See safe dependency versions
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager
Fluid Attacks identifies the vulnerable dependencies you use and informs you what versions to upgrade to. The suggestion provided is the closest version that fixes the reported vulnerability while preventing breaking changes.
Follow these steps:
Enter the group where the vulnerability is located and click on the weakness name.
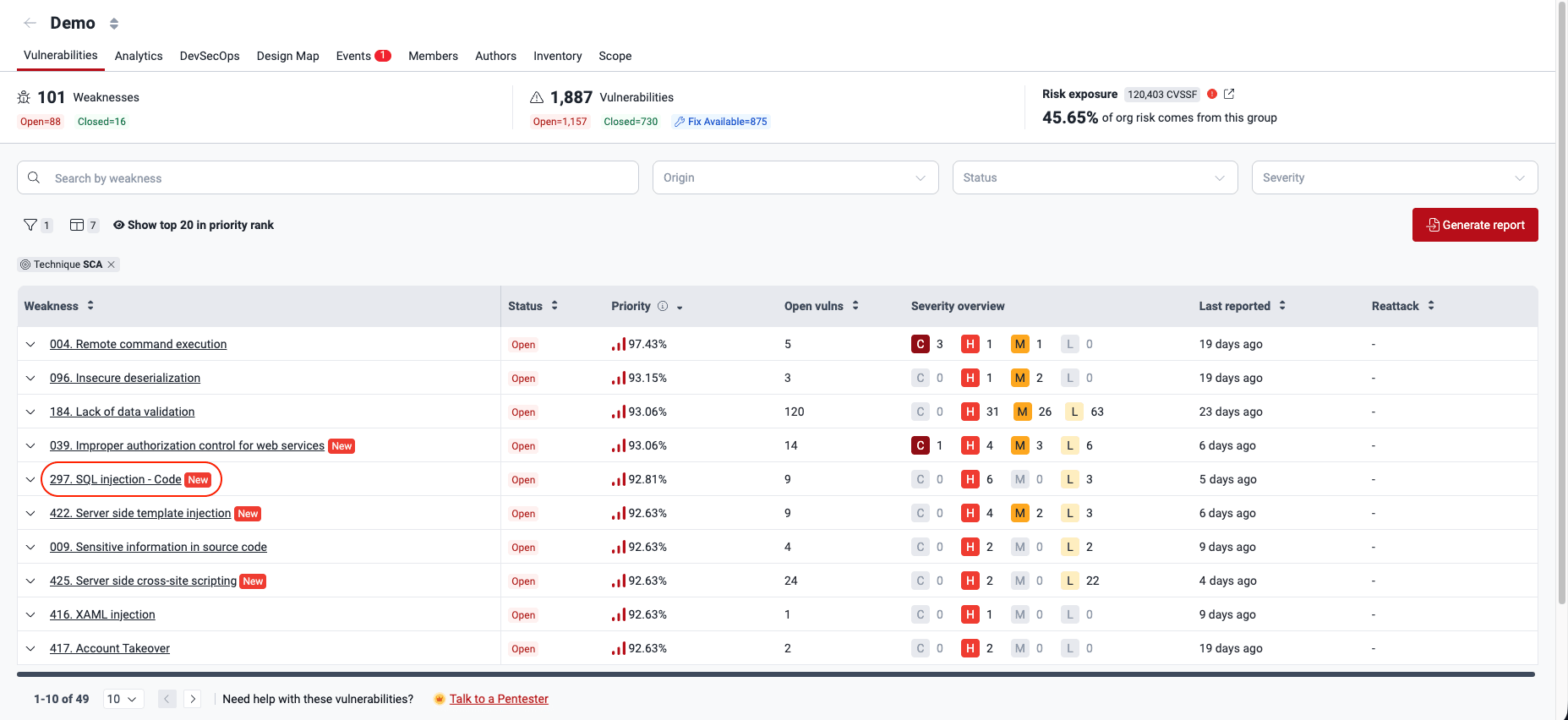
From the table, click on the third-party software vulnerability of your interest.
-
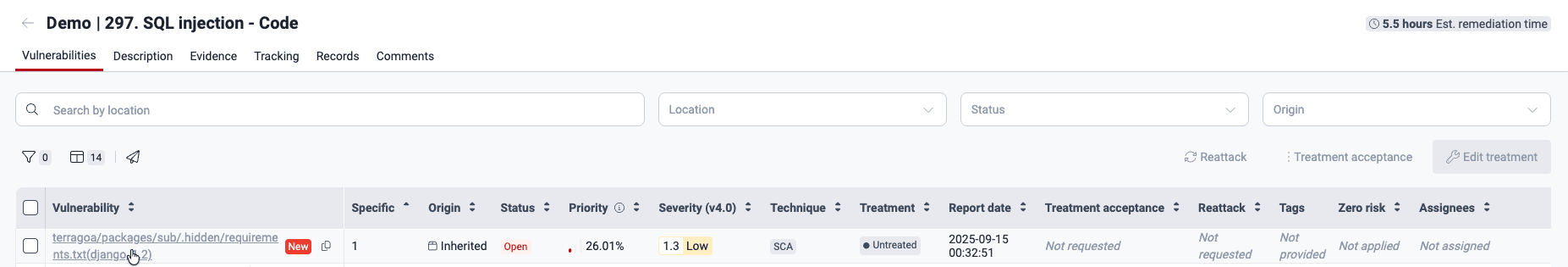
Switch to the How to fix tab in the pop-up window.
-
Read the information on what version to upgrade to.
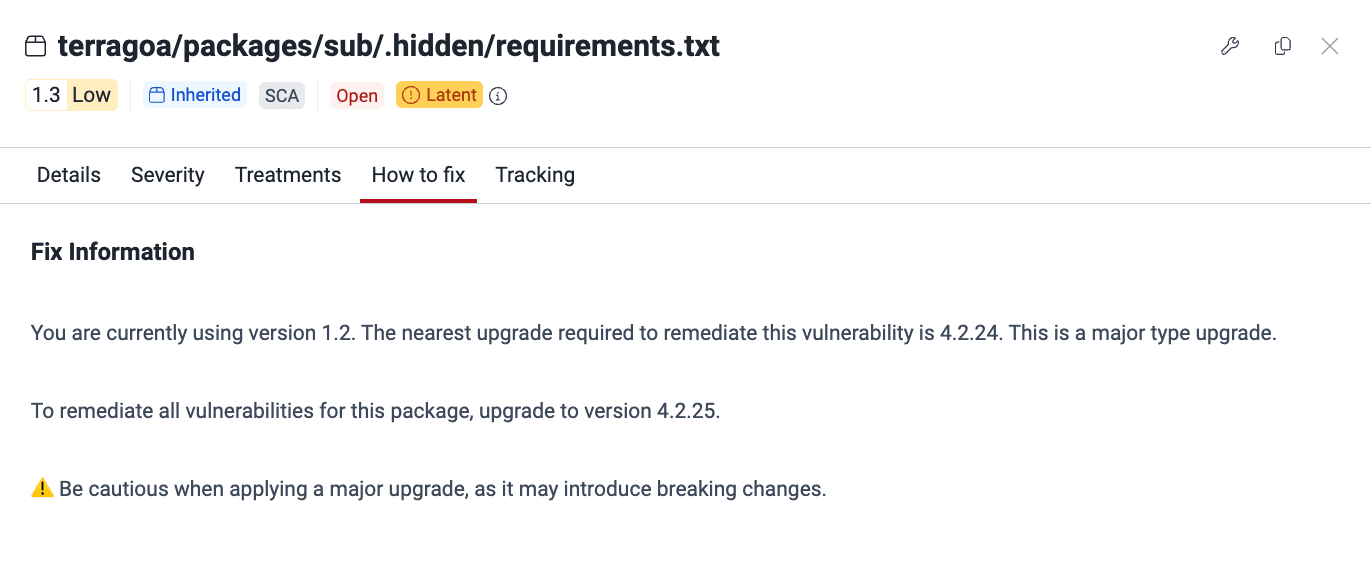
When you have upgraded your dependencies to their safe versions, run a reattack.