Enable and disable notifications
- Click on the user menu located at the top-right corner of your screen.
- Select Notifications from the menu.
- In Notification configuration, toggle the on/off button next to a notification type to enable or disable its delivery to your email.


The following are the descriptions of the types of notifications offered by Fluid Attacks.
Notifications for clients
CI Gate token alerts
CI Gate token
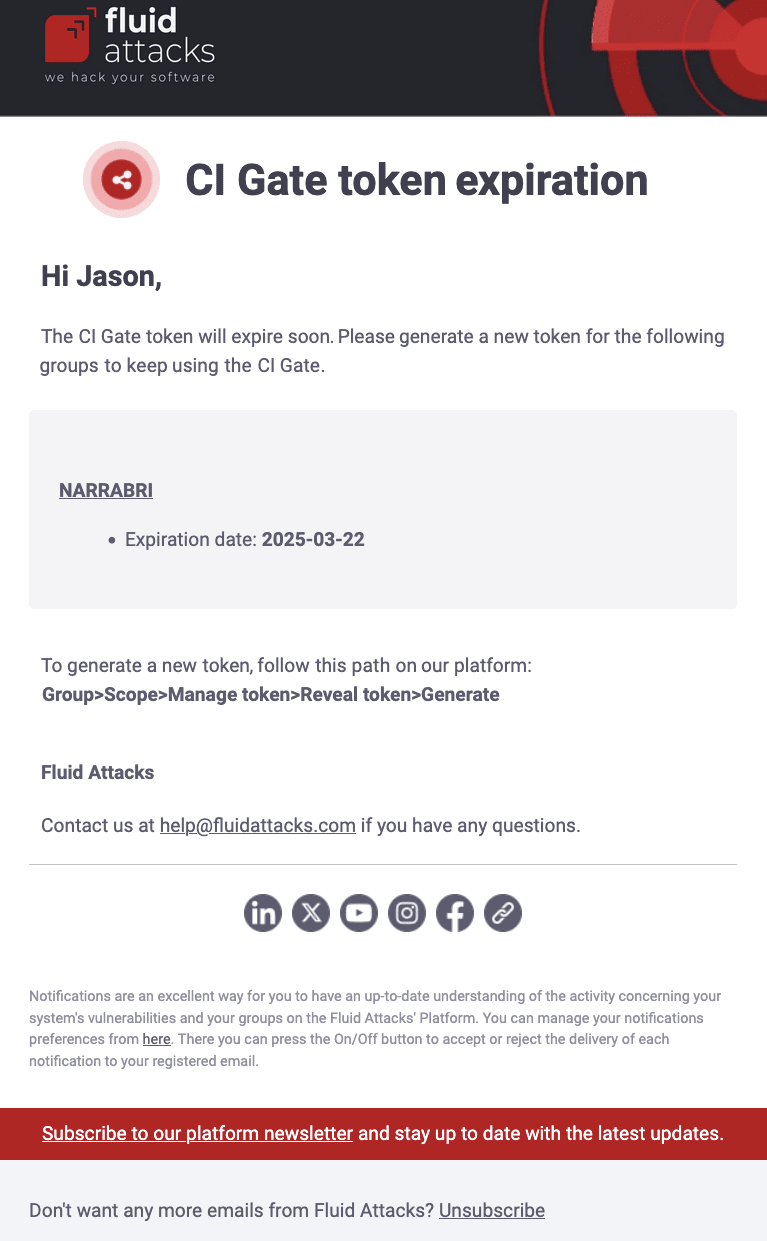
CI Gate token expiration
If CI Gate token alerts are enabled, you receive an email seven days before a group's CI Gate token expires, reminding you that the token must soon be updated. The message informs you of the group's name, the token's expiration date and the path on the platform to update the token.
Event digest
If enabled, you receive an email listing all the events generated the previous day in all the groups you have access to. Events are situations from your side that prevent security testing of part of the scope or its entirety. This notification also shows any new comments added in the events' Consulting sections.
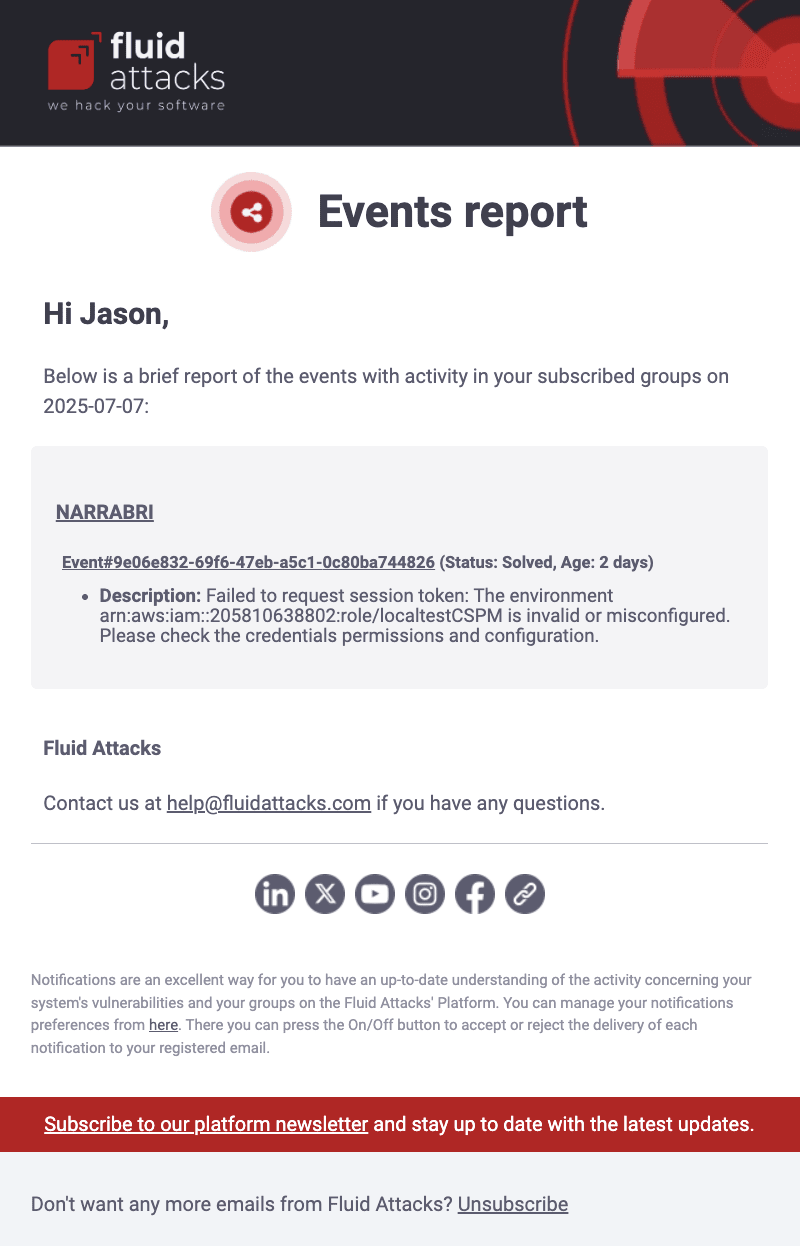
Event alerts
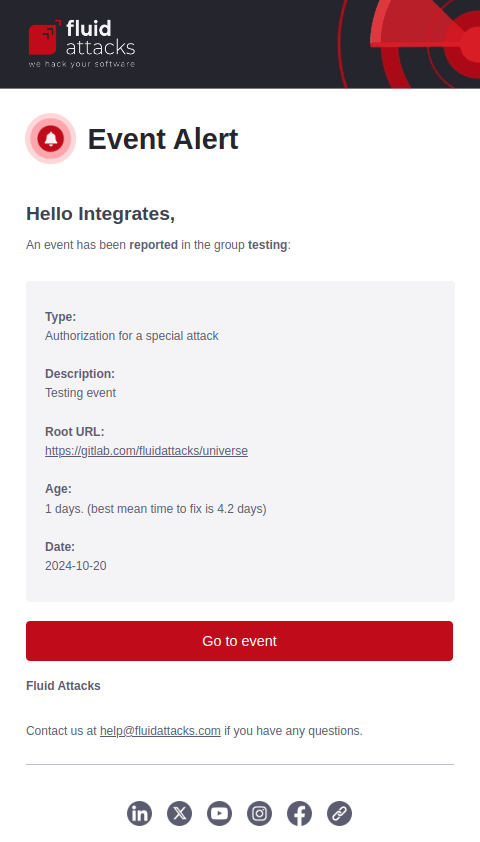
When enabled, you are notified via email about new events reported and solved within a group. The notification of unsolved events includes details such as event type, creation date and days it has remained unsolved. Additional emails are sent at specific intervals (seven days and 30 days) if the event remains open, and a final email is sent when the event is solved. The latter includes your team's description of the solution given. Each notification provides a direct link to the event report on the platform.
Files updates
 Role required: Group Manager
Role required: Group Manager
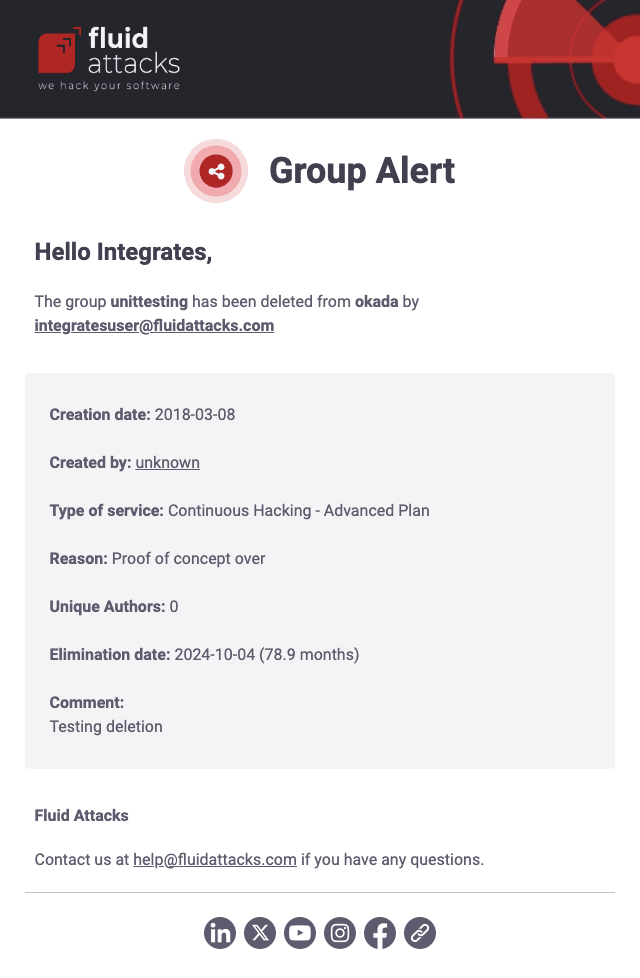
Group information updates
Group alert
If the Group information updates notification is enabled, you receive an email when your group is removed from the platform. The message shows relevant information such as the email of the member who deleted the group, the subscription plan and the reason for deletion.
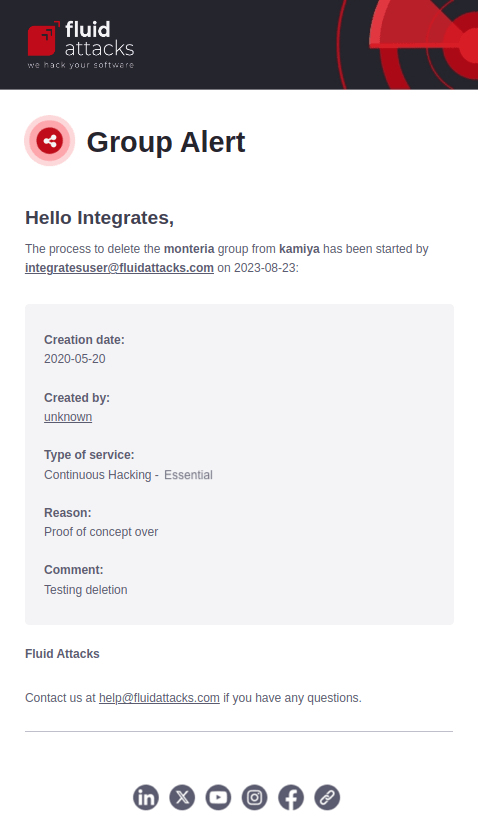
When the group deletion is confirmed, you get an email announcing it. The details provided are the same as those in the previous email.
Updated group information
Policies updated
Newsletter
Consulting alerts
 Plan required: Advanced
Plan required: Advanced
Portfolio updates
Inactivity alert
If enabled, you receive an email if you have not logged into the platform for three weeks.

 Note: Regardless of their role, a member is automatically removed after 90 days of inactivity.
Note: Regardless of their role, a member is automatically removed after 90 days of inactivity.Repository updates
Environment alert
 Role required: Group Manager
Role required: Group Manager
Time to register environments
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group Manager
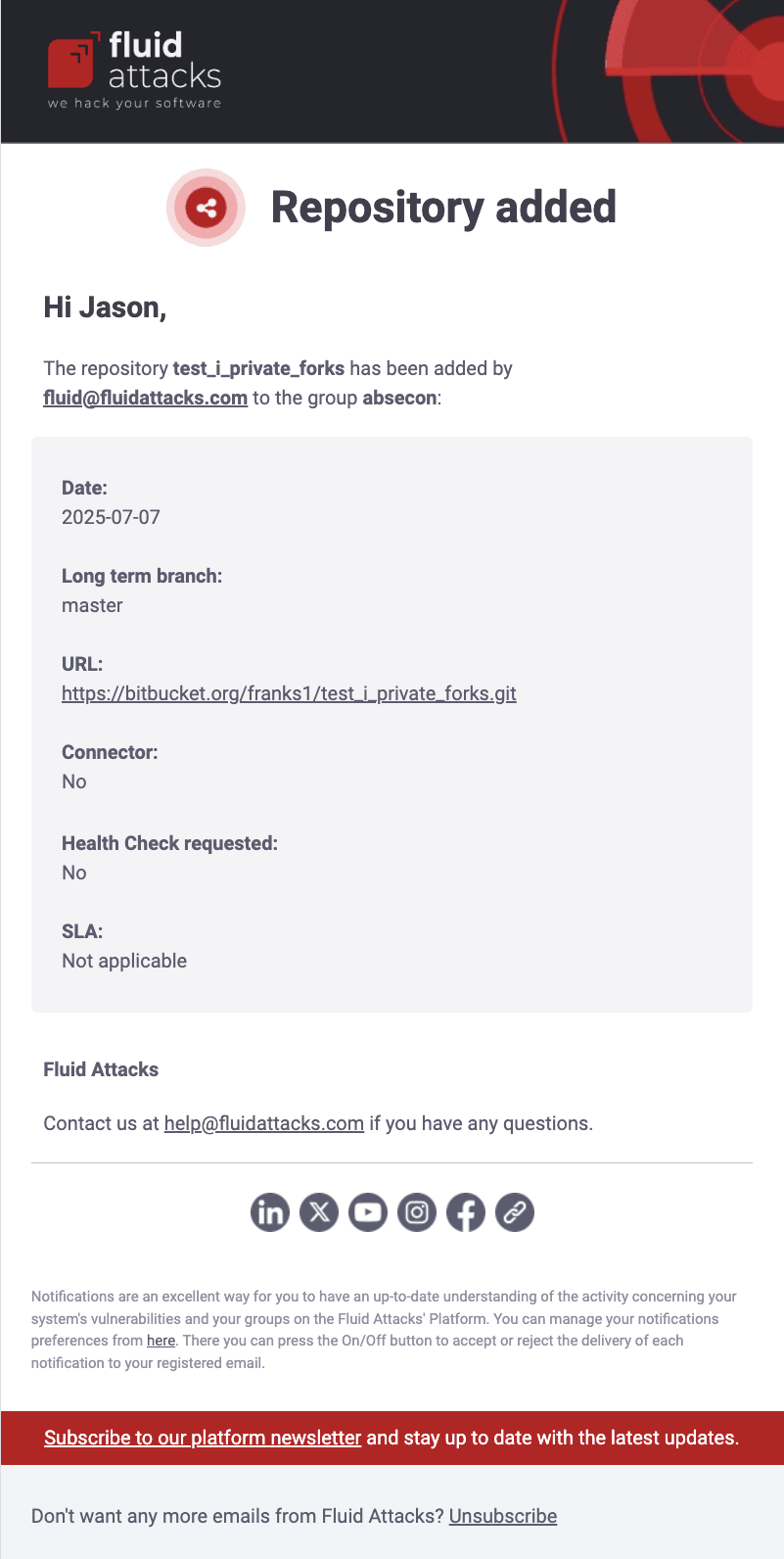
Repository added
 Role required: Group Manager
Role required: Group ManagerWhen Repository updates is enabled, a notification is sent to your email whenever a new root is added in your group's Scope section. It displays the email address of the member who added it and some relevant information about this target of evaluation, such as the evaluated branch and whether Health Check (i.e., manual testing of the preexisting source code) was requested.
Repository status
 Role required: Group Manager
Role required: Group Manager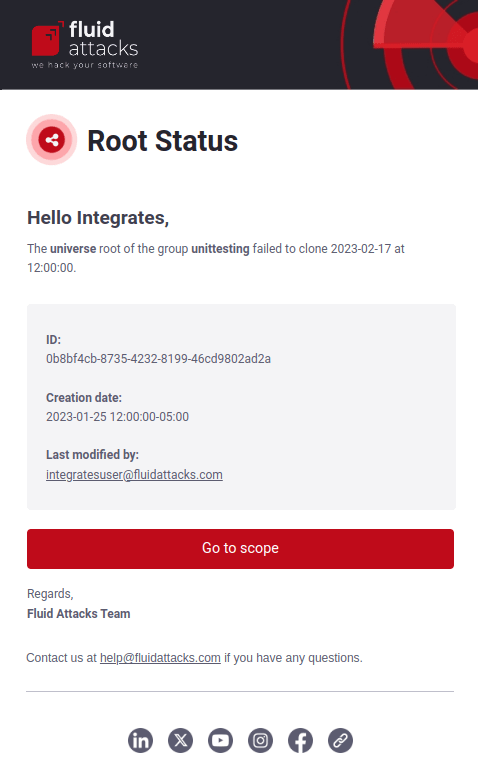
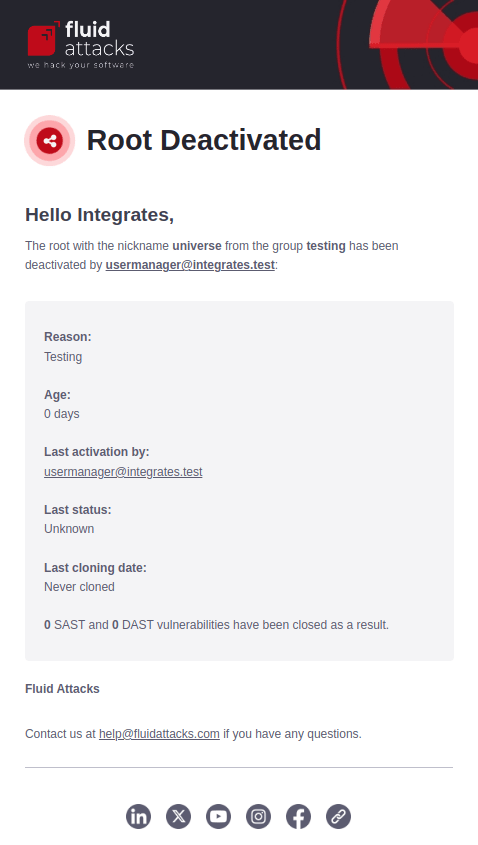
Repository deactivated
If Repository updates is enabled, you receive this notification when a root is deactivated. It includes details such as the reason for deactivation, how long the root was registered on the platform, and any vulnerabilities found in it with SAST and DAST scans that are closed as a result (i.e., marked with the 'Safe' Status).
Repository moved
If Repository updates is enabled, you receive this notification if a root is moved to a different group. The email specifies which root was moved, its original location and its new location.

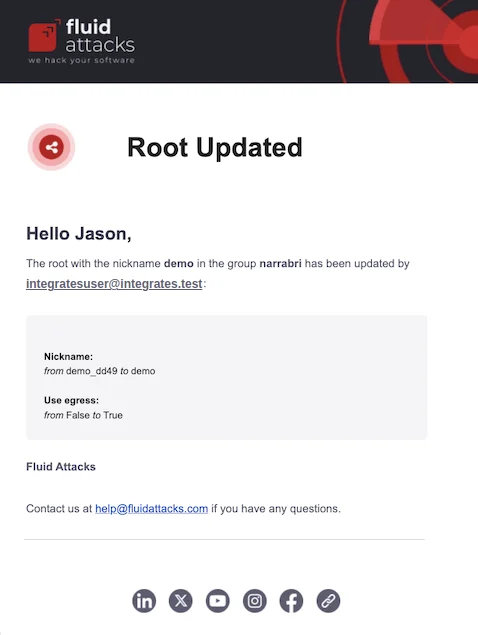
Repository updated
This notification is triggered when Repository updates is enabled, and an existing root in the Scope section is edited. The email informs of the nickname of the root that was modified, the email of the member who modified it, and the modifications, specifying the previous and current values.
Services updates
 Role required: Group Manager
Role required: Group Manager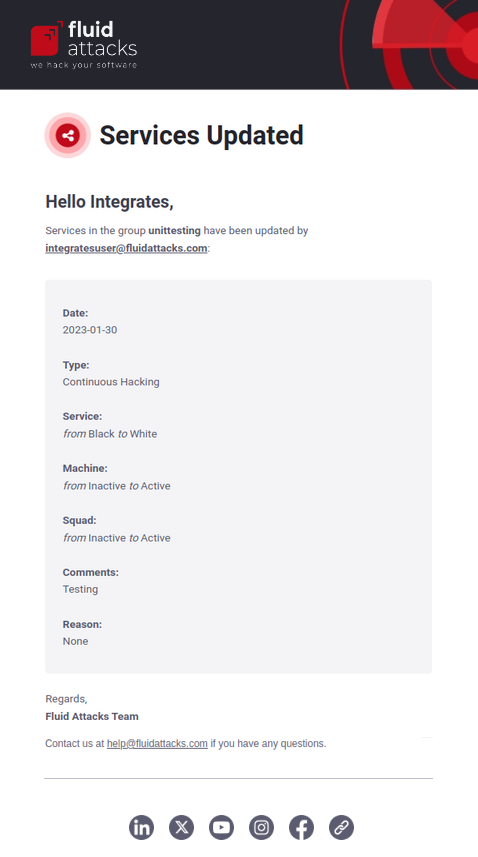
Member update

Treatment updates
Treatment report
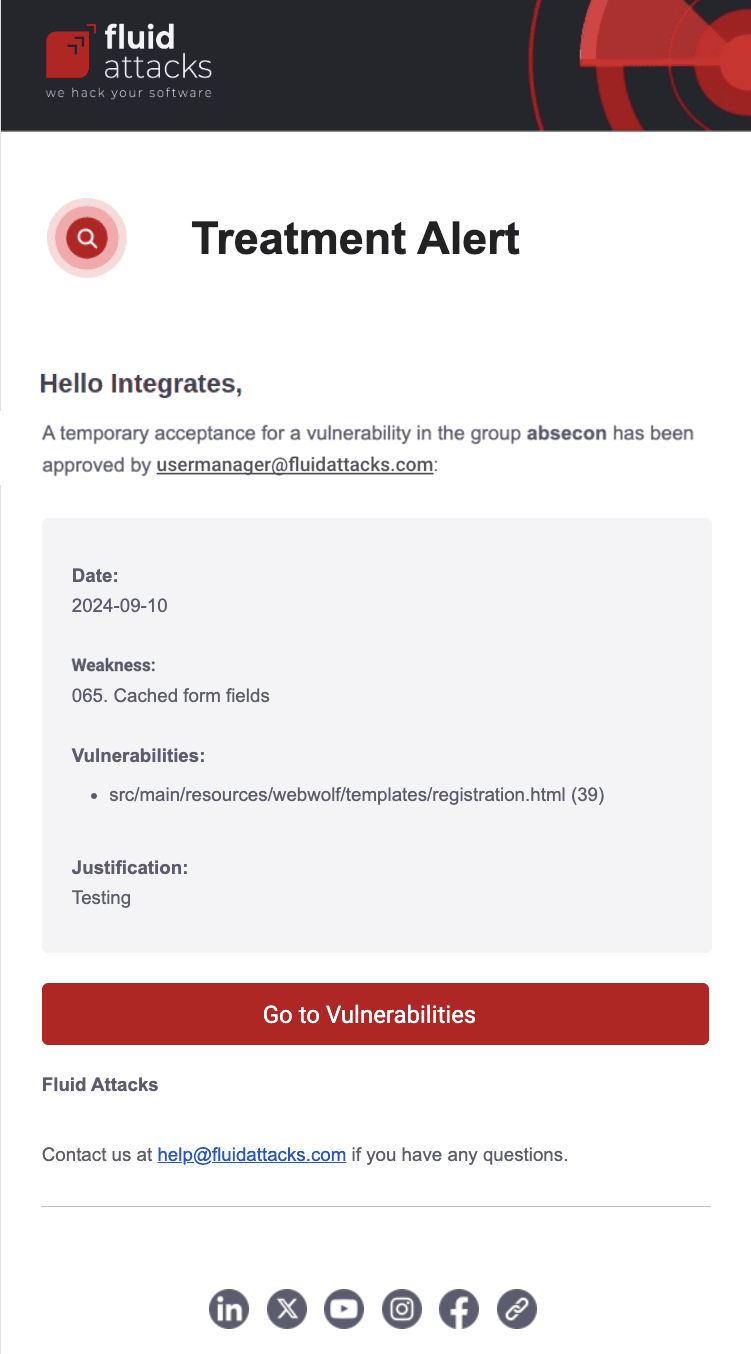
Updated treatment
When enabled, you are notified via email whenever new treatments for vulnerabilities are defined or existing ones are modified within your organization. The notification indicates the type of vulnerability, the group where it was reported, who was assigned, and the specific treatment applied. It also provides a direct link to the vulnerability type on the platform.
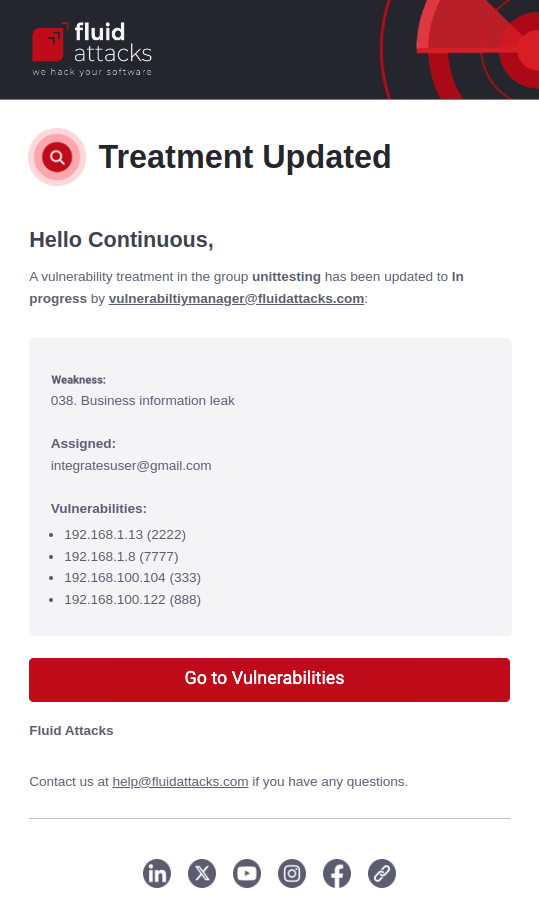
Vulnerabilities expiring
When you have Treatment updates enabled, you receive daily emails for seven days until a Temporarily accepted treatment expires for vulnerabilities in your groups. The message indicates the name of the group, the type of vulnerability, the vulnerability's location, and the days remaining for expiration.
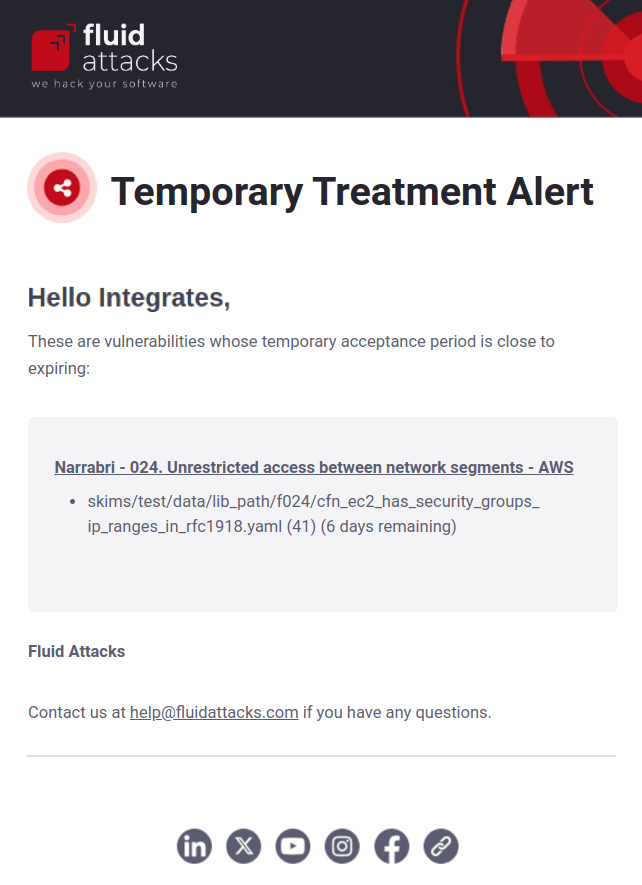
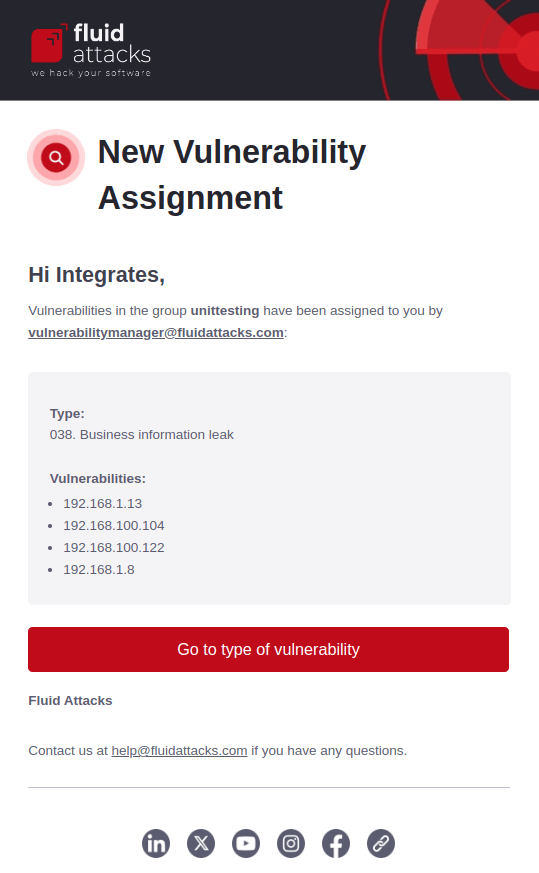
Vulnerability assignment alerts
If enabled, you receive an email when vulnerabilities are assigned to you. This notification includes the name of the type of vulnerability, the vulnerability's location(s), the group where it was reported, and a direct link to the type of vulnerability on the platform.
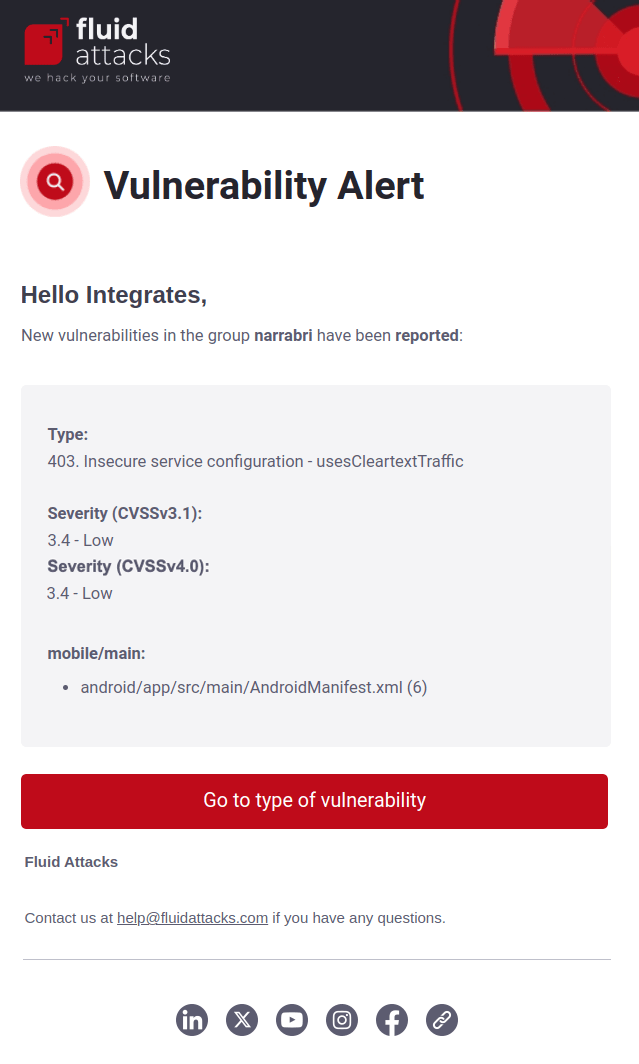
Vulnerability alert
If enabled, you receive emails when Fluid Attacks identifies (or your team remediates) a vulnerability in your system with a CVSS score equal or higher than the one you specify in the Minimum severity field. The notification includes the name of the group, the type of vulnerability reported, its severity according to the CVSS v3.1 and v4.0, and a direct link to the type on the platform.
Not configurable
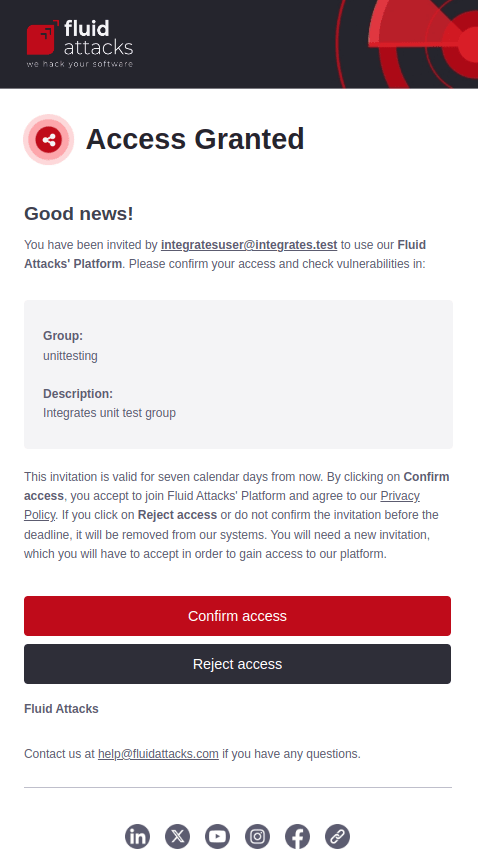
Access granted
To join an organization or group on the platform, you need an invitation from an Organization Manager or a Group Manager, respectively, which you must confirm. The invitation email contains the inviter's email address, the organization's or group's name and description, and a link to Fluid Attacks' Privacy Policy. By confirming the invitation, you agree to the Privacy Policy. You have seven calendar days to confirm before the invitation expires.
 Note: This notification is also the one sent to authors when invited to join the platform.
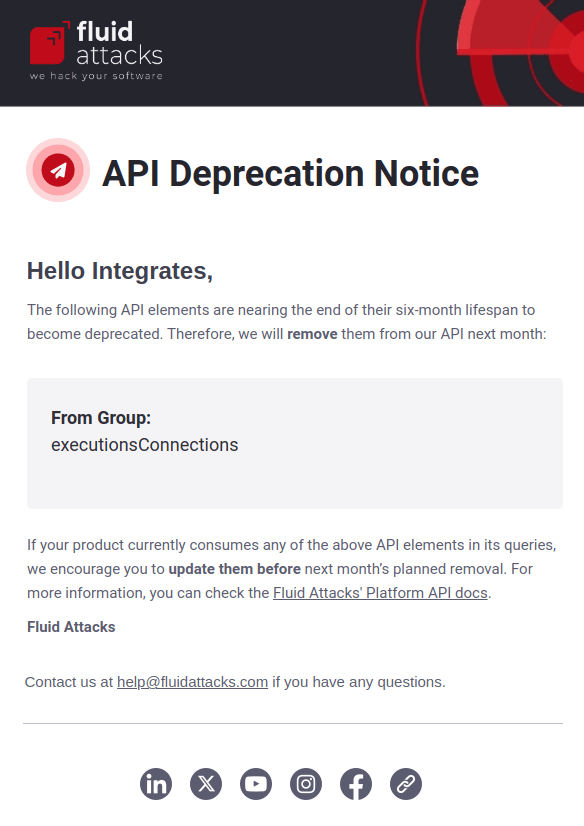
Note: This notification is also the one sent to authors when invited to join the platform.API deprecation notice
If you use Fluid Attacks' API token, you will be sent emails one month in advance when a field of the API token is going to be deleted. The message mentions the field(s) in question.
Confirm deletion
This notification is sent when you decide to delete your account from the platform. Clicking on the confirmation button effectively removes your account.
Group vulnerabilities report
Missing member
 Role required: Group Manager
Role required: Group Manager
New sign in report
You get this email every time you sign in using a one-time password (OTP). The message contains the location, IP address, browser, operating system and date associated with this activity. It also prompts you to report suspicious activity to your organization. Bear in mind that you do not receive this email if the device used for signing in is a valid trusted device.
SBOM file
You get this email after you request an export of your software bill of materials (SBOM). The message specifies how you configured the report and provides a link to download it.
ZTNA down
If you use the Connector connection, you receive notifications when the connector status is down, alerting you to any connectivity issues. The email informs you of relevant information, including the affected organization's name and the number of roots for which this connection is used.
Free-trial-exclusive notifications
Abandoned trial
This notification reminds users who started but have not completed the free trial registration that they are a few steps away from enjoying the Continuous Hacking Essential plan benefits for 21 days. The mentioned benefits focus on Fluid Attacks' multi-method vulnerability scans, single-pane-of-glass platform, and remediation support through artificial intelligence.
Abandoned trial 2
This notification is sent to users who have not completed the free trial registration 24 hours after they started it. Users are told that they just need to add their Git repository and can ask for guidance through the process at help@fluidattacks.com.
Abandoned trial 3
This notification is sent to users who have not completed the free trial registration 48 hours after they started it. Users are encouraged to go to app.fluidattacks.com/SignUp and resume the registration steps. They are also told to contact help@fluidattacks.com if they need assistance.
Free trial
This notification welcomes new free trial users who have completed the enrollment process. This email provides links to the Fluid Attacks platform's certifications and the Knowledge Base pages detailing the following: inviting members, installing the IDE extensions, and adding Git repositories to test.
Free trial 2
Free trial 3
This email is sent to free trial users seven days after they have completed the enrollment process. It encourages them to take a look at the graphs and figures the platform offers in its Analytics sections, with a focus on tracking vulnerability remediation performance. The message also includes an invitation to complete the free online certifications for learning to use the platform.
Free trial 4
This email is sent to free trial users 14 days after they have completed the enrollment process. It mainly encourages the use of Fluid Attacks' CI Gate, which can be run in CI/CD systems to break builds if they have vulnerabilities that are in noncompliance with the customized policies. The user is informed of the effectiveness of this measure in reducing the time until remediation, as evidenced in Fluid Attacks' latest annual report.
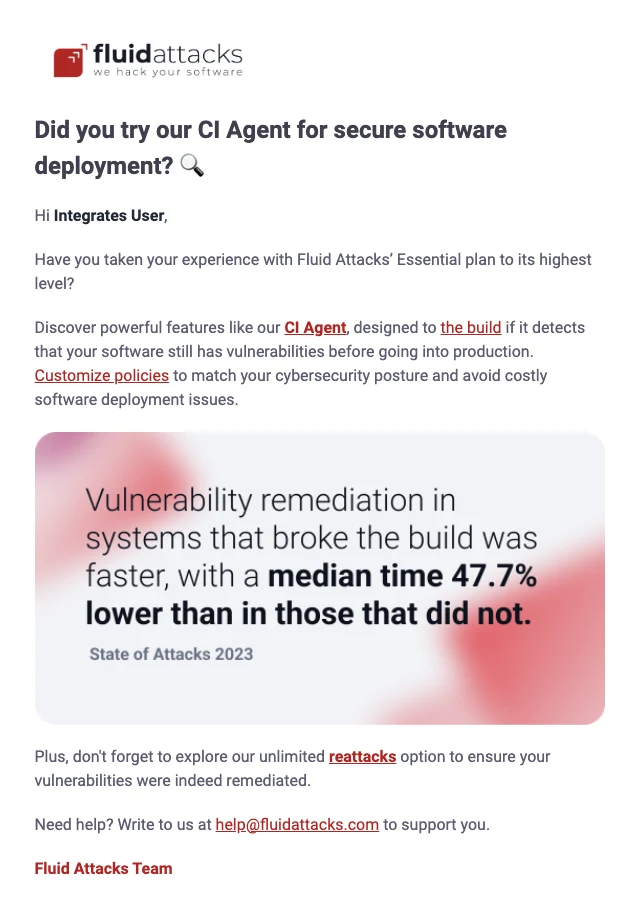
Free trial 5
This email is sent to free trial users 18 days after they have completed the enrollment process. It encourages users to upgrade to Fluid Attacks' paid plan that includes manual security testing performed by the team of pentesters, namely, Continuous Hacking Advanced. The user is informed of the advantages of this kind of tests for the identification of risk exposure and critical severity vulnerabilities, as evidenced in Fluid Attacks' latest annual report. Additionally, this email warns users that their information on the platform is deleted once they choose not to get a paid plan when the free trial expires.
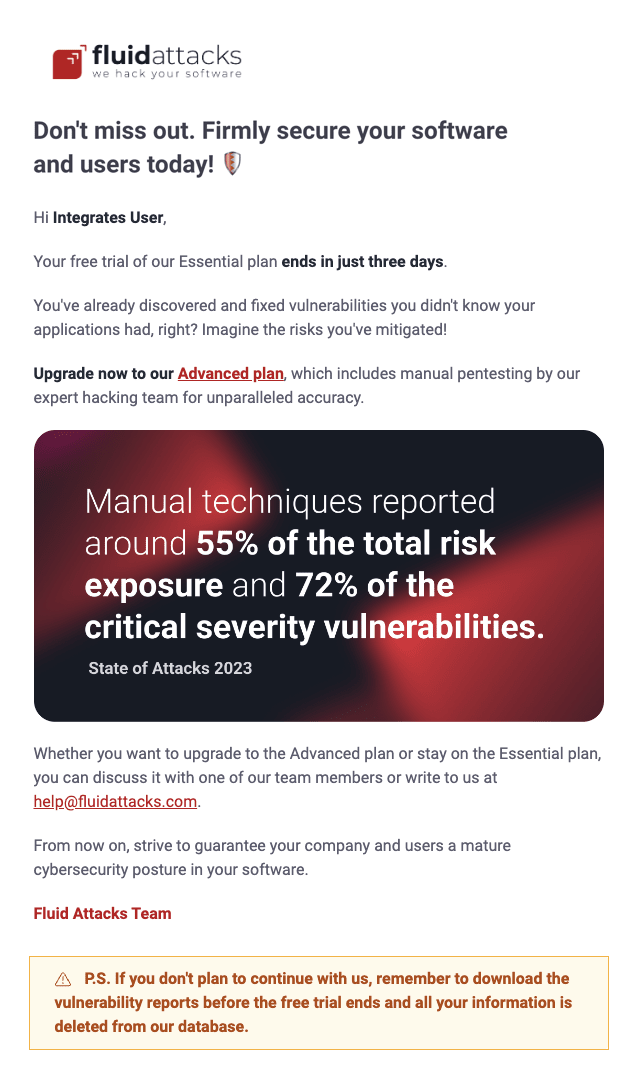
Free trial 6
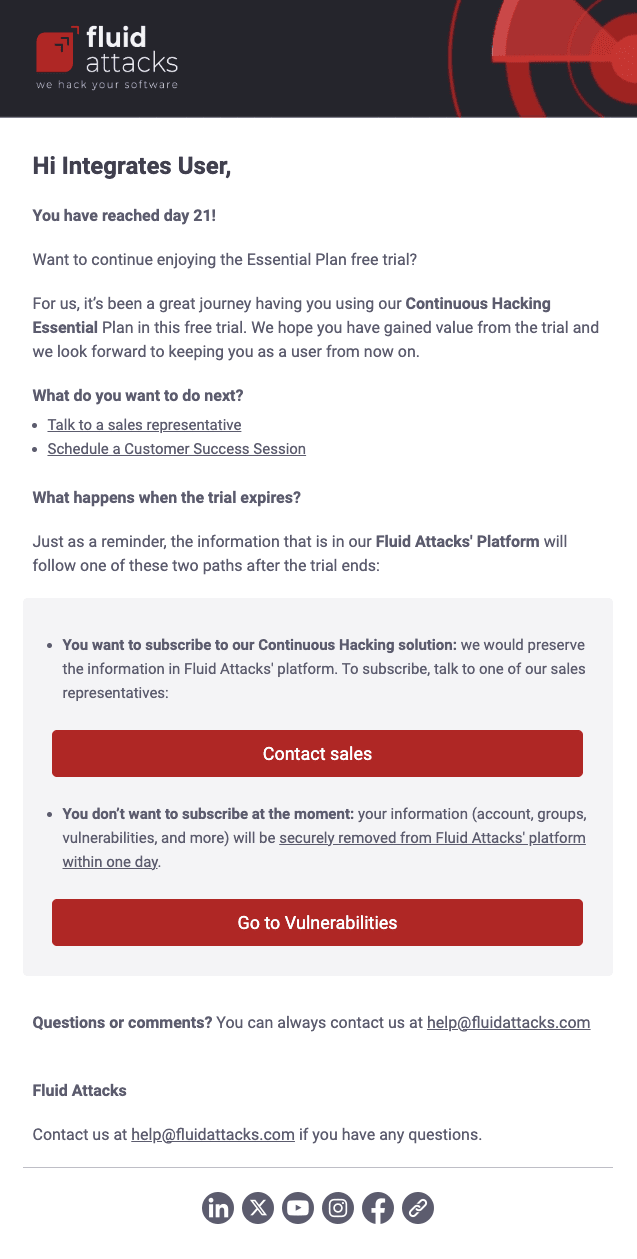
This email is sent to users the day their 21-day free trial expires. It instructs them on how to acquire a paid plan and asks them to provide their feedback or submit a review on Gartner Peer Insights.
Free trial 7
This email is sent to free trial users 24 days after they started the trial, that is, three days after its expiration, when they did not acquire a paid plan. Users are encouraged to shared their thoughts on Fluid Attacks' solution in an email to help@fluidattacks.com or a review on Gartner Peer Insights.
Free trial 8
This email is sent to free trial users 27 days after they started the trial, that is, six days after its expiration, when they did not acquire a paid plan. Users are reminded of the importance of continuous cybersecurity. Further, they are asked to provide their questions or feedback at help@fluidattacks.com.
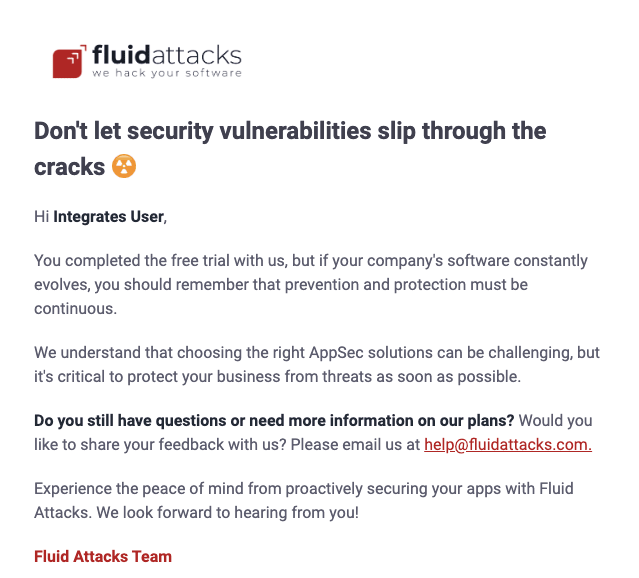
Free trial over
This notification informs users that their free trial has ended and provides the option to continue using Continuous Hacking. It also says what happens to the information on the platform depending on the users' decision to get a subscription plan or not.
Trial first scanning
This email informs free trial users about the first scan result or if a scanning failure occurred.

If the scan did not find vulnerabilities, the message notifies users of this result instead and encourages them to add more repositories to test, providing a link to the platform.

If the first scan fails due to a cloning issue, users are notified in an email that prompts them to check the repository data or replace the repository if needed, and provides a link to the platform.

Notifications exclusive to Fluid Attacks staff
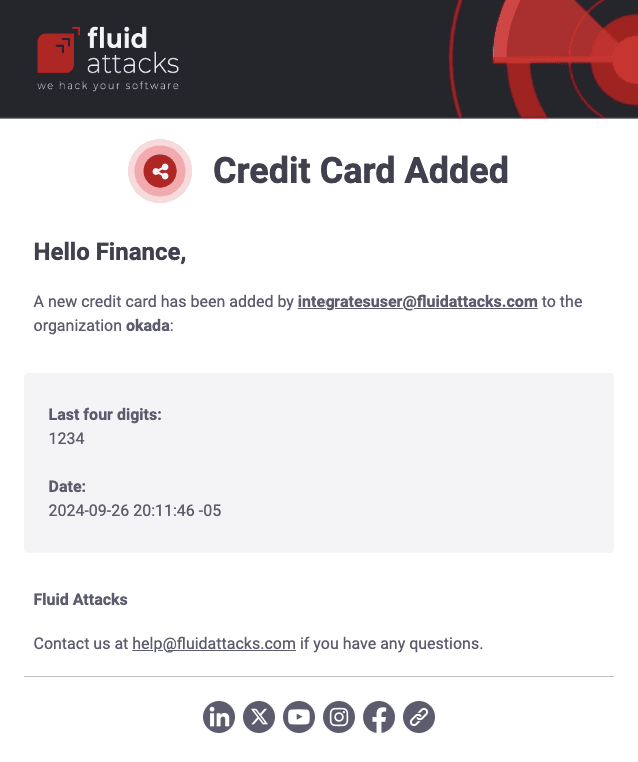
Credit card added
Authorized Fluid Attacks personnel get this email when a new credit card is added to an organization's payment methods. The message indicates the organization's name, the email of the user who added it, the card's last four digits, and the date it was added.
Draft updates
Vulnerability submission
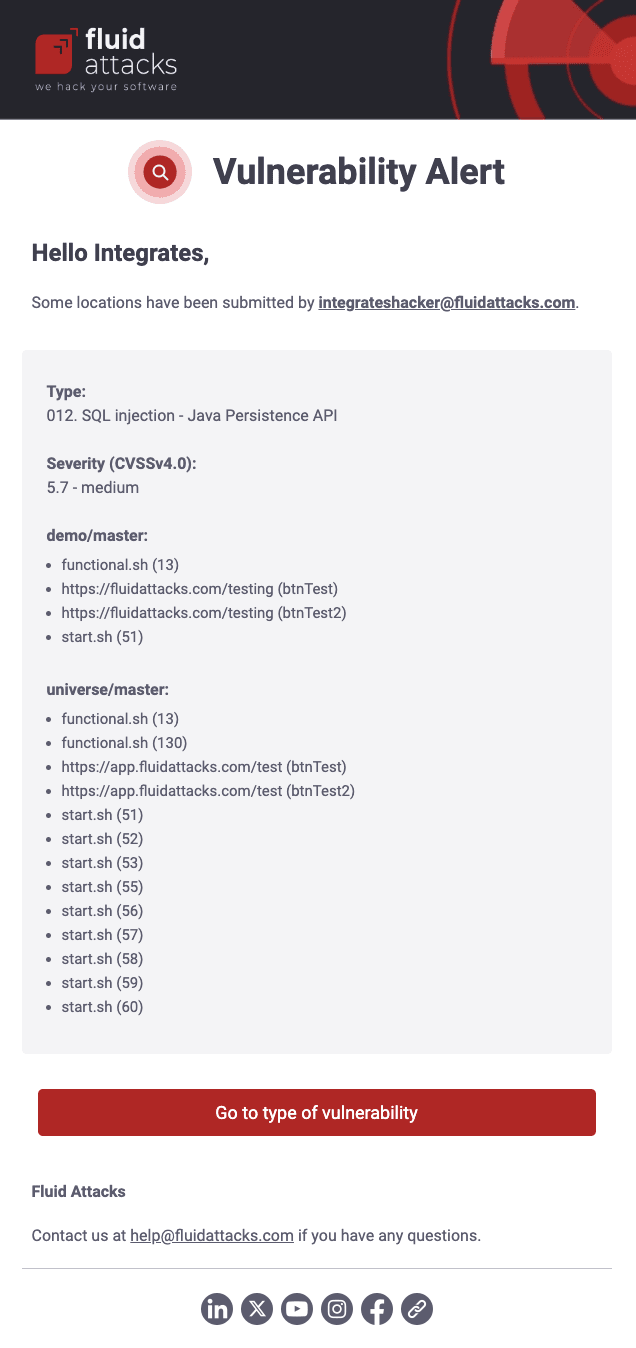
As a security analyst, when you report vulnerabilities in a group, you do so as a draft for the approval or rejection of a reviewer. If you enable Draft updates notifications, you receive an email telling you when a draft is submitted. It includes relevant information such as the type of vulnerability, location(s), and CVSS severity score. At the end of the message, there is a button to direct you to the type of vulnerability.
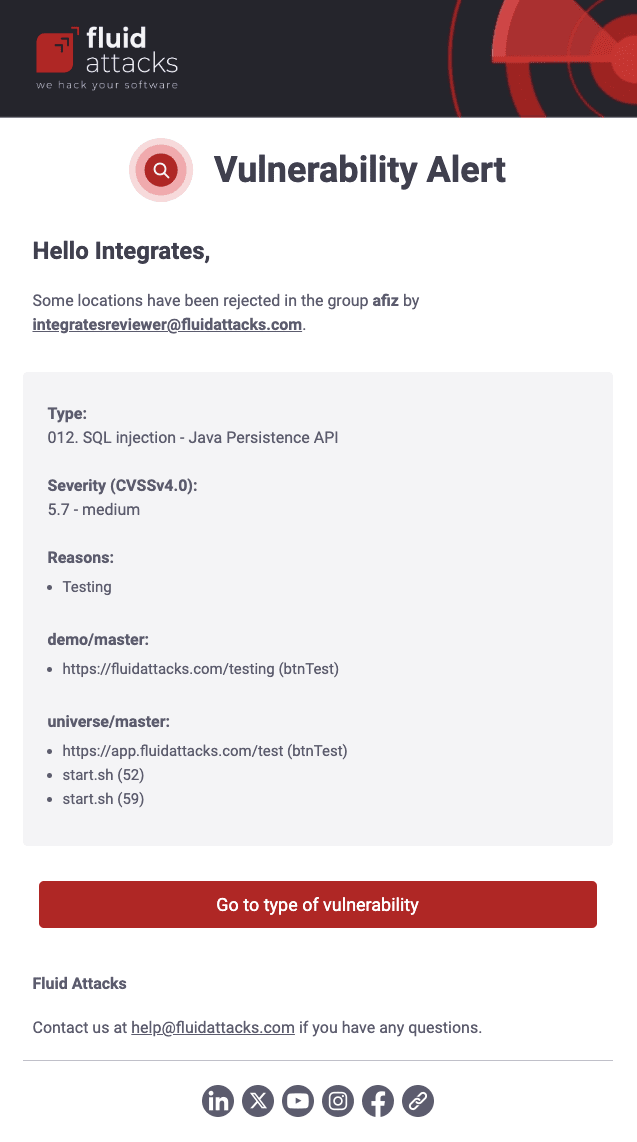
Vulnerability rejection
As a security analyst, if you enable Draft updates notifications, you receive an email telling you when a draft is rejected (its status then changes to not-submitted). The message tells you relevant information such as who rejected it and for what reason, the name of the type of vulnerability, its CVSS severity score, and who had submitted it. At the end of the message, there is a button to direct you to the type of vulnerability.
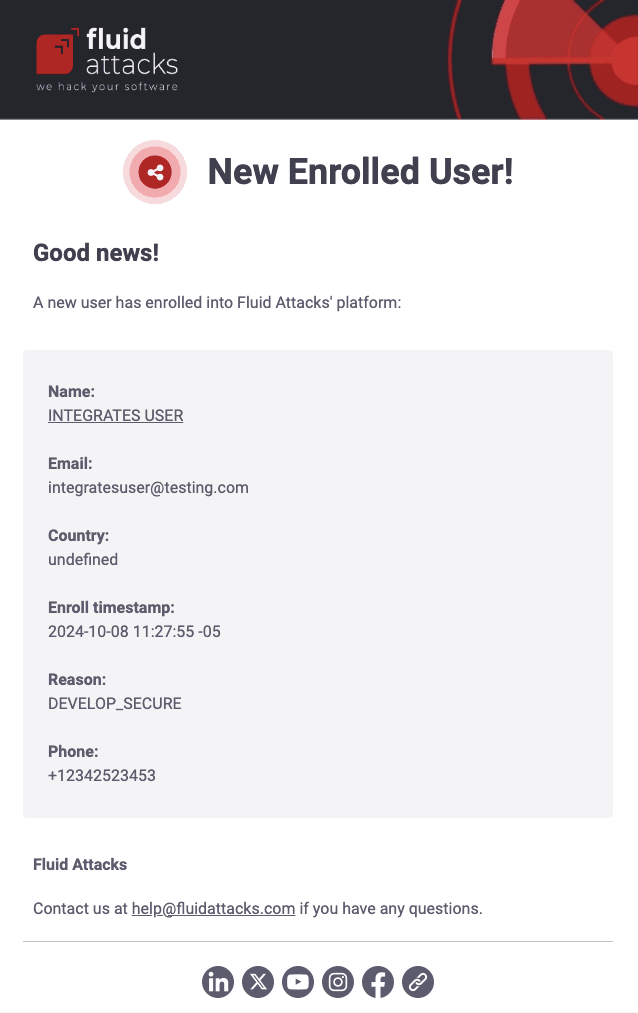
New enrolled
Authorized Fluid Attacks personnel get this email when there is a new member in your organization on the platform. The message provides a link to the member's LinkedIn profile and other details, such as their email, phone number, and registered country.
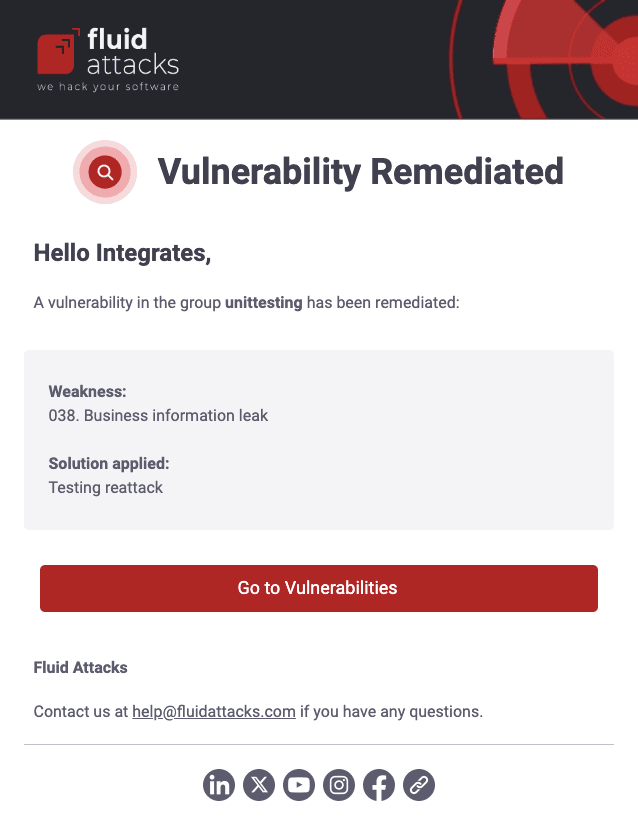
Vulnerability updates for staff
Vulnerability remediated
Type of vulnerability deleted
If you enable Vulnerability updates notifications, you receive emails when a type of vulnerability or a draft is removed. The message contains the email address of the person who removed it and their justification, the group in question, the name of the type of vulnerability, and the type's ID.