Request a vulnerability be dismissed as Zero Risk

Role required: User, Vulnerability Manager or Group Manager

Note: Zero Risk requests generated by members with the User role must be approved by a Vulnerability Manager or Group Manager before they are considered by Fluid Attacks. Without this member's approval, the reported vulnerability will break the build when Users attempt to deploy the system version containing it.
There is a treatment that you can request for any reported vulnerability when, according to a judicious analysis by your organization, said vulnerability poses no threat. This treatment appears as "Request zero risk" within the treatment options on Fluid Attacks' platform.
You can submit your request either from the vulnerability's information window or the window to edit vulnerabilities. The latter allows you to request the treatment for more than one vulnerability.
Follow these steps to use the "Request zero risk" option from the information window.
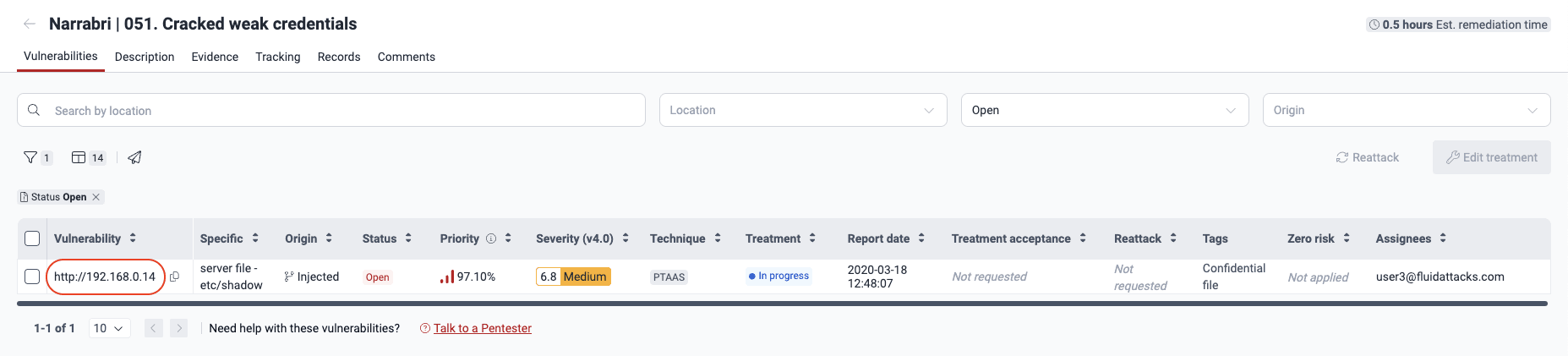
- In the Vulnerabilities section, click on the weakness in question to see its related vulnerabilities.
- Click on the intended vulnerability.
- In the information window, click on the Treatments tab.
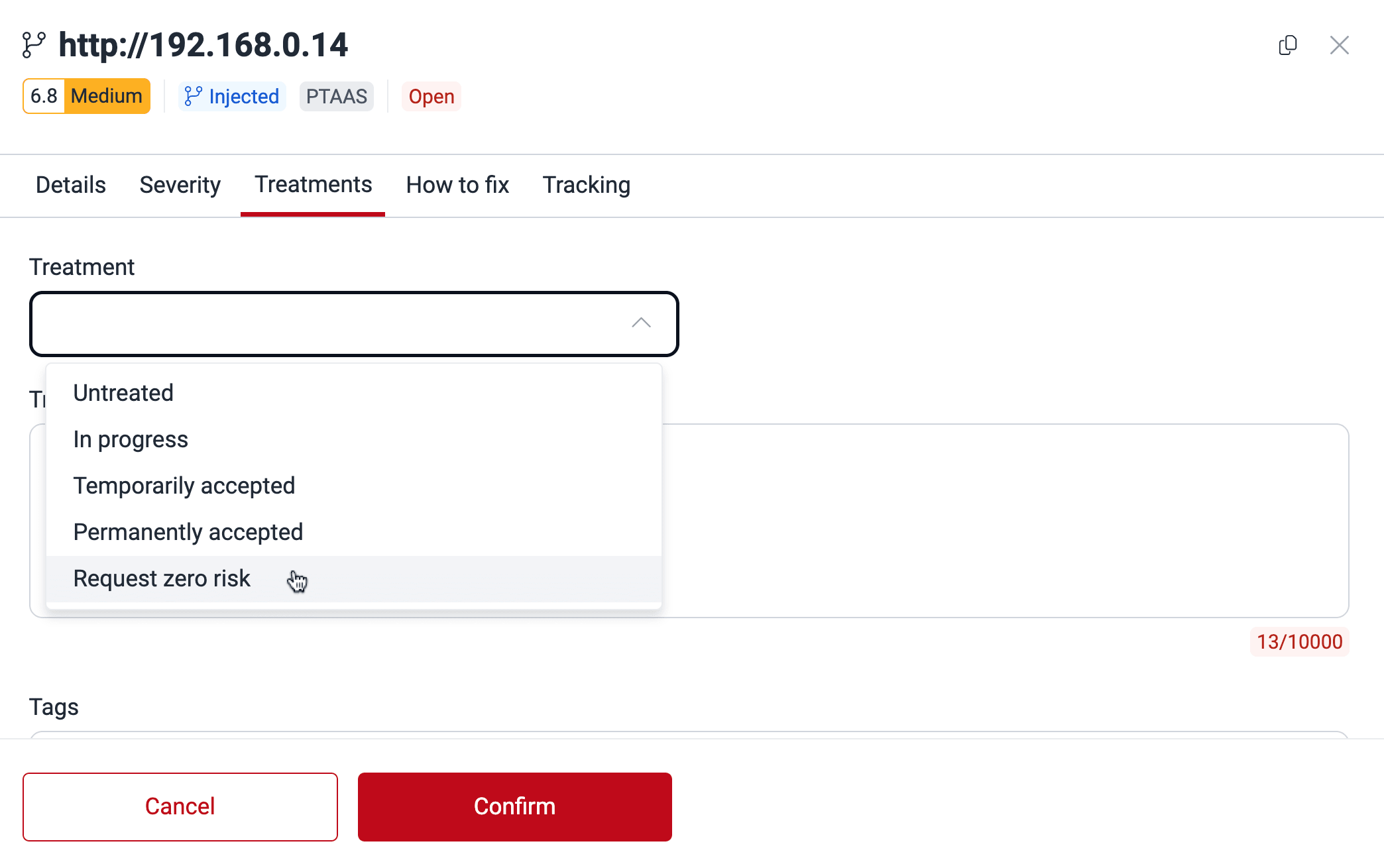
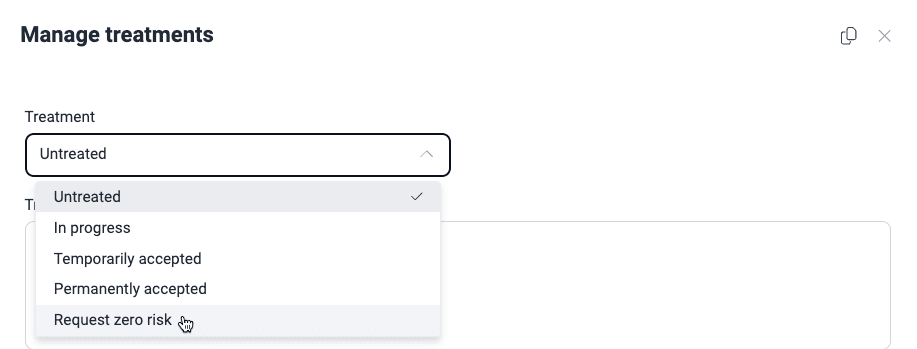
- Select Request zero risk from the Treatment dropdown menu.
- Write a justification for your request, optionally add or remove tags, and click the Confirm button.

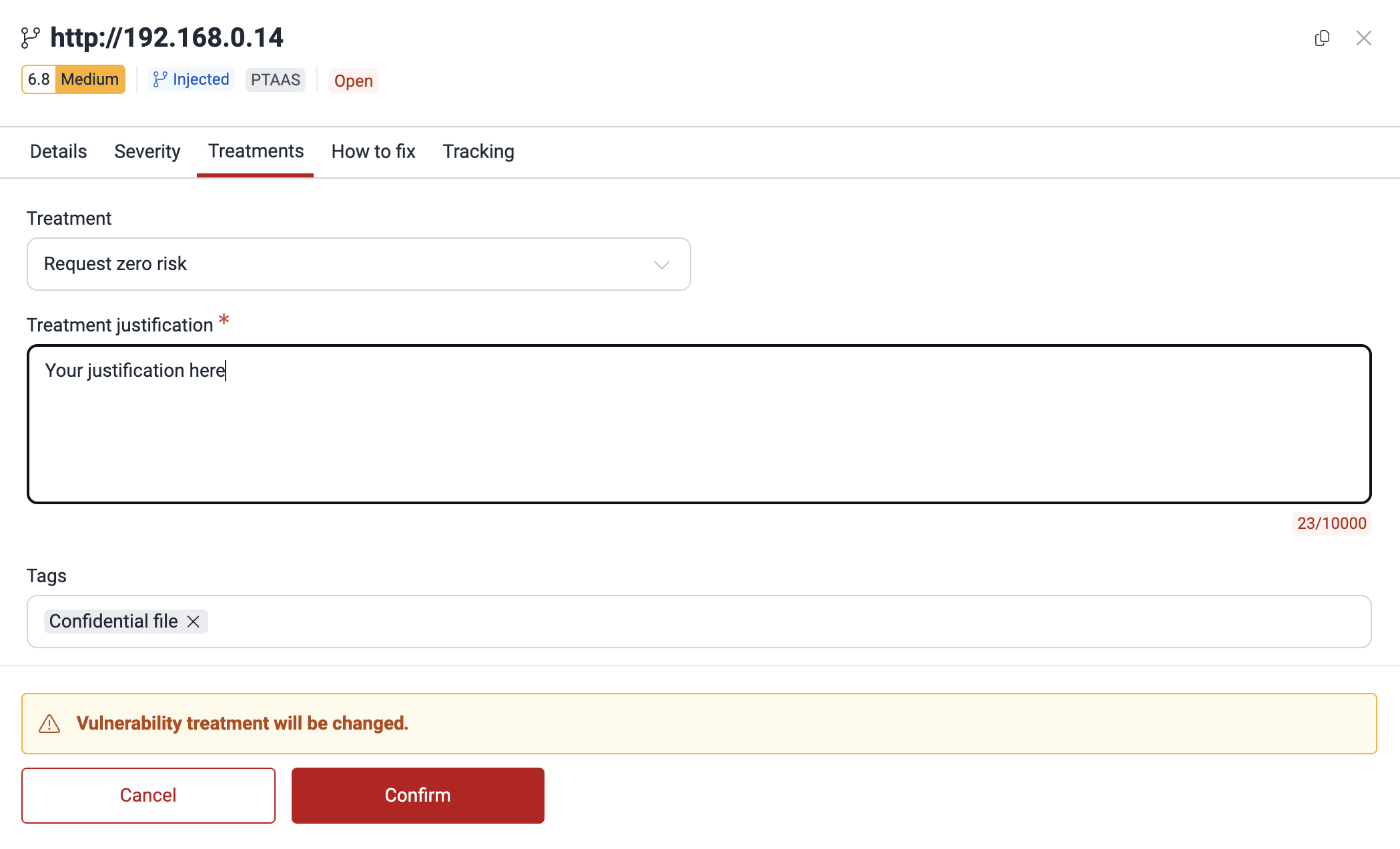
Fluid Attacks will read your justification to consider whether the vulnerability actually poses no threat at all, in which case Fluid Attacks will delete it from the Vulnerabilities table. However, if Fluid Attacks still considers there is risk caused by that vulnerability, then it will remain reported.
The following are the steps to request the treatment from the Manage treatments window.
- In the Vulnerabilities section, click on the weakness in question to see its related vulnerabilities.
- Tick the checkbox next to the reported vulnerability for which you want to assign the treatment. Then click on Edit treatment.
- Select Request zero risk from the Treatment dropdown menu.
- Add a justification for your request and update the remaining fields if needed.
- Click on Confirm when you are done.
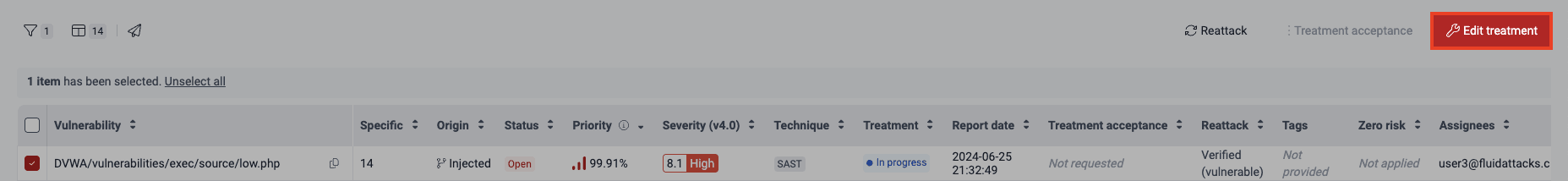

If you want to assign the treatment "Request zero risk" to more than one vulnerability, tick their corresponding checkboxes and click the Edit button.

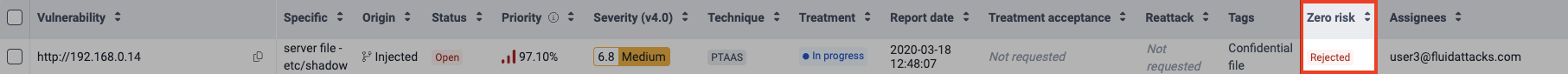
You can see Fluid Attacks' decision on your request in the Zero risk column.

Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.