Continuous Hacking PoV
Fluid Attacks goes beyond a PoC (Proof of Concept) to provide potential customers with a PoV (Proof of Value). A PoC demonstrates that a solution works, but a PoV additionally helps determine if that solution is right for your company. The PoV emphasizes the value our solution will represent to your business, making it easier to justify its implementation.
This document provides detailed information about the scope, requirements, and workflow of Fluid Attacks' PoV.
Scope
Fluid Attacks' Proof of Value shows organizations the quantitative and qualitative value of Fluid Attacks' flagship AppSec solution: the Continuous Hacking Advanced plan. The PoV is explicitly agreed upon between the two parties (i.e., Fluid Attacks and the organization) and has the following scope:
- Access to the platform: it is unlimited during the entire PoV.
- Downloadable resources: Executive reports, Technical reports, and Group certificates.
- Information retention: all data collected on the platform for the organization will be deleted after two (2) weeks from the end of the PoV if the organization does not decide to become Fluid Attacks’ customer.
Requirements
Obligatory for the application to test
It must be a complete web or mobile application (i.e., back and front, not just APIs).
It must be stored in a Git repository that can be accessed by repository managers such as GitLab, GitHub, Bitbucket, or Azure.
Fluid Attacks must be granted access to the Git repository with read and clone privileges.
If the repository is hosted on a private network, not in the cloud, the organization must supply Fluid Attacks with the necessary permissions for the connection.
The application must be in a continuous development lifecycle (i.e., the lead's development team must regularly make changes during the PoV).
The associated environment must be accessible 24/7 for continuous testing.
Expected
The application should have over 200 thousand lines of code (excluding third-party libraries).
The organization should have a fully configured CI pipeline.
From the previous month and throughout the whole POV, the organization's development team should have at least five (5) developers.
The organization's project manager should be able to attend a weekly 30-minute follow-up meeting with Fluid Attacks' engagement manager.
The organization's team should remediate at least 30% of the vulnerabilities reported during the first half of the PoV.
By the end of the PoV
The organization must comply with the following:
Provide feedback on the experience in a satisfaction survey or brief conversation.
Review the platform on Gartner Peer Insights.
Reference the experience to other organizations.
Create a short video or podcast testimonial about the PoV.
Workflow
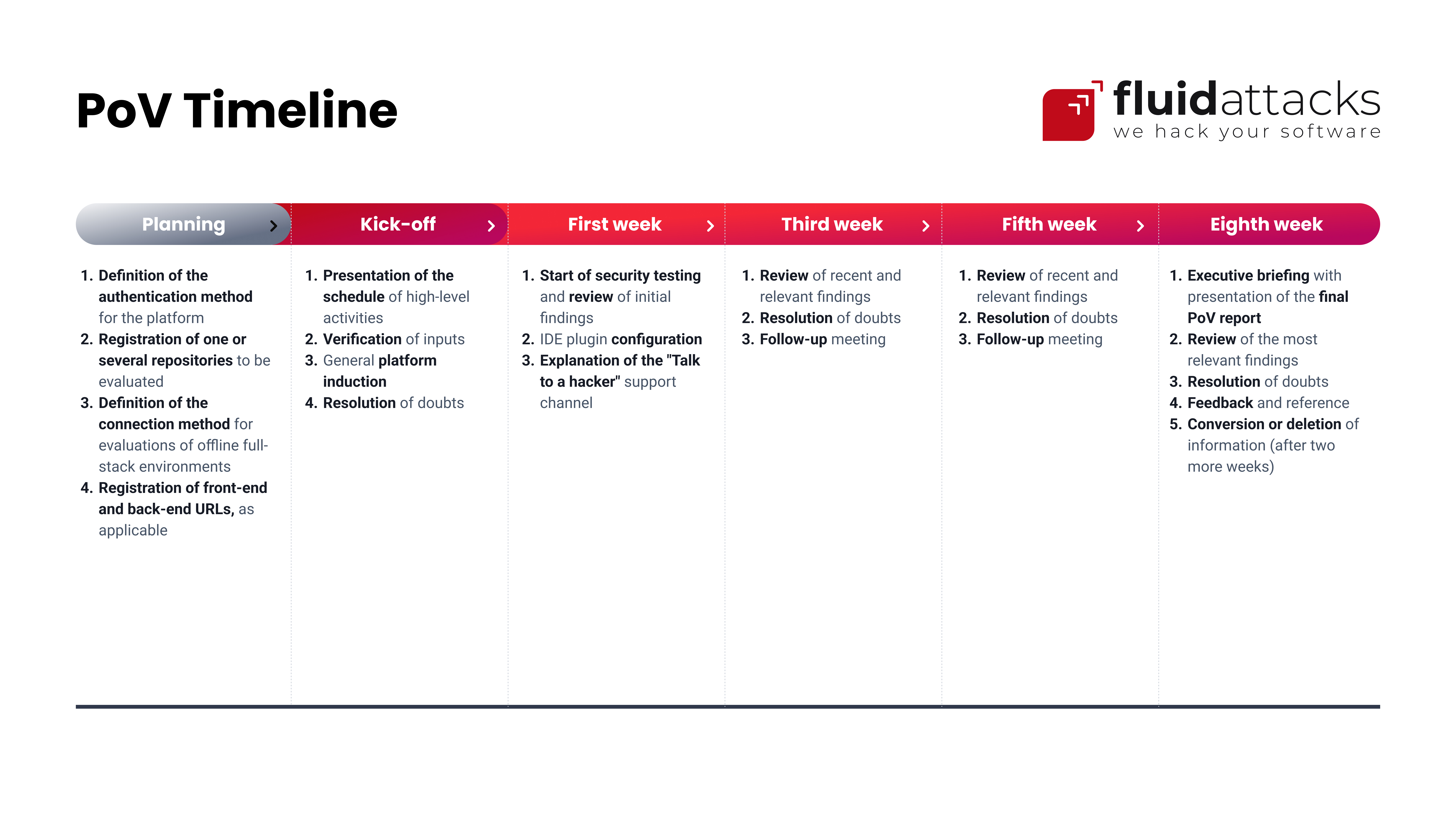
The following are activities that are carried out during the time agreed with the organization for the Proof of Value, usually sixty (60) days.
Planning
- Definition of the target of evaluation (ToE): The organization provides information on the names and types of applications to be assessed and the associated repositories, branches and environments and generates the credentials for each application.
- Identification of responsible parties: The organization determines who in their team manages the projects, remediates vulnerabilities and controls software deployment.
- Definition of the type of connection: The organization, with the help of the Fluid Attacks engagement manager, determines whether the connection is to the cloud or a private network and whether access to the repositories is via OAuth, SSH, or HTTPS.
- Scheduling of a kick-off meeting.
Guidance
- Kick-off meeting: The engagement manager introduces organization team members to the Fluid Attacks vulnerability management platform. They then establish a connection to applications and access to repositories. Finally, they schedule onboarding and follow-up meetings.
- Onboarding meetings: Fluid Attacks' Customer Success meets with members of the organization's team whenever necessary to instruct them on using the platform, its plugins, other integrations, and the CI Gate, among other things.
- Follow-up meetings: The engagement manager from Fluid Attacks and the project manager and other stakeholders from the customer's side meet weekly to review and evaluate their experiences and outcomes in the PoV.
Implementation
- Automated security testing: Fluid Attacks' scanners continuously look for vulnerabilities in the ToE during different phases of its development lifecycle through SAST, DAST, SCA, and AI SAST techniques.
- Manual security testing: After AI assistance in prioritizing potentially vulnerable files, Fluid Attacks' team of pentesters continuously searches for security issues in the ToE using methods such as manual pentesting, secure code review and reverse engineering.
- Vulnerability management: Based on the reports delivered on the platform and, if needed, explanatory sessions with Fluid Attacks experts, the organization's team assigns and works out the remediation of vulnerabilities. For the latter, they may also use generative AI on the platform or VS Code plugin to get fix suggestions. In addition, they request reattacks whenever they want to verify that the remediations were successful and establish policies to break the build with the CI Gate whenever there are unacceptable vulnerabilities in their software before going into production.
Completion
- Executive briefing: For an hour or so, stakeholders from the customer side (e.g., CTO, CISO, technical security and DevOps leaders) and Fluid Attacks (e.g., engagement manager and account executive) meet to present and discuss the final results of the PoV.
- Feedback and referral: In compliance with the above, the organization's team provides feedback on their experience with Fluid Attacks' solution through Gartner Peer Insights and invites other companies to participate in a PoV.
- Conversion: Once the PoV is complete, the organization determines and communicates whether it wants to become Fluid Attacks’ customer.
After the PoV ends