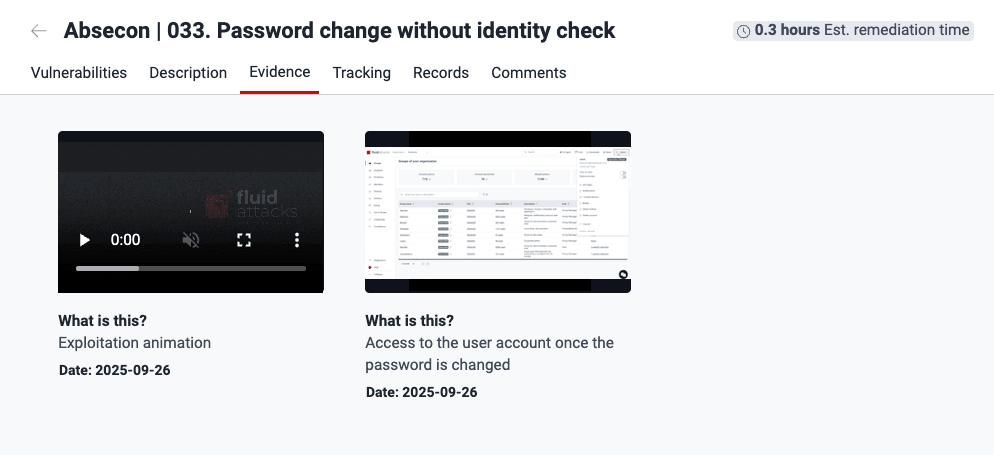
Examine the evidence of exploitability
The Evidence section on Fluid Attacks' platform provides supporting proof of the existence of a type of vulnerability in your software and, if applicable, is where the team of pentesters shares how they exploit the security issue in question. To view evidence, follow these steps:
- Enter the group where the type of vulnerability was reported.
- In Vulnerabilities, click on the name of the weakness.
- Switch to the Evidence tab.
 Click on a resource to enlarge it, and then you can download it.
Click on a resource to enlarge it, and then you can download it.Evidence is presented in the form of pictures (with the .png and .jpg extensions) and videos (with the .webm extension), to convince you of the vulnerability's presence in your system and, if applicable, actual threat to information in it.
These are important points to consider regarding evidence:

Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.