View analytics for the group level only

 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
Vulnerabilities closing reason
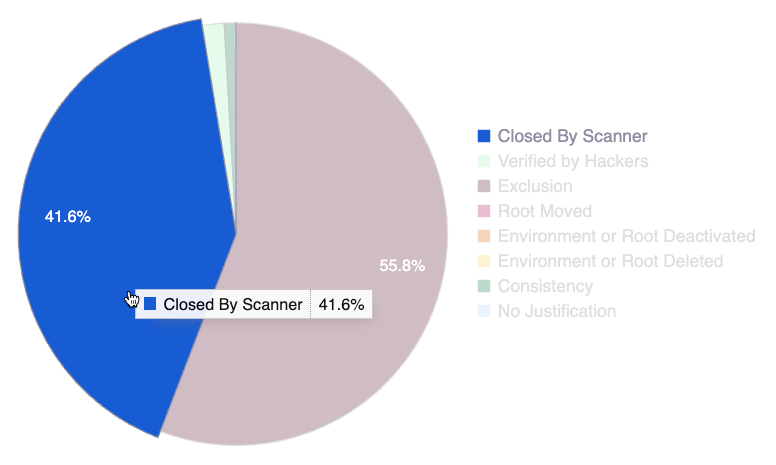
- Hover over a slice to see the reason and percentage information
- Hover over a chart legend to highlight the corresponding slice in the chart
- Click on a chart legend to exclude the corresponding reason from the percentage calculation
Group availability time
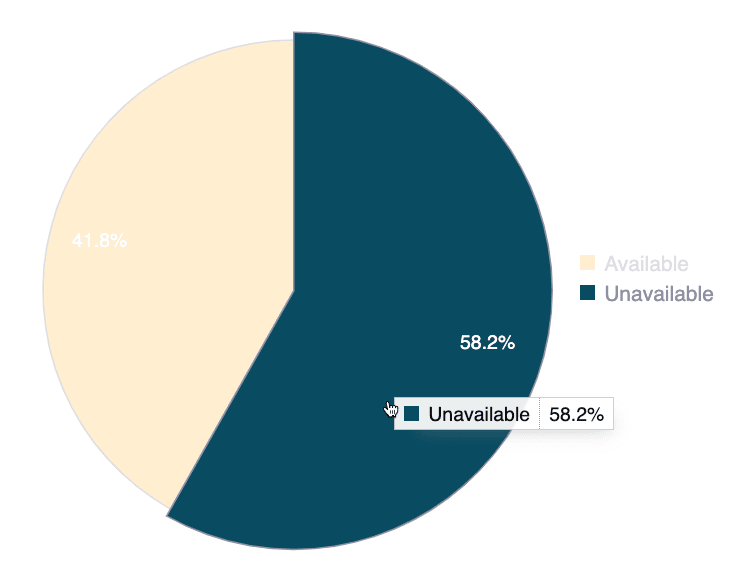
The group availability metric displays the percentage of time the group has had unresolved events throughout its entire existence. Events are situations that prevent Fluid Attacks' tool or team of pentesters from conducting security testing on part of the group's scope or its entirety. This information provides a quick overview of the group's promptness in guaranteeing the conditions required for complete assessments.
- Hover over a slice to see the status and percentage information
- Hover over a chart legend to highlight the corresponding slice in the chart
- Click on a chart legend to exclude the corresponding status from the percentage calculation
Total exclusions
Exclusions by repository

Days since group is failing
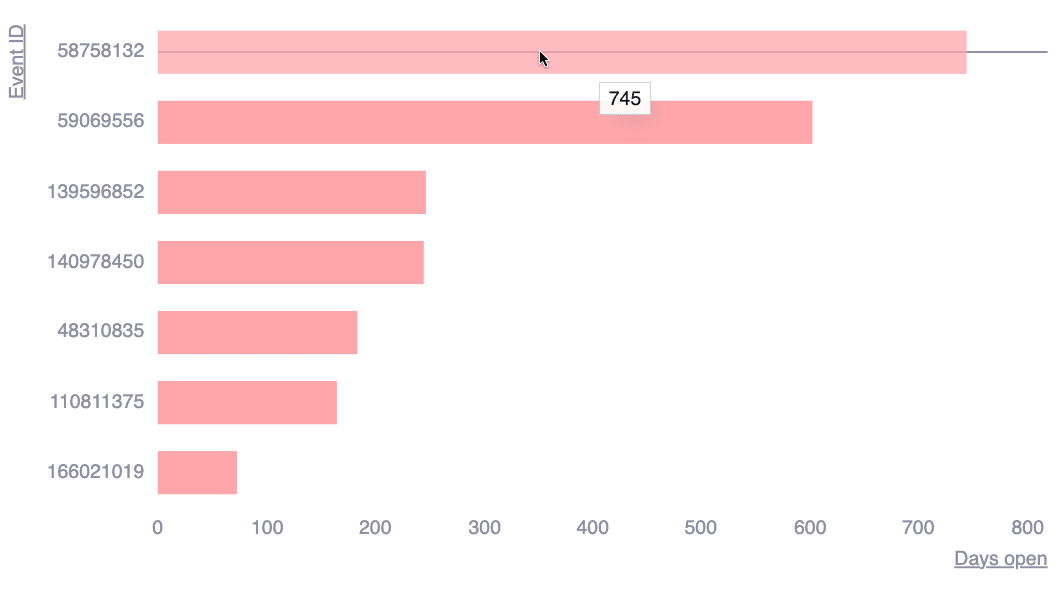
This chart shows the number of days each event in your group has remained unresolved. This information helps you prioritize long-standing issues.
Weaknesses by tags
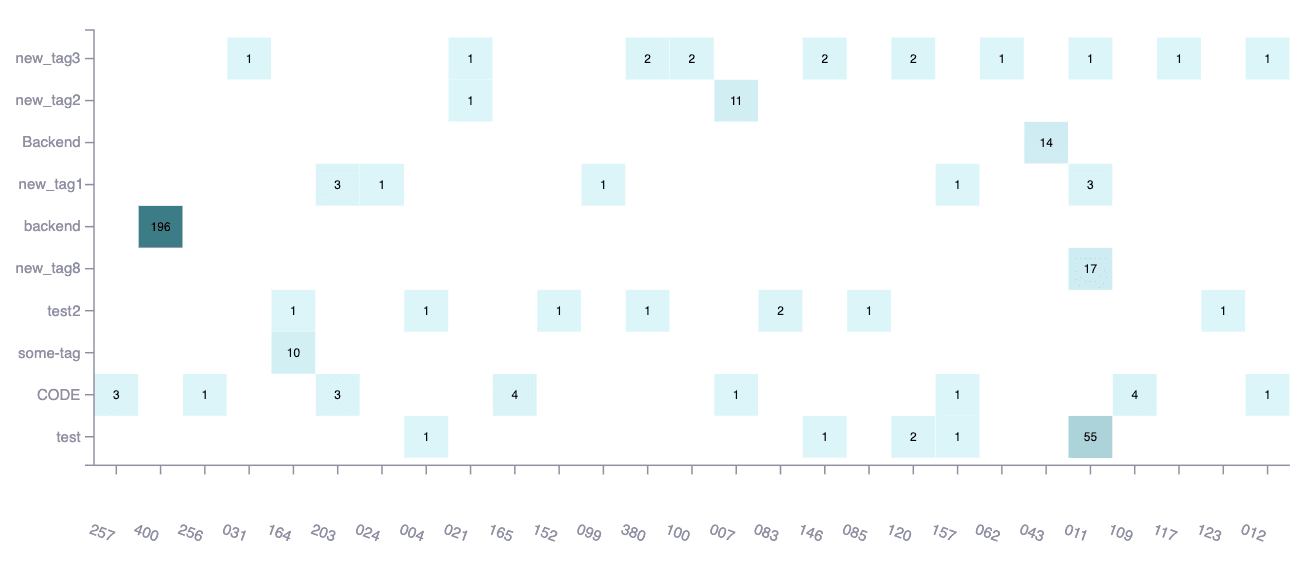
This chart shows the times each of your tags are used in multiple of the reported types of vulnerabilities. You can see vulnerabilities' tags in the Locations section and add them by editing vulnerabilities. This helps you analyze security issues in your group using categories that are especially significant for your team.

CI Gate-related analytics
By enabling CI Gate, you can verify the status of security vulnerabilities on your system. You can embed this application, which is offered as a Docker container, into your continuous integration system to benefit from the following:
-
You would be running fast and automatic scans on the code you just wrote.
-
You can (optionally) set CI Gate to flag the build as failed if it finds any noncompliance with your organization policies or group-specific policies. This strict mode can be customized with severity thresholds and grace periods according to your team's needs.
-
Statistics from over a hundred different systems show that breaking the build with CI Gate increases the remediation ratio and speed, helping you build a safer system and save on remediation costs throughout your software security development lifecycle (SDLC).
Service status
This is an indication of whether Fluid Attacks' CI Gate is currently Active or Inactive.
Service usage
This figure is the number of times your team has run CI Gate to proactively check the status of vulnerabilities in your builds.
Repositories and branches
This figure is the number of repositories and branches you check with CI Gate.
Your commitment towards security
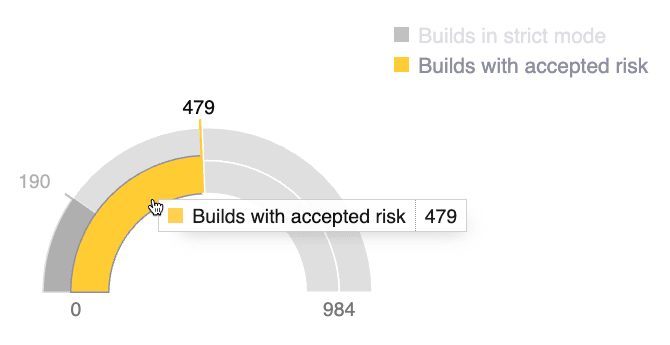
CI Gate's primary objective is to serve as a gatekeeper for your team's deployments. Your team is responsible for important vulnerability management settings affecting CI Gate's behavior, such as the following:
- CI Gate's strict mode: Enabled by default, the strict mode helps prevent the introduction of vulnerable code into your system by halting builds or deployments if vulnerabilities are detected which have not been fixed.
- Vulnerability acceptance: Vulnerabilities that have been accepted on the Fluid Attacks platform are disregarded even in strict mode, allowing CI Gate to proceed with builds or deployments as determined by your team.
This chart shows the number of CI Gate's executions with strict mode enabled and that for executions that found accepted vulnerabilities. This information helps your team create goals for the accepted risk to be low and for the usage of strict mode to be high.
- Hover over a portion to see the status and number information
- Hover over a chart legend to highlight the corresponding portion in the chart
- Click on a chart legend to hide the corresponding status from the visual comparison
Builds risk
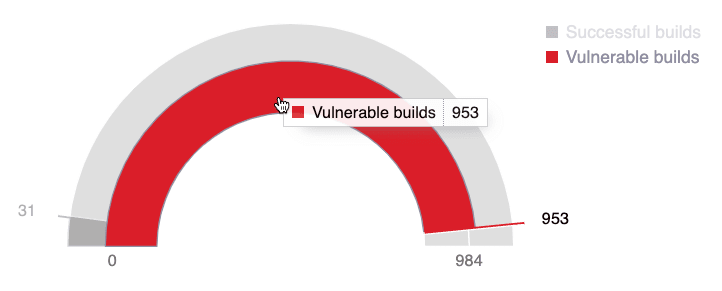
This chart shows the number of CI Gate's executions (detailed in the group's DevSecOps section) in which vulnerabilities were found and those in which there were none. This information helps you understand how well you are avoiding risky deployments.
- Hover over a portion to see the status and number information
- Hover over a chart legend to highlight the corresponding portion in the chart
- Click on a chart legend to hide the corresponding status from the visual comparison

