Continuous Hacking methodology
Description
Fluid Attacks' Continuous Hacking is a solution that combines its application security testing tools, artificial intelligence (AI), and a team of pentesters to accurately find and help remediate security vulnerabilities throughout the software development lifecycle (SDLC) and ensure secure deployments.
Fluid Attacks reports risk exposure promptly to its clients and supports them to achieve high remediation rates and guarantee high-quality and safe products to their end users. Fluid Attacks' security testing involves different techniques, namely, static application security testing (SAST), dynamic application security testing (DAST), software composition analysis (SCA), secure code review (SCR), penetration testing as a service (PTaaS), reverse engineering (RE), and AI SAST. Further, Fluid Attacks uses its own AI tool to sort files in a code repository by their probability of containing security vulnerabilities, thus informing Fluid Attacks' pentesters of which files to prioritize in their tests to start finding vulnerabilities faster.
Fluid Attacks accurately detects vulnerabilities in continuous cycles that involve the following:
- Automated attack: Fluid Attacks' automated tools scan your system and report the common vulnerabilities, showing low false positive rates. The tools perform the following techniques: SAST, DAST, and SCA. Moreover, Fluid Attacks has an additional AI-powered tool for more advanced SAST.
- AI-powered triage: Fluid Attacks' AI is specially trained with thousands of snippets of vulnerable code. A dedicated module helps prioritize potentially vulnerable files for review.
- Manual security testing: Fluid Attacks' highly certified team of pentesters continuously examines code, infrastructure and applications for security vulnerabilities through secure code review, PTaaS and reverse engineering.
- Release process: Fluid Attacks' experts review the findings, discard potential false positives and assess the validity of results.
- Escapes validation: Fluid Attacks' experts seek to reduce false negatives by searching even deeper for vulnerabilities.
- Pruning: Fluid Attacks' experts are responsible for identifying false positives in tool and human reports to eliminate that noise at its source and prevent recurrence.
- GenAI-assisted remediation: AI-powered Autofix and Custom Fix support options, available in IDE extensions and on the platform, enable rapid remediation of vulnerabilities in code.
- Reattack: Fluid Attacks' experts evaluate the effectiveness of your fixes and whether new vulnerabilities emerged due to the implementation.
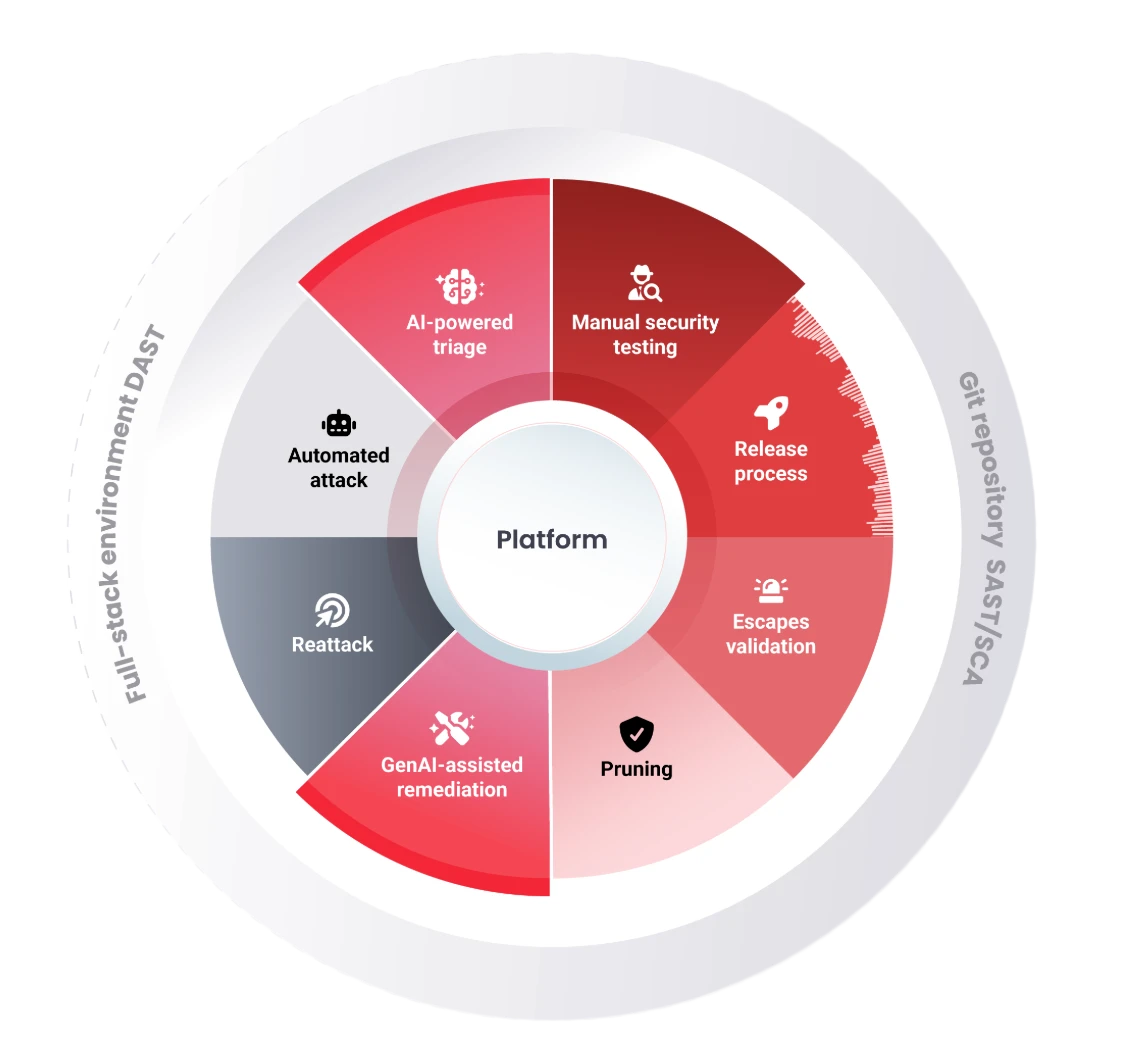
Visual depiction of Fluid Attacks' vulnerability detection cycle
Fluid Attacks helps you develop secure software and have secure deployments into production. To ensure secure development, Fluid Attacks performs tests during the entire SDLC. It reports all findings, both by its tool and pentesters, to you on its platform. There, you can learn about the specific lines of code affected, find links to documentation with examples of compliant code, control the remediation process, request retests to verify fixes and keep track of their progress in risk mitigation, among other vulnerability management tasks. To help developers easily incorporate vulnerability management into their workflow, Fluid Attacks offers integrations with several tools developers often use.
Fluid Attacks' support in the vulnerability remediation process is through custom and automated fixes generated by AI from its platform and VS Code extension. Additionally, Fluid Attacks' feature called "Talk to a Pentester" allows you to meet with an expert for help understanding vulnerabilities. Further, Fluid Attacks offers a CI agent to prevent your development team from deploying software versions with unmanaged vulnerabilities, thus helping to enforce your policies and urge the development team to fix the software security issues.
Learn about the different plans in the Continuous Hacking free trial, plans and pricing.
Needed supplies
- Version control system with Git technology
- Internet access to code repositories, with read and clone privileges (if access is through a private network, its proper configuration and credentials are needed)
- URLs of the environments and/or installers for mobile apps (.apk, .ipa) to test
- Access credentials to every application (for each role to test)
- Access permissions to the integration environment

Ideally, all system credentials should be usable from Linux without human intervention.
Scope
The scope of testing is defined by the active elements within it. Specifically, it is made up of active repositories and mobile environments registered on the platform, excluding those URLs and endpoints expressly excluded by the client. Furthermore, if an unexpected endpoint is identified in the code, the client's authorization is needed to include it within the scope.
All documentation about managing the scope is in Manage assets to test.
Verification of security requirements
Fluid Attacks Continuous Hacking reviews the client's compliance with all the security requirements carefully curated from several important international standards. These checks are mandatory and not customizable, as the solution is designed for comprehensive testing. The client can alternatively use the Fluid Attacks CLIs for targeting specific weaknesses, which are linked to requirement violations.

Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.