Introduction
Interacts is a Model Context Protocol (MCP) server programmed with Pydantic AI that provides tools for interacting with the Fluid API, enabling vulnerability management, organization insights, and GraphQL query execution. While used in the platform as the AI Agent, it allows integration with AI tools.
Features
- Vulnerability Management: Fetch and analyze vulnerabilities across groups.
- Organization Insights: Access organization and group information.
- Analytics: Retrieve analytics data for organizations and groups.
- GraphQL Integration: Execute custom GraphQL queries.
- Type System Exploration: Inspect API types, mutations, and queries.
- Knowledge Base: Access to AI-powered knowledge base assistance.
Architecture
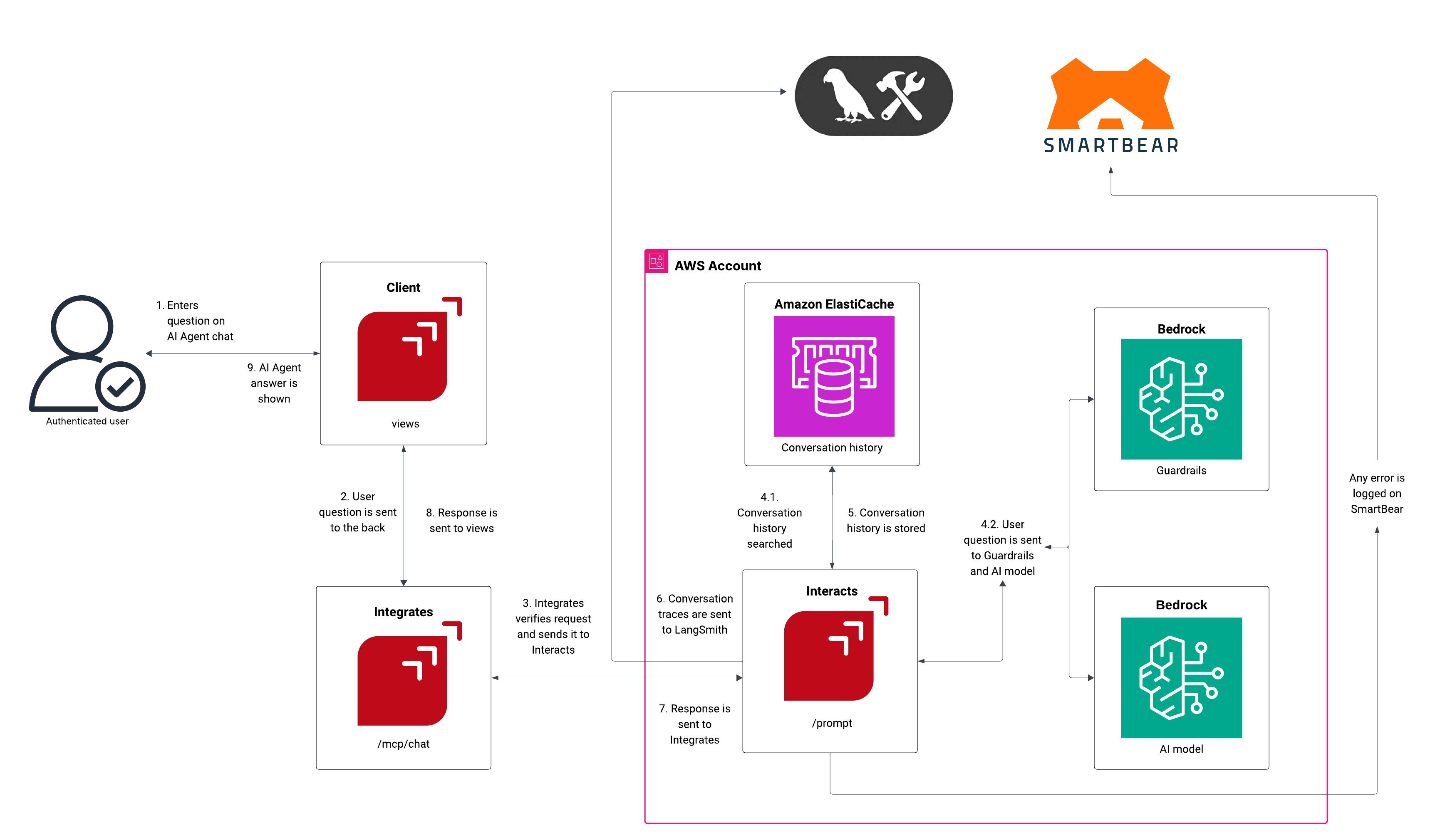
- User writes request on chat
- An authenticated user enters a question in the AI Agent chat interface
- The request is sent from the Client (views component)
- Request routing
- The user's question is sent to the backend (Integrates component) to the websocket endpoint (/mcp/chat)
- Integrates verifies the request and forwards it to the Interacts component to the /prompt endpoint
- Conversation context retrieval
- Interacts queries Amazon ElastiCache to search for relevant conversation history
- This provides context for the AI to maintain conversation continuity
- AI processing: The user's question is sent to two Bedrock components
- Bedrock (Guardrail): Ensures the response meets safety and appropriateness standards
- Bedrock (AI model): Generates the actual AI response
- Response generation and validation
- The AI model generates a response based on the user's question and conversation history
- The response passes through the Guardrail for safety validation and PII masking
- If the response meets safety criteria, it proceeds; otherwise, it may be modified or rejected
- Conversation history update: After processing, the updated conversation history is stored back in Amazon ElastiCache, ensuring future interactions have the complete conversation context
- Monitoring and logging: Conversation traces are sent to LangSmith for monitoring and debugging purposes
- Response delivery
- The validated response is sent from Interacts back to Integrates
- Integrates forwards the response to the Client (views)
- The AI Agent's answer is displayed to the authenticated user
- Error handling: Throughout the process, any errors are captured and logged to SmartBear for monitoring and debugging
Tools
Information Retrieval Tools
get_organization_groups- Get groups associated with an organization
- Parameters:
organization_id_or_name: Organization identifier or nameget_group_git_roots- Get Git root information for a specific group
- Parameters:
group_name: Name of the groupnickname: Root nickname (optional)search: Word to match on git URL or nickname (optional)start_cursor: Cursor to start from (optional)get_group_ip_roots- Get IP root information for a specific group
- Parameters:
group_name: Name of the groupsearch: Word to match on IP address (optional)start_cursor: Cursor to start from (optional)get_group_url_roots- Get URL root information for a specific group
- Parameters:
group_name: Name of the groupsearch: Word to match on URL (optional)start_cursor: Cursor to start from (optional)describe_graphql_type- Get detailed information about a specific GraphQL type
- Parameters:
type_name: Name of the type to inspectquery- Execute a custom GraphQL query
- Parameters:
query: GraphQL query to executevariables: Variables for the query (optional)get_organization_analytics- Retrieve analytics information for an organization
- Parameters:
organization_id_or_name: Organization identifier or namedocument_name: Type of analytics documentget_group_analytics- Retrieve analytics information for a group
- Parameters:
group_name: Group namedocument_name: Type of analytics documentget_devsecops_agent_executions- Retrieve Forces execution information for a group
- Parameters:
group_name: Name of the group to fetch executions forafter: Cursor for pagination (optional)exit_code: Filter by execution exit code (“0” for success, “1” for failure) (optional)first: Number of results to return (optional)from_date: Filter executions from this date (optional)git_repo: Filter by repository (optional)git_repo_exact_filter: Exact match filter for repository (optional)fetch_finding_vulnerabilities- Fetch vulnerabilities for a specific finding
- Parameters:
finding_id: ID of the finding to fetch vulnerabilities forstate: Filter by vulnerability state (optional)sort_criteria: Criteria to sort vulnerabilities (optional)sort_order: Order to sort vulnerabilities (optional)first: Number of results to return (optional)cursor: Cursor for pagination (optional)tags: Filter by tags (optional)package_manager: Filter by package manager (optional)technique: Filter by technique (optional)where: Filter by location (optional)treatment: Filter by treatment status (optional)severity_rating: Filter by severity rating (optional)fetch_group_findings- Fetch findings for a specific group
- Parameters:
group: Name of the group to fetch findings forstate: Filter by finding state (optional)severity: Filter by severity (optional)technique: Filter by technique (optional)where: Filter by location (optional)fetch_group_root_vulnerabilities- Fetch vulnerabilities for a specific group root
- Parameters:
group_name: Name of the grouproot_nickname: Nickname of the root to fetch vulnerabilities forstate: Filter by vulnerability state (optional)severity: Filter by severity (optional)first: Number of results to return (optional)after: Cursor to start from (optional)get_unsolved_events- Get unsolved events for a group
- Parameters:
first: Number of results to return (optional)after: Cursor to start from (optional)ask_to_knowledge_base_assistant- Ask questions to the knowledge base AI assistant
- Parameters:
query: The question to ask the knowledge base assistant
Inspection Tools
get_api_queries- Get available API query operations
- Parameters: None
get_api_mutations- Get available API mutation operations
- Parameters: None
get_mutation_details- Get detailed information about a specific mutation
- Parameters:
mutation_name: Name of the mutation to inspect
Resources
Api SDL (~50058 tokens)- GraphQL Schema Definition Language file
Fluid Attacks Overview (~2881 tokens)- Documentation about API entities, roles, and permissions
Setup
API Token
- Generate an API token for authentication with the Fluid Attacks API
Usage with Cursor and VSCode
{
"mcpServers": {
"fluidattacks-mcp": {
"type": "http", "url": "https://app.fluidattacks.com/mcp/messages/", "headers": {
"Authorization": "Bearer YOUR_API_TOKEN_HERE" }
}
}
}
Usage with Claude Desktop
Requirements
- Node.js 18 or higher installed on your system. If you don’t have it, install it from the official website.
Add the following to your mcp.json:
{
"mcpServers": {
"fluidattacks-mcp": {
"command": "npx", "args": [
"-y", "@fluidattacks/mcp" ],
"env": {
"API_TOKEN": "your_api_token_here" }
}
}
}
Tip
Have an idea to simplify our architecture or noticed docs that could use some love? Don't hesitate to open an issue or submit improvements.