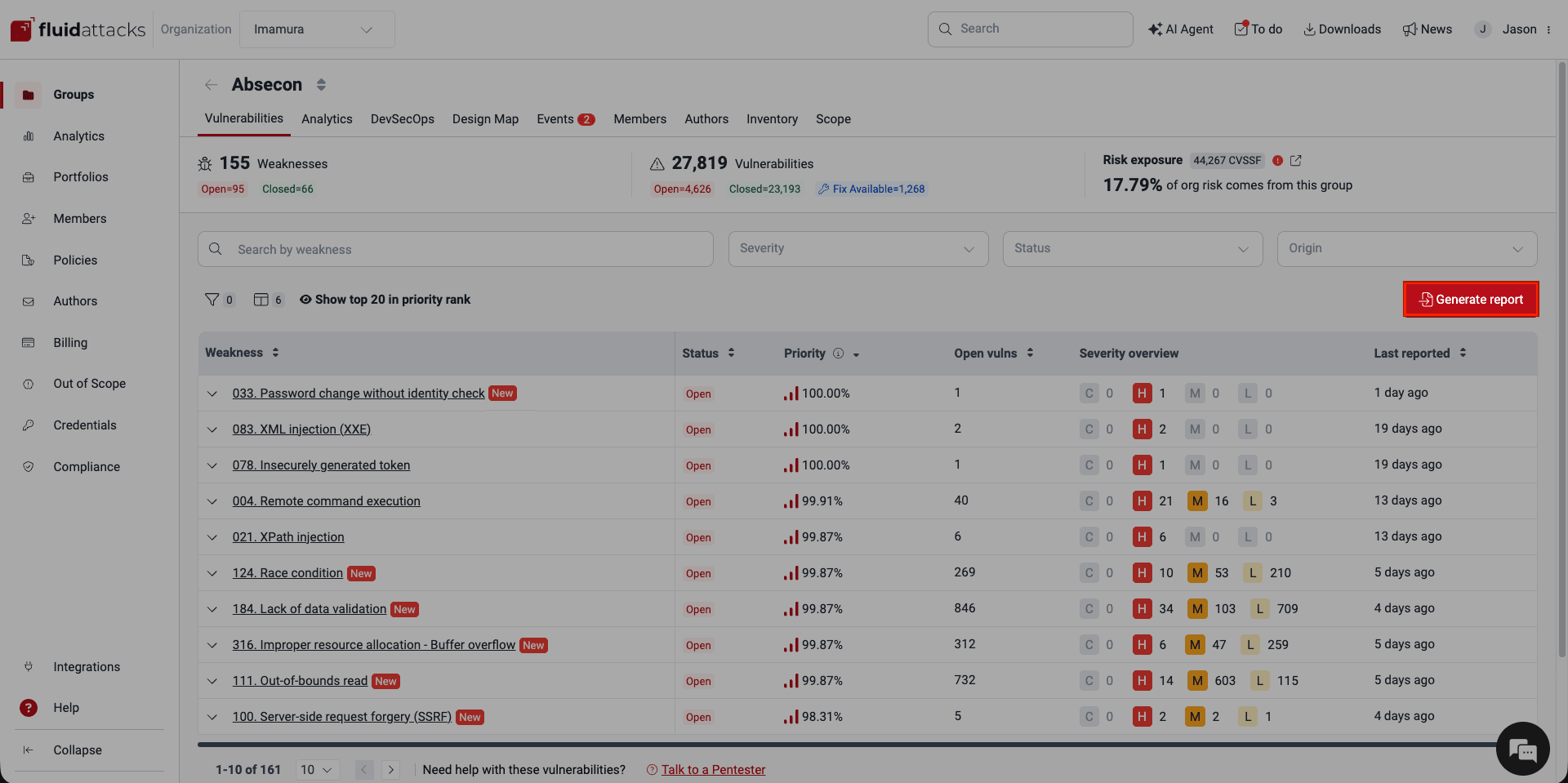
Download a report of detected vulnerabilities
 Since April 4, 2025, reports use CVSS v4.0 exclusively.
Since April 4, 2025, reports use CVSS v4.0 exclusively.Download a group's vulnerability report

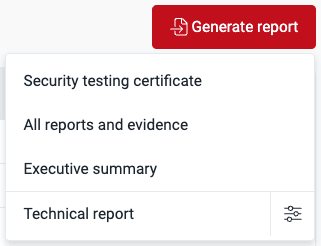
The following report options are available, offering varying levels of detail about reported vulnerabilities within a specific group:
-
Security testing certificate: Available to Group Managers only, it is a document that certifies that your system is undergoing security testing by Fluid Attacks (requires completion of the information section). Among the certificate contents is the number of reported vulnerabilities categorized by their CVSS qualitative ratings, how many of them have been remediated, how many accepted, and the number of reported risk exposure units.
-
All reports and evidence: It is a ZIP folder containing vulnerability reports (i.e., executive summary and technical report), a file listing compromised records, and pictures and videos that constitute vulnerability evidence.
-
Executive summary: It is a summarized PDF report of all group vulnerabilities, tailored for management review.
-
Technical report: It is a customizable, detailed XLSX report of group vulnerabilities, ideal for technical analysis.
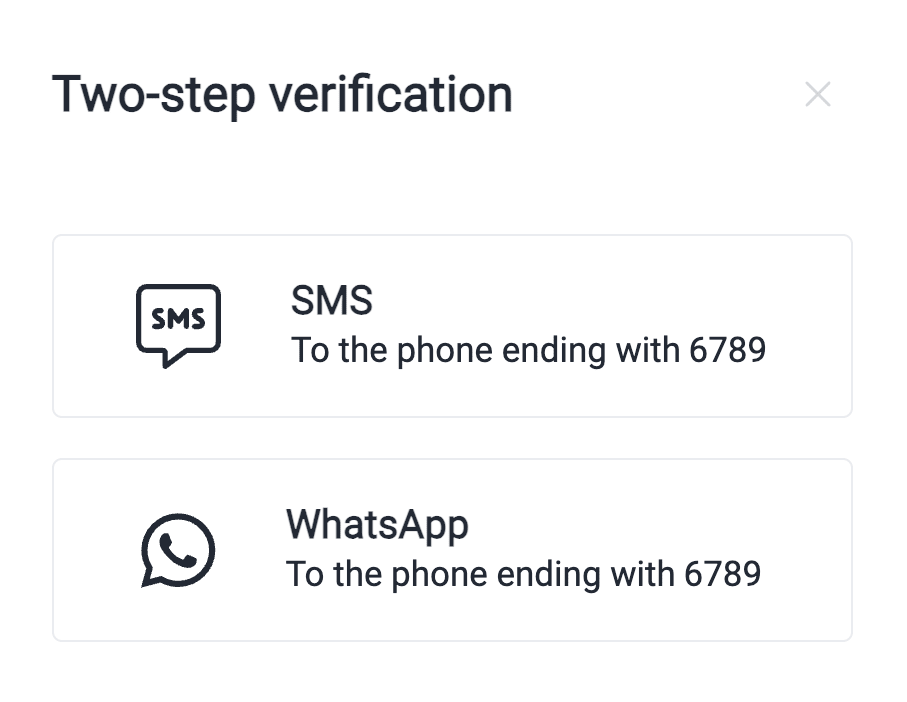
Window for choosing the verification code delivery method
 Note: Please note that there may be restrictions on sending the OTP code by SMS in Canada.
Note: Please note that there may be restrictions on sending the OTP code by SMS in Canada.Definitions of the technical report columns
- #: Row number
- Weakness: The category that best describes the vulnerability
- Weakness ID: Unique identifier for the weakness
- Vulnerability ID: Unique identifier for the vulnerability
- Package: Name of the package that may be unsafe
- Vulnerable version: Package version in use
- CVE: Common Vulnerabilities and Exposures (CVE) identifier
- Location: Specific path where the vulnerability is present
- Stream: Steps to reach the vulnerability in dynamic environments
- Specific: Precise line, field or port that presents the vulnerability
- Description: Detailed description of the vulnerability
- Status: Current Status of the vulnerability, where 'VULNERABLE' means it is present, whereas 'SAFE' means it has been remediated
- Severity: Severity score based on the Common Vulnerability Scoring System (CVSS) v4.0
- Related Requirements: Likely unfulfilled security requirements
- Impact: What an attacker can achieve exploiting the vulnerability
- Threat: The attack vector an attacker has to follow and the privileges they require to exploit the vulnerability
- Recommendation: Suggested actions to fix the vulnerability
- External BTS: URL of the issue in your bug tracking system (BTS) related to this vulnerability
- Compromised Attributes: Data or information compromised due to the vulnerability (e.g., usernames, IDs, passwords)
- Tags: User-defined tags to categorize or identify the vulnerability
- Business Criticality: Priority score; a numerical value representing the organization-defined importance of this security issue
- Technique: Security testing technique used to detect the vulnerability
- Report Date: Date when the vulnerability was confirmed
- Closing Date: Date when the vulnerability was fixed (if applicable)
- Age in Days: Number of days since the vulnerability was confirmed
- First Treatment: Initial treatment applied to the vulnerability
- First Treatment Date: Date when the first treatment was applied
- First Treatment Justification: Justification given for applying the first treatment
- First Treatment Expiration Date: Expiration date for the first treatment (if Temporarily accepted)
- First Assignee: Email of the first person who was assigned to remediate the vulnerability
- Current Treatment: Current treatment applied to the vulnerability
- Current Treatment Date: Date when the current treatment was applied
- Current Treatment Justification: Justification given for applying the current treatment
- Current Treatment Expiration Date: Expiration date for the current treatment (if Temporarily accepted)
- Current Assignee: Email of the person who is currently assigned to remediate the vulnerability
- Pending Reattack: Whether the reattack (i.e., verification of the effectiveness of your fix) is currently Requested (Yes or No)
- # Requested Reattacks: The total number of times that a reattack has been requested
- Remediation Effectiveness: The percentage representing one positive reattack outcome (confirming the vulnerability was fixed) out of all the reattacks carried out
- Last Requested Reattack: Date of the most recent reattack request
- Last Reattack Requester: Email of the person who requested the most recent reattack
- CVSSv4.0 Vector String: The values used to derive the score represented textually
- Attack Vector: How remote the attacker can be in order to exploit the vulnerable system
- Attack Complexity: How easy it is for the attacker to exploit the vulnerability
- Privileges Required: Level of privileges an attacker needs
- User Interaction: Whether user interaction is required for exploitation
- Vulnerable Confidentiality Impact: The impact of exploitation on information confidentiality
- Vulnerable Integrity Impact: The impact of exploitation on information integrity
- Vulnerable Availability Impact: The impact of exploitation on information availability
- Exploit Maturity: Probability of exploitation given the current state of techniques for it, exploit code availability, and actual exploitation "in the wild"
- Subsequent Confidentiality Impact: Exploitation impact on information confidentiality in one or more systems other than the vulnerable system
- Subsequent Integrity Impact: Exploitation impact on information integrity in one or more systems other than the vulnerable system
- Subsequent Availability Impact: Exploitation impact on information availability in one or more systems other than the vulnerable system
- CWE IDs: Common Weakness Enumeration (CWE) identifier
- Commit Hash: ID of the commit that created the vulnerability
- Root Nickname: User-defined nickname of the root where the vulnerability was found
- Root Branch: The specific branch that is tested and where the vulnerability was found
- Severity Level: CVSS qualitative rating
- EPSS: Exploit Prediction Scoring System; a value ranging from 0 to 100 that corresponds to the likelihood that the vulnerability will be exploited in the wild. This value is retrieved from the FIRST database by the Fluid Attacks scanner's SCA module.

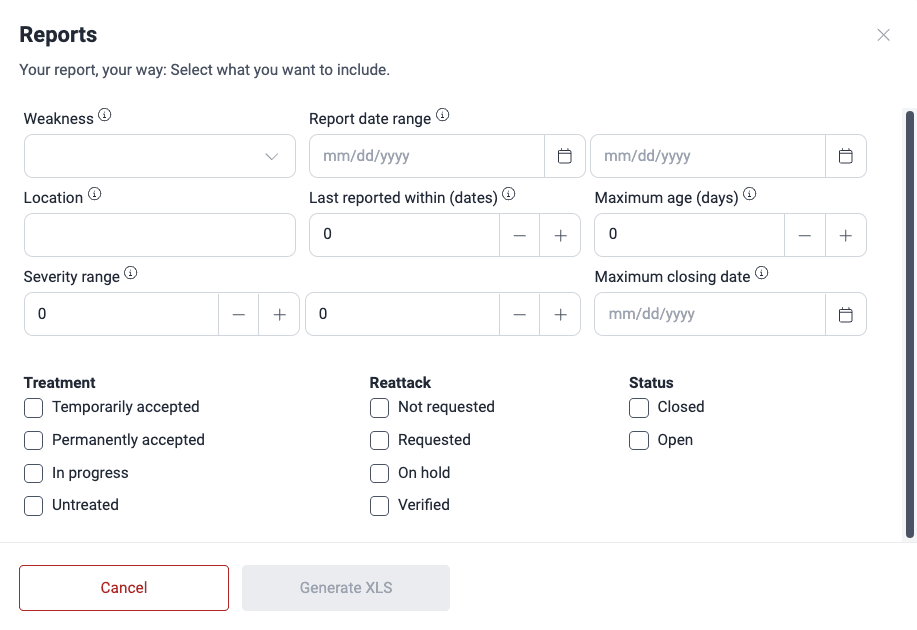
Filter the technical report

- In the Vulnerabilities section, click on Generate report.
- Click on the filters button on the right side of the Technical Report option.
- A pop-up window appears, presenting you with the filter options.
- Weakness: The category that best describes the vulnerability
- Report date range: The dates within which vulnerabilities were reported
- Location: Specific path where the vulnerabilities are present
- Last reported within (dates): Include only types whose last report was more recent than the specified value (given in days)
- Maximum age (days): Include only types whose first report was more recent than the specified value (given in days)
- Severity range: Minimum and maximum CVSS severity scores
- Maximum closing date: Include only vulnerabilities remediated on a date more recent than the one specified
- Treatment: Currently applied vulnerability treatment
- Reattack: Current reattack status
- Status: Whether the vulnerability is currently present ('Open') or not ('Closed')
- Customize your report as needed and click on the Generate XLS button.
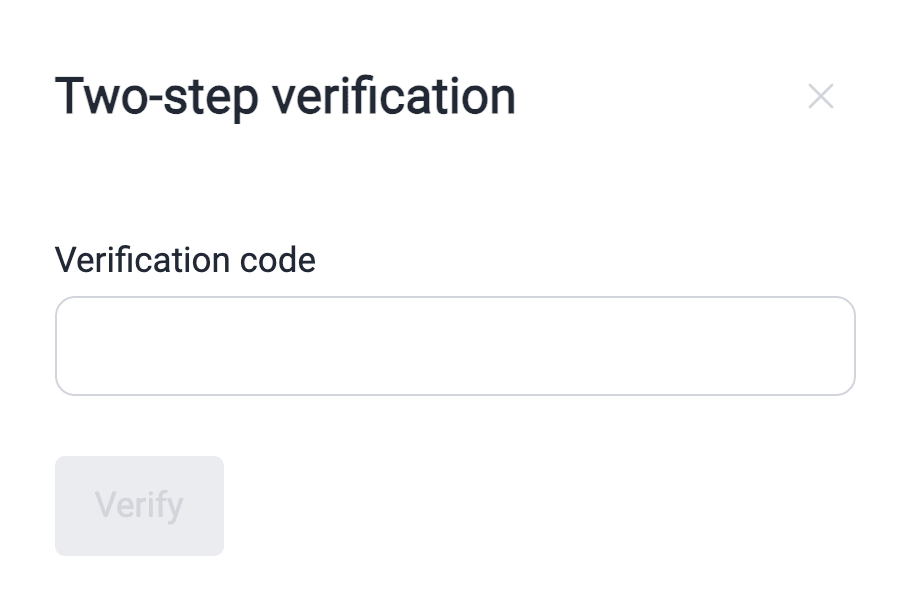
- Choose where you want to receive the code for two-step verification (SMS app or WhatsApp).
- Enter the code you received and click on Verify.
- After successful verification, wait for the email informing the filtered report in XLSX format is available and download it with the platform's Downloads function.


Download a report of all vulnerabilities in the organization

To download a comma-separated values (CSV) file containing all of your organization's vulnerabilities (including their vulnerability statuses), follow these steps:
- Go to the Analytics section at the organization level (i.e., the one you access through the collapsible menu).
- Click the Vulnerabilities button on the top right corner of the section.
- Choose where you want to receive the two-step verification code (SMS app or WhatsApp).
- Enter the verification code you received and click Verify. Your browser then downloads a compressed file containing the CVS file. This file is available on the platform for seven days after generation.
 You can also obtain this information via API using the
You can also obtain this information via API using the vulnerabilitiesUrl method. Find the details on how to make API requests to the platform in the Fluid Attacks API documentation.