Prevent the deployment of builds with vulnerabilities
CI Gate, aligned with your organization's or group's general policies, can automatically break builds that contain vulnerabilities that have not been remediated nor accepted. Breaking the build means preventing any software author from deploying a build with said vulnerabilities into production. This mechanism prompts your team to address security issues, effectively prioritizing security at that moment of the software development lifecycle.
A CI Gate token is required for installation of the gate. To use CI Gate, ensure Internet connectivity, so it can connect to Fluid Attacks' API. Continue reading to learn how to manage this token. Further below are references to configuring policies to break the build and viewing CI Gate's executions.
 Note: Token generation, update, and reset are completely up to your team.
Note: Token generation, update, and reset are completely up to your team.Generate the CI Gate token
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager-
Go to the Scope section of the group where you want to use CI Gate.
-
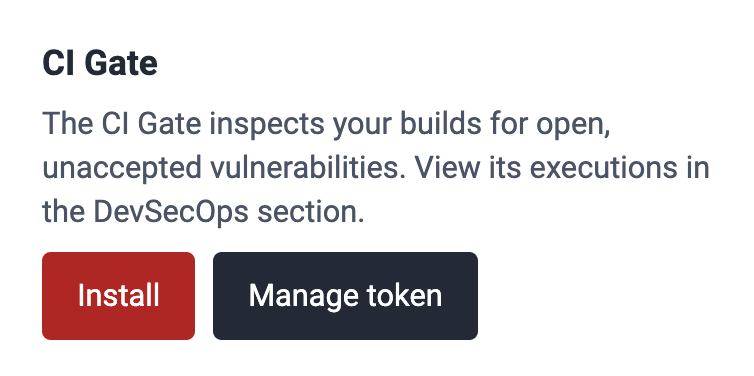
Scroll all the way down to locate the CI Gate card.
Click the Manage token button.
In the pop-up window, click on Generate.
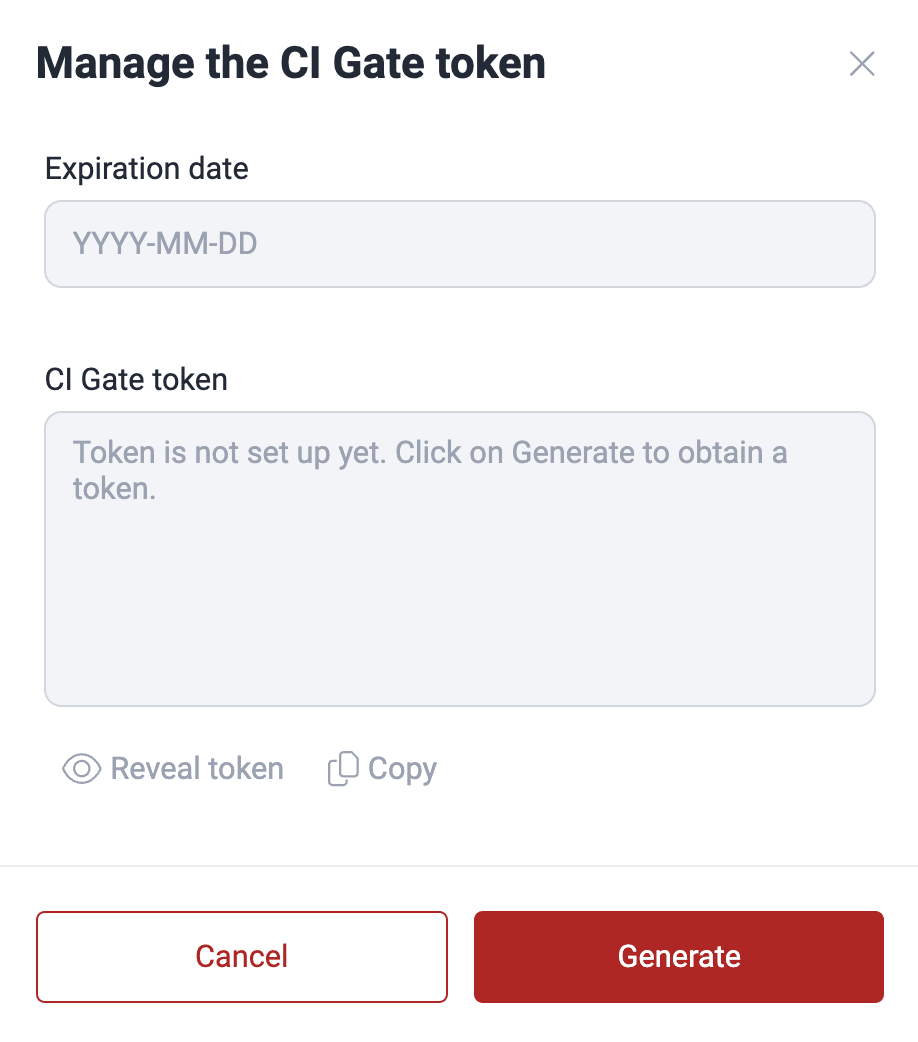
Once generated, you can click on Copy to capture the token for immediate use. The token is valid for 180 days and is unique to the group where it is created.
You can always come back and click on Reveal token to view it.
Update the CI Gate token
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerFluid Attacks' platform sends you a notification seven days before the CI Gate token expires.
Reset the CI Gate token
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerYou can reset the CI Gate token while your current one is still valid. Follow these steps:
-
Go to your group's Scope and locate the Manage token button.
-
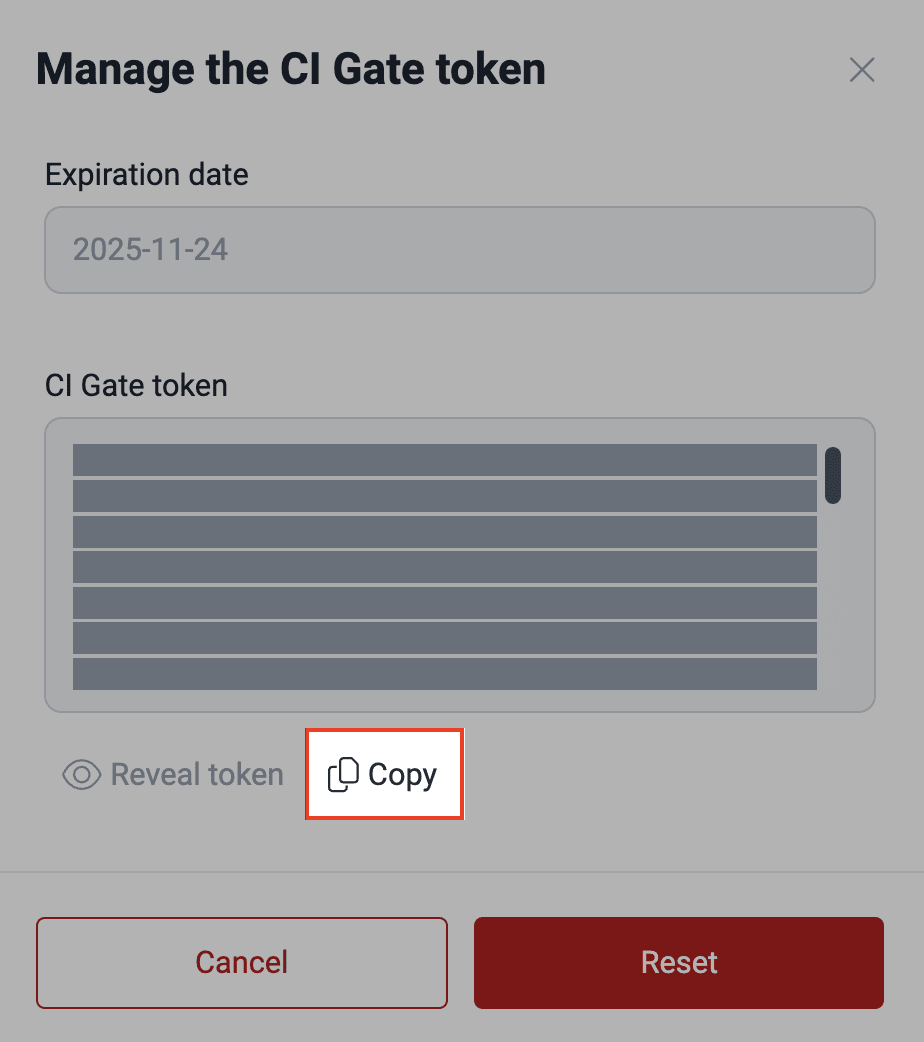
In the pop-up window, click on Reveal token.
-
Once your current token is displayed, click the Reset button to generate a new token.
The new token is generated in the pop-up window, and you can copy it for immediate use.
 Troubleshooting: If you encounter errors during token management, refresh the Scope section and retry. If the issue persists, contact Fluid Attacks support at help@fluidattacks.com with detailed information about the problem.
Troubleshooting: If you encounter errors during token management, refresh the Scope section and retry. If the issue persists, contact Fluid Attacks support at help@fluidattacks.com with detailed information about the problem.Configure policies to break the build
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager- Grace period where newly reported vulnerabilities will not break the build
- Minimum CVSS score of an open vulnerability to break the build
- Number of days until vulnerabilities are considered technical debt and do not break the build

View the CI Gate execution details
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerOn Fluid Attacks' platform, you can inspect the outcomes of each execution of CI Gate for a specific group, such as whether it broke the build and what unremedied vulnerabilities it found. To do it, go to the group's DevSecOps section. Read about the latter in View details of the security of your builds.
 Free trial
Free trial