Find reachable dependency vulnerabilities
Fluid Attacks' static code scans detect third-party dependencies used in your software and verify whether it is actually using the dependencies' vulnerable functions. Ensuring that detected dependency vulnerabilities are actually reachable by threat actors is possible thanks to Fluid Attacks' Reachability feature.
Know which dependencies have vulnerabilities
Fluid Attacks allows you to understand your software supply chain, identifying the dependencies in your software and indicating for which of them vulnerability advisories have been issued.
If using the platform, this information is shown in the Packages section, along with details such as the dependency's location in your projects and whether it contains malware.
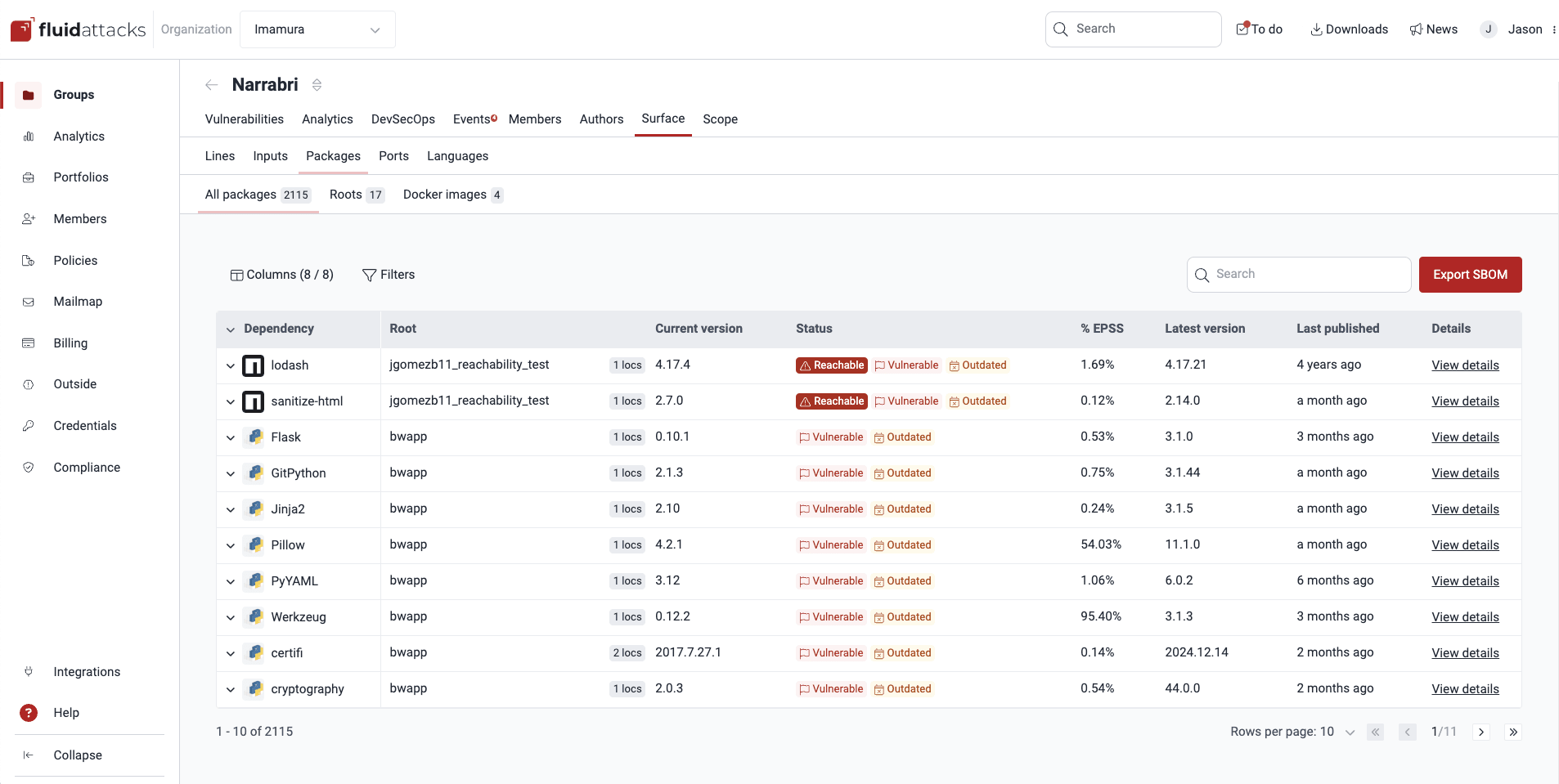
This section shows the dependencies with associated advisories as 'Vulnerable' and, importantly, differentiates which are 'Reachable'. Regarding the latter, Fluid Attacks identifies whether your application is calling a function or other kind of code element related to the vulnerability, thus raising the chances of the vulnerability in question being exploitable in the context of your application.
Know reachable dependency vulnerabilities
Leveraging the Reachability feature, Fluid Attacks' scans track down your use of the third-party dependencies' vulnerable functions. If it is confirmed that your software is at risk by using those dependencies, then you get the corresponding vulnerability reports.
If using the platform, every reachable vulnerability is reported
- in the Packages section with the tag 'Reachable';
- in the Vulnerabilities section within the specific type of vulnerability it represents for your project.
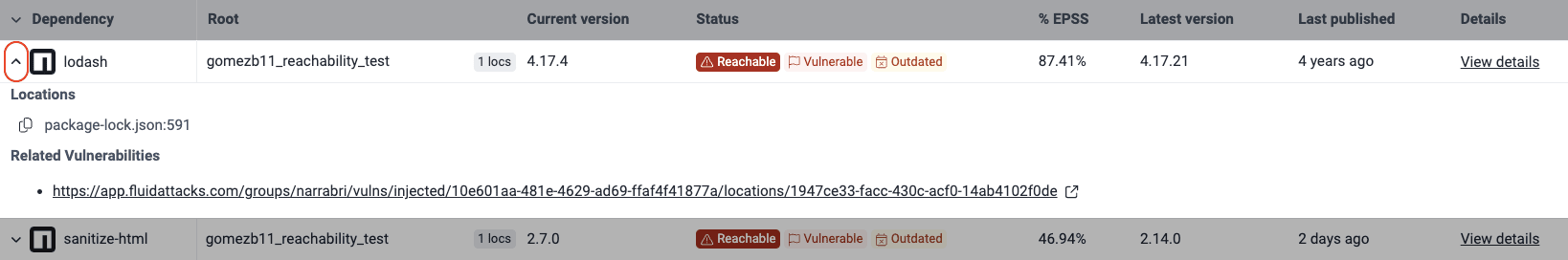
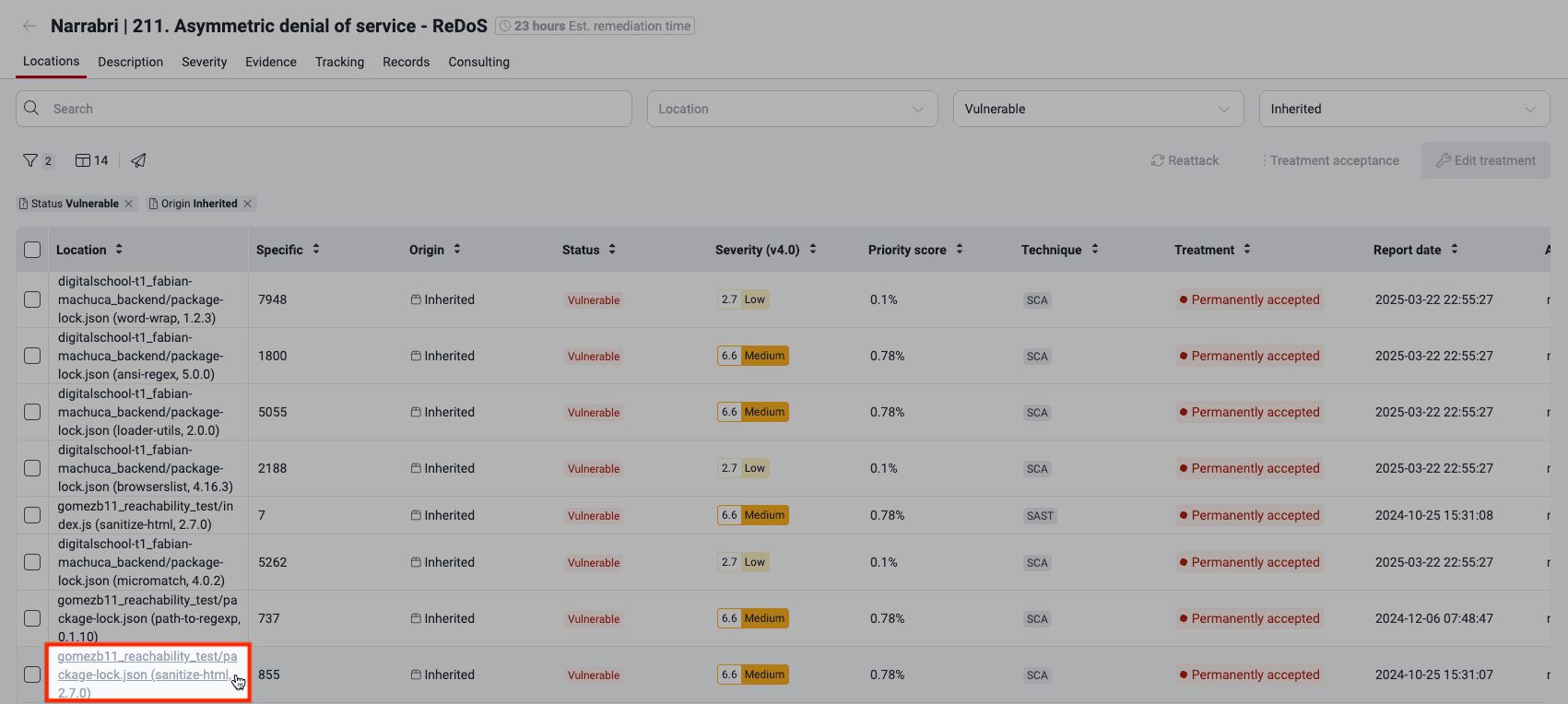
From the Packages section, to learn where the vulnerability is in your project,
- expand the row,
- click on the link under Related Vulnerabilities,
- identify the file path and line of code (LoC) that calls or leads to the vulnerable function.
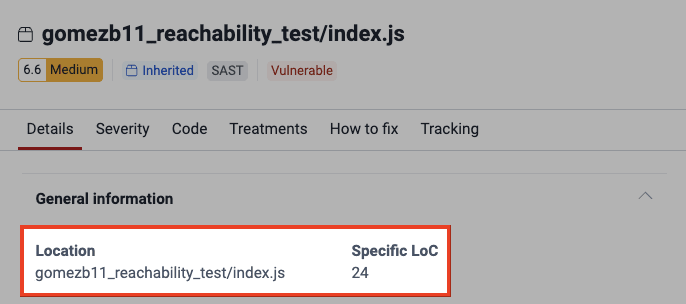
Back in the Packages section, if you click on View details, you can see the specific reachable dependency vulnerability marked with a warning sign next to its CVE ID.
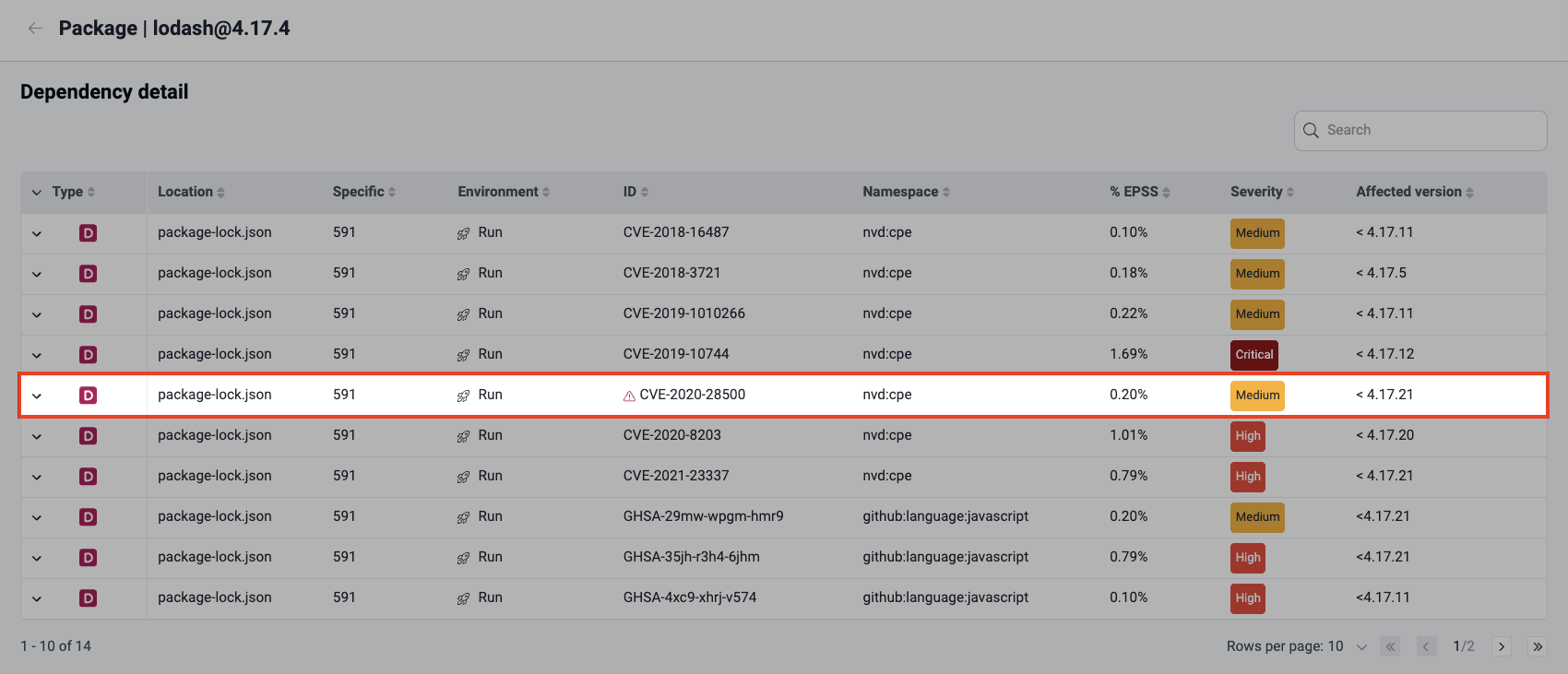
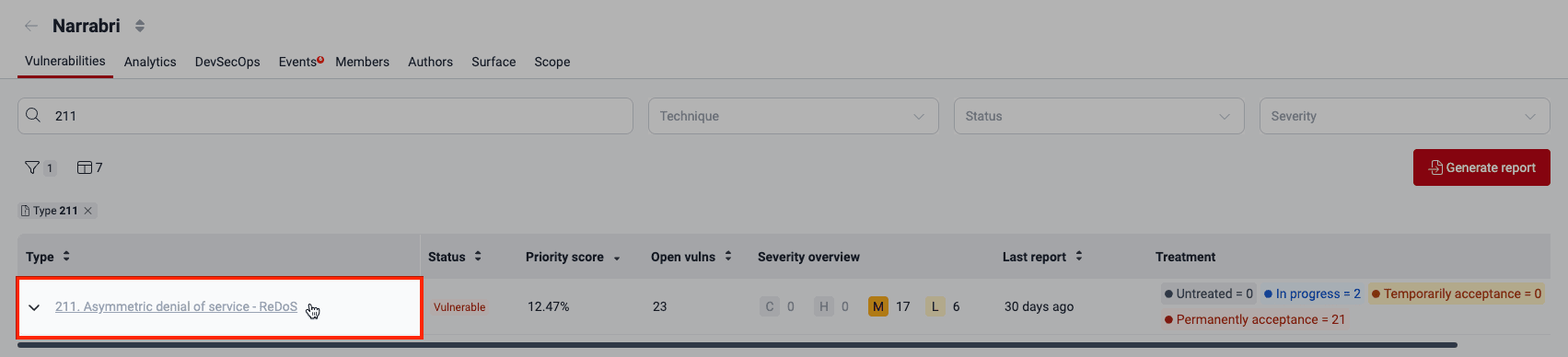
From the Vulnerabilities section, to identify a reachable dependency vulnerability,
- select a type of vulnerability,
- select a vulnerability whose Origin is 'Inherited',
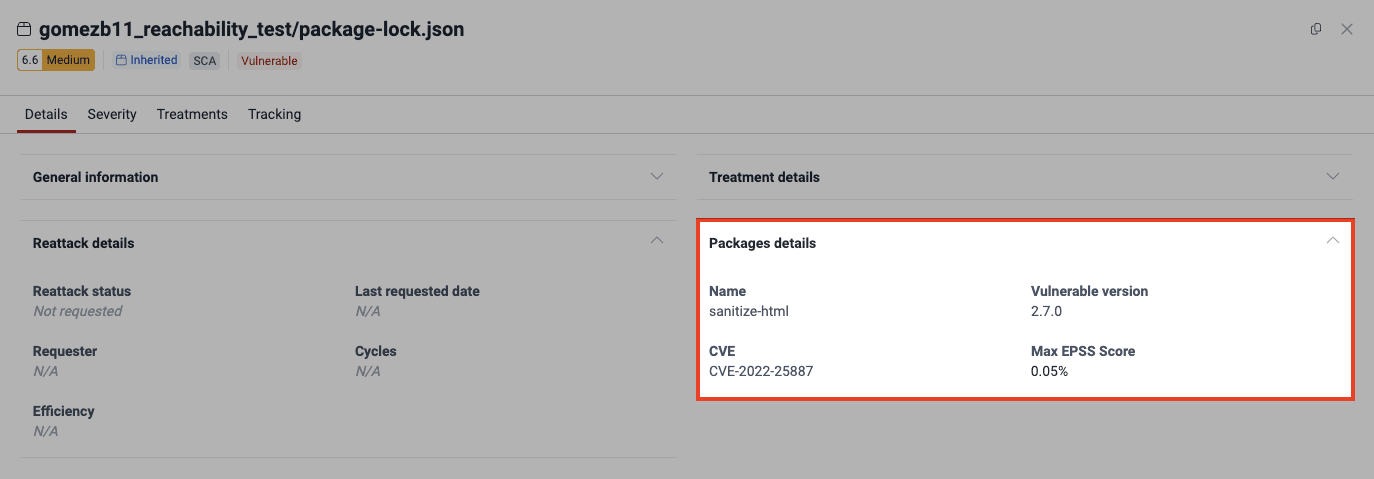
- identify within Packages details the information about the vulnerable dependency version in use and its vulnerability's exploitability.
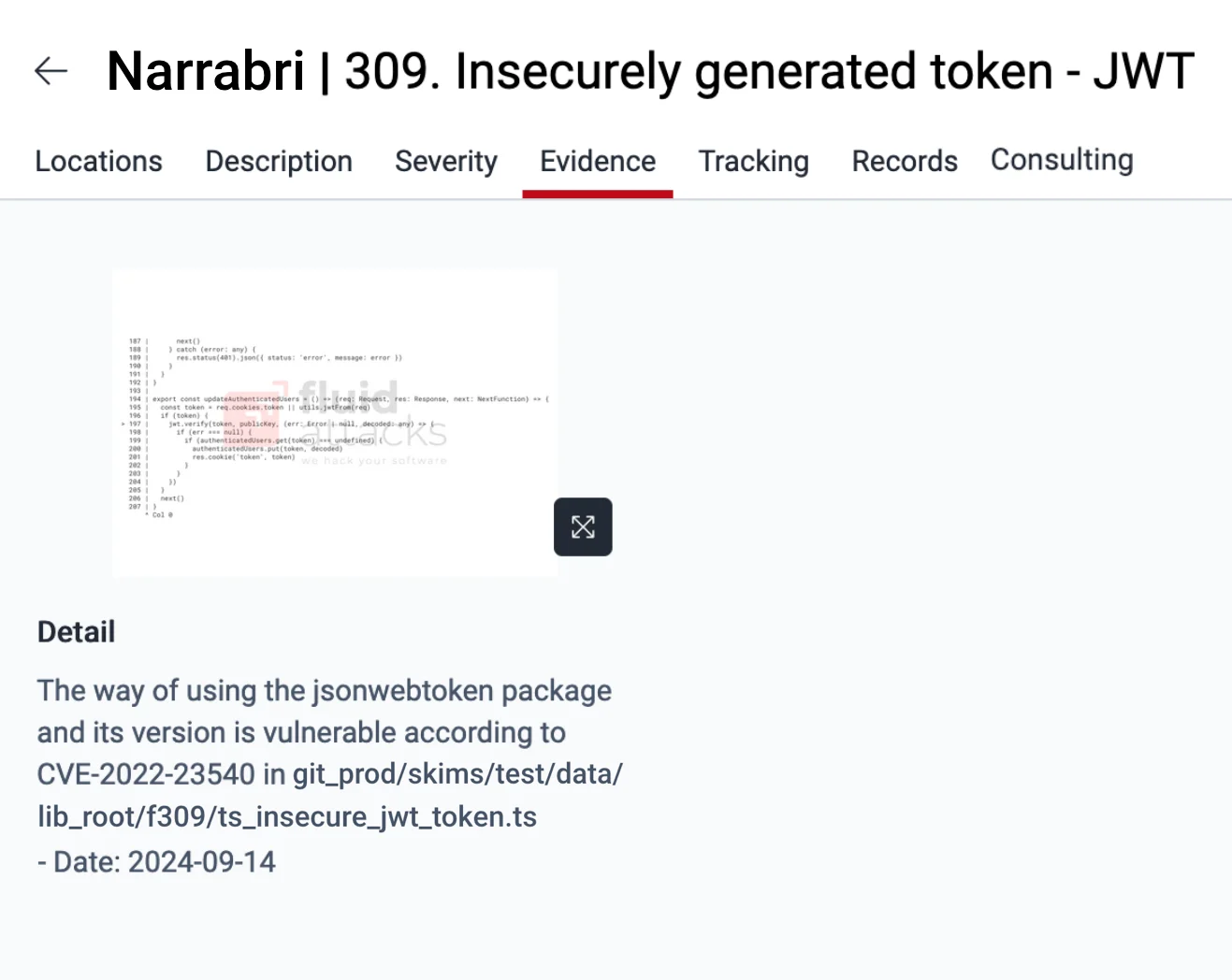
Moreover, in the Evidence section of the type of vulnerability, you can see a screenshot showing your vulnerable code in context along with the mention of the CVE ID reported for the dependency.

Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.