Verify whether a fix was successful
As part of vulnerability management, you should reassess the code after a fix attempt. This is because a fix can introduce further vulnerabilities or be no fix at all for the original vulnerability.
Read the section Fix your code to understand how Fluid Attacks can help you successfully address vulnerabilities. When you have applied your fix, follow the steps on this page.
At Fluid Attacks, reassessments are called "reattacks." Do the following to request automated reattacks by the tool or manual reattacks by Fluid Attacks' team of pentesters:
Enter the group where the vulnerability you want to reattack was reported and go to the Scope section.
Click on the Update button to clone the latest version of the repository. This is to submit the version that contains the fixed code for testing.
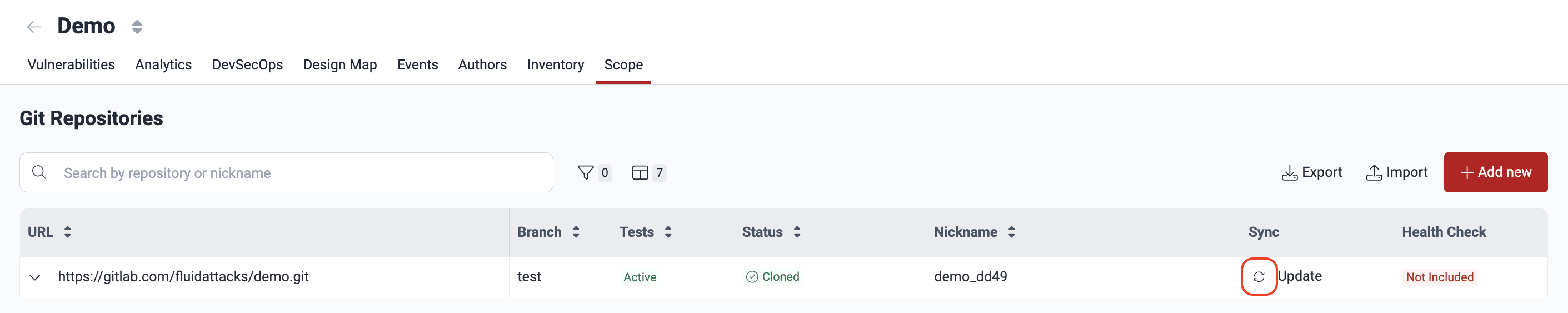
Check the Status value of the repository. When the status is 'Cloned', you can move on to step 3.
 Repos are cloned when you use this option and every two hours on workdays.
Repos are cloned when you use this option and every two hours on workdays.In the Vulnerabilities section, click on the name of the weakness you wish to reattack.
Select the path where you have already effectuated a fix and click Reattack.
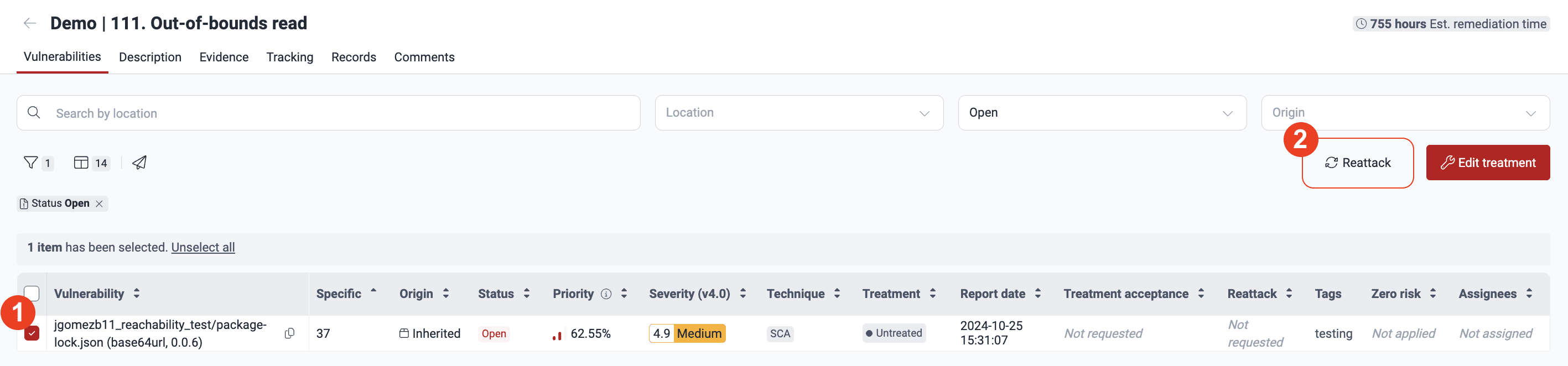
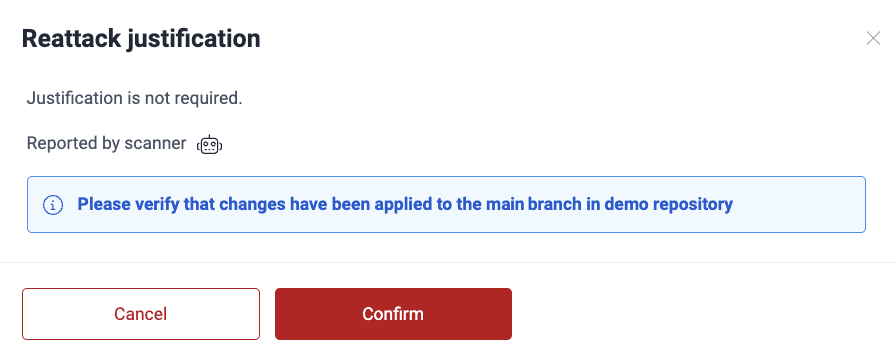
In the pop-up window, click Confirm, acknowledging that you have synced the fixed version to the platform.
 If you have the Advanced plan, and the vulnerability was reported by the team of pentesters, you instead have to describe the applied fix and click Confirm.
If you have the Advanced plan, and the vulnerability was reported by the team of pentesters, you instead have to describe the applied fix and click Confirm.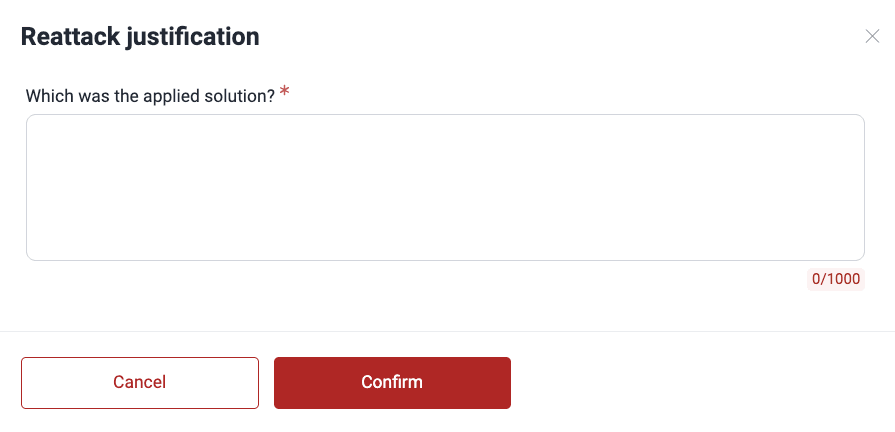
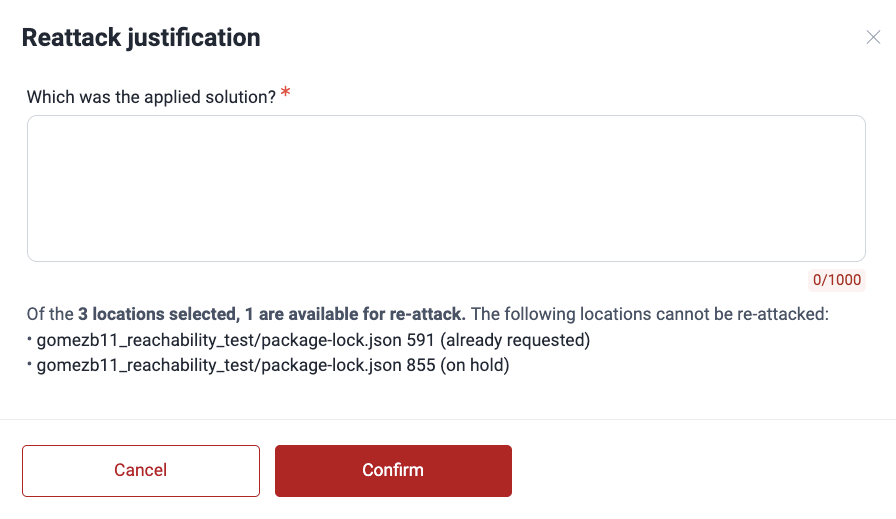
If the vulnerability is still present, you will get a comment informing you of this in the Comments section of the weakness. In the Locations table, the reattacked vulnerability will show the value Verified (vulnerable) in the Reattack column.
As a security measure, you can use Fluid Attacks' CI Gate to break the build if vulnerabilities with specific attributes are present in it.
