Know your Groups section
Covered authors and repos
A header in the Groups section gives you information on the total covered and missed contributing authors and repositories across the organization's groups.
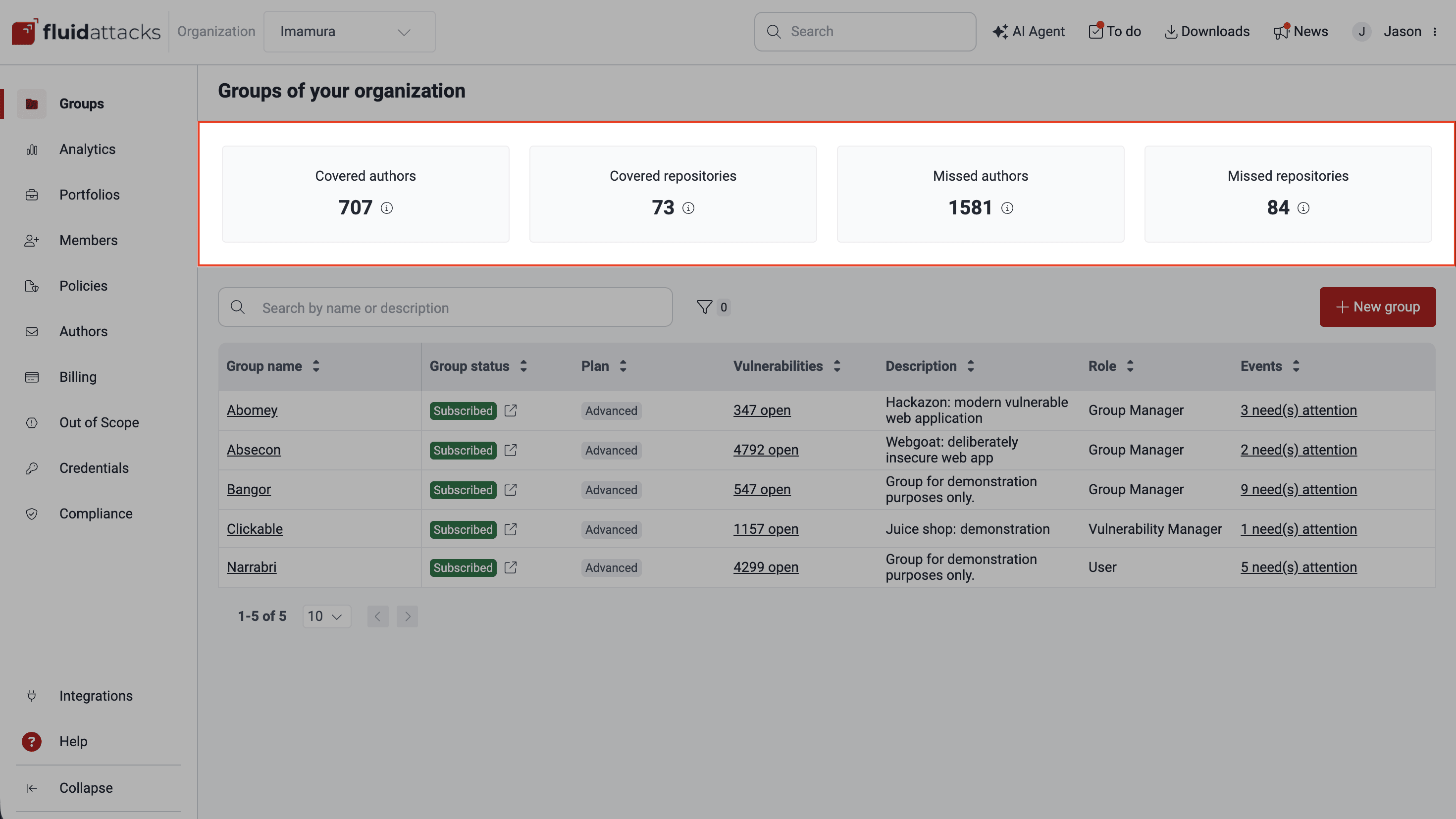
- Covered authors: Total number of authors who have made commits to the repository or repositories
- Covered repositories: Total number of repositories at the organization level that have been added to groups for source code analysis
- Missed authors: Total number of authors who have made commits to missed repositories
- Missed repositories: Total number of repositories are not included in groups for source code analysis (learn more about these in See retrieved repositories not yet added to any group)
Clicking on any of these four boxes will redirect you to the platform's Outside section.
Group table
In the group table, you find the names of all the groups you have access to within your organization, along with details about the groups and your role in it. This table has seven columns, the contents of which may be organized alphabetically or numerically (either in ascending or descending order) by clicking on the arrows next to each column name. You can filter the table by group name or subscription plan, and you can use the search box to display only the rows that have the content you type in it.
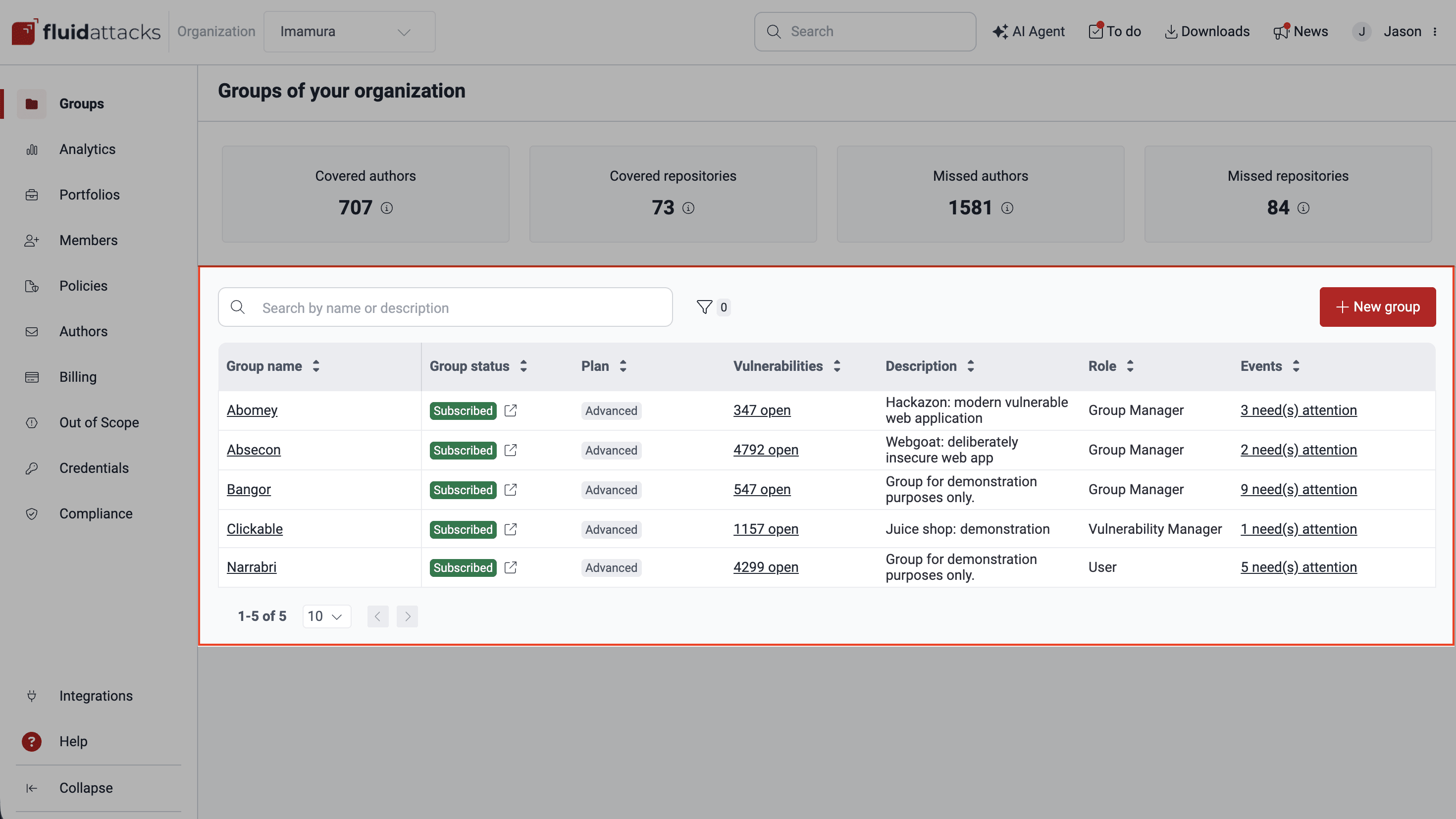
The groups table provides you with the following information:
- Group name: The name your organization has given to the group
- Group status: The group's payment status, which can be one of the following:
- Subscribed: A valid payment method has been provided
- Free-trial: The group is assessed under the free trial of the Essential plan, which does not require providing a payment method
- Suspended: Either the validity of the provided payment method is being analyzed or a payment method has not been provided upon completion of the free trial
- Plan: Either the plan to which the group is subscribed or the indication that the group is assessed under a free trial; accordingly, this column may display one of the following values:
- Essential: Secures your application through completely automated security testing and help in vulnerability remediation
- Advanced: Leverages the Essential plan features and the manual security testing and help in understanding vulnerabilities from a team of pentesters
- Free-trial: Secures your application through all the Essential plan features for 21 days
- Vulnerabilities: Either the total number of open vulnerabilities detected in the system(s) associated to the group or the status of the assets provided for the group; accordingly, this column may display one of the following values:
- Add repository: The group exists but a repository to assess has not been added
- Cloning: A repository is being cloned for security testing
- Cloning error: There is an error in the cloning process of all the group's roots
- Testing: A successfully cloned root is being tested
- No vulnerabilities: No vulnerabilities have been found in the system(s) associated to the group
- [#] open: The total number of vulnerabilities detected in the group that have not been remediated
- Description: A short description of the group given at its creation
- Role: Your role within the group, which can be one of the following:
- User: Role for those responsible for understanding and remediating vulnerabilities detected in your software projects
- Vulnerability Manager: Role for those responsible for reviewing the requests of developers (generally with the User role) and tracking progress in remediation
- Group Manager: Role for those responsible for granting access and roles, managing the target of evaluation and policies, and tracking progress in remediation
- Events: The number of unsolved events in the group (i.e., situations that prevent the assessment of part, or the entire, target of evaluation)

You can access sections dedicated to a group by clicking on its name. Your access to the group sections and usage of their available functionalities depend on your role on the platform. You can read a short description of each group-level section on the page Platform sections and header items.
Create a new group
 Role required: Organization Manager
Role required: Organization Manager Creating a new group increases the cost of Fluid Attacks' Continuous Hacking so make sure it is a concerted action within your organization.
Creating a new group increases the cost of Fluid Attacks' Continuous Hacking so make sure it is a concerted action within your organization.
Filter group table data
 Role required: User, Vulnerability Manager, Group Manager or Organization Manager
Role required: User, Vulnerability Manager, Group Manager or Organization Manager
Find filters in Groups

Apply filter

Search the group table
 Role required: User, Vulnerability Manager, Group Manager or Organization Manager
Role required: User, Vulnerability Manager, Group Manager or Organization ManagerSee events impeding tests in groups
 Role required: User, Vulnerability Manager, Group Manager or Organization Manager
Role required: User, Vulnerability Manager, Group Manager or Organization Manager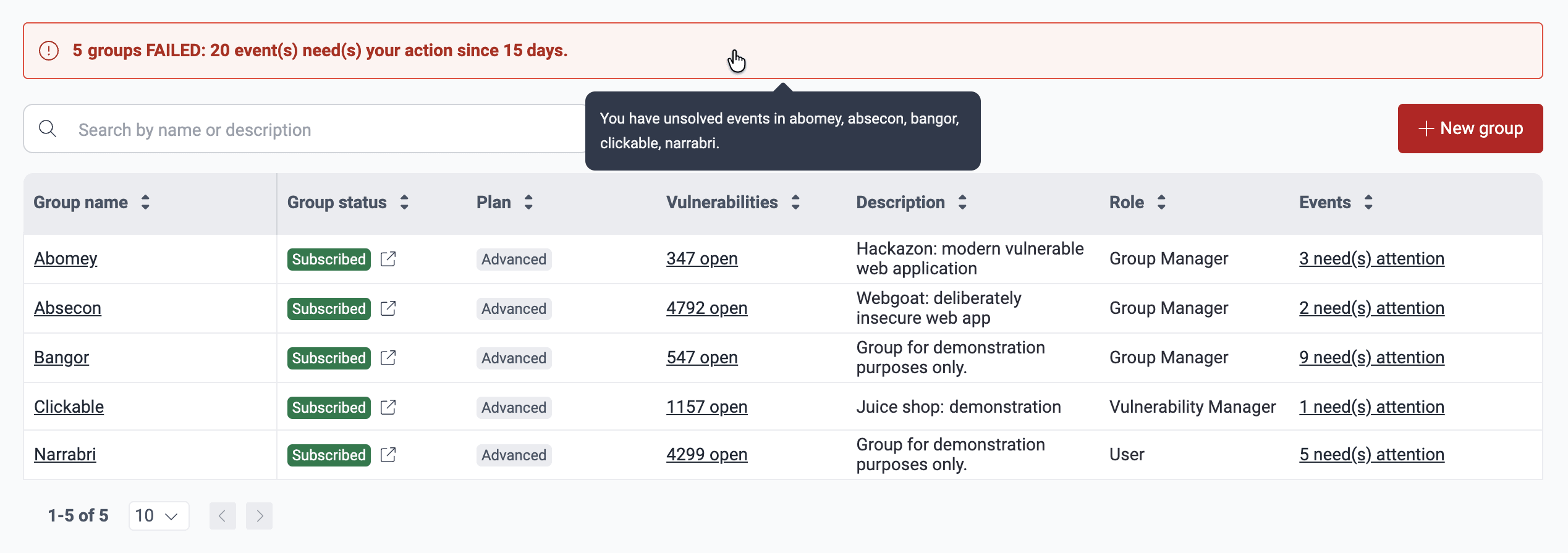
To learn about the types of events and managing them, read the page Resolve Events impeding tests.
Switch between groups
 Click to access group list
Click to access group list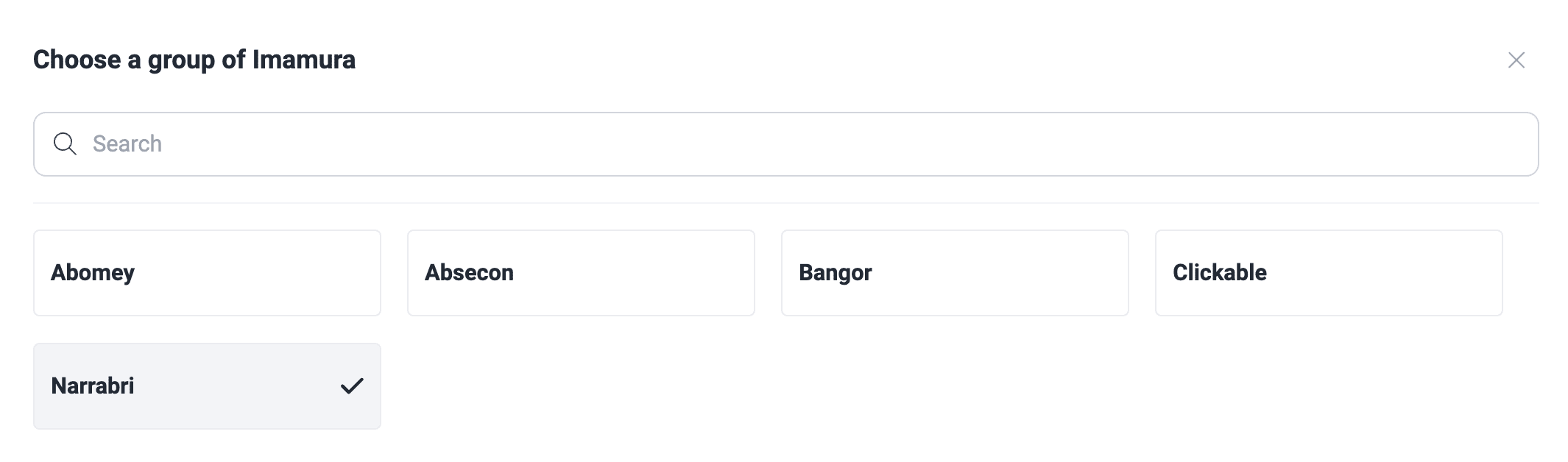 Select a group to enter
Select a group to enter Free trial
Free trial