Explore the user menu
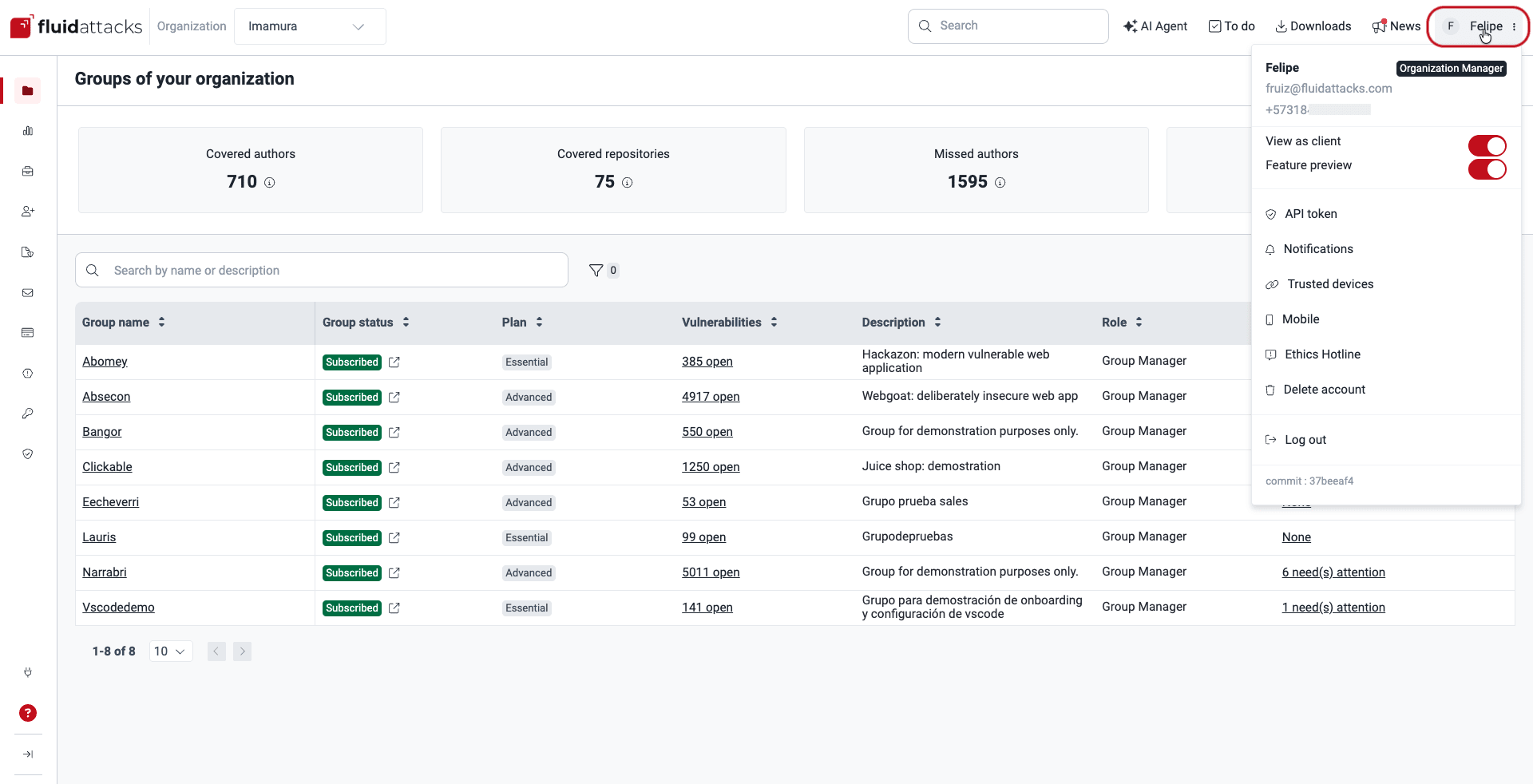
See your name, email, phone number and role
The top of the user menu displays your username, email address, mobile phone number and role within the organization. Bear in mind that your role at the group level is not necessarily the one you have at the organization level. To learn about the available roles and their permissions, read Understand roles.

Generate or revoke the API Token
The API token option lets you generate or revoke a token for accessing and utilizing the platform's API as well as Fluid Attacks' integrations. To generate the token, go to API token > Add token, enter a name and expiration date up to six months from the current date, and click Confirm. To revoke the token, go to API token > Revoke. For more information about API token management, read Learn the basics of the Fluid Attacks API.
 API token option in the user menu
API token option in the user menu API token management pop-up window
API token management pop-up windowManage notifications
The Notifications option directs you to a platform section that allows you to customize the alerts you want to receive at your email address. For a comprehensive understanding of each alert, read Enable and disable notifications.
 Notifications option in the user menu
Notifications option in the user menu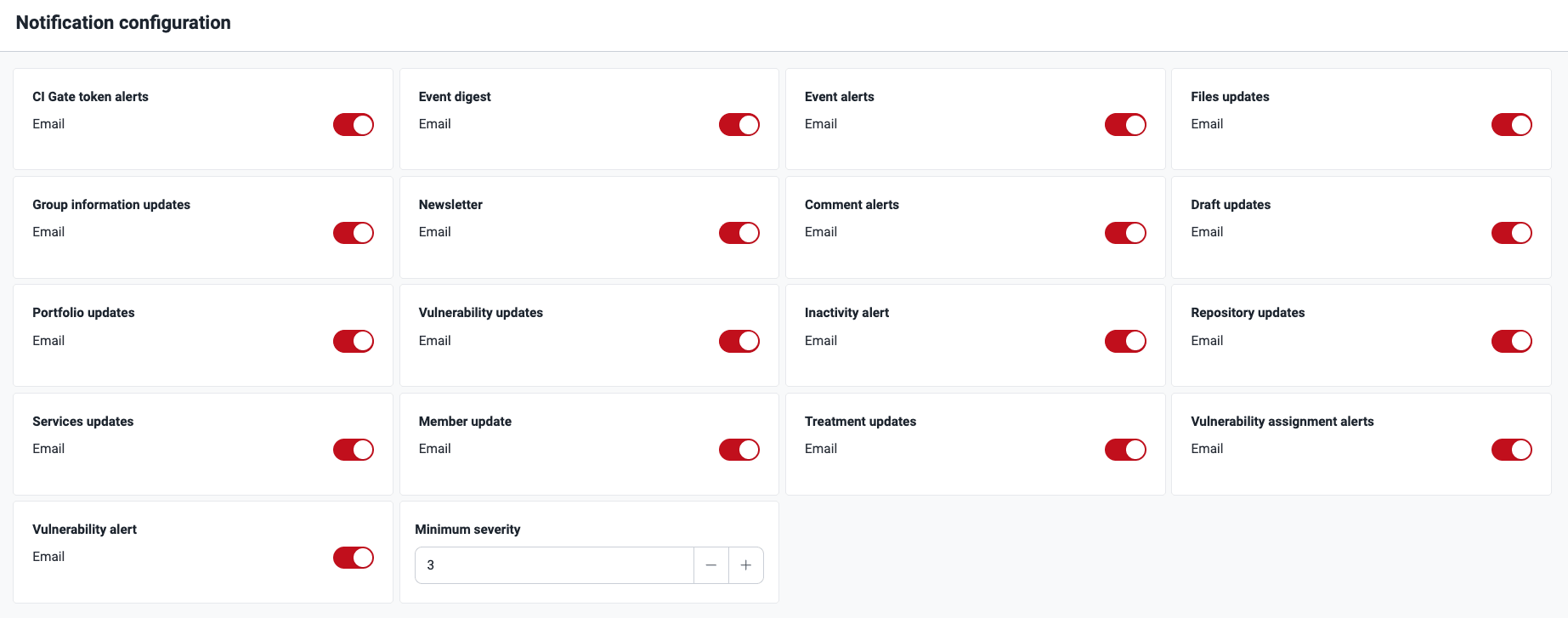 Notifications section
Notifications section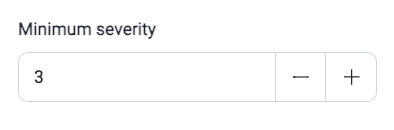
Manage your trusted devices
Trusted devices are registered during the platform login process. This feature temporarily eliminates the need to provide a verification code when you access the platform with those devices. You can see a list of the latter in the section accessible by clicking the Trusted devices option.
 Trusted devices option in the user menu
Trusted devices option in the user menu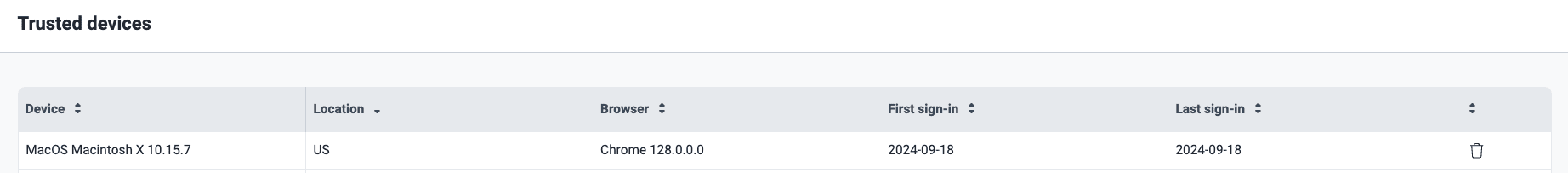 Trusted devices section
Trusted devices section- Device: Operating system
- Location: Country of login
- Browser: Browser name
- First sign-in: Initial login date
- Recent activity: Last login date from the trusted device.
To delete the device, simply click on the trash can icon ( ).
).

- The "jti", which is an ID of a JSON Web Token (JWT), stored in browser cookies
- Your web browser details
- Your operating system details
However, if you do not select this option, the platform then requires a one-time password (OTP) each time you log in.
Register or change your phone number
The Mobile option enables you to register or update your mobile phone number, a requirement for downloading reports from Fluid Attacks' platform reports.

Clicking Mobile opens a pop-up window. If you have not registered your number yet, add it and enter the verification code sent via SMS or WhatsApp message.
 Mobile pop-up window
Mobile pop-up window Option to edit phone number
Option to edit phone numberEthics Hotline
The Ethics Hotline option takes you to a third-party platform where you can submit anonymous feedback. You can report cases such as complaints on your behalf or other's. However, cases regarding positive experiences are also allowed for submission.

Delete account
Choose Delete account to trigger the steps to permanently remove your account and access privileges if you no longer need the platform.


 Note: Regardless of their role, all members are automatically removed after 90 days of inactivity.
Note: Regardless of their role, all members are automatically removed after 90 days of inactivity.Log out

Platform version

View as client


Feature preview


