See vulnerabilities assigned to you
The platform's To do section is where you keep track of all vulnerabilities whose remediation has been assigned to you. To access this section, simply click the To do button located in the header.

To learn how to assign fix work to yourself, read the corresponding information in Assign treatments.
 Note: Members with the Group Manager or Vulnerability Manager role can assign vulnerabilities to any member of the group.
Note: Members with the Group Manager or Vulnerability Manager role can assign vulnerabilities to any member of the group.Know your Assigned vulnerabilities table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerThe table in Assigned vulnerabilities within the To do section provides a comprehensive overview of the vulnerabilities you are responsible for addressing.

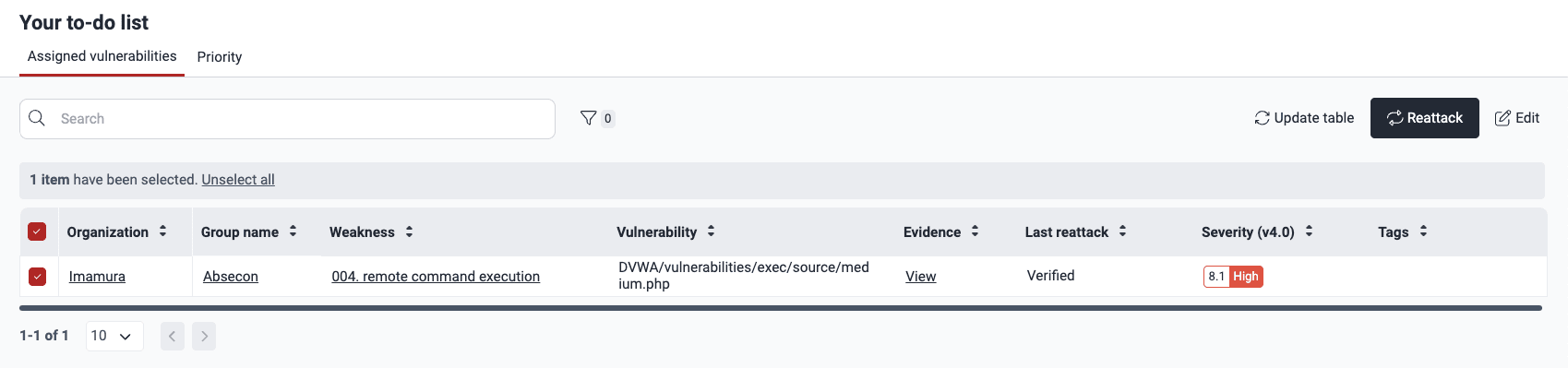
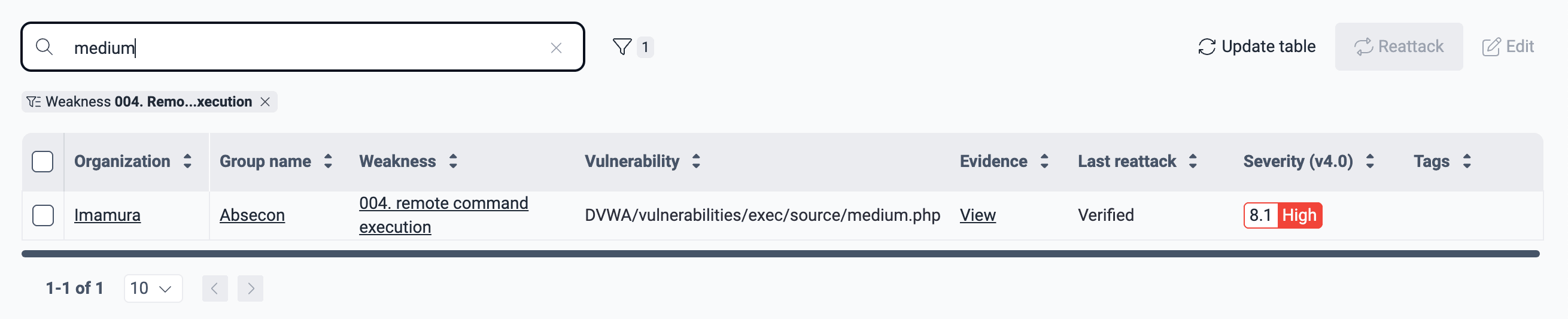
This is the information provided in the table:
- Organization: The organization where the vulnerability was identified
- Group name: The group where the vulnerability is present (click on the group name to go to the Vulnerabilities section of that group)
- Weakness: The weakness in question (click on it to go to its dedicated section within the group)
- Vulnerability: The vulnerability's location
- Evidence: The link to the Evidence section of the type of vulnerability
- Last reattack: The status of the most recent reattack request for this vulnerability
- Severity (v4.0): The severity level of the vulnerability, based on the Common Vulnerability Scoring System (CVSS)
- Tags: Any tags associated with the vulnerability during assignment
Edit vulnerabilities in your to-do list
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group Manager Members with the User role can assign fix work to themselves and edit the External BTS and Tags.
Members with the User role can assign fix work to themselves and edit the External BTS and Tags.To edit a vulnerability in the to-do list, follow these steps:
- Go to the To do section.
- In the table, select the checkbox on the left of the vulnerability in question.
- Click the Edit button.
- Make the necessary changes in the form. Only Vulnerability Managers and Group Managers can modify the values of Treatment and Assignee. (For descriptions of the fields, read Assign treatments.)
- Click on Confirm to apply the changes.

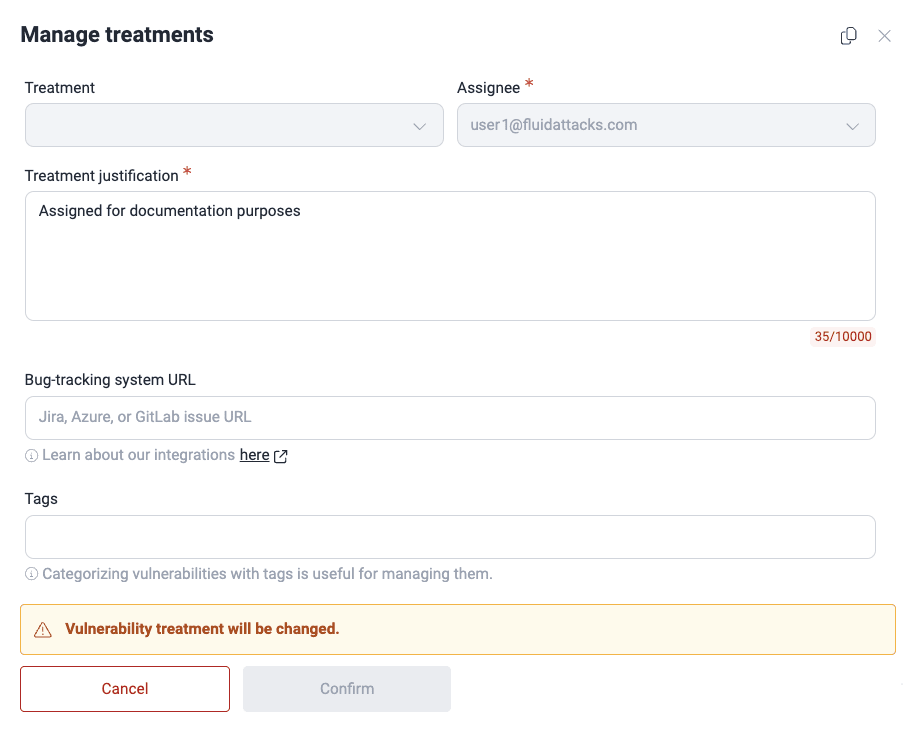
Any changes made trigger notifications to members subscribed to them.
Request a reattack
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerAfter fixing your code to remediate a vulnerability, you can request a reattack to verify the effectiveness of your fix. You can ask for reattacks from the Locations and To do sections.
Here are the steps to perform a reattack from the To do section:
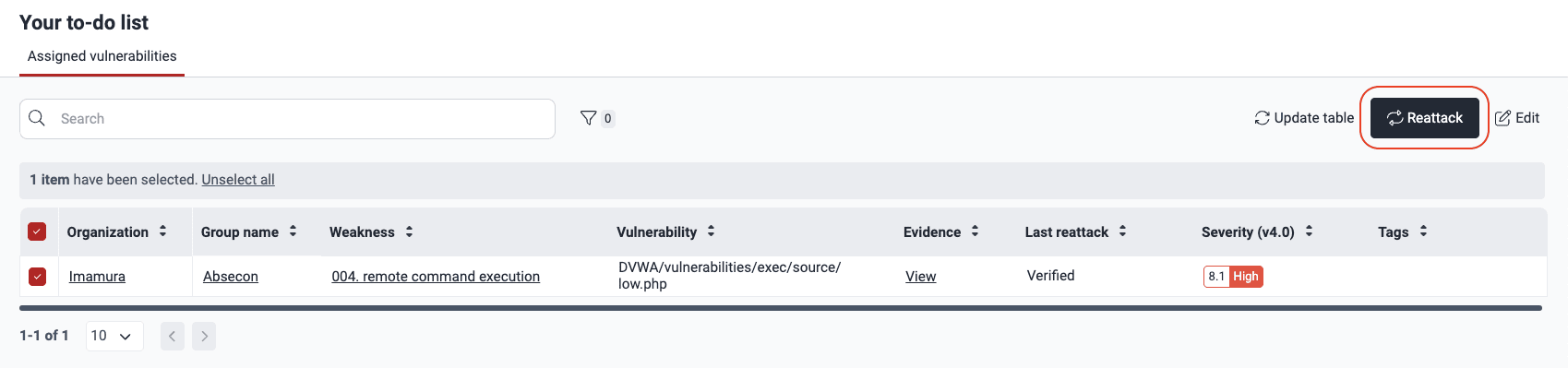
- In the To do section, select the vulnerability that you addressed.
- Click the Reattack button.
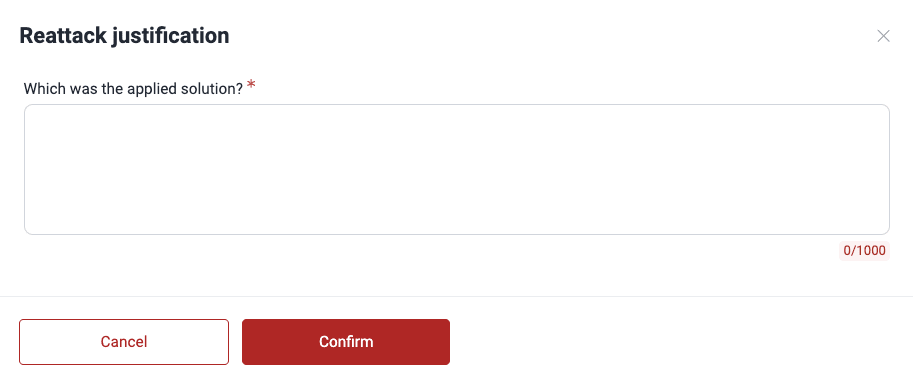
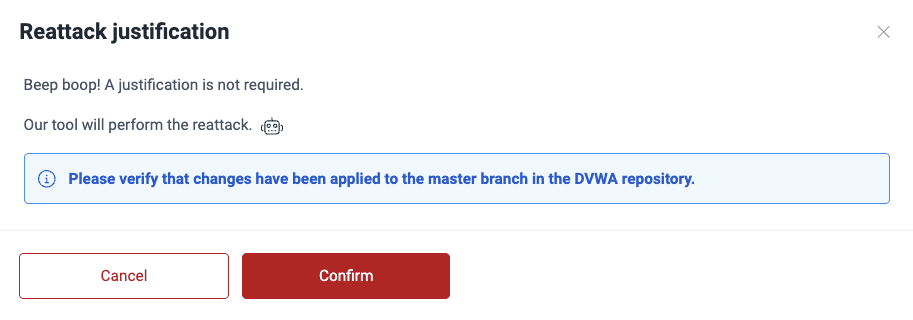
- In the pop-up window, if applicable, provide a justification for the reattack request (minimum 10 characters).
- Click on Confirm to send the request.
If the vulnerability was reported by the scanner, you are just asked to make sure the changes were applied (i.e., that the system version synced to the platform contains the fixes).

Filter the Assigned locations table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerFiltering allows you to quickly refine the displayed vulnerabilities based on specific criteria. To access the options, click on the filters button ( ).
).

To clear an applied filter, simply click on the X next to it.

Refresh the Assigned locations table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerTo update the displayed vulnerabilities and reflect any recent changes, therefore having your pending tasks list up to date, click the Update table button.

Search the Assigned locations table
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerThe search bar filters the information by showing only the rows of the table that match your search.
See events across your groups
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group ManagerThe Events section in To do provides key details on situations that are hindering security testing in the groups you manage. This space gives you a holistic view, allowing you to manage and respond to events effectively, especially when supervising multiple groups.
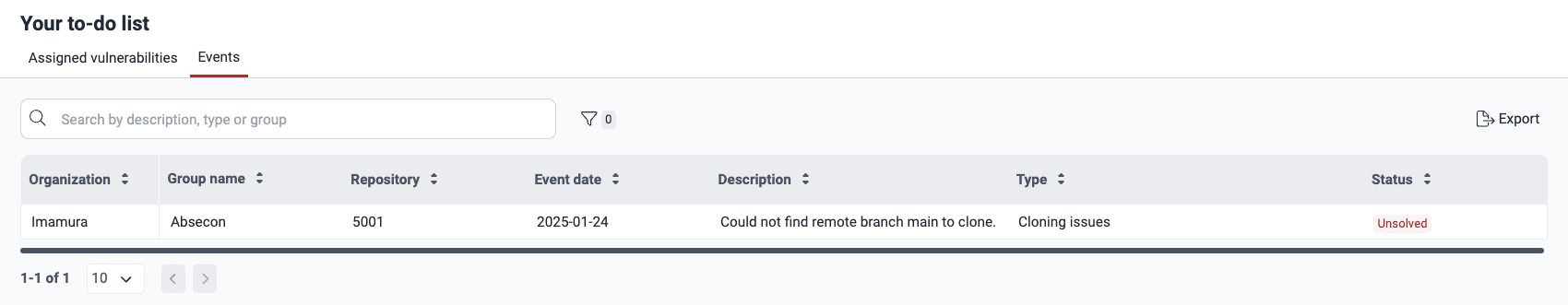

Read a description of the columns in Know your events table.
Filter events
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group ManagerYou can use the Filters option to easily find the events you are looking for.

Export events
 Role required: Vulnerability Manager or Group Manager
Role required: Vulnerability Manager or Group Manager
Be aware that any applied filters limit the data included in the exported CSV file. Ensure your filters are correct before exporting. To quickly remove them, click on the X next to them.
Click on the Export button to download the contents of the table in a CSV (comma-separated values) file.
Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.