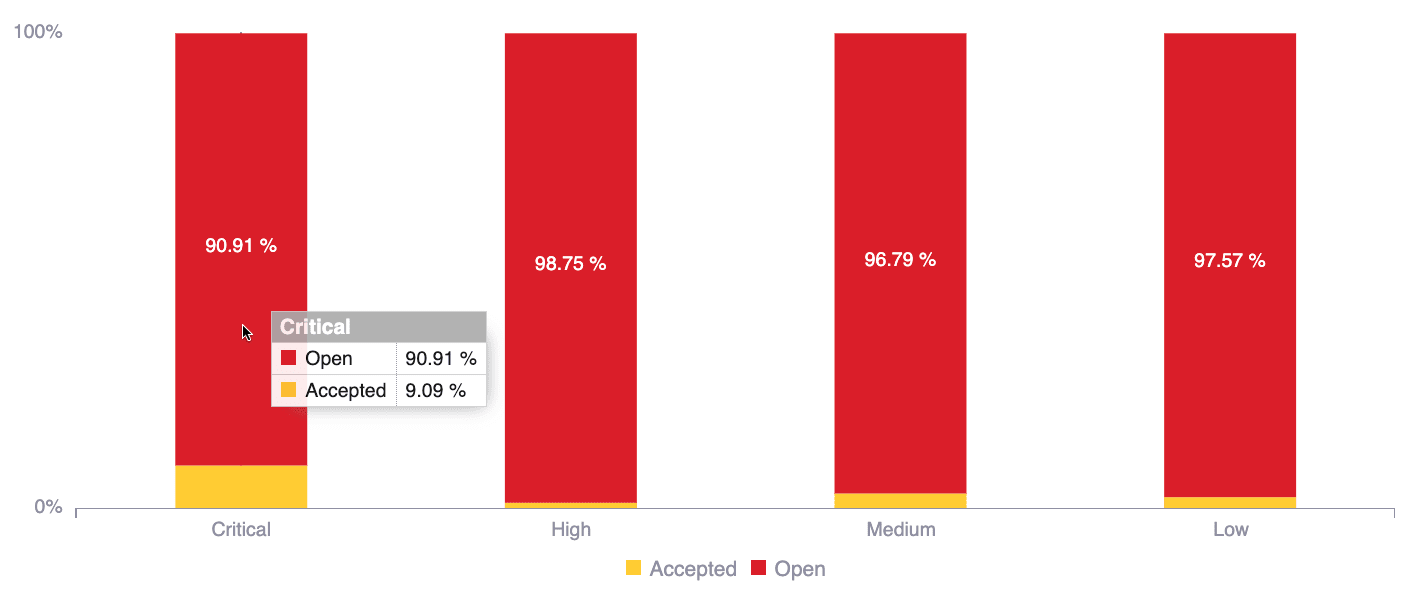
This chart displays the shares of accepted versus open vulnerabilities, categorized by qualitative severity rating (low, medium, high, and critical). Open vulnerabilities are those that have not been remediated nor accepted. This information helps you understand the risks you have chosen to accept.
- Hover over a bar to see all the complete percentages information
- Hover over a chart legend to highlight the corresponding portion in the chart
- Click on a chart legend to hide the corresponding information from the visual comparison
Vulnerabilities by assignment
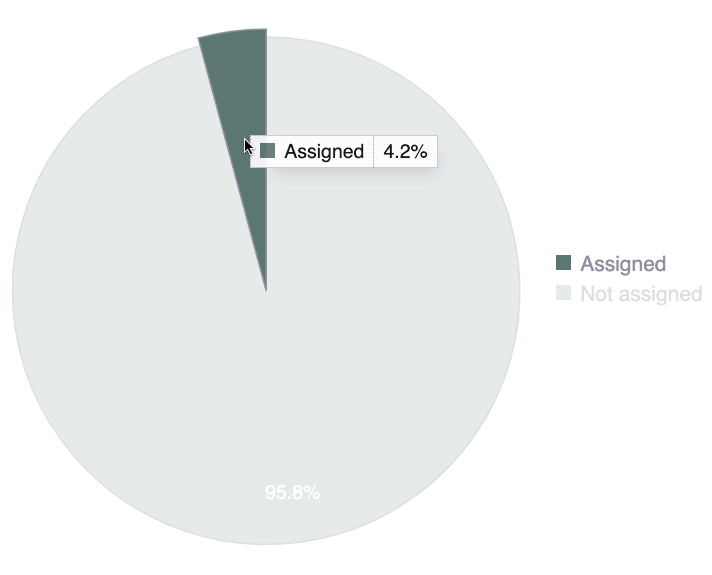
This chart shows the percentage of vulnerabilities not yet remediated that have been assigned to your team members for fixing versus those still unassigned. This chart provides a quick overview of your vulnerability assignment.
- Hover over a slice to see it highlighted along with the name of the assignment status and corresponding percentage
- Hover over a chart legend to highlight the corresponding slice
- Click on a chart legend to exclude the corresponding status from the percentage calculation
Status of assigned vulnerabilities
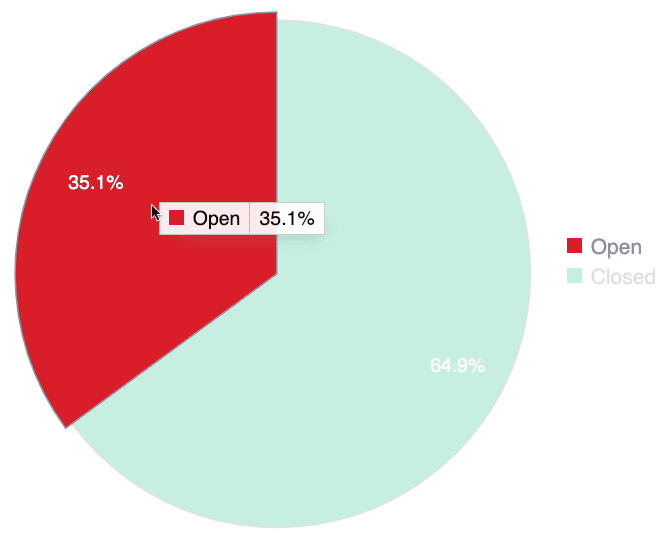
This figure presents, of all vulnerabilities that were assigned for remediation, what percentage is open (pending to be fixed) and what percentage is closed (already fixed). This information allows you to track the progress of your team in addressing assigned vulnerabilities.
- Hover over a slice to see it highlighted along with the name of the vulnerability status and corresponding percentage
- Hover over a chart legend to highlight the corresponding slice
- Click on a chart legend to exclude the corresponding status from the percentage calculation
Top weaknesses by exposure


 icon:
icon:- Exposure: Default view
- Vulns: See ranking in number of vulnerabilities instead of risk exposure
- Code: See ranking in risk exposure caused only by vulnerabilities found in source code
- Infra: See ranking in risk exposure caused only by vulnerabilities found in infrastructure
- App: See ranking in risk exposure caused only by vulnerabilities found in the running application
Vulnerabilities treatment
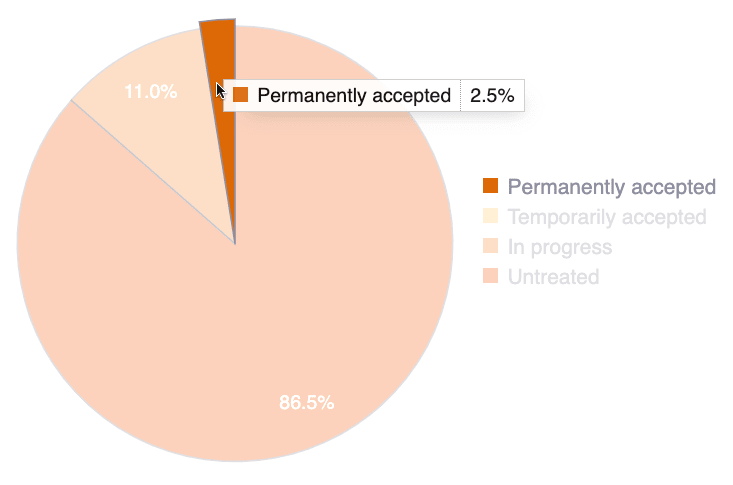
This chart displays the distribution of detected vulnerabilities still present in your systems by their current treatment:
- Permanently accepted: Vulnerabilities you do not intend to fix, accepting the risks permanently (you can, nonetheless, fix them at any given moment without the platform causing any complication)
- Temporarily accepted: Vulnerabilities you intend to fix later, accepting the risks until a specific date
- In progress: Acknowledged vulnerabilities assigned to one of your team members for remediation
- Untreated: Newly reported vulnerabilities awaiting treatment assignment
- Hover over a slice to see it highlighted along with the name of the treatment status and the corresponding percentage
- Hover over a chart legend to highlight the corresponding slice
- Click on a chart legend to exclude the corresponding status from the percentage calculation
Reporting technique
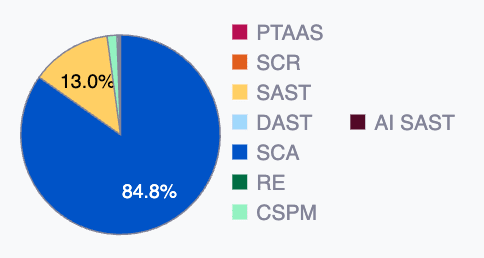
This chart shows the percentage breakdown of all reported vulnerabilities based on the security testing technique used to detect them. This information provides insights into the kind of issues more frequently present in your system. The techniques are the following:
- PTaaS: Dynamic analysis done manually
- SCR: Static code analysis done manually
- SAST: Automated static code analysis
- DAST: Automated dynamic analysis
- SCA: Automated analysis of third-party dependencies
- RE: Reverse engineering of your system done manually
- AI SAST: AI-powered static code analysis
- Hover over a slice to see it highlighted along with the technique's name and corresponding percentage
- Hover over a chart legend to highlight the corresponding slice
- Click on a chart legend to exclude the corresponding technique from the percentage calculation
Active resources distribution
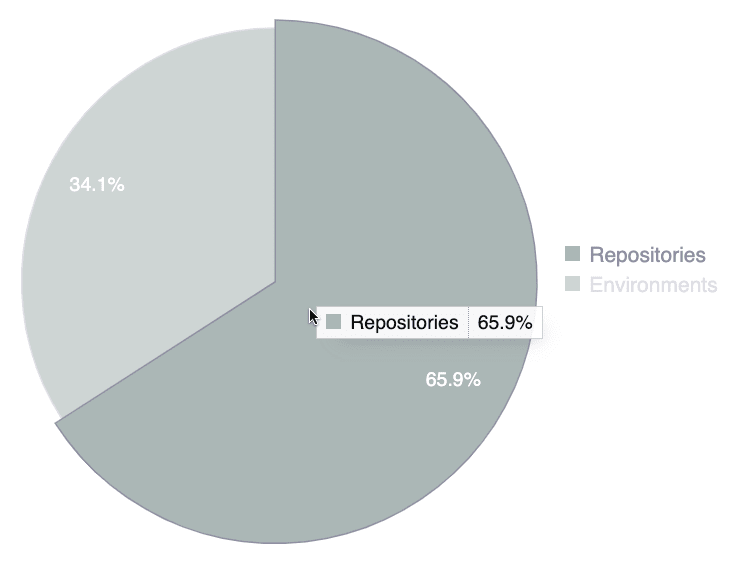
This chart illustrates the composition of your assets under assessment, contrasting the share represented by source code repositories with the share comprised of URLs or IPs linked to those repositories. This information might be useful for characterizing the scope of evaluation.
- Hover over a slice to see it highlighted along with the resource's category and corresponding percentage
- Hover over a chart legend to highlight the corresponding slice
- Click on a chart legend to exclude the corresponding category from the percentage calculation
Total weaknesses

This figure is the number of weaknesses reported to you out of all the types recognized by Fluid Attacks' categorization. These categories are the ones into which security issues found in your system most likely fall.
Total vulnerabilities
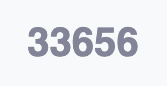
This figure is the total amount of reported security issues with a specific location within your system. This information may be of help to justify the need for additional security investments.
Total exclusions

Exclusions are vulnerabilities deliberately omitted by you. The total number of exclusions your group has is shown.
Exclusions by root
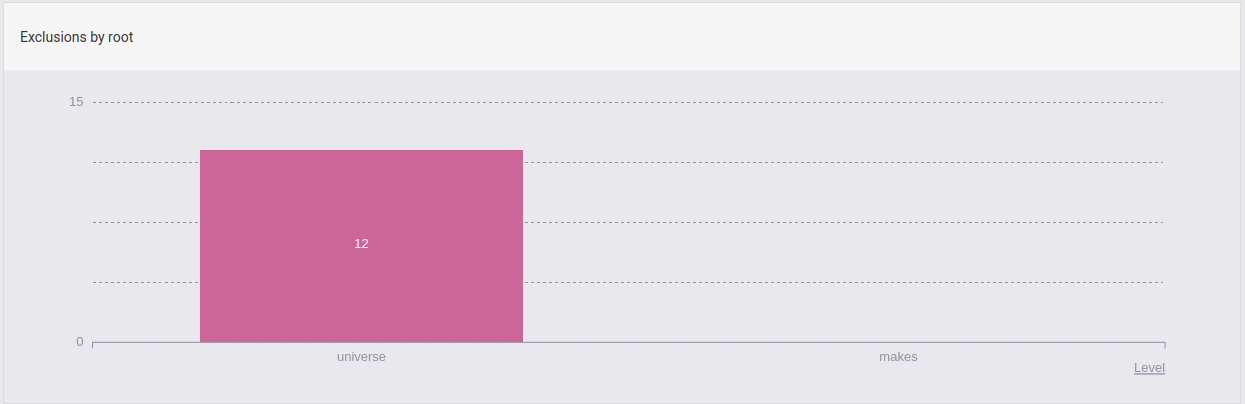
These are all your exclusions categorized by root.
Vulnerabilities by tag

This chart shows the number of vulnerabilities for each of the tags your team has categorized them into when assigning a treatment. This information allows you to analyze the security issues in your software using categories that are especially significant for your team.
Vulnerabilities by Priority score

This chart shows the number of vulnerabilities for each of the Priority values your team has given them when assigning a treatment. This information might help your team to understand its vulnerability prioritization strategy.
Accepted vulnerabilities by user
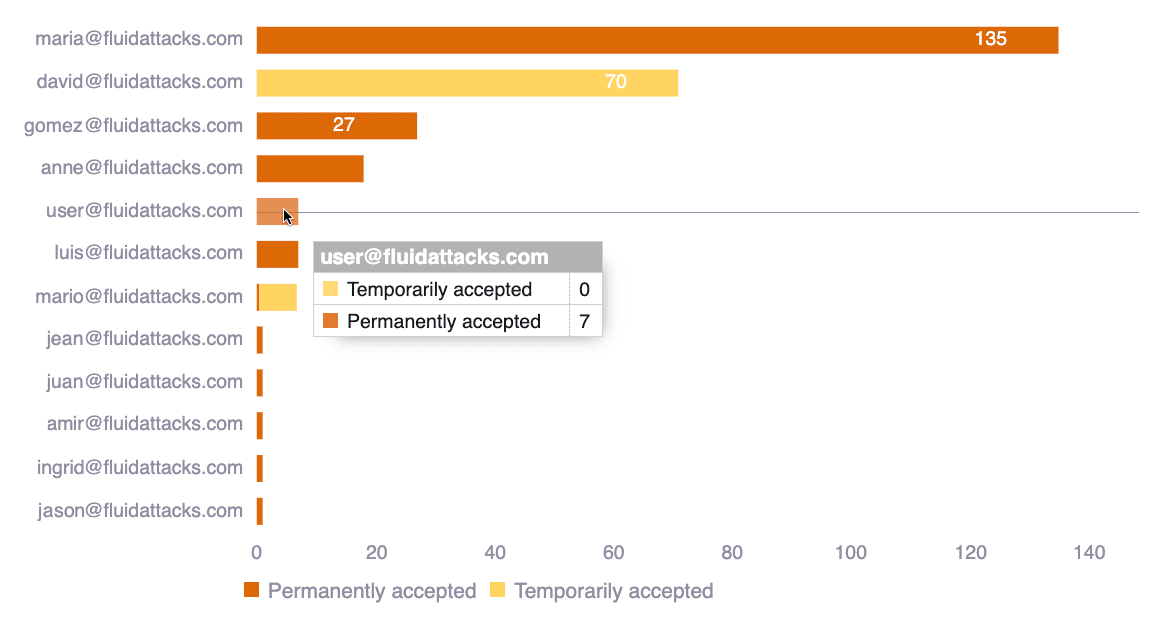
This chart shows you the number of accepted vulnerabilities grouped by the user who assigned the treatment. This information provides details about accountability for this important vulnerability management decision.
- Hover over a bar to see all the complete number information
- Hover over a chart legend to highlight the corresponding portion in the chart
- Click on a chart legend to hide the corresponding information from the visual comparison
Exposure by assignee
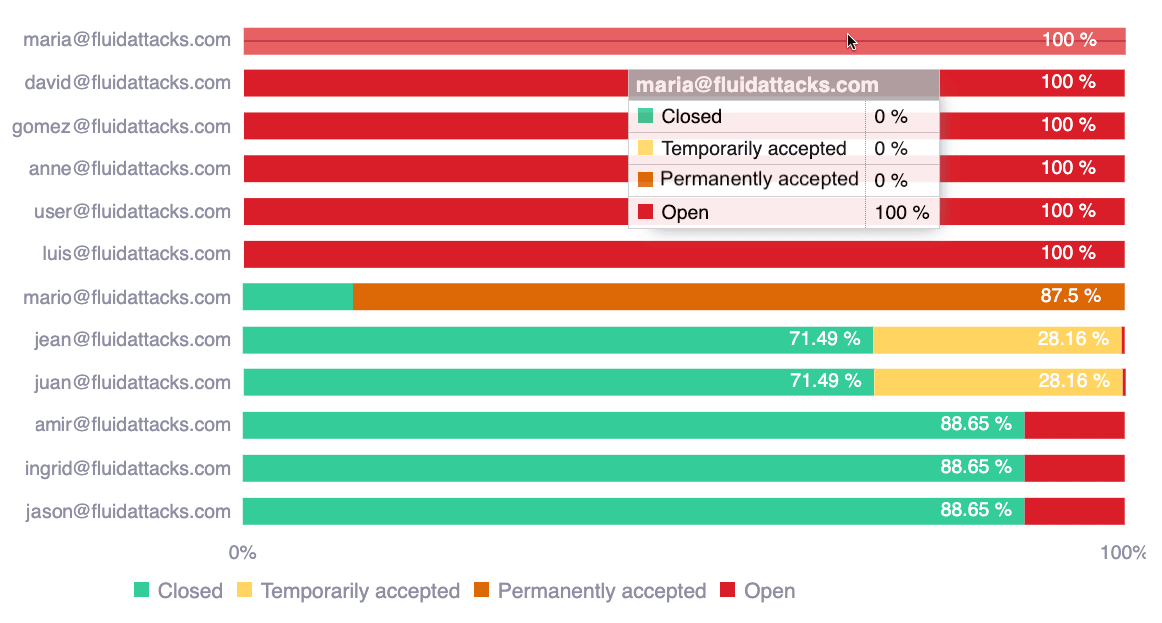
This chart shows how team members have managed the risk exposure (CVSSF) assigned to them, which is identified by the statuses of vulnerabilities that cause that risk exposure. Open vulnerabilities are those still present and unaccepted; whereas closed ones are those remediated. The information in this chart provides details about accountability for vulnerability remediation.
- Hover over a bar to see all the complete percentage information
- Hover over a chart legend to highlight the corresponding portion in the chart
- Click on a chart legend to hide the corresponding information from the visual comparison

 icon.
icon.Files with open vulnerabilities in the last 20 weeks
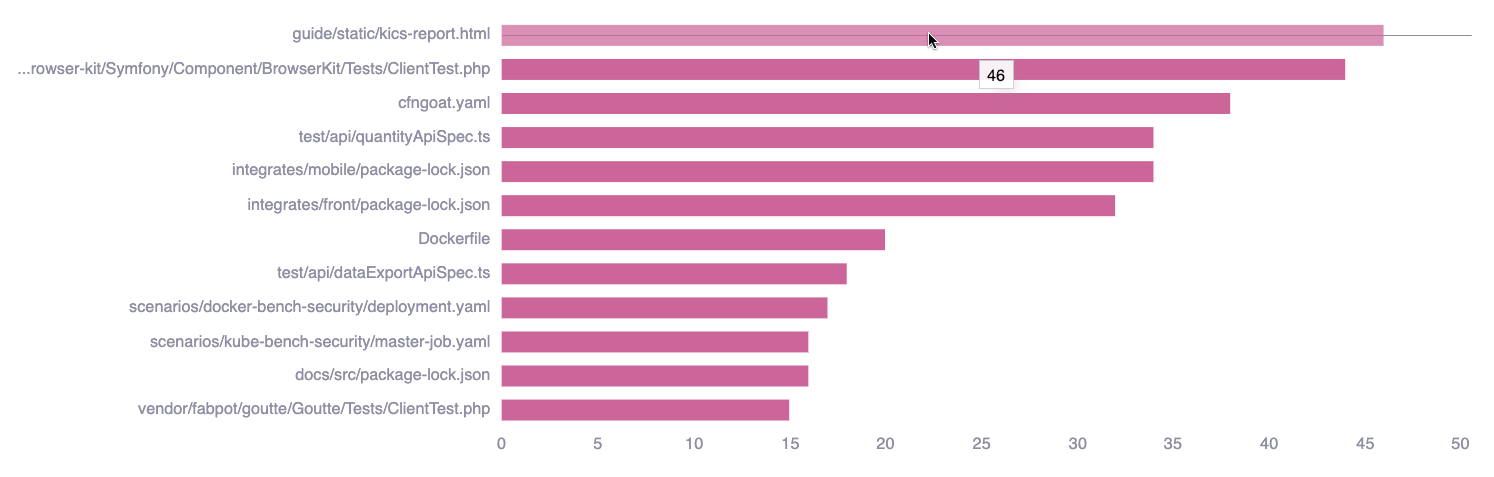
This chart shows the paths of files with vulnerabilities from the last 20 weeks, not yet remediated nor accepted, along with the total number of such vulnerabilities in each file. This information helps you pinpoint the files that should be prioritized in your remediation efforts.
Hover over a bar to see the precise number of vulnerabilities.

