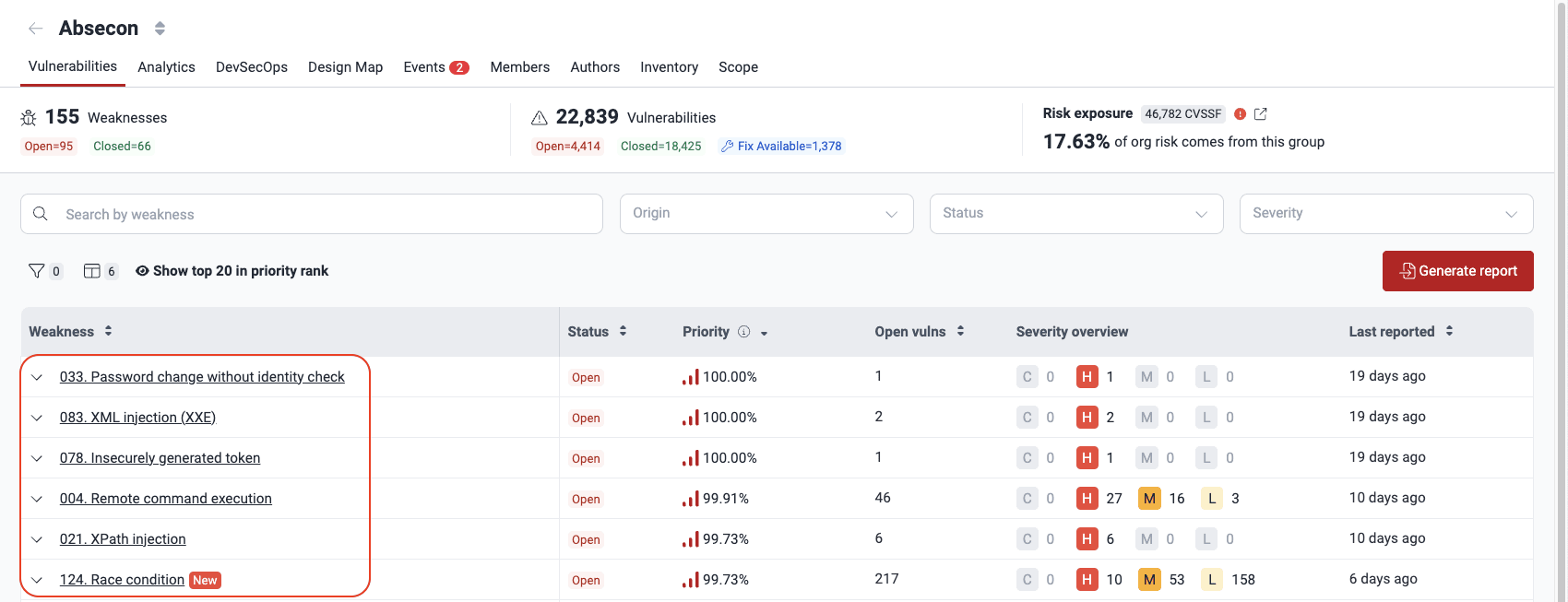
See where vulnerabilities are and more details
See a vulnerability summary
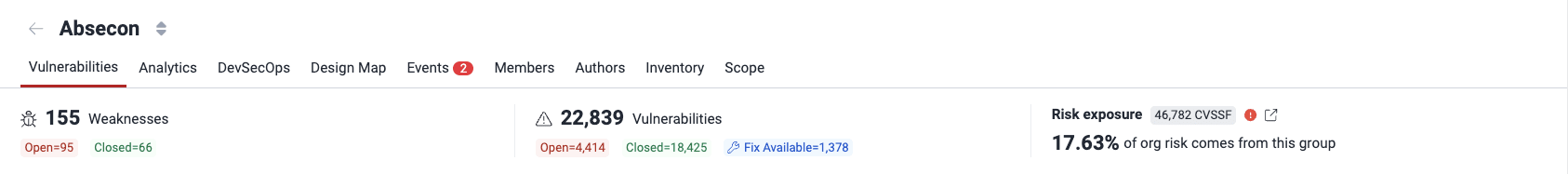
- Weaknesses: The number of categories into which detected security issues most likely fall
- Open: The number of weaknesses corresponding to vulnerabilities that are present in the system
- Closed: The number of weaknesses that were reported in the past but are currently not present in the system
- Vulnerabilities: The number of spots in the system where security issues have been detected
- Open: The number of vulnerabilities that are present
- Closed: The number of vulnerabilities that were reported in the past but are currently not present
- Fix Available: The number of present vulnerabilities that can be fixed with the help of Custom Fix or Autofix or for which a suggested package update is available
- Risk exposure: The sum of the CVSSF scores of all the vulnerabilities that have not been remediated (beneath is the percentage corresponding to the group's share of risk exposure within the organization)

See the list of vulnerabilities detected

- Since March 10, weaknesses 011 and 393 are no longer used to report vulnerabilities found with SCA. Instead, when you use a vulnerable software dependency, it is reported to you under the weakness the dependency actually has.
- Since April 4, severity information on the platform is exclusively available in CVSS v4.0.
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager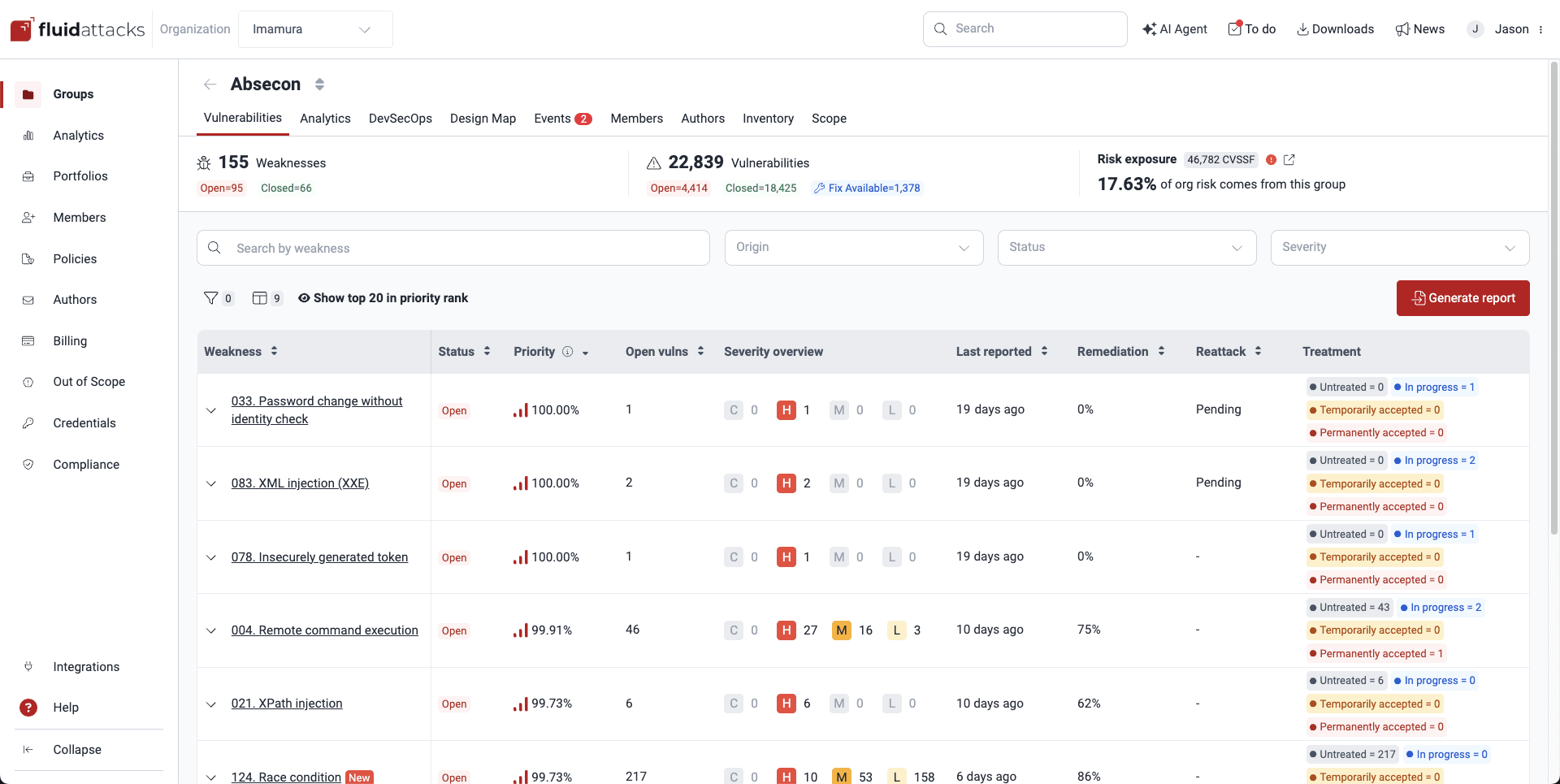
 Note: A weakness is a category following Fluid Attacks' classification, whereas a vulnerability is a specific instance of that weakness found in your software.
Note: A weakness is a category following Fluid Attacks' classification, whereas a vulnerability is a specific instance of that weakness found in your software.Know the Vulnerabilities table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerThe Vulnerabilities table conveniently groups the vulnerabilities detected in your system by weaknesses and provides general details.
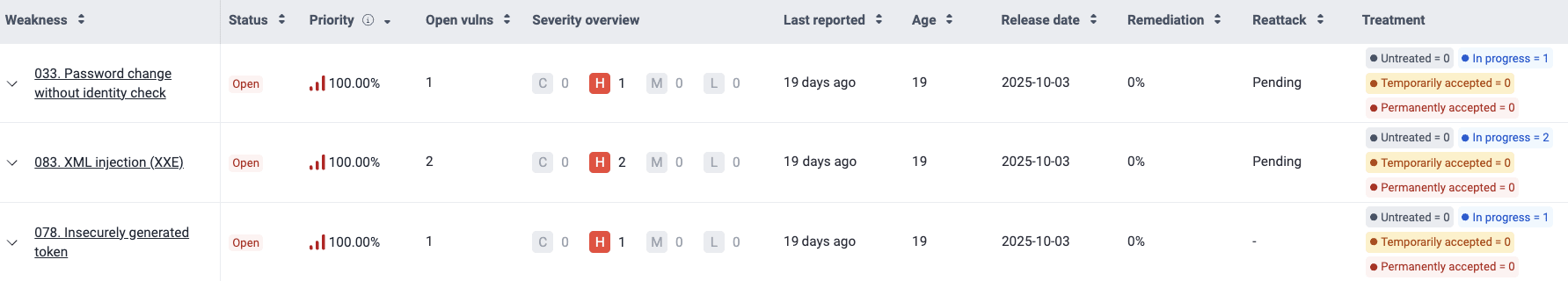
- Weakness: The standardized security weakness best matching the characteristics of the vulnerabilities in your system
- Status: Indicates the condition of this weakness, where it is Open if the weakness is present or Closed if the weakness has been remediated
- Priority: The percentile, relative to all vulnerabilities identified so far, occupied by the vulnerability with the highest remediation priority score among all those grouped within a given weakness. The priority score calculation depends on (a) your organization's prioritization policies based on the transitivity of the affected dependency, the phase of use of the vulnerable component, whether it is listed in CISA's KEV list, the EPSS, and the estimated time to fix; and (b) a default score calculated using the Common Vulnerability Scoring System (CVSS) as follows: (4^(CVSS-4)) / 4,096.
- Open vulns: The count of vulnerabilities in your system, related to the weakness, that are still present
- Severity overview: The number of detected vulnerabilities of each CVSS qualitative severity rating, which groups scores as follows:
- Low (0.1 - 3.9)
- Medium (4.0 - 6.9)
- High (7.0 - 8.9)
- Critical (9.0 - 10.0)
- Last reported: Days since the last detection of a vulnerability from the respective weakness category (regardless of the current Status)
- Age: Days since this weakness was first detected in your system
- Release date: Date when the weakness was first reported in your system
- Remediation: Percentage of the related reported vulnerabilities remediated by your team
- Reattack: Status of reattacks for this weakness ('Pending' if a reattack is due, '-' otherwise)
- Treatment: The number of vulnerabilities per assigned treatment

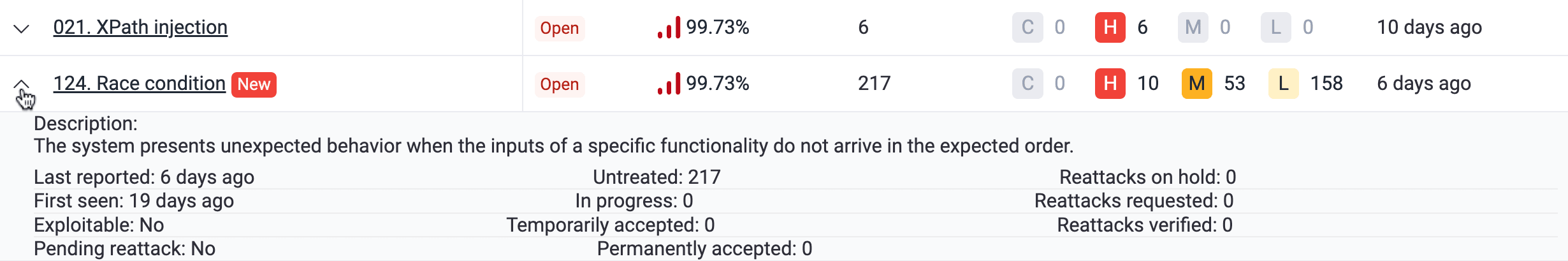

Spot newly reported vulnerabilities
Newly reported weaknesses are highlighted with a New label for seven days in the table, helping you quickly identify them.
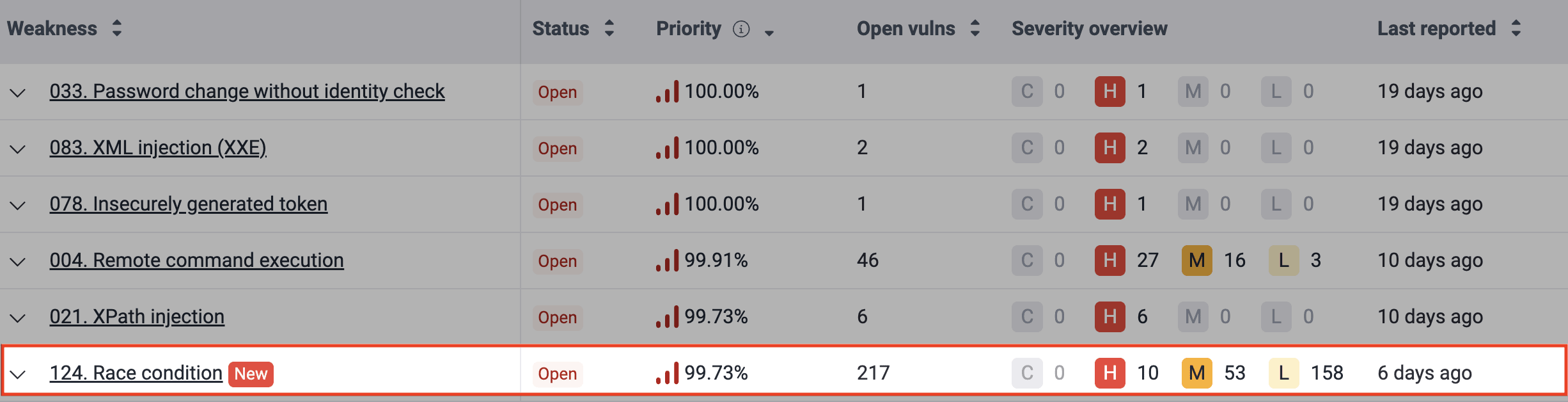
Search the Vulnerabilities table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager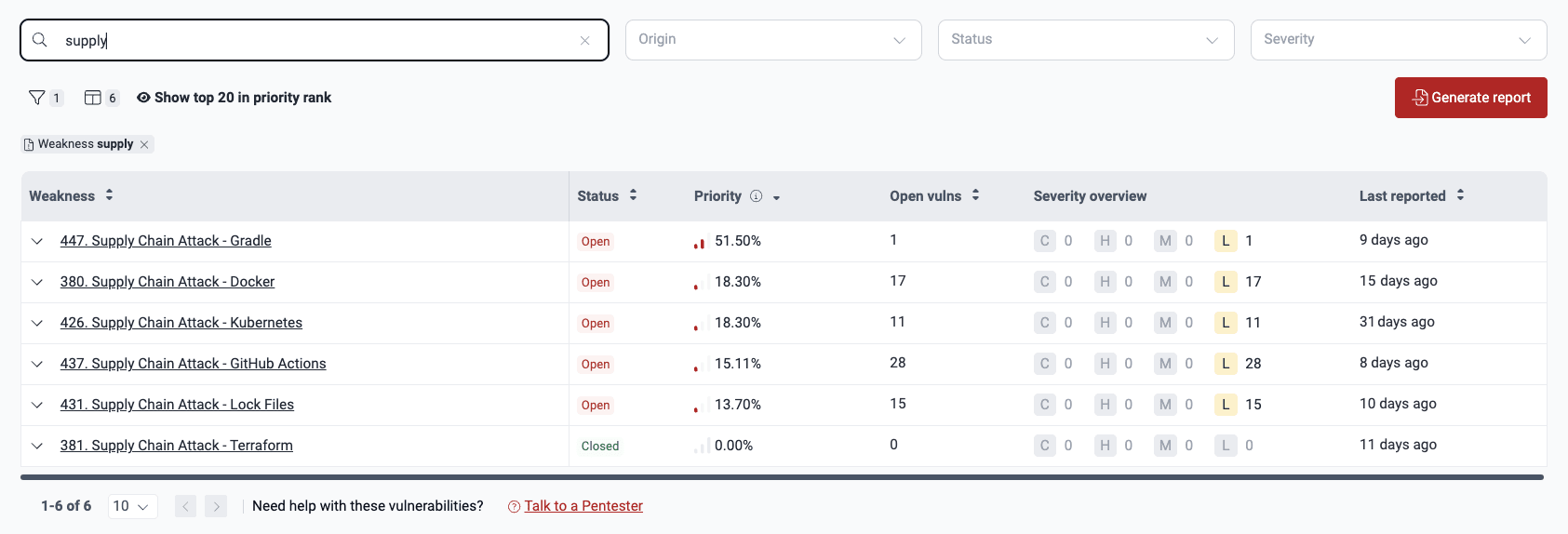
Filter the Vulnerabilities table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
Filters icon

Select a filter option

Select values and apply filter

 Note: Your filters persist only in the Vulnerabilities section of the group you applied them to.
Note: Your filters persist only in the Vulnerabilities section of the group you applied them to.
See top 20 vulnerabilities to prioritize
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
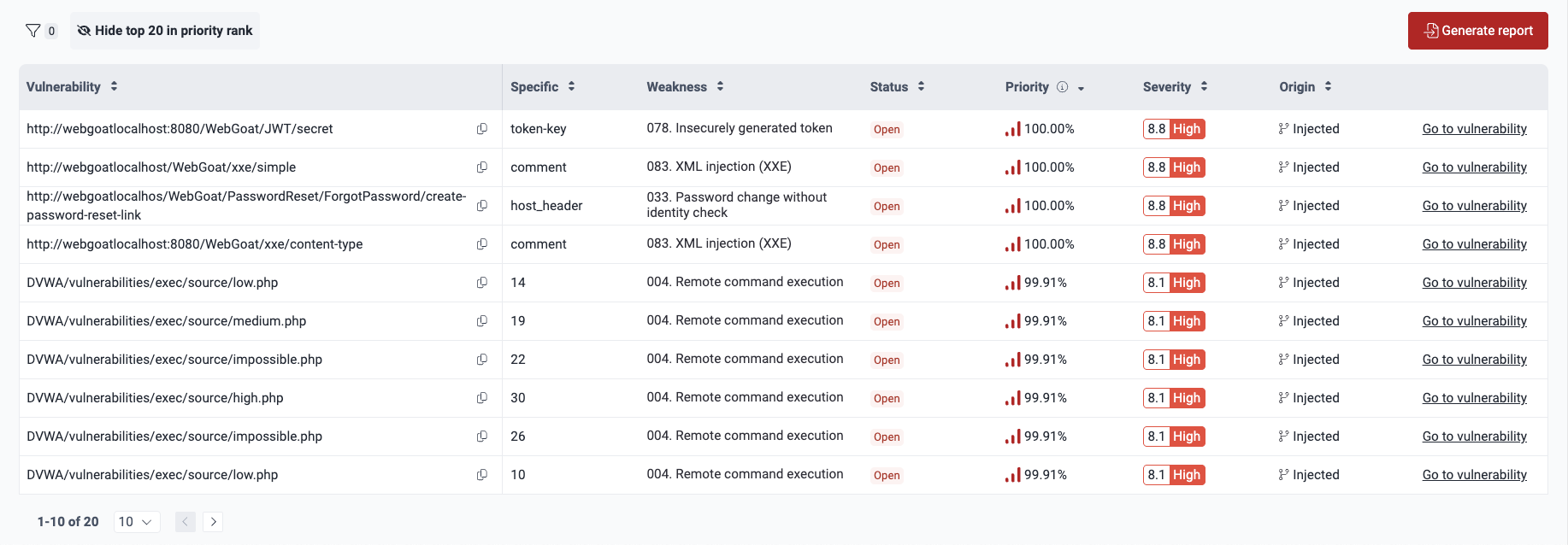
Hide and show columns in the Vulnerabilities table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager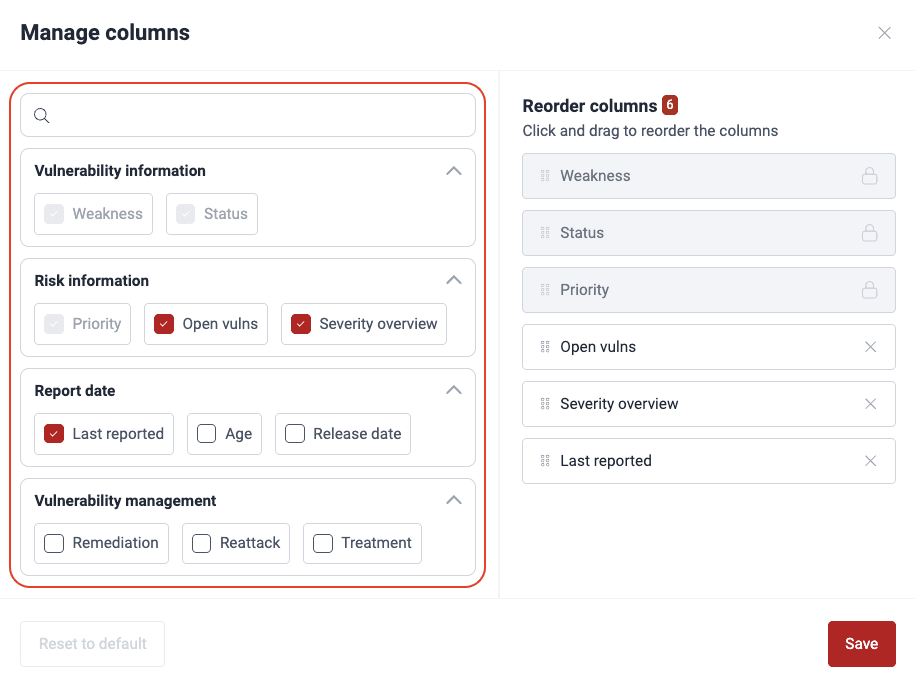

 Note: Your preferences for which columns to see persist across Vulnerabilities sections within your groups.
Note: Your preferences for which columns to see persist across Vulnerabilities sections within your groups.Reorder columns in the Vulnerabilities table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager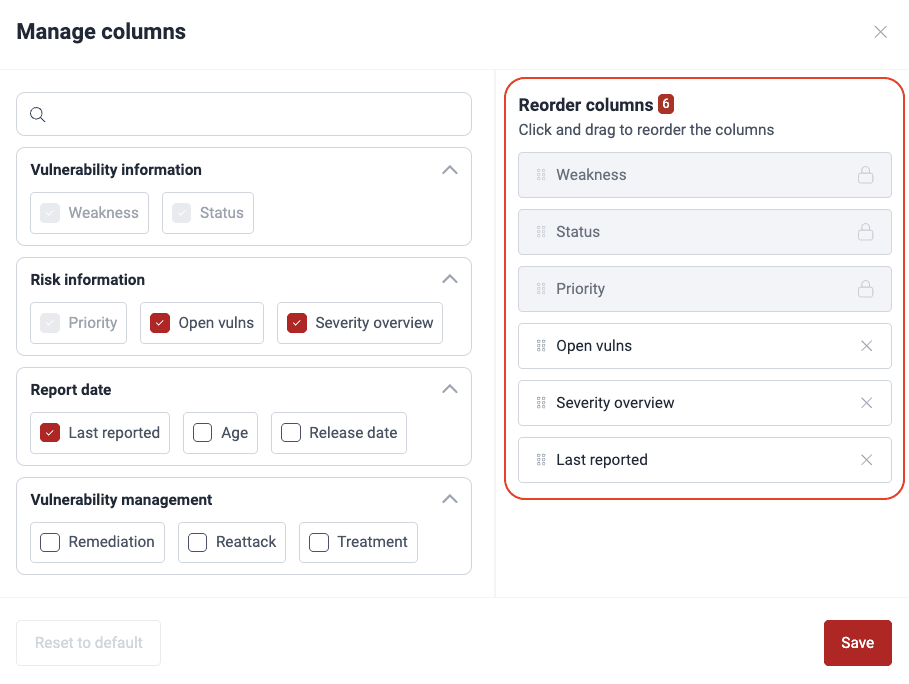
 Note: Your column order preferences persist across Vulnerabilities sections within your groups.
Note: Your column order preferences persist across Vulnerabilities sections within your groups.Generate reports
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group Manager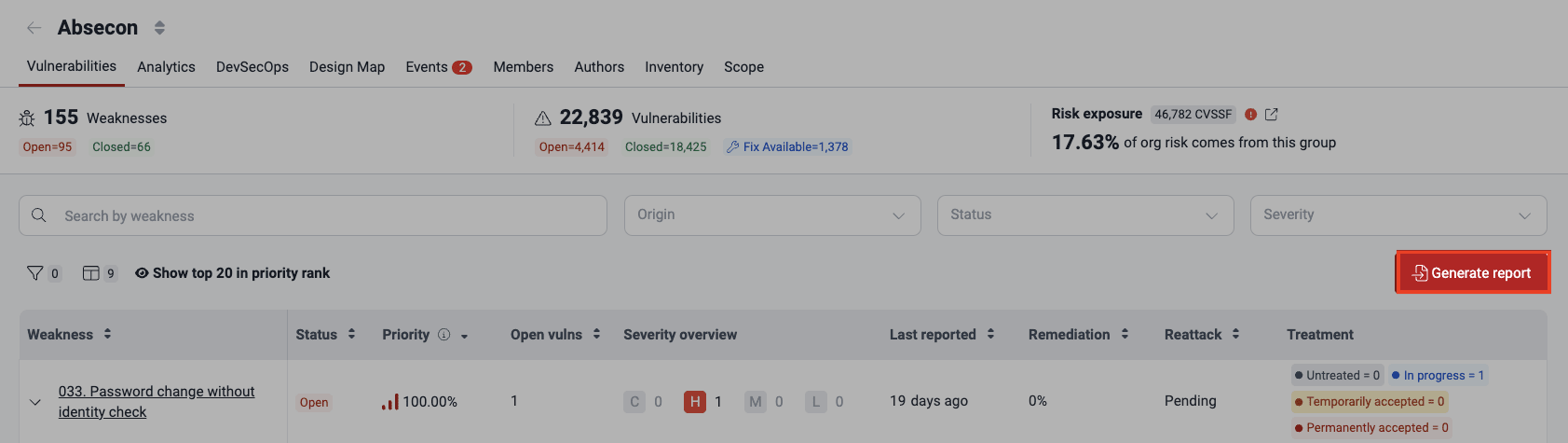

See where vulnerabilities are located
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
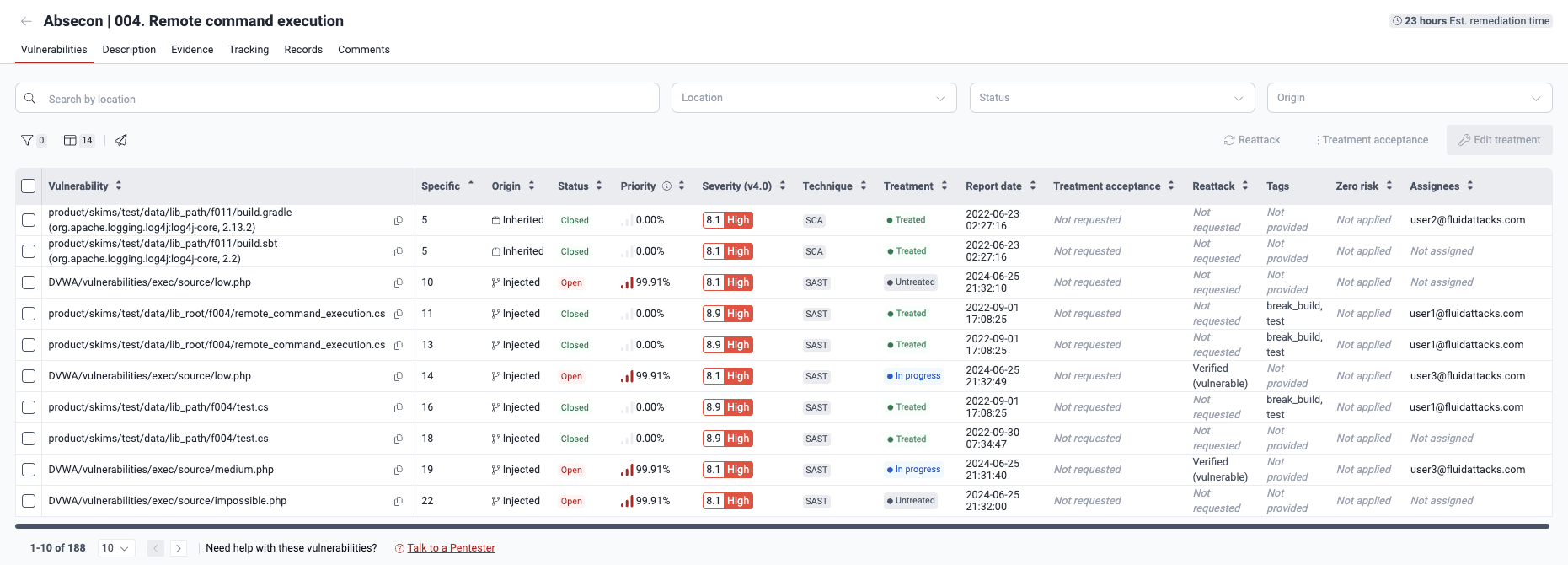
- Vulnerability: The found vulnerability, identified by its file path
- Specific: The exact lines of code, inputs (e.g., password fields) or ports where the vulnerability was found (thus the repetition of files in Location sometimes)
- Origin: Whether the vulnerability is Inherited (present in third-party code) or Injected (present in code owned by your team).
- Status: Indicates whether the vulnerability is Open (present) or Closed (no longer present) in the line of code, input or port
- Severity (v4.0): The Common Vulnerability Scoring System (CVSS) v4.0 score assigned to the vulnerability
- Priority: The percentile, relative to all vulnerabilities identified so far, occupied by the vulnerability. The priority score calculation depends on (a) your organization's prioritization policies based on the transitivity of the affected dependency, the phase of use of the vulnerable component, whether it is listed in CISA's KEV list, the EPSS, and the estimated time to fix; and (b) the result of (4^(CVSS-4)) / 4,096.
- Technique: The security testing technique used to detect the vulnerability, which can be one of these:
- SAST: Automated static code analysis
- DAST: Automated dynamic analysis
- SCA: Automated analysis of third-party dependencies
- SCR: Static code analysis done manually
- PTaaS: Dynamic analysis done manually
- RE: Reverse engineering of your system done manually
- AI SAST: AI-powered static code analysis
- Treatment: The defined treatment for the vulnerability:
- Untreated: The vulnerability treatment assignment is due
- In progress: The remediation of the vulnerability has been assigned to a member of your team
- Temporarily accepted: The vulnerability is accepted until a defined date
- Permanently accepted: The vulnerability is accepted indefinitely
- Treated: The vulnerability is no longer present
- Report date: The date and time when the vulnerability was reported
- Treatment acceptance: The status of a vulnerability acceptance request, which may be one of the following:
- Submitted: The initial status of the request while waiting for the decision of a Vulnerability Manager or Group Manager
- Approved: The request was approved by a member with any of the above roles
- Rejected: The request was denied by a member with any of the above roles
- Reattack: Status of reattack requests or outcomes, if applicable, which may be one of the following:
- Pending: Fluid Attacks is yet to communicate the outcome of the requested reattack
- On hold: The requested reattack is not possible until your team solves an event impeding testing
- Verified open: The reattack evidences the vulnerability is still present
- Verified closed: The reattack evidences the vulnerability is no longer present
- Tags: Any tags you or your team have added to identify the vulnerability
- Zero risk: Whether your organization has flagged the vulnerability as representing no risk to it
- Assignees: The individuals assigned to address the vulnerability



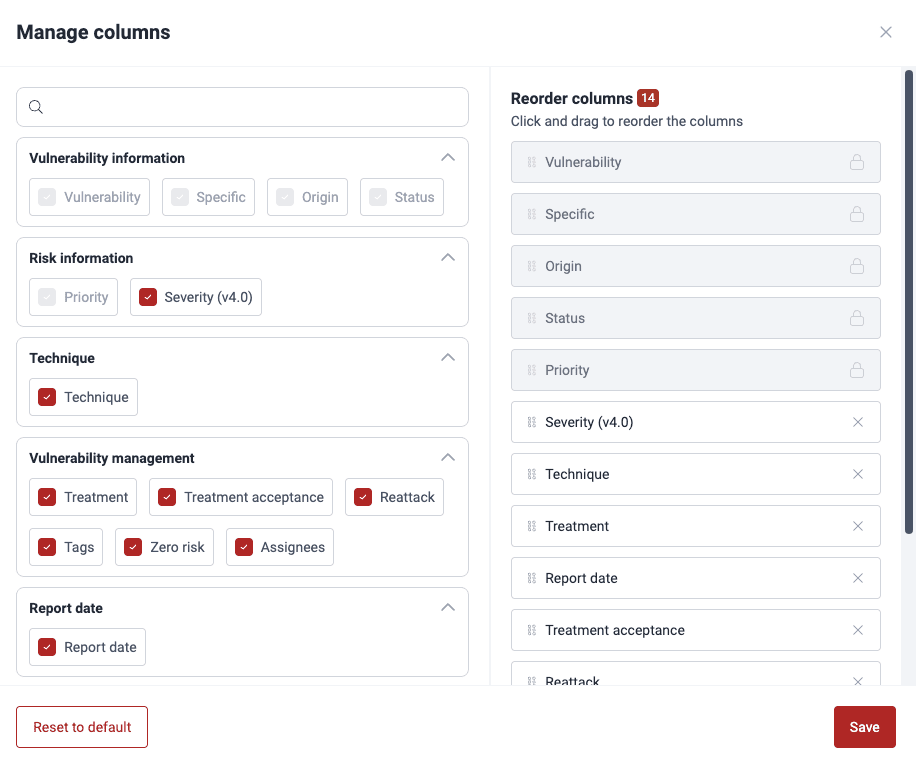

 Note: Your preferences for which columns to see persist across Vulnerabilities sections within your groups.
Note: Your preferences for which columns to see persist across Vulnerabilities sections within your groups.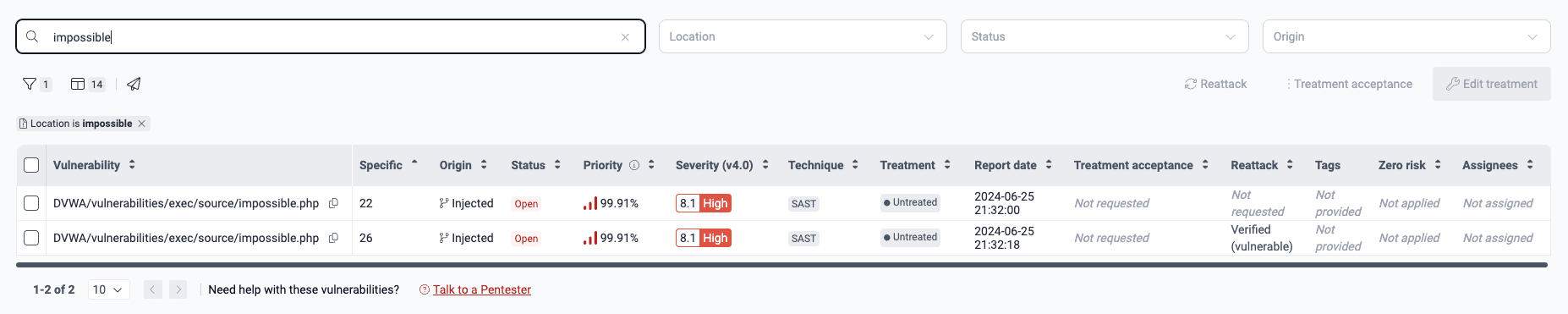

Click on the filters button

Select a filter option

Select values and apply filter


See inside a vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerYou can click on a vulnerability in the Vulnerabilities section to open a pop-up window with a header and multiple tabs: Details, Severity, Code (if applicable), Treatments (if applicable), How to fix, and Tracking. This window has a unique URL for easy sharing with team members or Fluid Attacks staff, which you can copy by clicking on the link icon.
- Latent: (a) The vulnerability is in a package declared in your code, but (b) the package is not imported.
- Potential: (a) The vulnerability is in a package declared in your code, (b) the package is imported by your application's code, but (c) the vulnerability is not necessarily the vulnerable function described in the CVE entry.
- Reachable: (a) The vulnerability is in a package declared in your code, (b) the related package is imported by your application's code, and (c) the vulnerability is the vulnerable function described in the CVE entry.
See the details of a specific vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager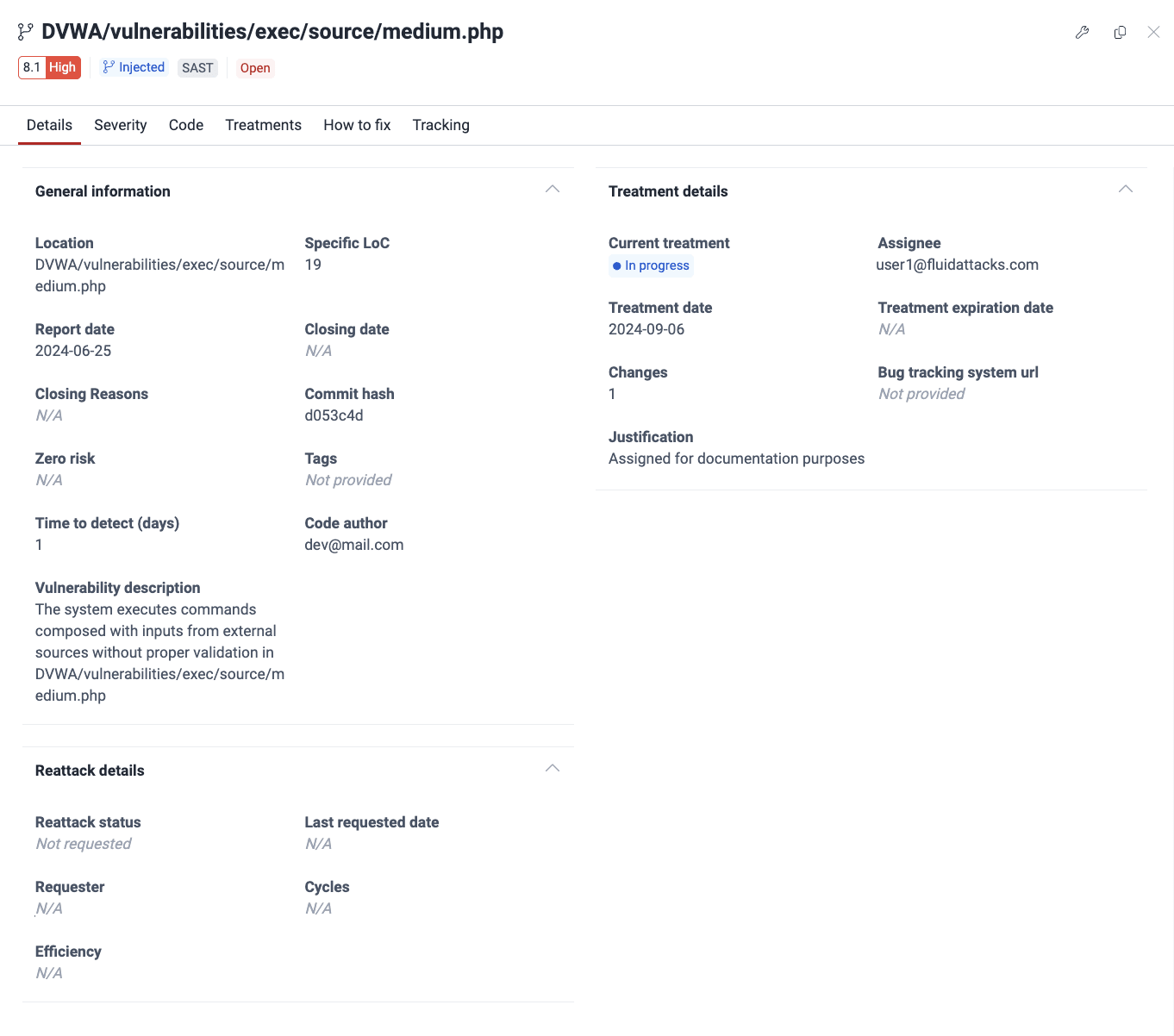
These are the details shown in this tab:
- General information:
- Location: The file path or environment URL
- Specific LoC/port/input: The specific line of code, port number, or input field affected
- Report date: The date the vulnerability was reported
- Closing date: The date it was verified the vulnerability is no longer present or, for another reason, its Status changed from 'Open' to 'Closed'
- Closing reasons: The reason the vulnerability's Status changed from 'Open' to 'Closed'
- Commit hash: ID of the commit that created the vulnerability
- Zero risk: Indicates if the Zero risk treatment has been applied to this finding (your organization requests this treatment if the finding poses no risk)
- Tags: User-defined tags for identifying the vulnerability
- Time to detect (days): The days it took to report the vulnerability since the commit that introduced it
- Code author: Email of the contributor whose commit presents the vulnerability in question
- Vulnerability description: Fluid Attacks' definition of the vulnerability
- Location: The file path or environment URL
- Reattacks:
- Reattack status: If applicable, the outcome of the last reattack request (for possible values, see above)
- Last requested date: The date of the most recent reattack request
- Requester: The email of the member who requested the last reattack
- Cycles: The total number of reattack requests for this vulnerability
- Efficiency: The percentage representing one positive reattack outcome (confirming the vulnerability was fixed) out of all the reattacks carried out
- Reattack status: If applicable, the outcome of the last reattack request (for possible values, see above)
- Treatments:
- Current treatment: The currently applied treatment for the vulnerability
- Assignee: The email of the member assigned to address the vulnerability
- Treatment date: The date the treatment was applied
- Treatment expiration date: The expiration date for a Temporarily accepted treatment
- Changes: The number of times the treatment of that vulnerability has changed
- Bug tracking system url: URL of the issue in your bug tracking system (BTS) related to this vulnerability
- Justification: The reason provided for applying the treatment
- Dependency: The name of the vulnerable package
- Transitivity: Whether the vulnerable file in your software is directly or indirectly related to the third-party component in question:
- Direct: The file in your project explicitly imports and uses the third-party dependency
- Transitive: The third-party dependency is required by your direct dependencies, but not directly imported by the file in your project
- Undeterminable: For this file, it is impossible by anyone to determine whether the dependency is direct or transitive
- Advisory ID: The associated Common Vulnerabilities and Exposures (CVE) identifier of the vulnerable version
- %EPSS: The likelihood of the vulnerability being exploited compared to that of all other known vulnerabilities
- Stage: The stage(s) in which your project depends on the third-party dependency:
- Build: Your file depends on the third-party component only in the software development stage
- Run: Your file depends on the third-party component in the live production environment
- Reachability: Whether the function related to the vulnerability is called by your application's code (see a description of the possible values above)
- Version status: Whether you are using the dependency in its latest version or a newer one is available (it also indicates the specific used version and the latest one)
- Affected version: The vulnerable dependency version
- CPEs: The string following the Common Platform Enumeration (CPE) for identifying the dependency
- Namespace: Identifier indicating the supplier organization or project for the entry
- Advisory URLs ([#]): Reference URLs (e.g., URL of the vulnerability advisory)
- KEV: Whether the related vulnerability is in CISA's Known Exploited Vulnerabilities Catalog, meaning it has been exploited in the wild
Learn the severity of a specific vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager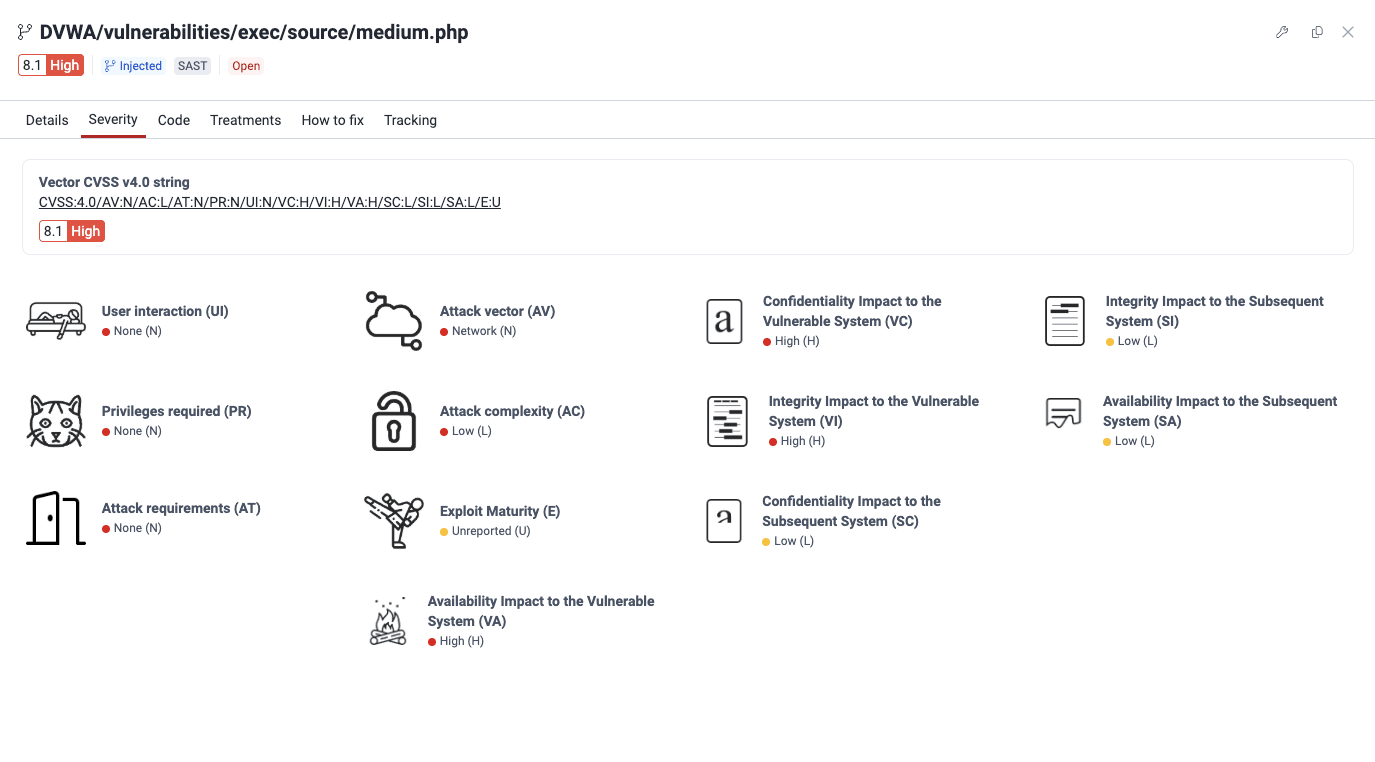
These are the details shown:
- Vector CVSS v4.0 string: The values used to derive the score represented textually
- The calculated severity score and its corresponding qualitative rating
- The severity score breakdown showing the values for each metric along with a visual representation of the value


See the vulnerable line of code
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager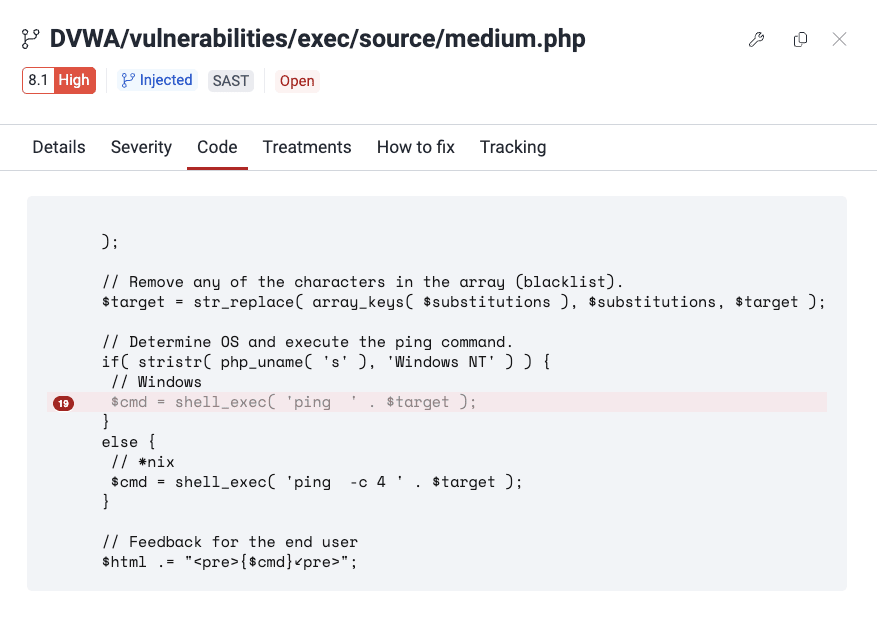
Edit treatment for a vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager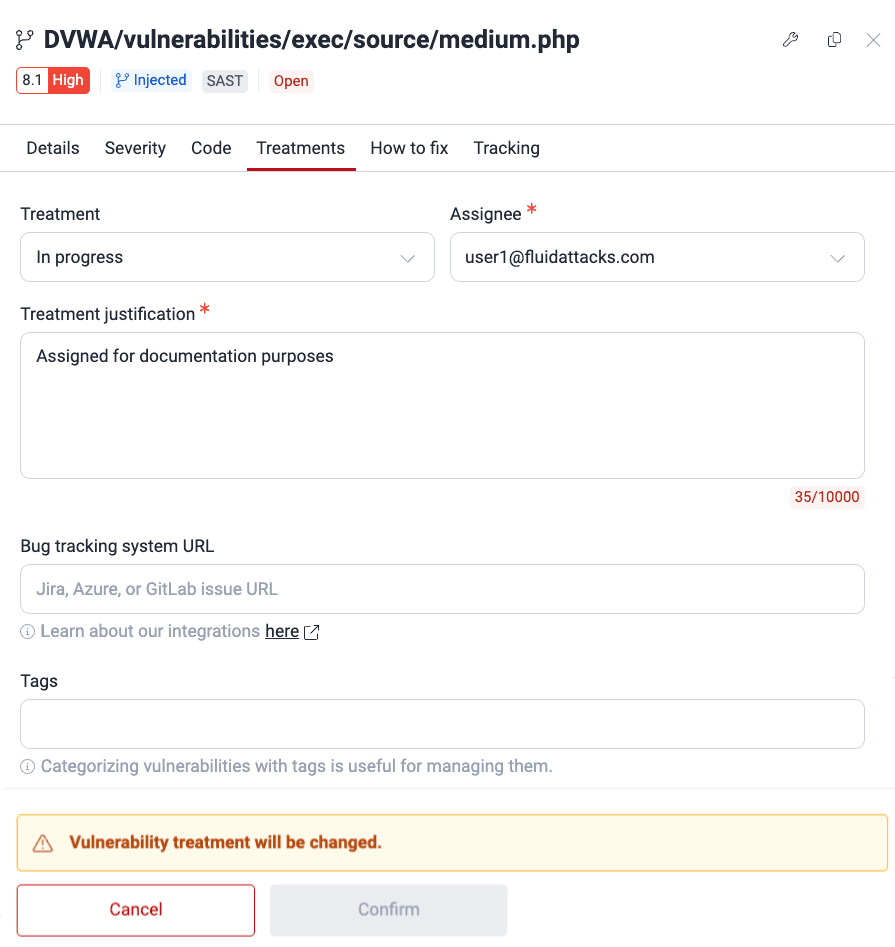
Get a custom guide to fix the vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager

 ) and let Fluid Attacks' Custom fix feature create this useful resource for you to plan the remediation of the vulnerability in question. Bear in mind that this feature is not available for some vulnerabilities.
) and let Fluid Attacks' Custom fix feature create this useful resource for you to plan the remediation of the vulnerability in question. Bear in mind that this feature is not available for some vulnerabilities.
Click the fix button
Get fixing guide
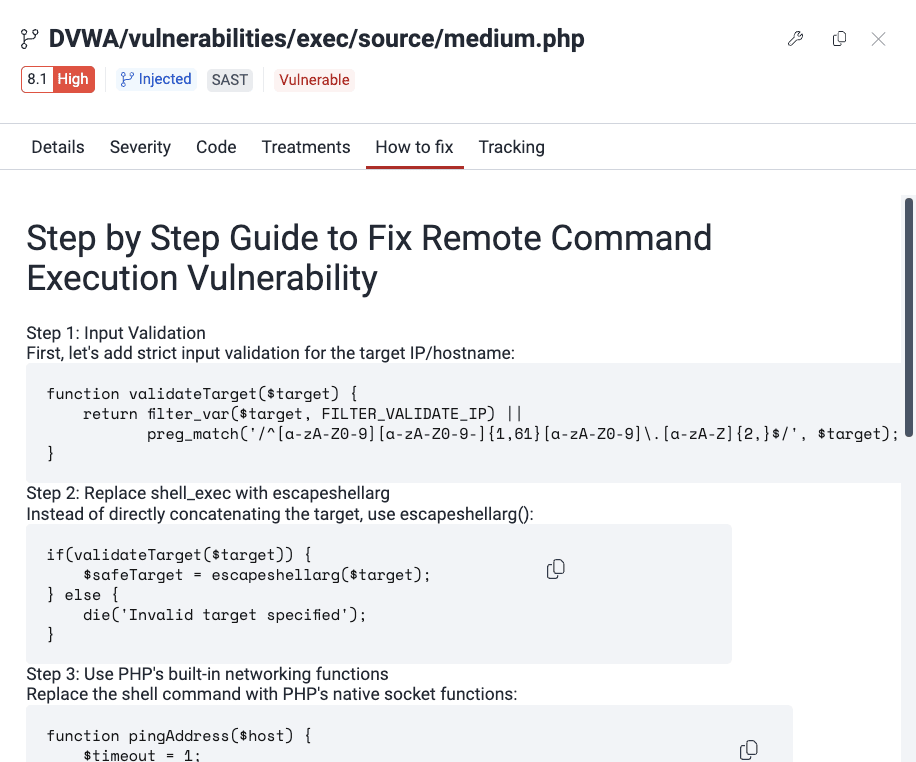
Get an automatic fix for the vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager

 ). Clicking on the button enables a pop-up window that displays requirements for using the feature and a link to download the extension.
). Clicking on the button enables a pop-up window that displays requirements for using the feature and a link to download the extension.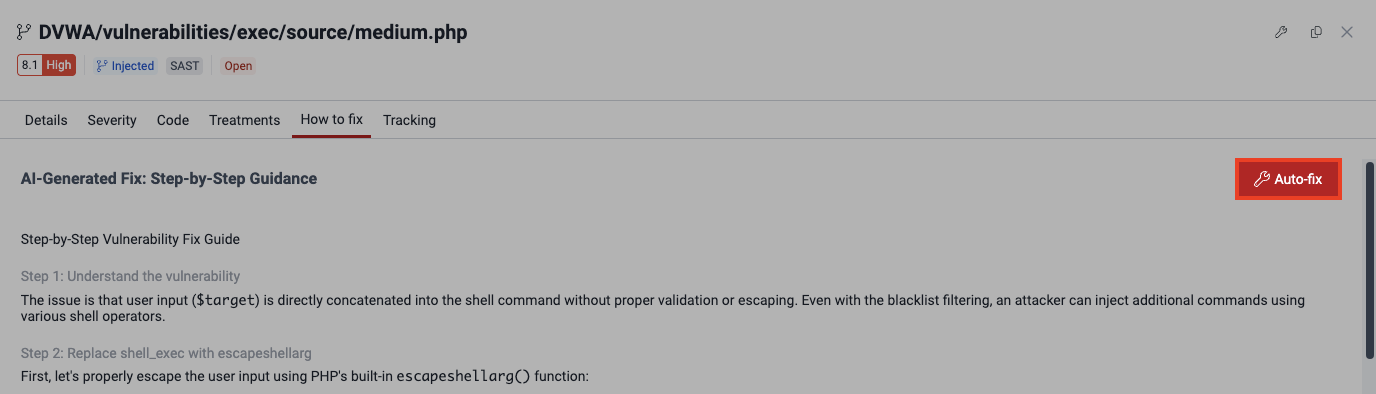
See the recommended dependency version
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerSee the history of a specific vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager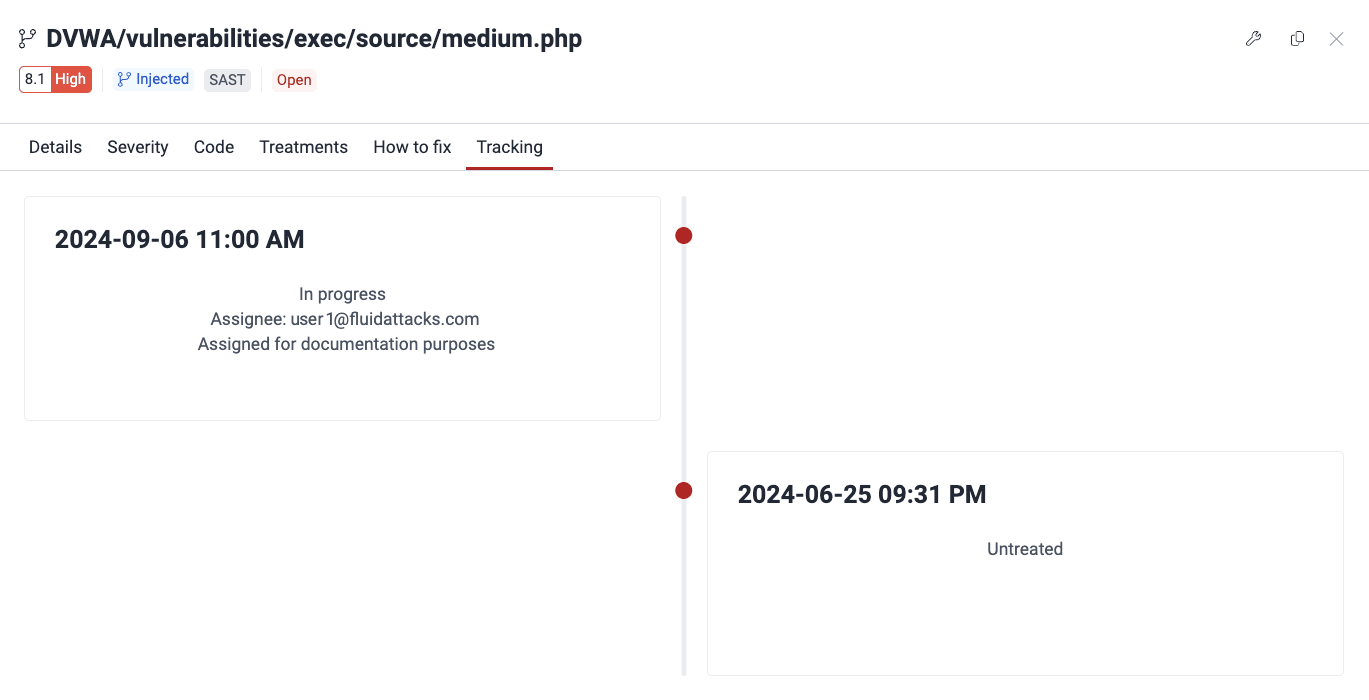
Get the link to share the details of a vulnerability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager ).
).

See the description of vulnerabilities
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerThe Description section provides definitions and relevant characteristics to more clearly understand the issues and possible fixes.
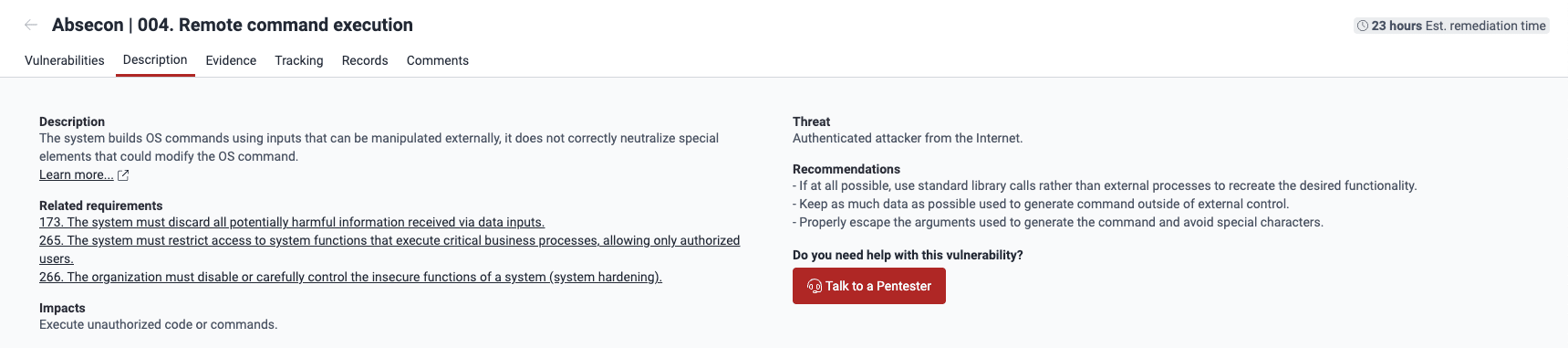
- Description: Fluid Attacks' definition of the weakness in question
- Related requirements: The security requirements, according to Fluid Attacks' classification, that may have been violated
- Impacts: What an attacker can achieve exploiting the vulnerability
- Threat: The attack vector an attacker has to follow and the privileges they require to exploit the vulnerability
- Recommendations: Advice for remediating the vulnerability
- Do you need help with this vulnerability?: Link to schedule a video meeting to discuss the vulnerability with one of Fluid Attacks' pentesters
See evidence of exploitability
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager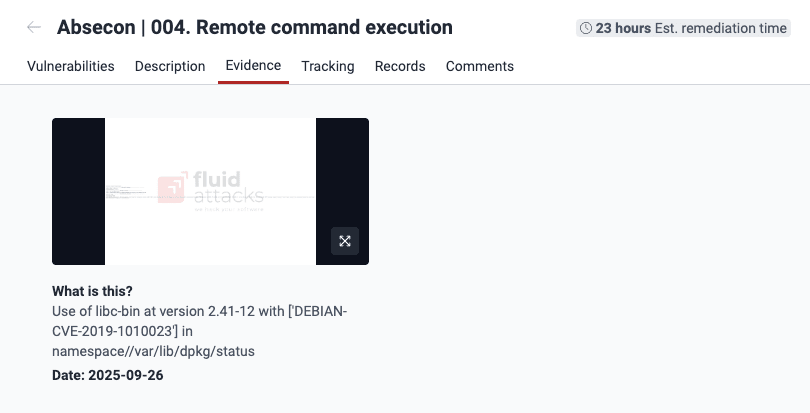
See the timeline of vulnerabilities
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
See affected records
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager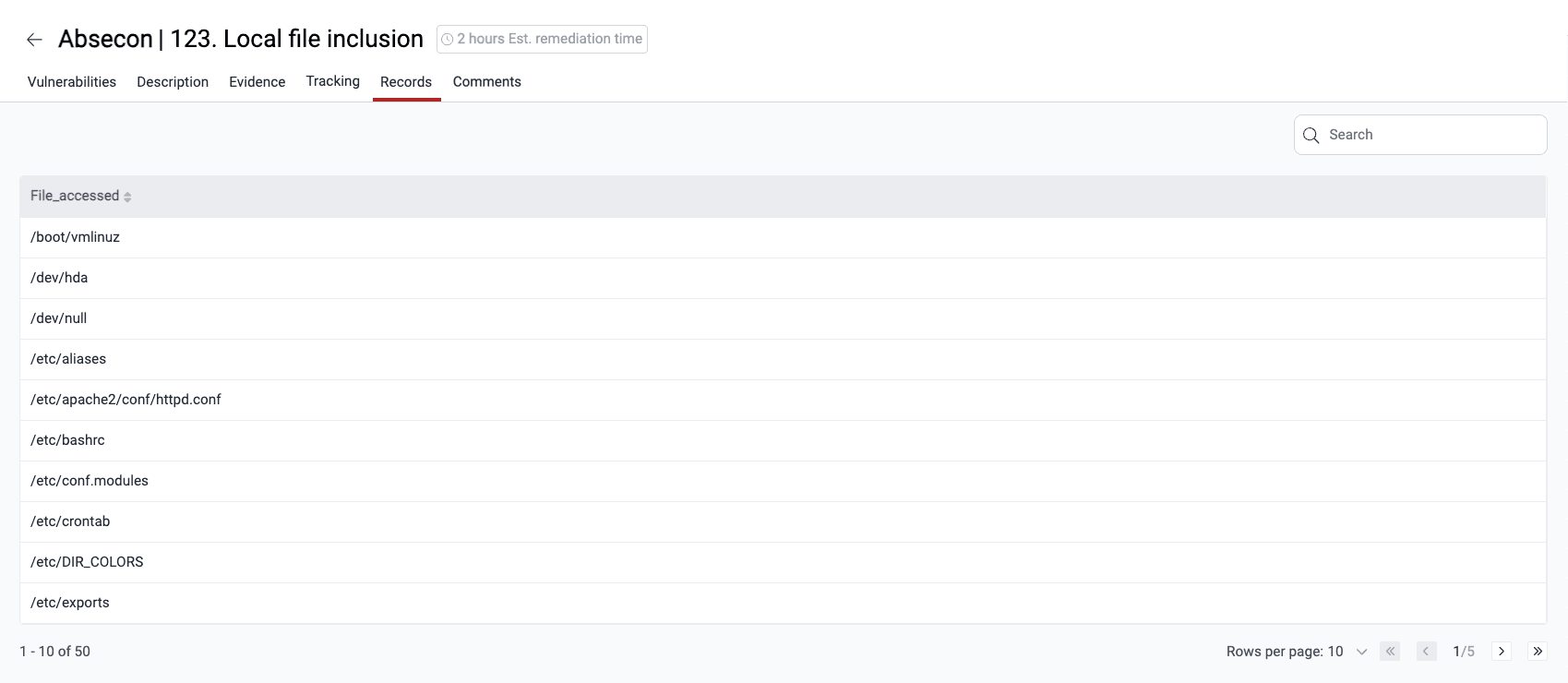

Comment on vulnerabilities
 Plan required: Advanced
Plan required: Advanced
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerThe Comments section is a forum-like space for discussions between your team and Fluid Attacks about the vulnerabilities in question. Any member can post a new thread or reply to an existing one. To learn more about this help option, read Post comments.


Notify of a vulnerability
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group Manager- Access the group where the target vulnerability was detected.
- In the Vulnerabilities section, click on the associated weakness.
- In the Vulnerabilities section, click on the notify button (
 ).
). - In the pop-up window, confirm the delivery by clicking Notify.

The notification is then sent to members who have Vulnerability alert enabled.
Request reattacks
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager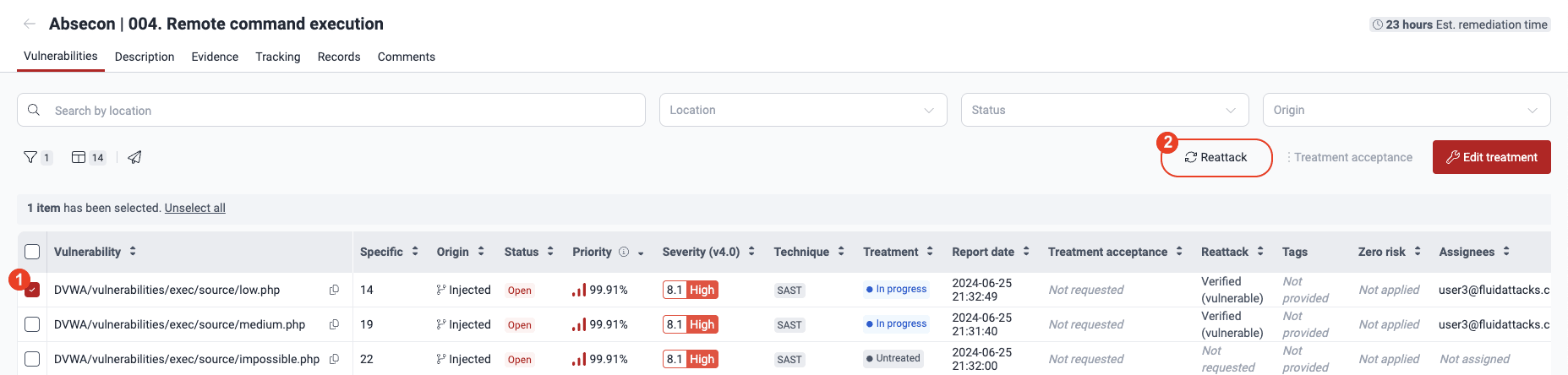
Edit treatment, assignee, BTS link and more
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group Manager
- Go to Vulnerabilities by clicking on a weakness name.
- In the table, select the checkbox on the left of the vulnerability that you need to edit.
- Click the Edit treatment button.
- Make the necessary changes in the form. Treatment and Assignee can only be modified by Vulnerability Managers and Group Managers. (For the descriptions of the fields, read Assign treatments.)
- Click on Confirm to apply the changes.
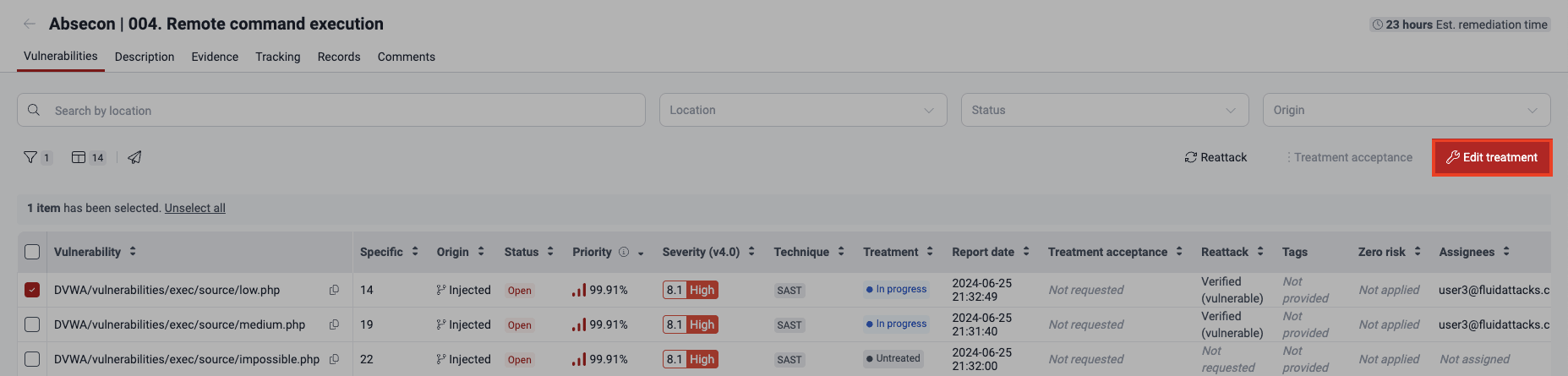

Approve vulnerability acceptance requests
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group Manager
 Free trial
Free trial