Platform sections and header items
Organization-level sections
Once you log in to the platform, you are at this level, which collects and presents information related to all the groups or projects your company has with Fluid Attacks.
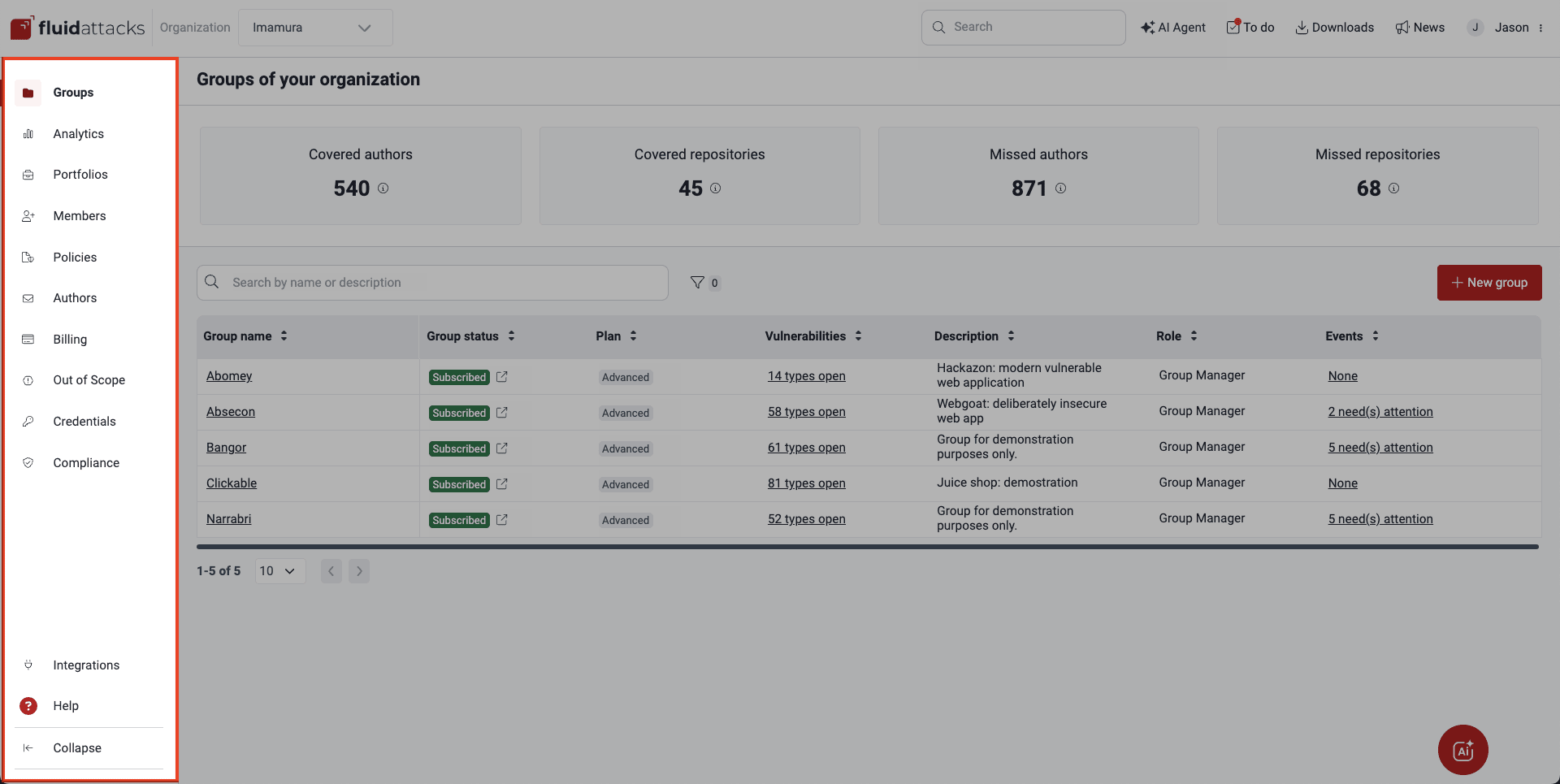
Groups
Your company may have several applications or software products and want to keep track of their security assessments and risk exposure separately. This is why you can create a group in the platform for each of them. In the Groups section, you find the list of your groups and several bits of information about each of them, as well as the total amounts of covered and missed contributing authors and repositories across the organization's groups.
Analytics
In the Analytics section at the organization level, you can view various charts, tables and figures with valuable information on security testing results, vulnerability management strategies, and progress in reducing risk exposure in your organization (i.e., including data from all its groups), among other things. Here are some examples of the information available:
- Exposure management over time
- Exposure benchmark
- Remediation rate benchmark
- Accepted vulnerabilities by CVSS severity
- Vulnerabilities treatment
- Reporting technique
Portfolios
Portfolios are sets of groups that you can create to establish and observe comparisons of some of the data displayed in their respective Analytics sections. In the Portfolios section, you will find the list of portfolios created by your organization.
Members
 Role required: Vulnerability Manager or Organization Manager.
Role required: Vulnerability Manager or Organization Manager.Policies
Fluid Attacks allows you to view or establish policies around accepting security vulnerabilities, preventing deployment into production when vulnerabilities are present, and prioritizing vulnerabilities for remediation. Those defined in the Policies section are inherited by all the groups in your organization, although group-specific policies may be established in the Scope section.
Authors

Billing
 Role required: Organization Manager
Role required: Organization ManagerOut of Scope
Fluid Attacks recommends you use Open Authorization (OAuth) to import the repositories to be tested. This entails connecting Fluid Attacks' platform to your account on a code repository hosting provider (such as GitLab) to retrieve the repositories there without sharing credentials with Fluid Attacks. The Out of Scope section shows the repositories that were not selected to be imported in the mentioned process and included in one of the groups. Therefore, those repositories are not yet within the scope of Fluid Attacks' security testing. In this section, you may add them to groups.
Credentials
In the Credentials section, if you have a Organization Manager role, you can authorize Fluid Attacks to retrieve your repositories on Azure, Bitbucket, GitHub or GitLab through OAuth. Such authorization is saved in the platform as credentials that can in future be associated to more assets they give access to so that they can be tested. However, actual credentials, such as username and password pairs, can also be added on this section. Fluid Attacks uses OAuth and credentials safely to have access to the target of evaluation (ToE).
Compliance
The Compliance section shows details of your organization's compliance with several international standards which are the basis for the security requirements that Fluid Attacks tests in your systems. Among the useful information provided here are how well your organization is doing with particular standards in comparison to other organizations and how many days it will take your organization to achieve compliance with all standards.
Logs
 Role required: User
Role required: UserIntegrations
Help
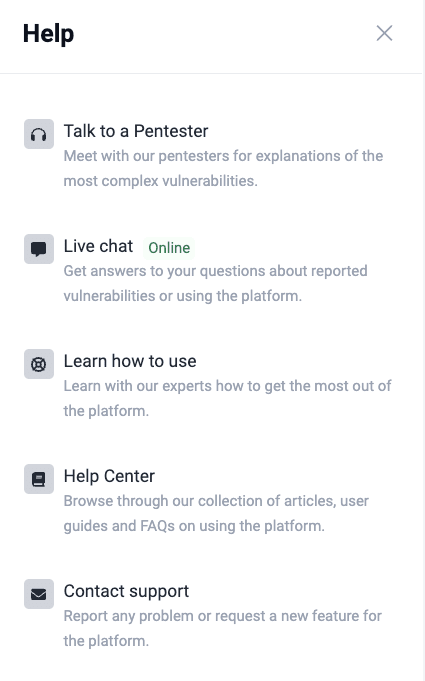
- Talk to a Pentester: Use this Advanced-plan-exclusive feature to have a videoconference with one of Fluid Attacks' pentesters about complex reported vulnerabilities. (You can view and use this option only while you are inside a group that is subscribed to the Advanced plan.)
- Live chat: Use this option to send Fluid Attacks questions about any feature of the platform and its use that you have not found the answer to in the Help Center.
- Learn how to use: Click on this option to find a link to the Fluid Attacks' certification tailored to your role that you can achieve in about one hour (see topics in Tutorial videos) or to schedule a live demo.
- Help Center: This should be your go-to option for any doubt you have. If Fluid Attacks' documentation does not help you, you can consider the other help options.
- Contact support: You can click on this option to send an email to Fluid Attacks.
Group-level sections
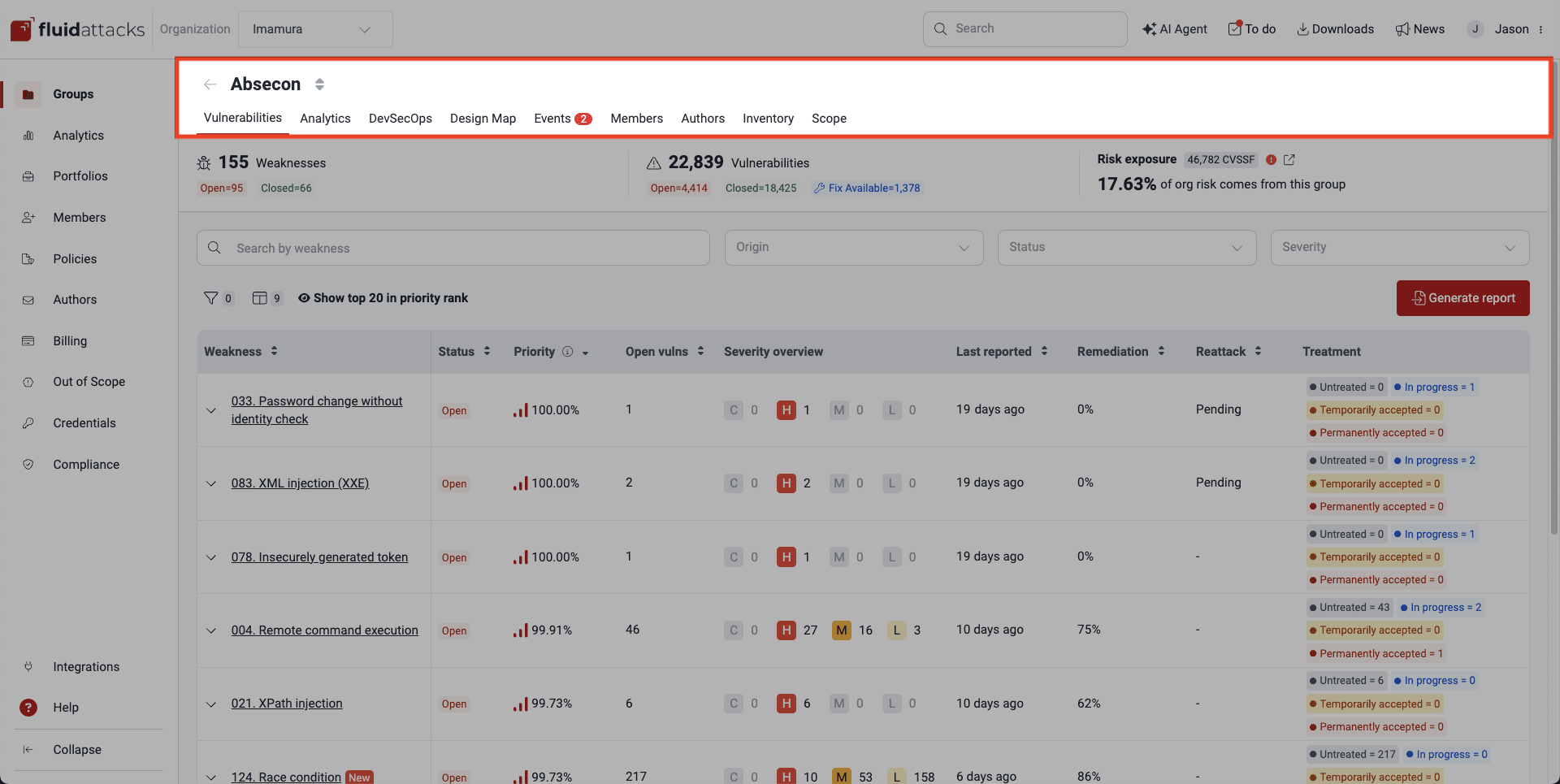
Vulnerabilities (by weakness)
The Vulnerabilities section on the platform is where you can access detailed information on all the confirmed security vulnerabilities found in your own code, including the recommendations for remediating them. They are conveniently categorized by weakness, according to Fluid Attacks' conceptualization.
When you click on the weakness name, you are presented with sections dedicated to vulnerabilities under it. The main features of these sections are summarized below on this page.
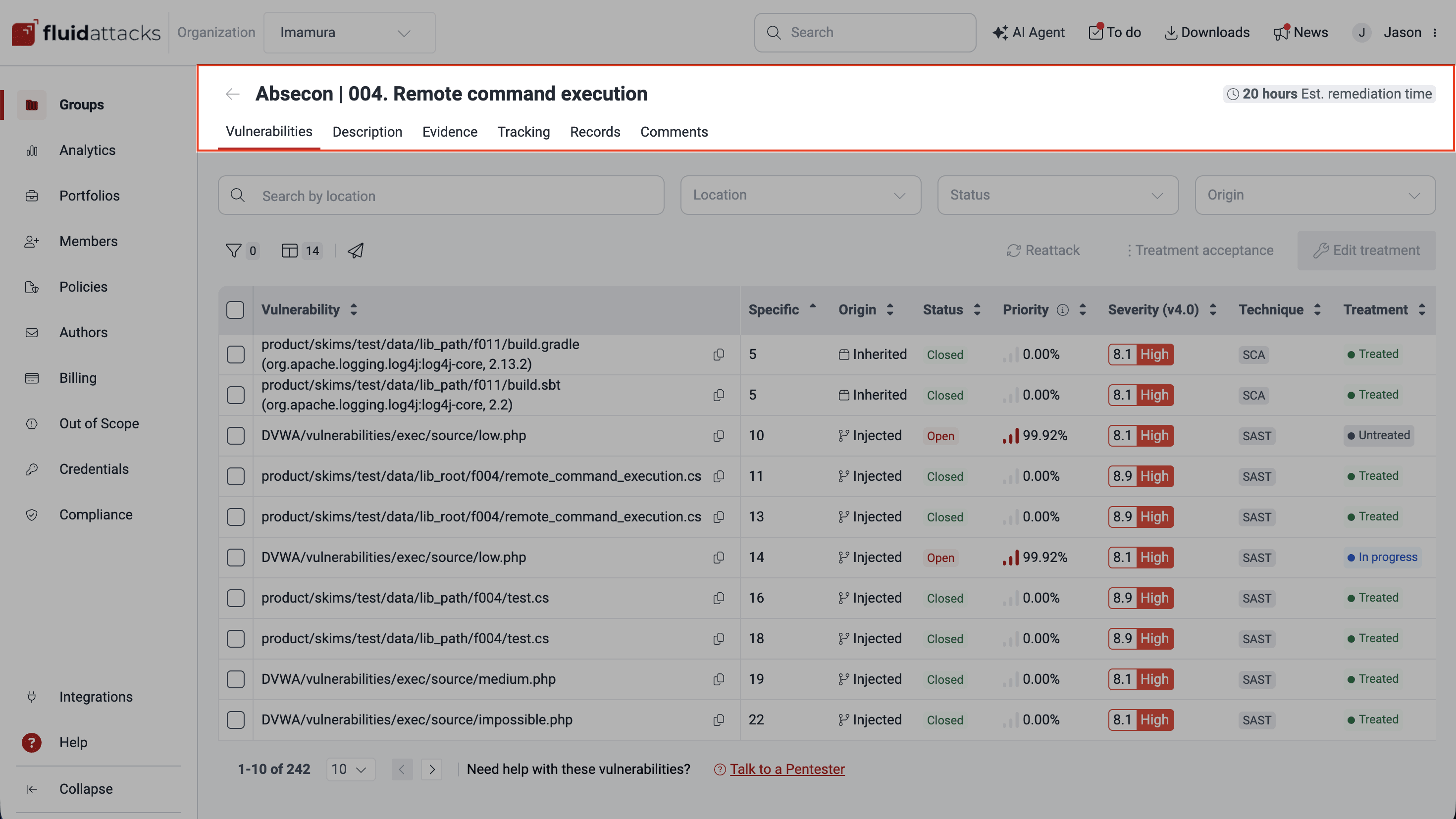
Vulnerabilities
In the Vulnerabilities section, you see the list of the vulnerabilities named after file paths and specific inputs/lines of code/ports where Fluid Attacks found them. Useful functions in this section include the options to define the treatment for vulnerabilities (e.g., assign fix work to yourself or someone in your team) and request a reattack (i.e., a retest to verify whether the vulnerability was successfully remediated).
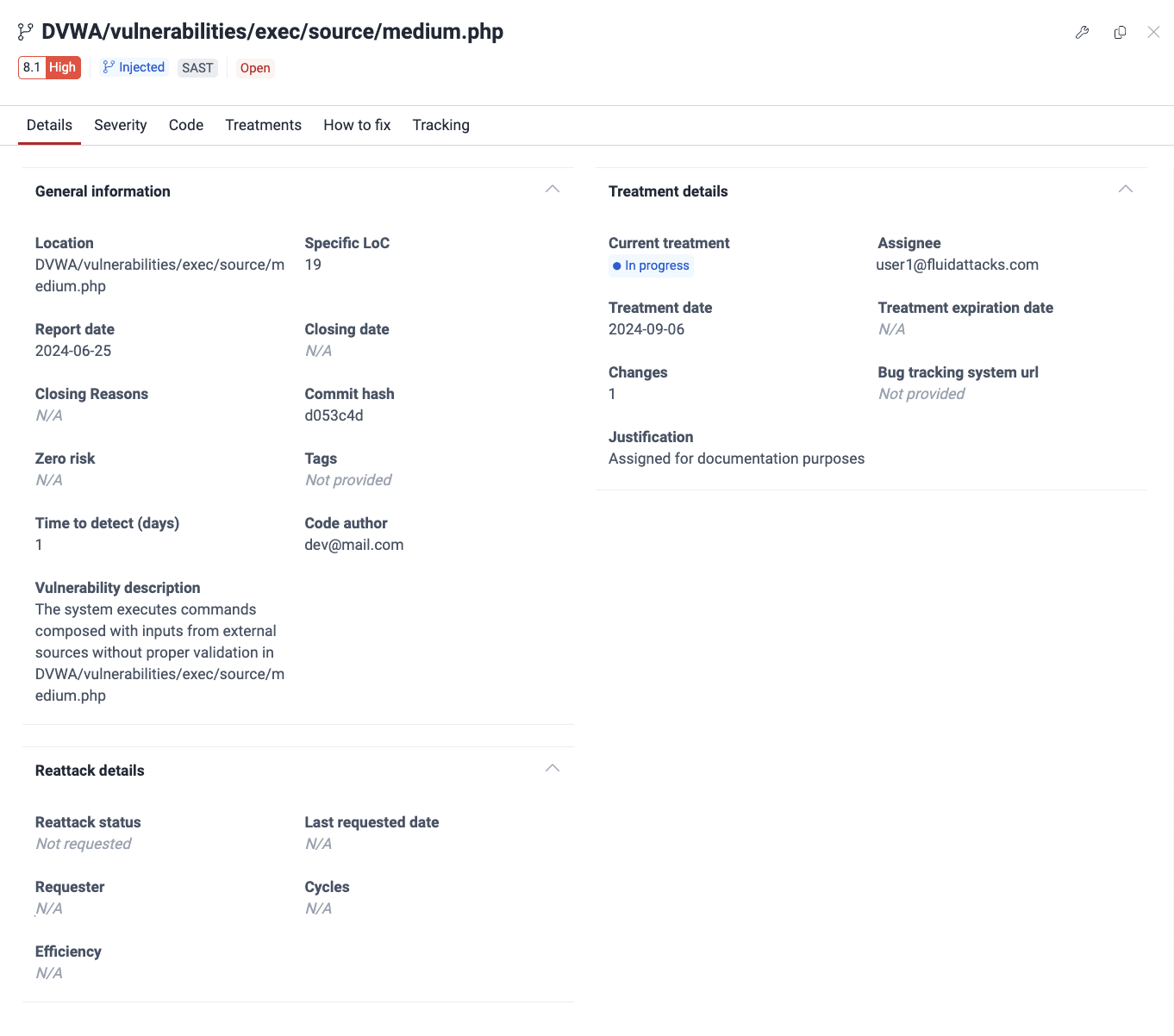
- Details: Description and current treatment, among other information
- Severity: Breakdown of the assigned severity score using the Common Vulnerability Scoring System (CVSS) v4.0
- Code: The actual line(s) of code presenting the vulnerability and lines that surround it/them
- Treatments: The current treatment and assigned tags with the option to change them
- How to fix: The AI-generated custom guide to remediate the vulnerability
- Tracking: The treatment and reattack history
Description
In the Description section you can learn the definition of the type of vulnerability along with the security requirements that may have been violated, the impacts expected of vulnerability exploitation, the characteristics of the threat actor that may exploit it, and recommended actions to fix the code.
Evidence
The Evidence section provides supporting evidence of the existence and exploitability of the specific type of vulnerability reported. The evidence can come in the form of images or videos.
Tracking
The detailed treatment history of the type of vulnerability is provided in the Tracking section, along with information on the number of vulnerabilities reported and remediated.
Records
In the Records section you find a table with sensitive information obtained by Fluid Attacks' team of pentesters after exploiting the vulnerability in your system. The data may be financial information (e.g., account numbers), personal information (e.g., phone numbers), and technical information (e.g., access tokens).
Comments
Comments is a forum-like section to communicate with Fluid Attacks about the reported vulnerabilities or to find out the outcome of reattacks.
 Note: Comments for vulnerabilities is available for users with the Essential plan in view mode.
Note: Comments for vulnerabilities is available for users with the Essential plan in view mode.Analytics (group-level)
Within the group-level Analytics section, you discover graphs and figures on the status and characteristics of reported vulnerabilities and your remediation practices related to that specific group. Among the group-specific analytics are those related to the status and executions of Fluid Attacks' CI agent.
DevSecOps
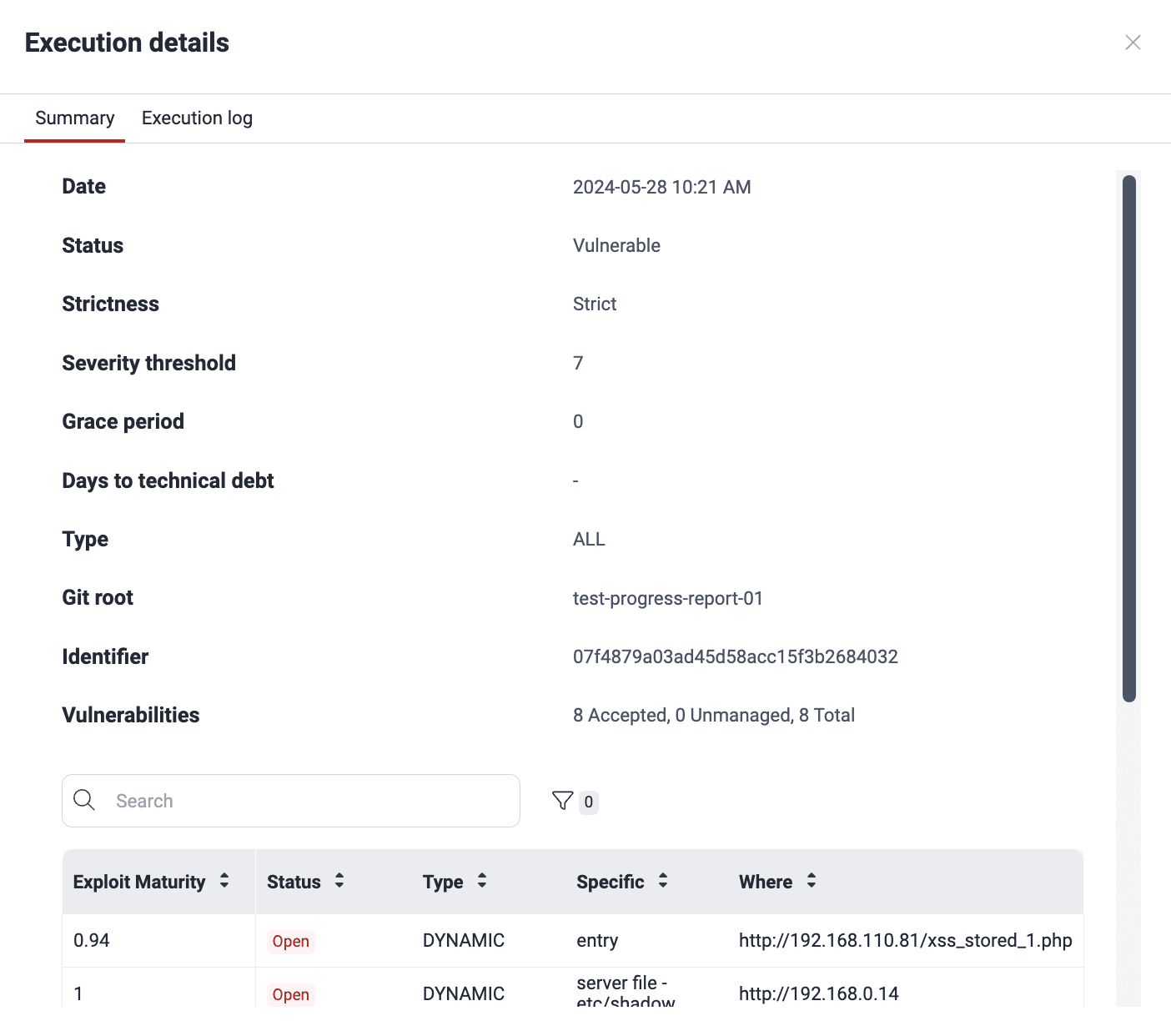
Fluid Attacks offers its CI Gate that you can install in your CI pipelines to break the build when attempting to deploy software versions with vulnerabilities into production. Breaking the build, when enabled, follows the policies set by your organization. The DevSecOps section shows the details and results of recent CI Gate executions.
Design Map
The Design Map section shows the correlations between your threat model and vulnerabilities Fluid Attacks has detected in your system. After uploading your threat model files, you can see your detailed threat descriptions matched with Fluid Attacks' vulnerability categories and their details, such as severity. This enables strategic prioritization of remediation efforts based on your specific security concerns.
Events
Fluid Attacks calls an "event" a situation that prevents testing of a part of the target of evaluation (ToE) or its entirety. Further, Fluid Attacks categorizes events into several types, for example, "credentials issues," when the information given for authentication is invalid. In the Events section, you can view the events that Fluid Attacks reports to you for your prompt action. Each reported event has sections dedicated to it, as shown in the following screenshot. The main features of these sections are summarized below on this page.
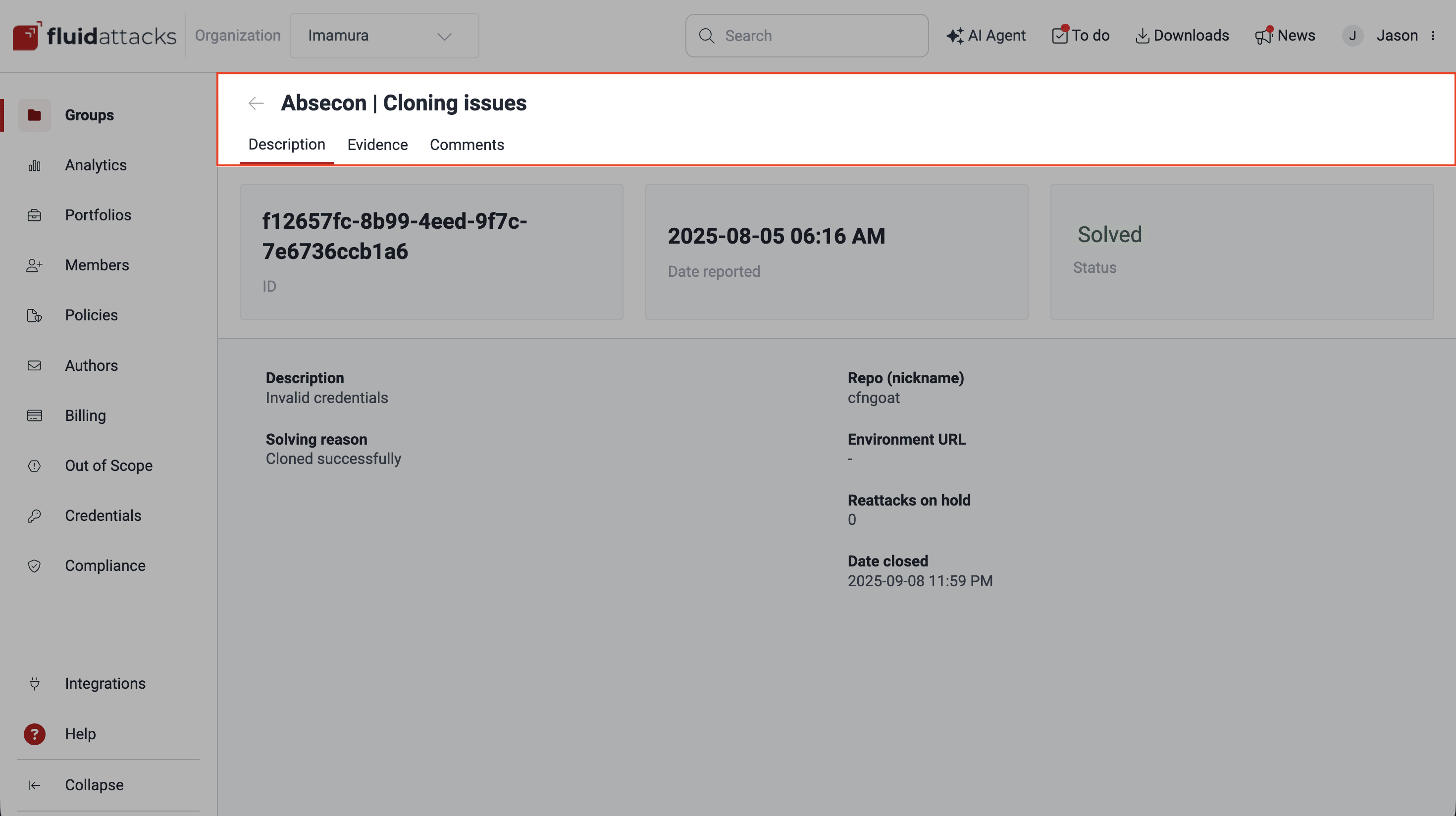
- Description: What the situation is, what part of the ToE it refers to, and whether it prevents reattacks
- Evidence: Images or videos that provide proof of the event
- Comments: Forum-like space to discuss the event
Members (group-level)
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group ManagerAuthors (group-level)
By "authors" Fluid Attacks refers to the developers contributing to the code repository each month. The Authors section gives you a list of such users and informs you whether they have registered to Fluid Attacks' platform. If you have the Group Manager role, you can invite authors not yet on the platform to register.
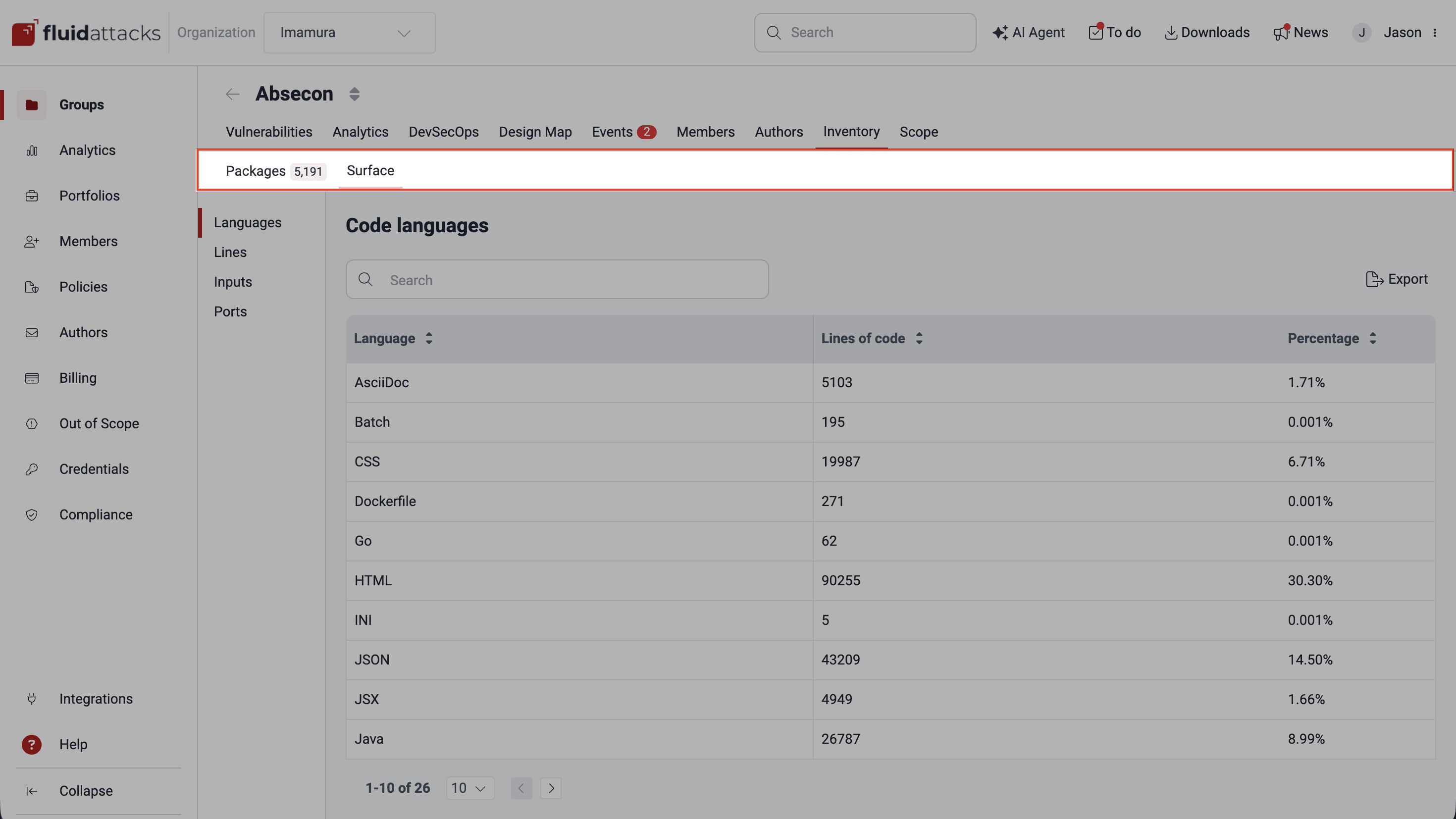
Inventory
Inventory's Packages section helps you keep track of the third-party dependencies in your software. Thanks to it, you can find out which dependencies have reachable vulnerabilities and where you are using them, enabling you to analyze your usage of them and make informed decisions.
Scope
In the Scope section you mainly define Fluid Attacks' Target of Evaluation (ToE). The following information is entered in this section to facilitate, or in some cases enable, security testing with Fluid Attacks' Continuous Hacking:
- Git Repositories: Git repositories where you version the application’s source code
- Environments: URLs where applications are deployed
- IP Roots: Web applications reachable through specified IP addresses (only in groups subscribed to black-box testing)
- URL Roots: Dynamic environments already deployed on a web server (provided only in groups subscribed to black-box testing)
- Files: Mobile applications, or any documents (i.e., software documentation) that could help understand or use the system under evaluation
- Portfolio Tags: Keywords to build portfolios, thus getting information and analytics for groups that share the tag
- Information: General information about your company, useful, for example, for generating complete security testing certificates
- Group Settings: Specific configuration options for the group, i.e., group context, group disambiguation, DevSecOps agent token management, function for the user to unsubscribe from the group, and function to delete the group
Platform header items
The top part of Fluid Attacks' platform, like the collapsible menu, is always visible as you navigate the application. Its functions include providing you access to your tasks and user information and settings.
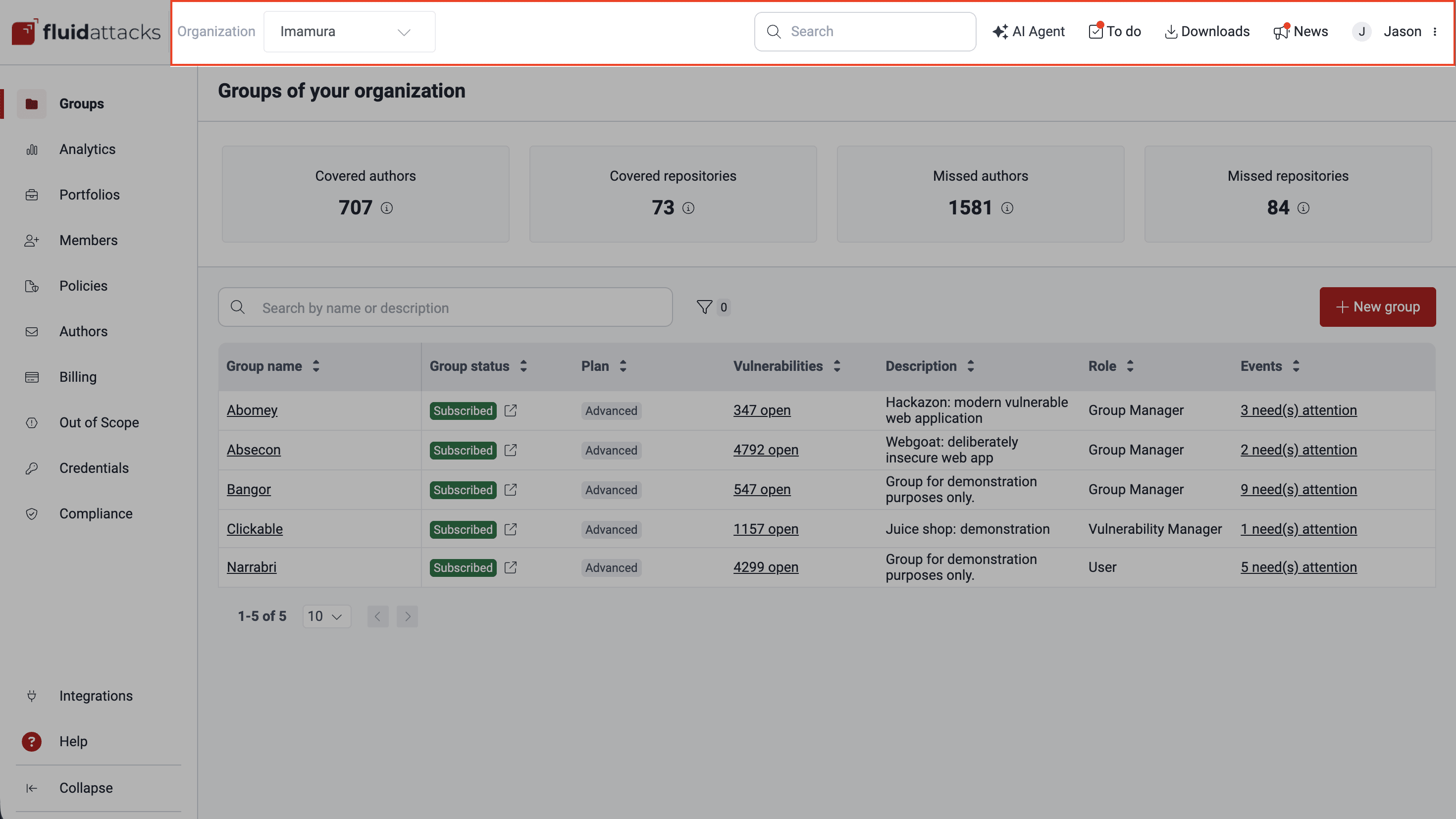
Organization menu
Group search box
AI Agent
To do
Downloads
News
User menu
View as client

Feature preview

API token
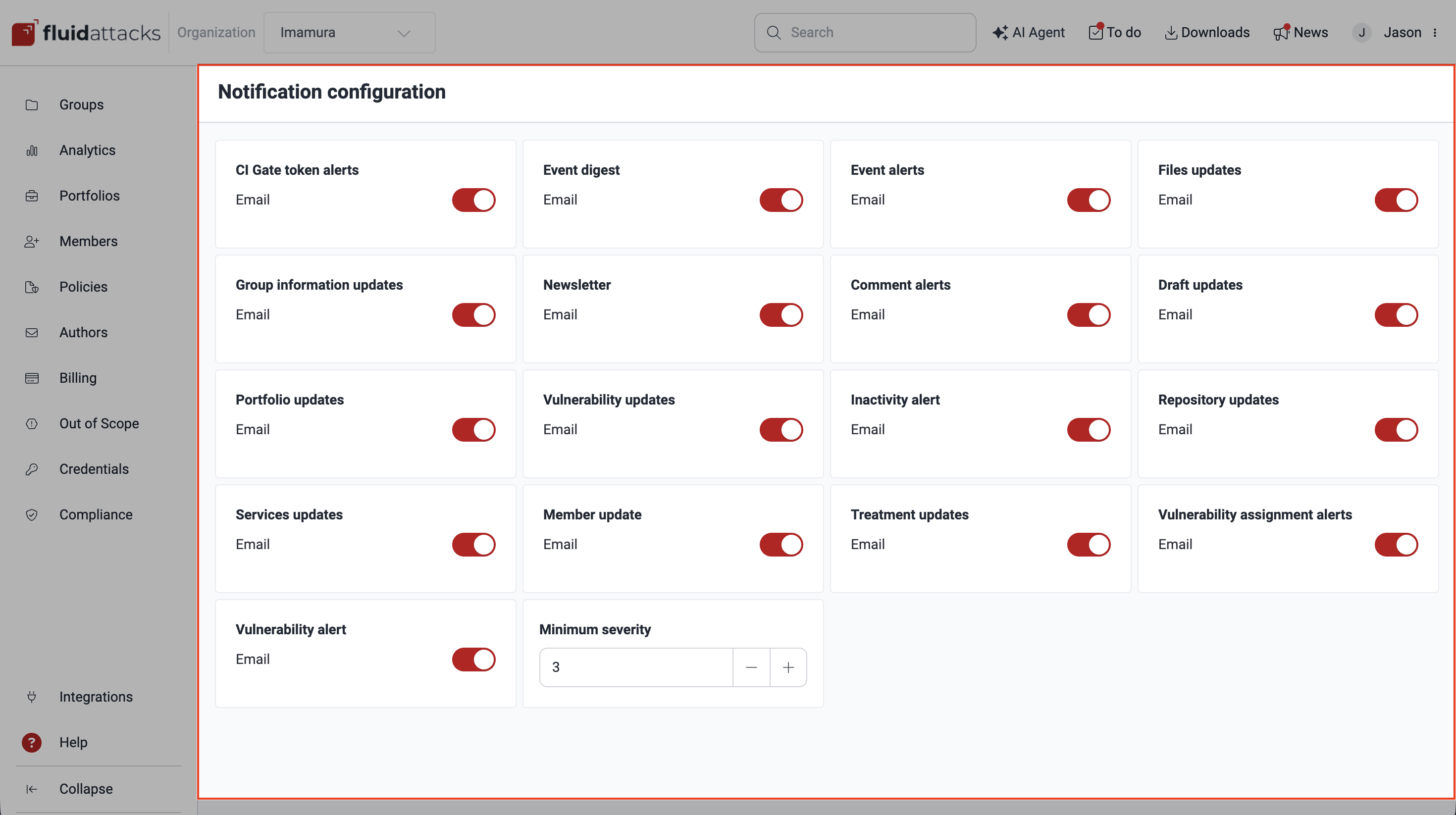
Notifications
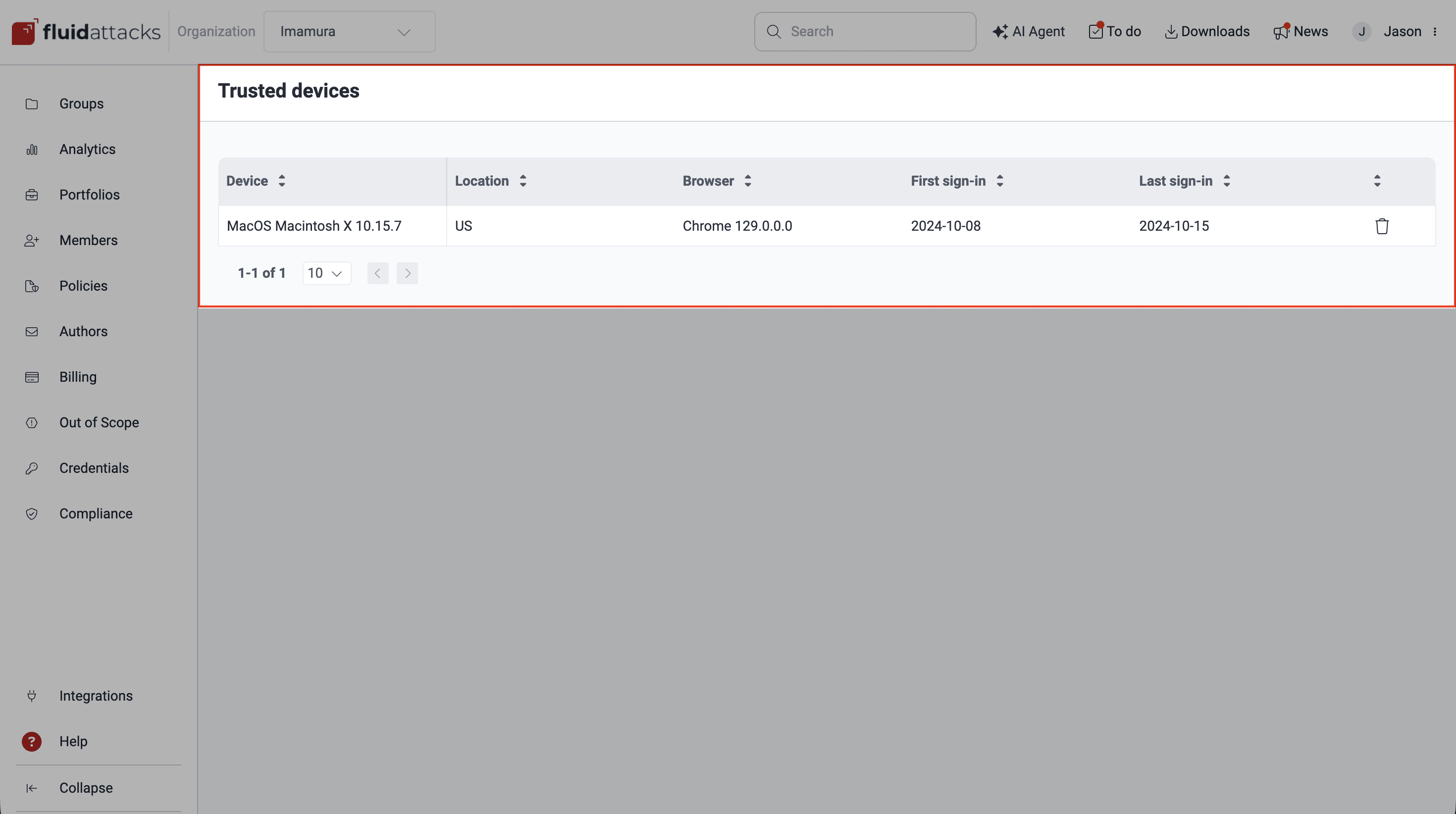
Trusted devices
Mobile
Ethics Hotline
Delete account
Log out
Platform version
