Verify fixes with reattacks
Request a reattack
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager Note: Before requesting a reattack, make sure you have synced the fixed software version to the platform.
Note: Before requesting a reattack, make sure you have synced the fixed software version to the platform.Go to the intended group's Vulnerabilities section and click on the weakness name.
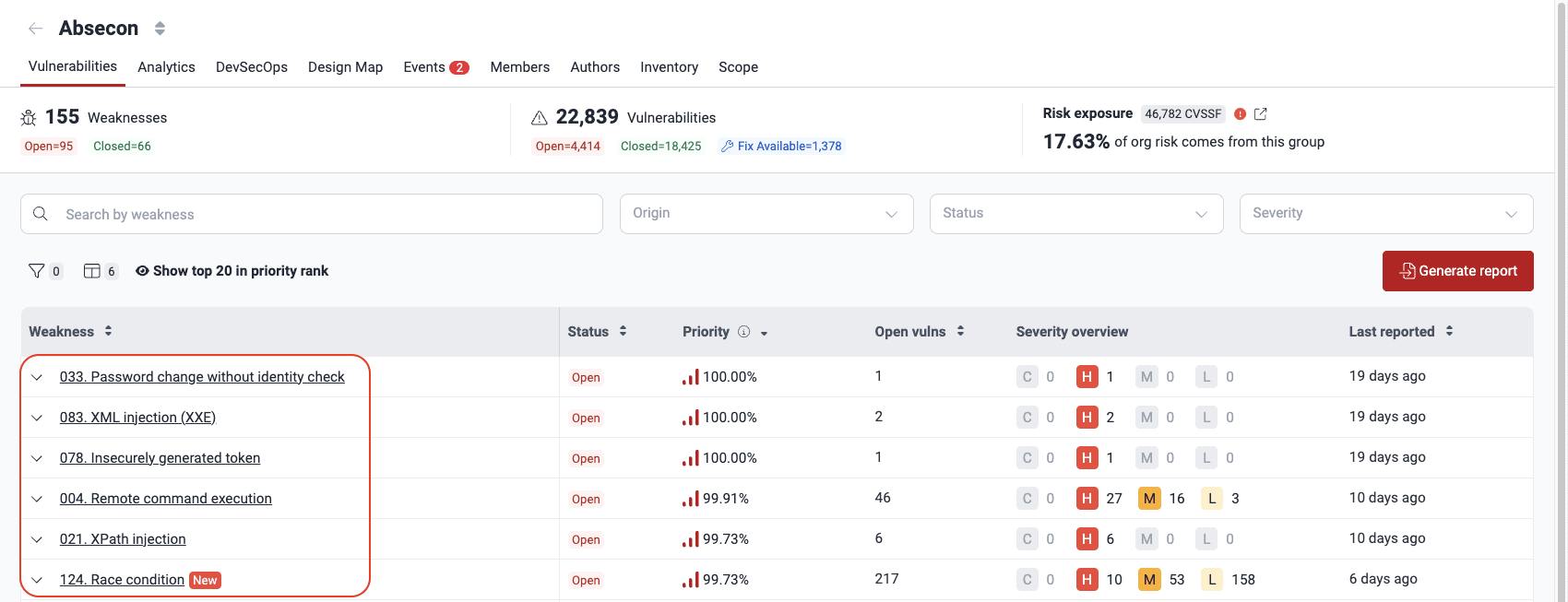
Select the vulnerability to be verified by the reattack. Only entries with the 'Vulnerable' status and whose reattack status is neither 'Requested' nor 'On hold' are eligible. Then click on the Reattack button.
-
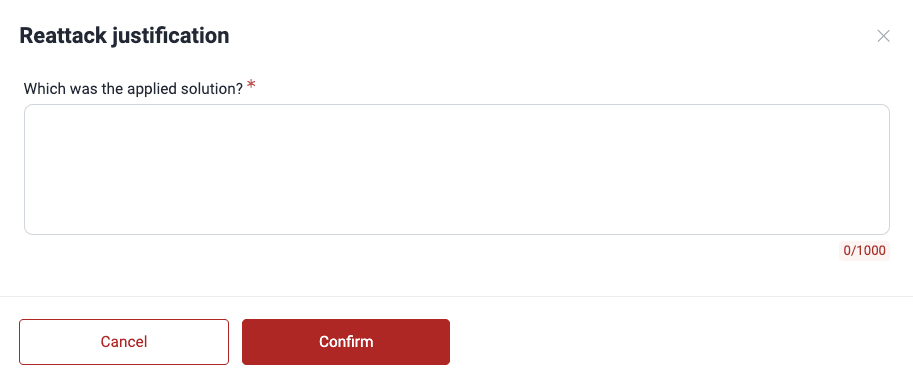
In the pop-up window, provide a detailed description (minimum 10 characters) of the fix you implemented to address the vulnerability (if applies).
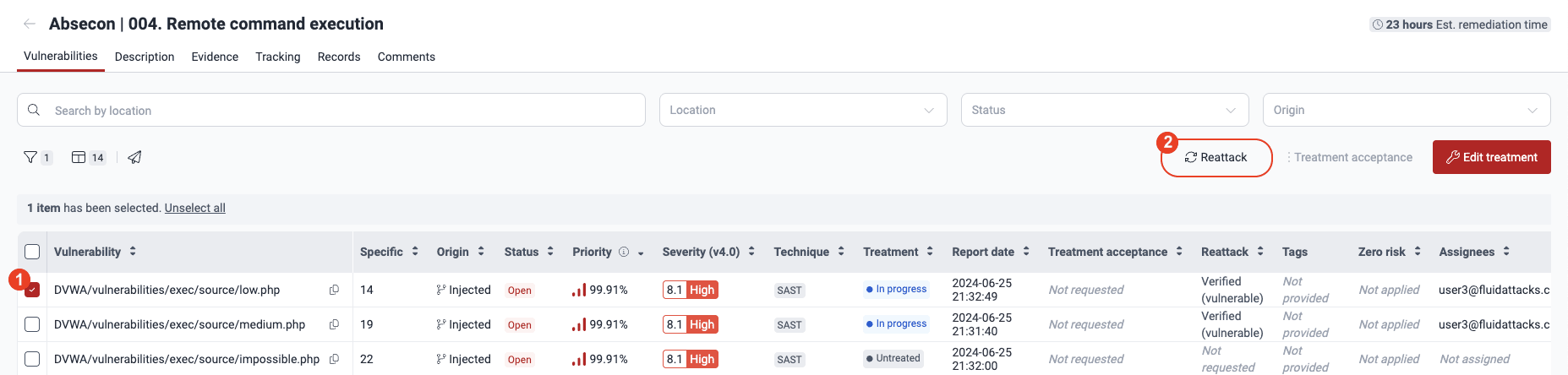
Click Confirm. The Reattack column for that vulnerability then displays the value 'Requested'.


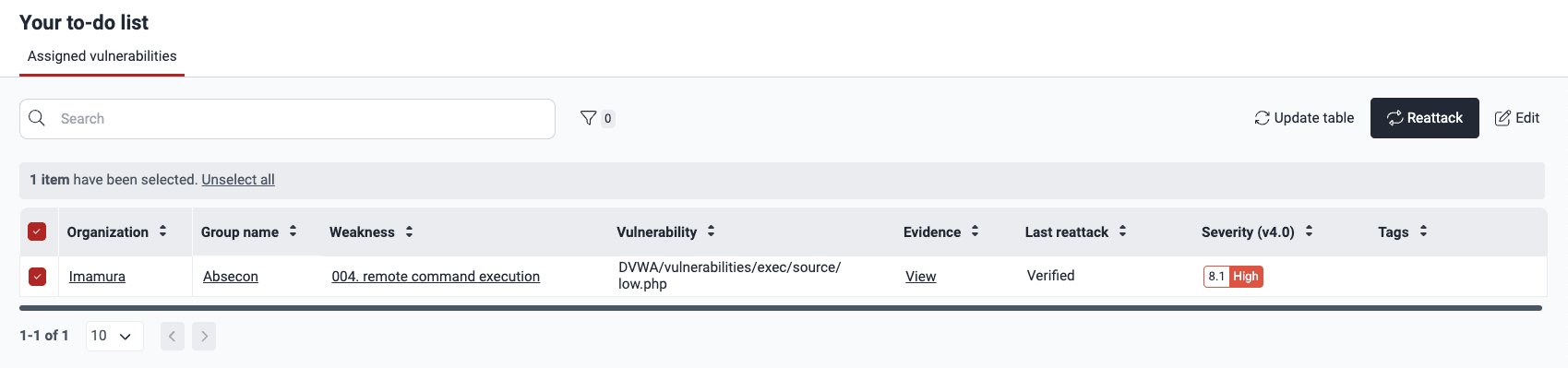
To request reattacks from the To do section, follow these steps:
- Go to the To do section.
- In Assigned vulnerabilities, select the vulnerability by its check box and click on Reattack.
- Provide a justification (minimum 10 characters) in the pop-up window (if applies) and click Confirm.

Reattack outcomes
On the platform, there are two possible reattack outcomes which are informed in the Reattack column of the Vulnerabilities table.
- Verified (vulnerable): The vulnerability is still exploitable. Fluid Attacks' tool or pentesters provide evidence of the exploit, accessible in the Evidence section. You should attempt remediation again and then request another reattack.
- Verified (safe): The vulnerability has been successfully remediated.
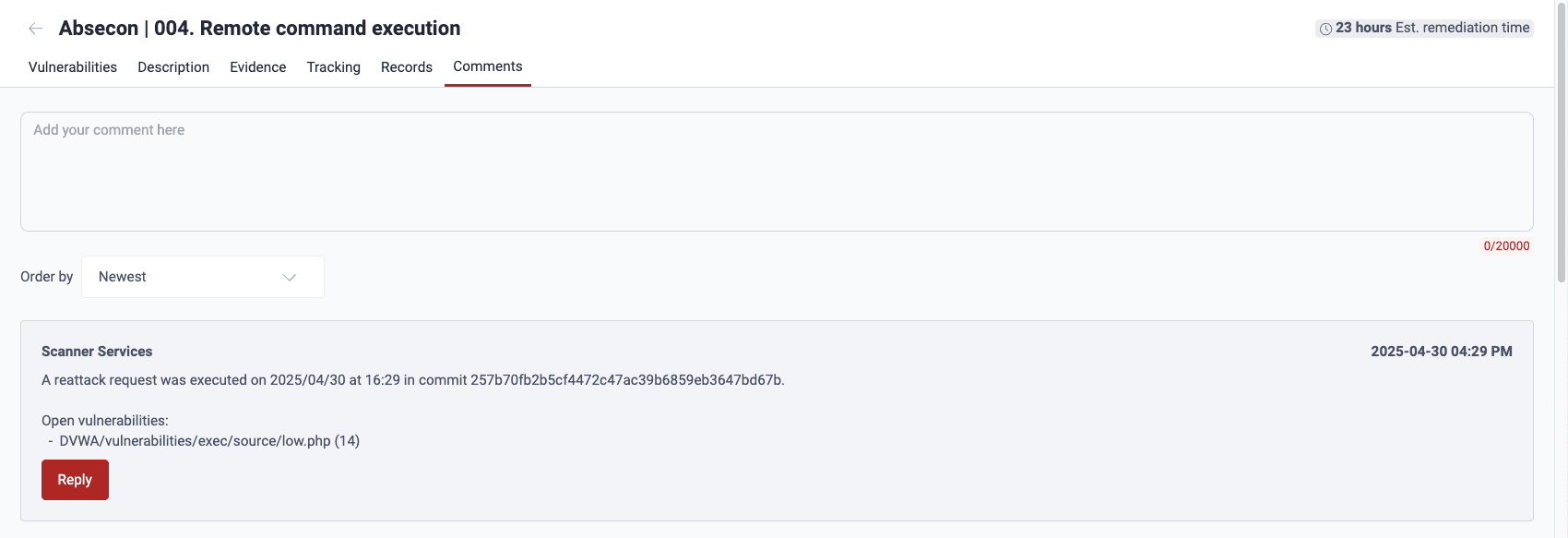
Reattack outcomes are recorded in the type of vulnerability's Tracking and Comments sections.
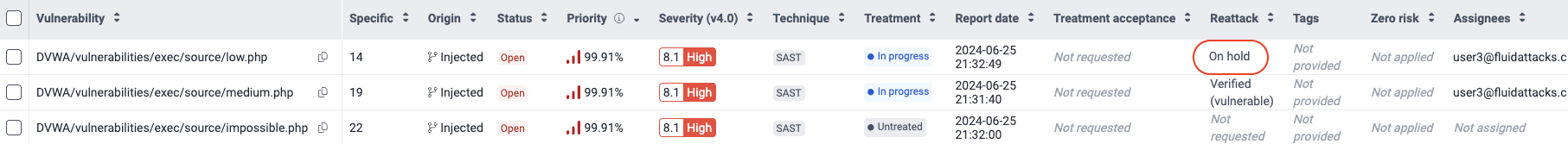
Reattacks on hold
Reattacks might be temporarily delayed due to situations from your side, which Fluid Attacks calls "events." To learn more about them, read Resolve events impeding tests. Delayed reattacks are shown in the Vulnerabilities table with the value 'On hold'.
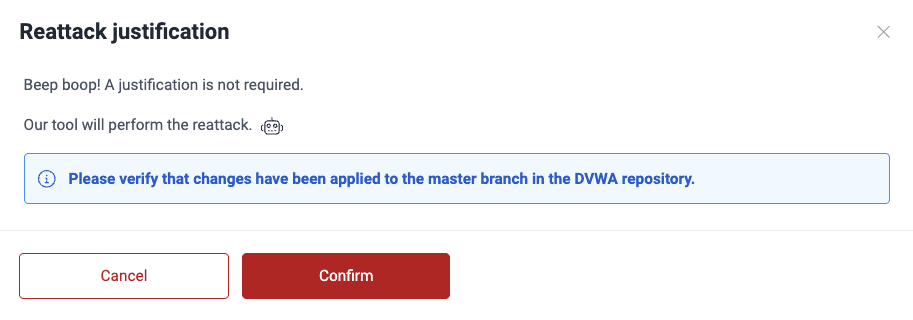
Reattacks for vulnerabilities detected by the automated tool
- No detailed justification is needed in your request as the tool does not take it into account. You are shown the following message instead.
- If you suspect a false positive or determine the finding poses no risk due to other security measures, contact Fluid Attacks or request the zero risk treatment, respectively, instead of a reattack.
- The posts in Comments sections are simple messages mentioning vulnerabilities present and remediated resulting from the reattack.
- If you have trouble remedying the vulnerability, consult the vulnerability and fixes documentation for code examples or use the Fluid Attacks features that leverage generative artificial intelligence to have an idea of how to proceed.
Reattack a permanently accepted vulnerability
 Role required: User, Vulnerability Manager or User Manager
Role required: User, Vulnerability Manager or User Manager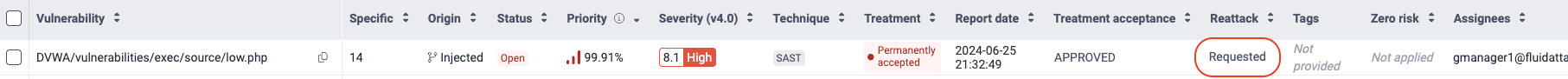
Error when requesting reattacks
Add new changes to your repository before requesting a new reattack
- the latest cloned version (last commit) of the repository associated with the vulnerability you are attempting to reattack is more than 1 day old,
- the vulnerability is still present in that last commit (or even in a previous commit).
These are the recommended steps when encountering this error:
-
Check the current version of the repository (in your remote version control system or remote container where the repository is hosted) and ensure the latest commit is recent and includes the fix.
-
Update the branch under evaluation (i.e., the one registered in the Scope section) to include the current version of the repository.
-
Return to the platform and request the reattack again.
-
If necessary, manually update the repository in Scope and request the reattack once its Status is OK.

- Repeat these steps for each repository associated with multiple vulnerabilities you wish to reattack.
- Contact help@fluidattacks.com if you face issues with the above steps or if you believe a repository update is not required.
You had already requested that reattack
You selected a vulnerability already marked as Safe
You selected a vulnerability whose reattack is On hold
Your current subscription does not include reattacks for the selected vulnerability
 Free trial
Free trial