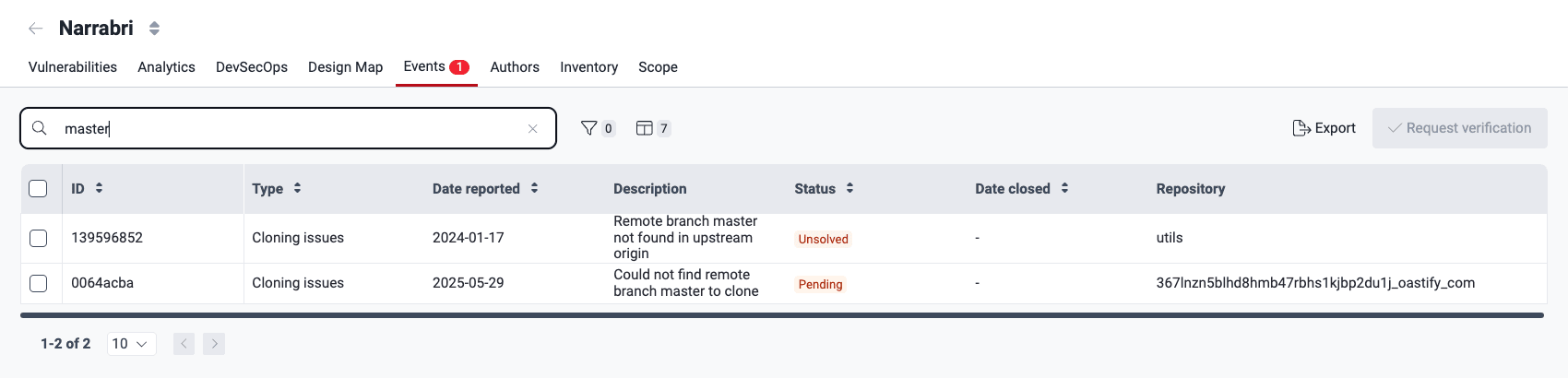
Resolve events impeding tests
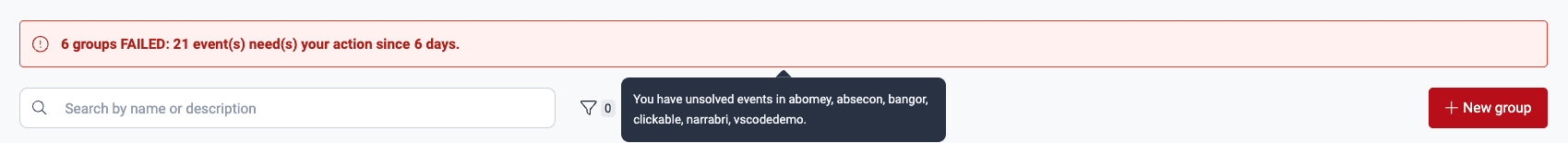
Whenever you have events to solve, you are told so in a red banner in the Groups section. The banner is shown for a few seconds only and informs the number of affected groups, unsolved events and days passed since the oldest of them was reported.

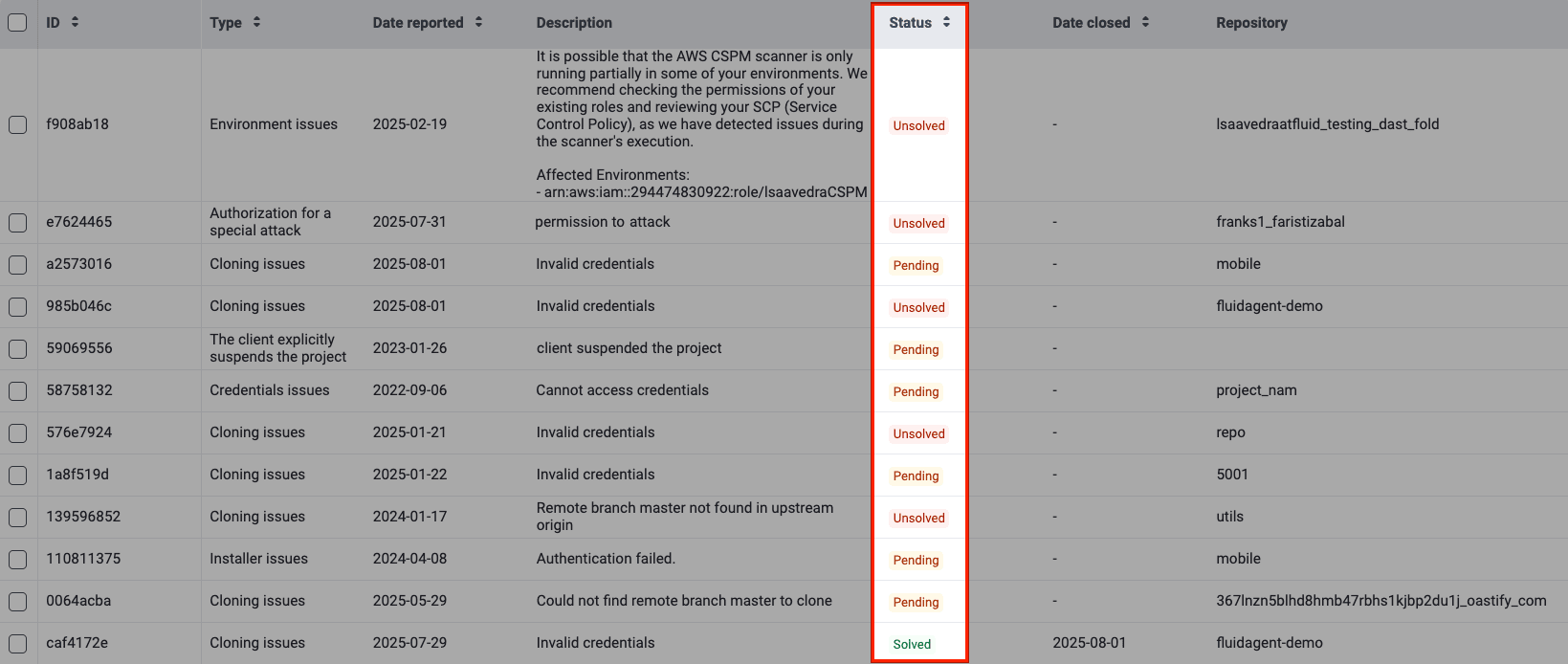
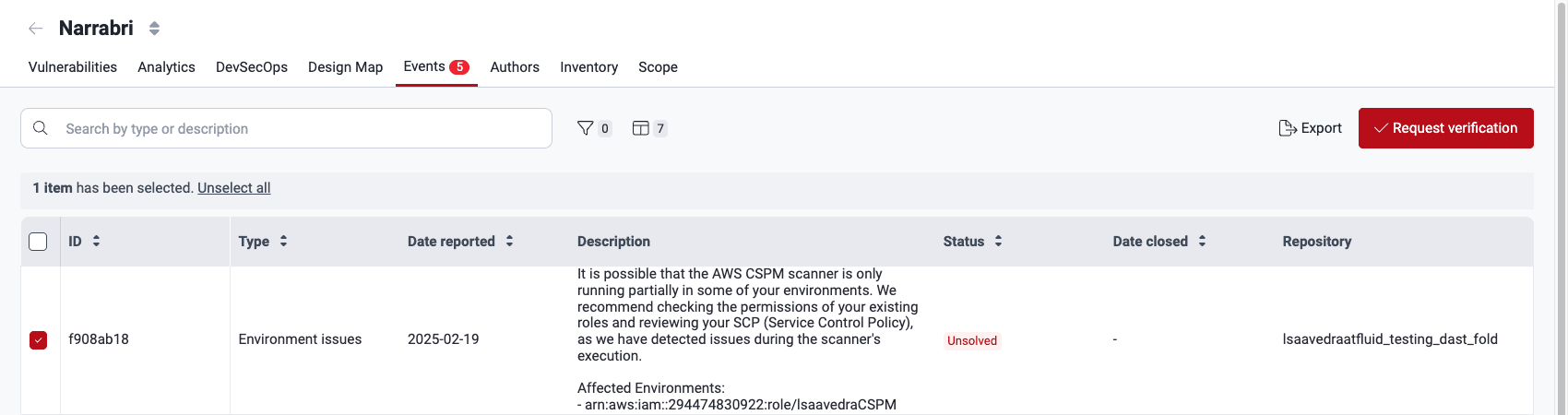
Know your events table

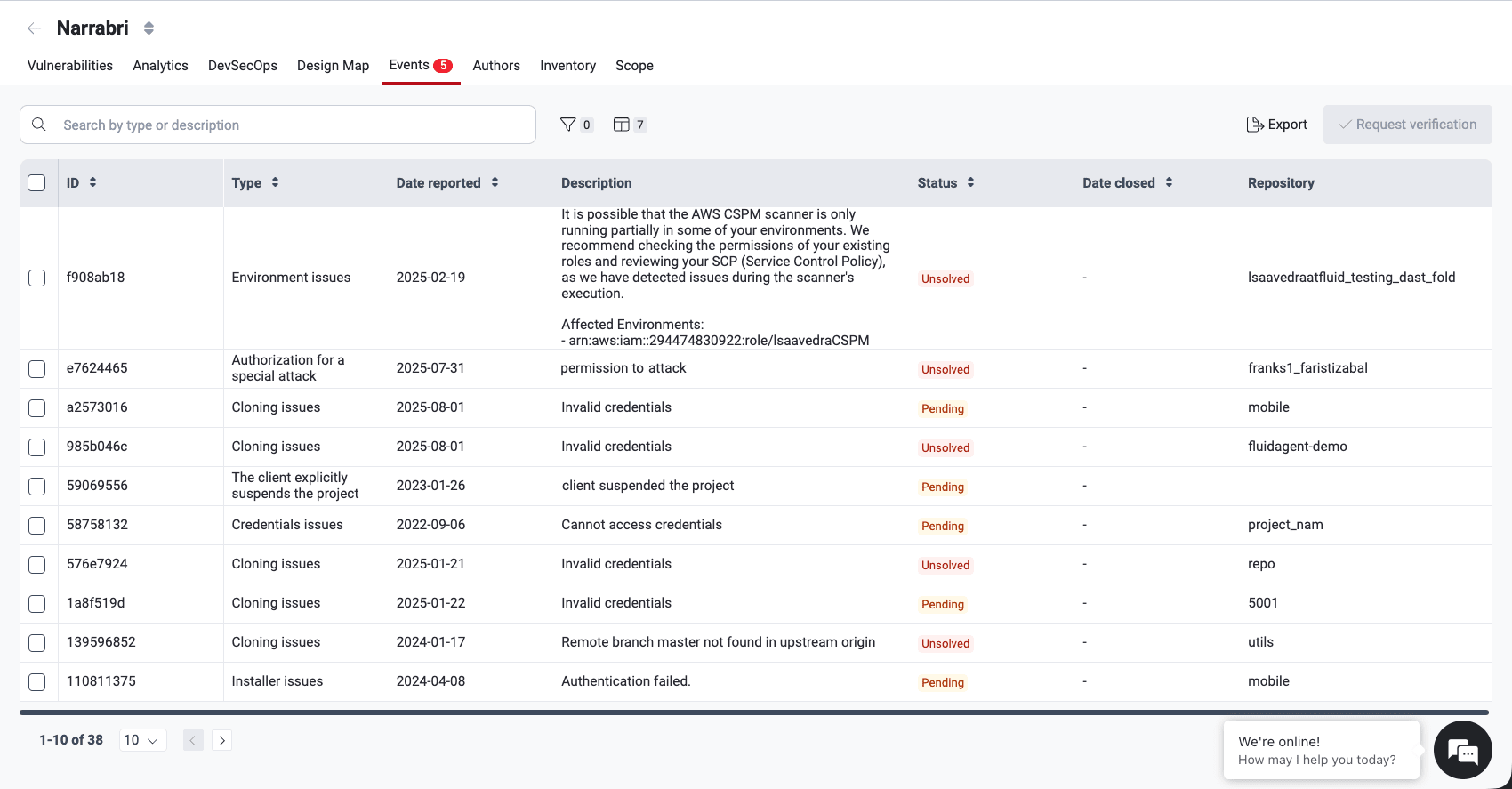
- ID: A unique identifier for the event
- Type: The category the issue falls under (read below the descriptions of event types)
- Date reported: The date the event was initially reported
- Description: A detailed explanation of the issue impeding the security assessment
- Status: The current state of the event, which can be "Solved," "Pending" or "Unsolved" (read below about these event status categories)
- Date closed: The date and time the event was resolved (if applicable)
- Repository: The nickname of the affected repo
Types of events
Fluid Attacks categorizes events as follows:
- Authorization for a special attack: A specific test requires explicit customer permission due to potential impact on availability or integrity.
- Cloning issues: There are problems with cloning the repository.
- Credentials issues: Access to the assets to test is prevented due to missing or invalid credentials.
- Data update required: User credentials or data need to be reset or updated to consume a service.
- Environment issues: There are issues with the testing environment, such as unavailability or functional problems.
- Installer issues: Problems arise when installing or running the application on mobile or desktop.
- Missing supplies: Necessary resources other than credentials are lacking.
- Network access issues: Loss of internet connectivity on the network port.
- Other: The issue does not fall into the predefined categories.
- Remote access issues: Problems with connection methods, hindering access to the environment.
- Request user modification/workflow update: Modifications to test users (e.g., a role change or unblocking) or workflow conditions are needed to resume testing.
- The client cancels a project milestone: The client cancels a predefined phase or deliverable within the project.
- The client explicitly suspends the project: The client temporarily suspends the project or excludes specific parts of the Target of Evaluation (ToE).
- ToE different than agreed upon: The client provides a ToE that is not covered by the Continuous Hacking plan.
- VPN issues: There are failures in the VPN connection.

Event status
In the platform's Events section, you find out about the state of an event in the Status column.
- Unsolved: The initial state upon reporting, requiring your action
- Pending: After you solve the event, and upon your request, the event awaits verification by Fluid Attacks
- Solved: The issue is successfully resolved and verified
View event details

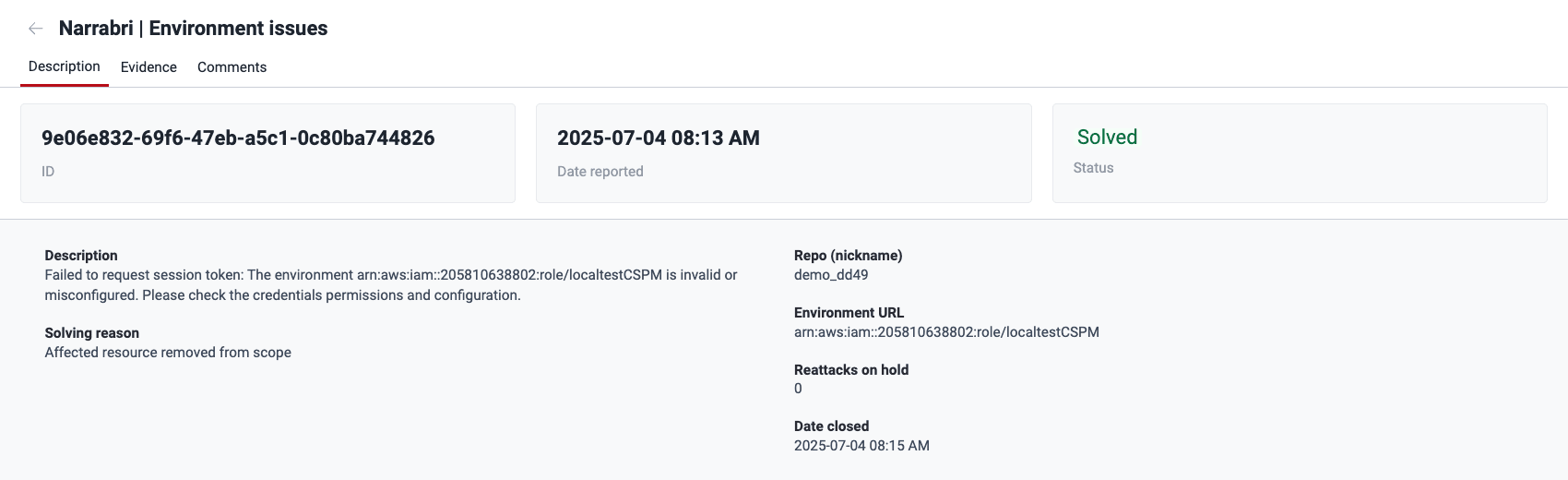
Description
In an event's Description section, you find the following information:
- Description: What the problem is (or was) specifically
- Solving reason: Why the problem is considered solved (if applicable)
- Repo (nickname): The nickname of the affected repository
- Reattacks on hold: The number of reattacks that have not been possible due to the event
- Date closed: The date Fluid Attacks verified the problem as solved (if applicable)
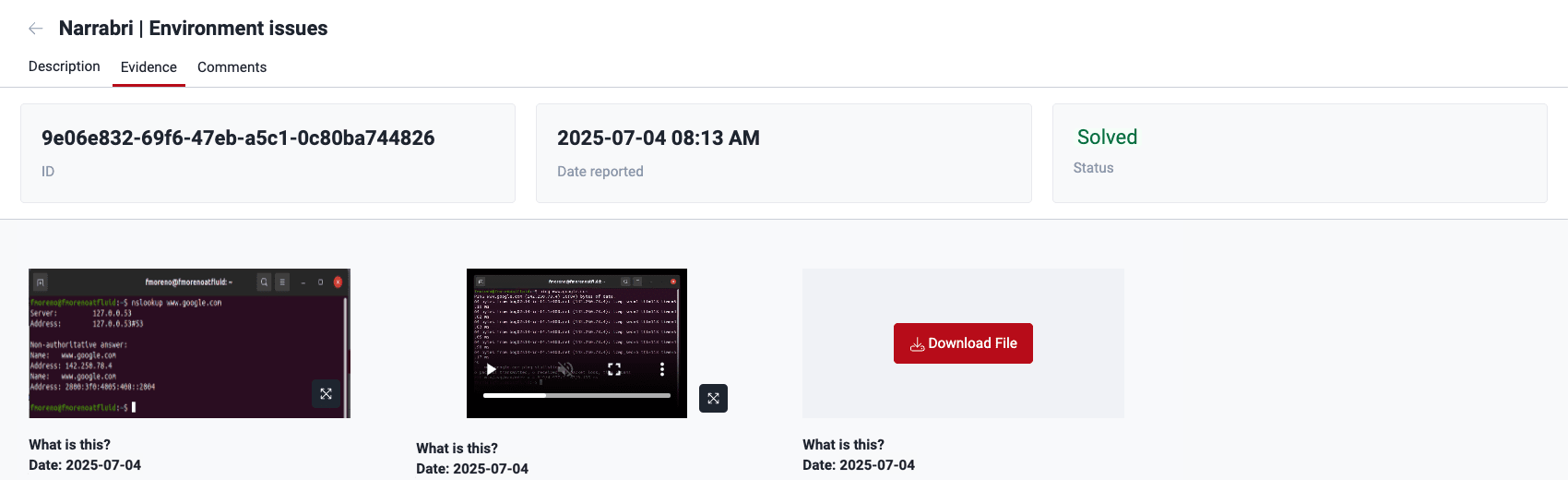
Evidence
In the event's Evidence section, you find screenshots or videos as proof of the issue that is impeding tests. You can click on a piece of evidence to enlarge it and access the option to download it. If there are several items, you can click on Download File to download them in a ZIP folder.
Comments

 Note: Comments is available in view mode for groups subscribed to the Essential plan. This allows members to see comments but not post.
Note: Comments is available in view mode for groups subscribed to the Essential plan. This allows members to see comments but not post.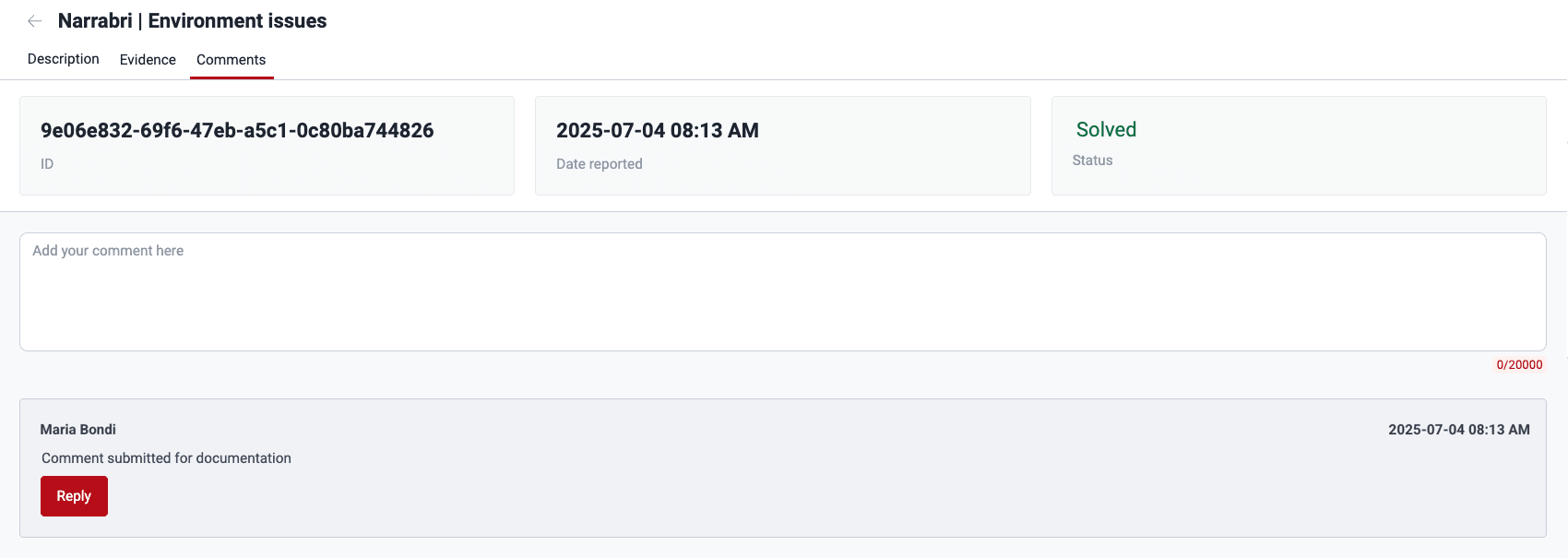
Request a verification that the event is solved

- Access the group's Events section.
- Select the checkbox next to the event you solved.
- Click on the Request verification button.
- Provide a description (at least 10 characters) of the implemented solution in the pop-up window.
- Click Confirm.

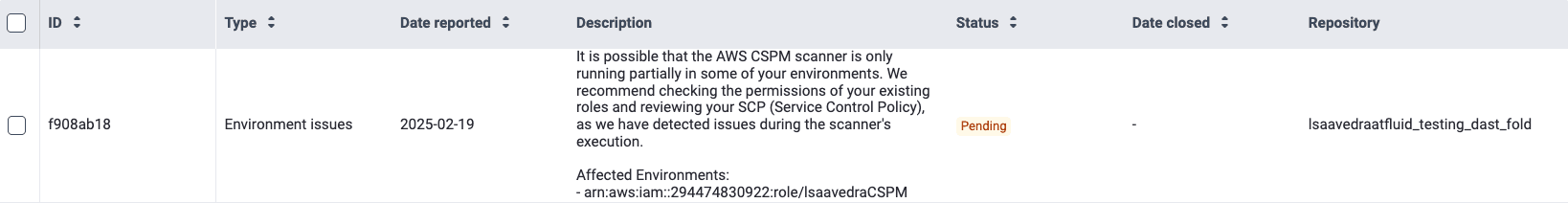
If Fluid Attacks decides that your provided solution was not effective, you receive a notification telling you so. The outcome is also made available as a comment in the Comments section. The process of verification is to be repeated as described above until the event is solved.
Filter the events table

 Find filters in Events
Find filters in Events Apply filter
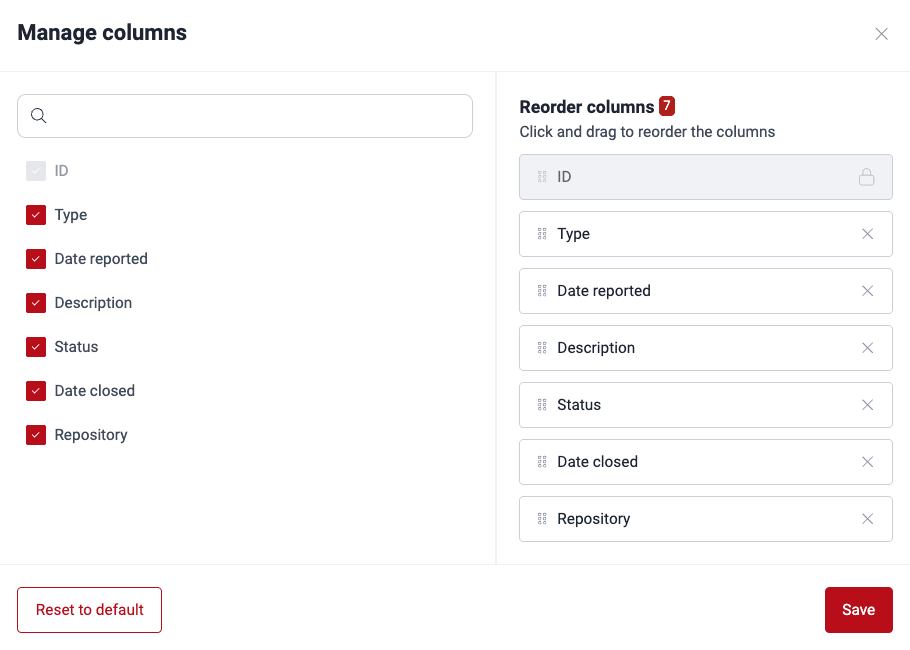
Apply filterShow or hide columns of the events table

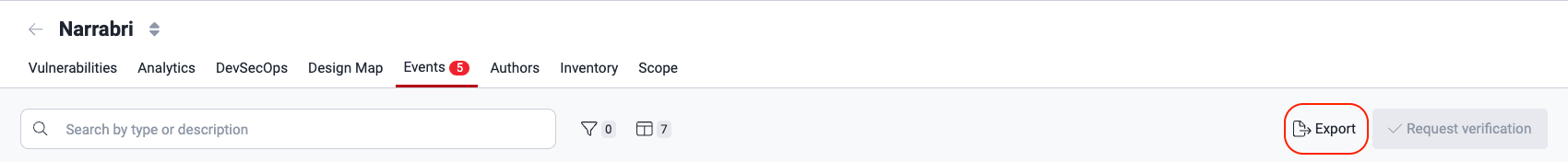
Export the events table


Search the events table
Type in the search box to show only the rows of the table where the content matches your search.