View vulnerable lines, use fix options and more
Fluid Attacks' VS Code extension offers the following functions:
-
Go to Criteria (links to Fluid Attacks' documentation on vulnerabilities)
You can access the above functions by either clicking on the Fluid Attacks extension in VS Code's activity bar or clicking on repository files marked with a red dot in VS Code's explorer. This page guides you through using these functions except for the last two, for which there are dedicated, more detailed, pages.

See vulnerable file and code line
You can view vulnerabilities reported in the Fluid Attacks platform from the IDE.
Click on the Fluid Attacks icon in VS Code's activity bar. You are then presented with a comprehensive list of vulnerability types detected in your code.

Click on the vulnerability type of your interest to view all affected files.
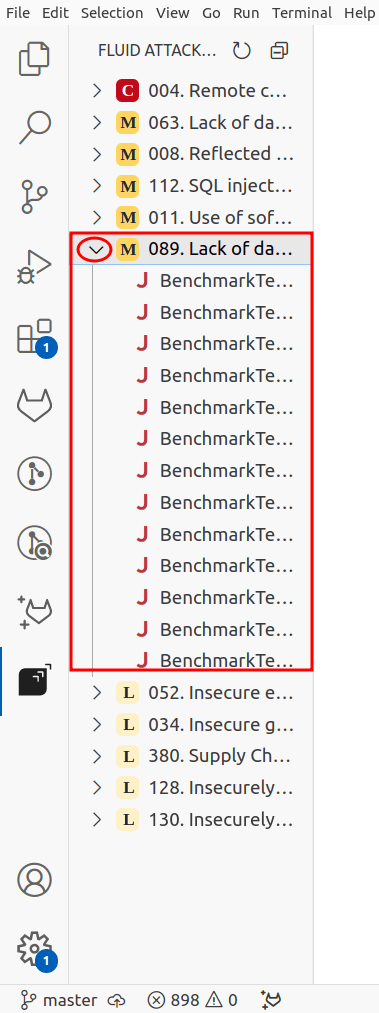
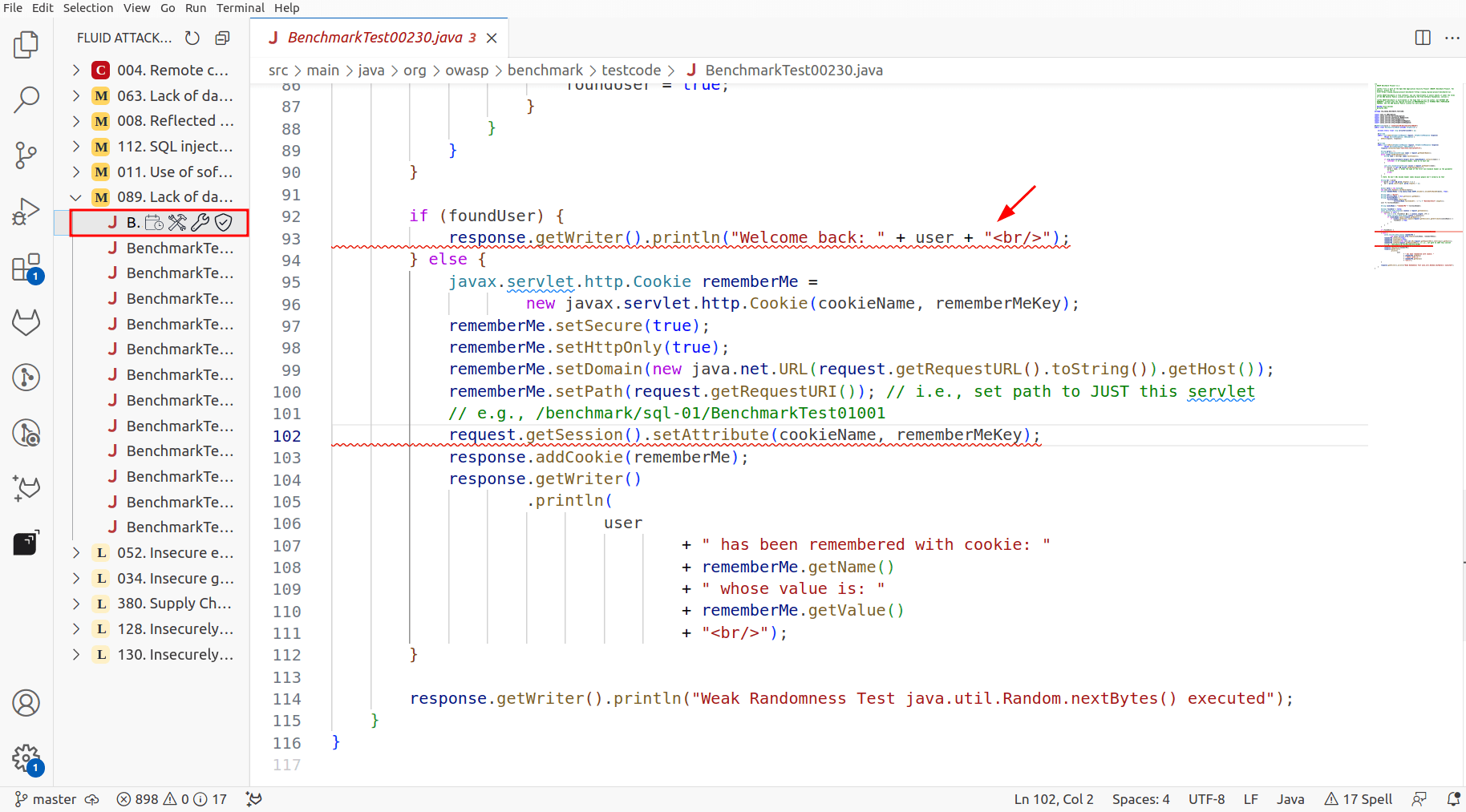
Select a file of your interest to identify the line of code where the vulnerability is present, which is underlined with red.

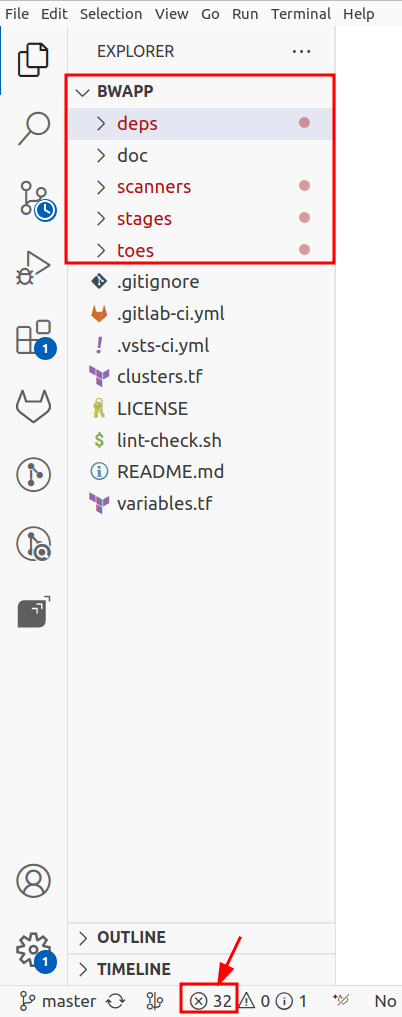
If starting from VS Code's explorer, follow these steps:
-
Open the project corresponding to the Git repository that is tested by Fluid Attacks. Files with vulnerabilities are marked with red dots.
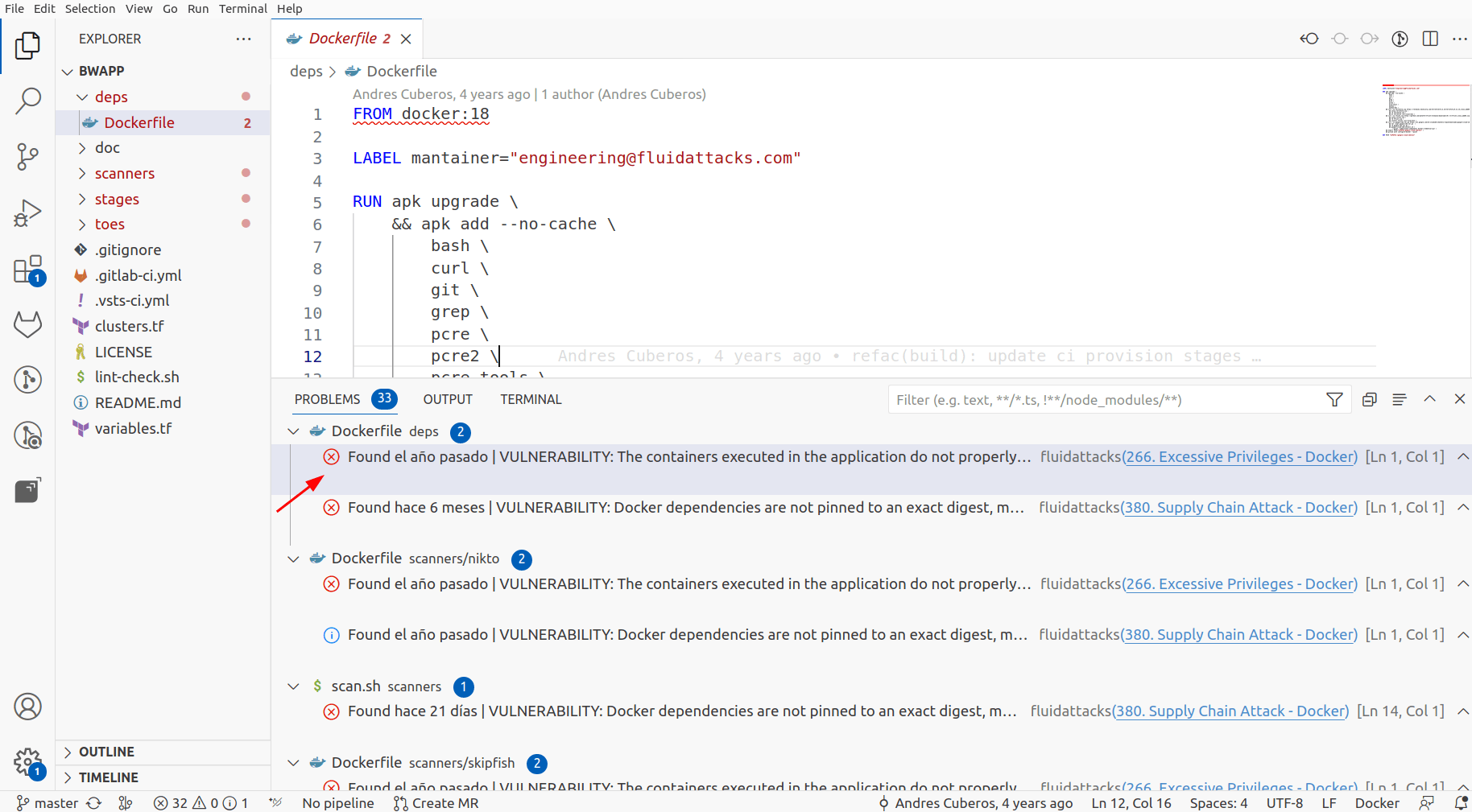
You may click on the files to open them or click on the X icon to open the panel listing the problems of every file.
-
Identify the vulnerable lines of code, which have a red underline.
If going with the latter, click on an item to open the file and see the vulnerable line of code.
Request reattacks
Reattacks refer to retests where Fluid Attacks verifies the effectiveness of your code fixes.
-
Click on the Fluid Attacks extension in VS Code's activity bar.
-
Expand the type of vulnerability you wish to explore by clicking on its name.
Click on a vulnerability to see some icons appear. Click on the shield icon to request a reattack.
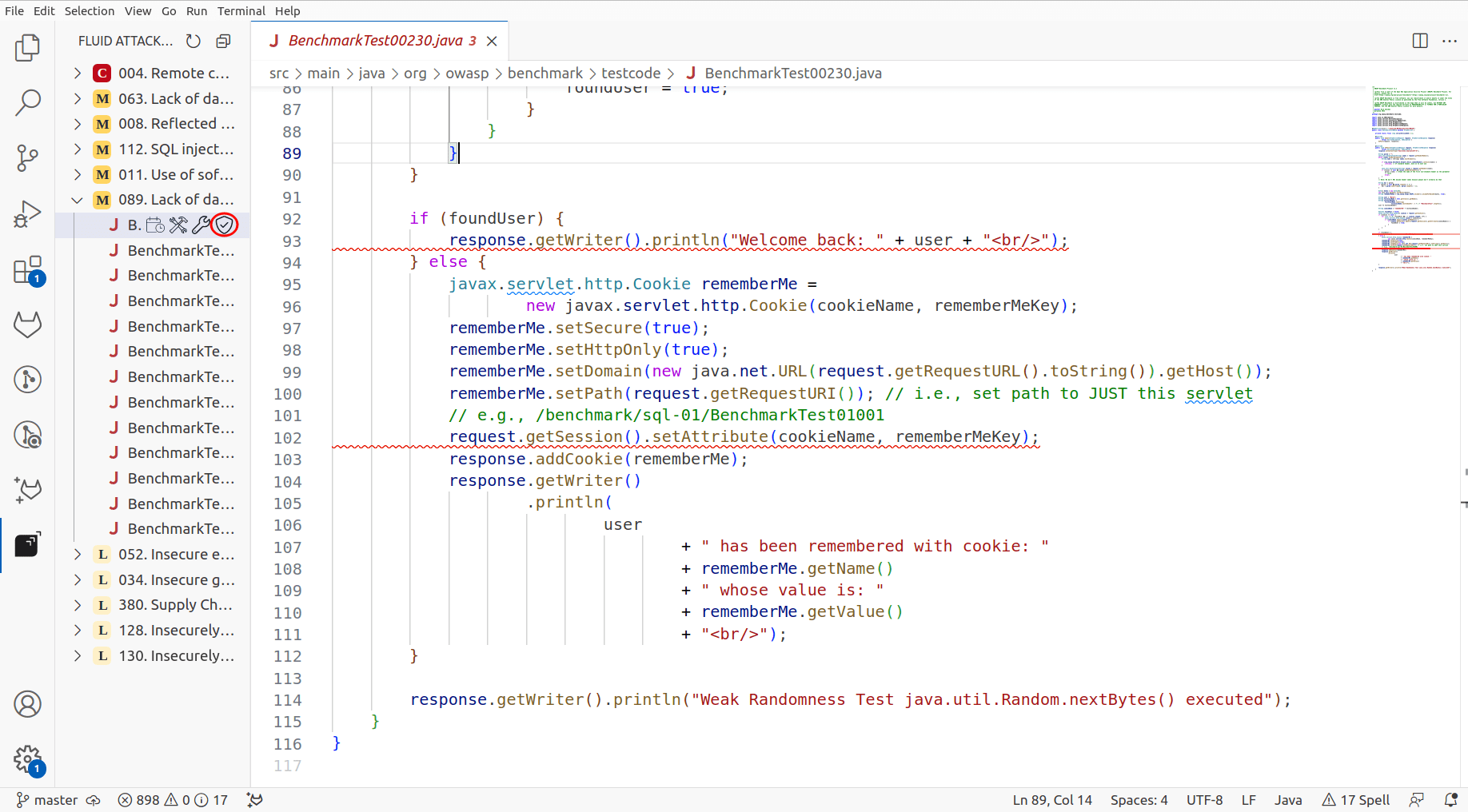
-
Write a description of the fix you applied and press Enter. Wait to receive a notification confirming the successful delivery of the request.
-
You can refresh the view and observe that the vulnerability's underline changes from red to blue, indicating that the reattack was successfully requested.
If starting from VS Code's explorer, follow these steps:
-
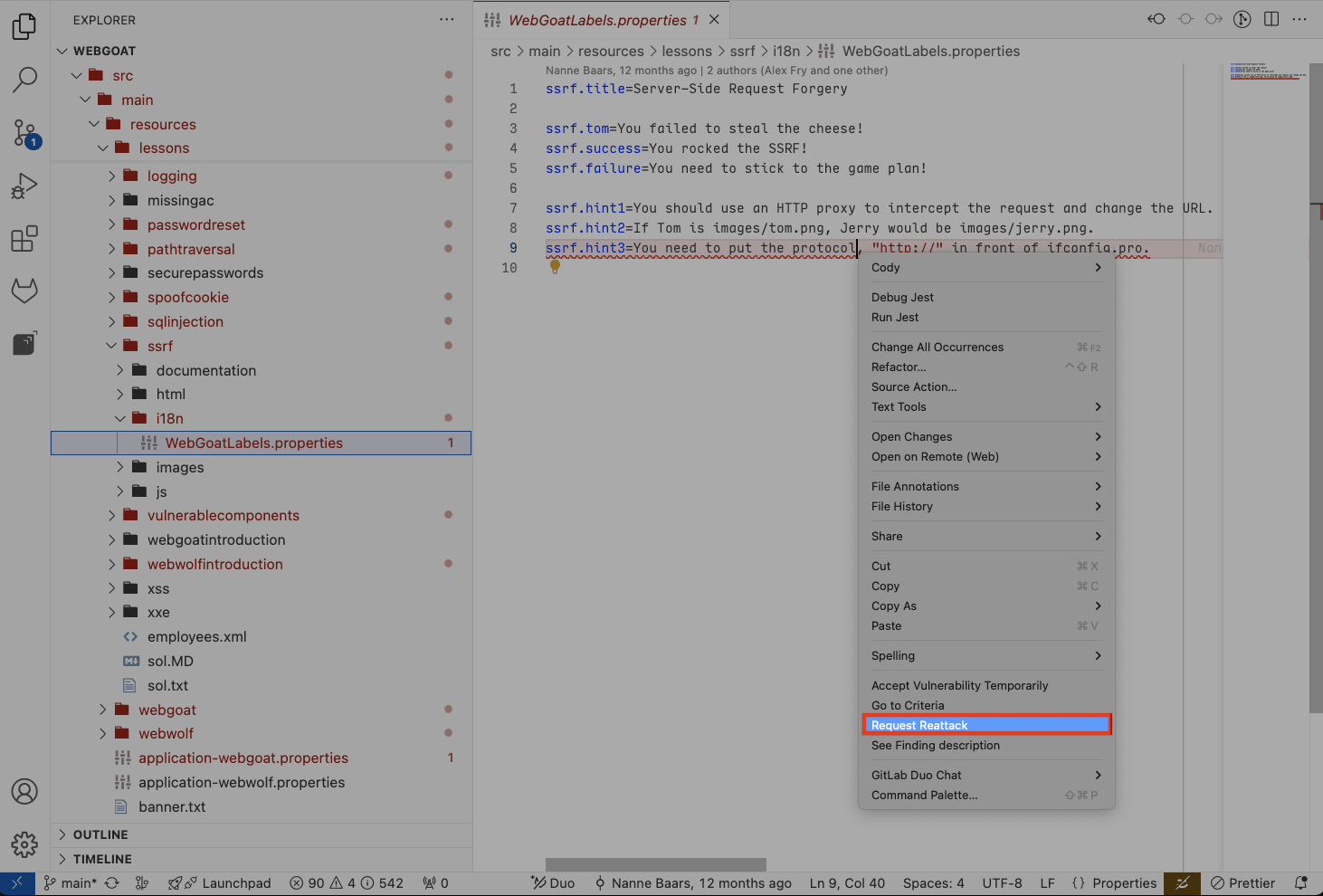
Click on the file to open it.
-
Right-click on the underlined code and locate the Request reattack option.
-
Write a description of the fix you applied and press Enter. Wait to receive a notification confirming the successful delivery of the request.
 Note: Remember to push your code to the tests/security/integration branch.
Note: Remember to push your code to the tests/security/integration branch.Go to Criteria and vulnerability on the platform
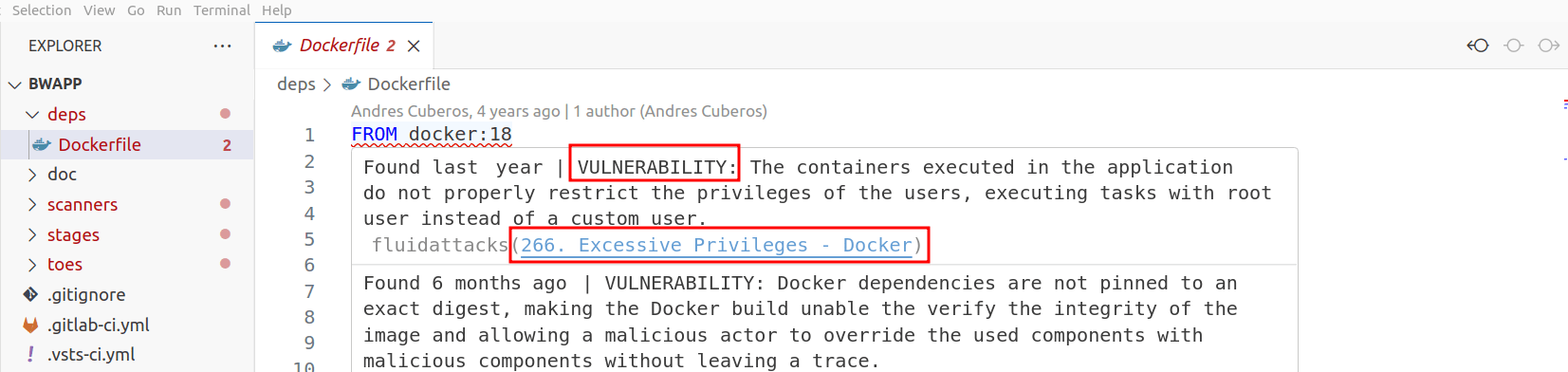
Fluid Attacks' VS Code extension provides you with external links to Fluid Attacks' Database (DB) and, separately, to the report of the vulnerability on the platform. Fluid Attacks' DB is documentation that mainly presents the standards, requirements and vulnerability types that determine the results of security testing.
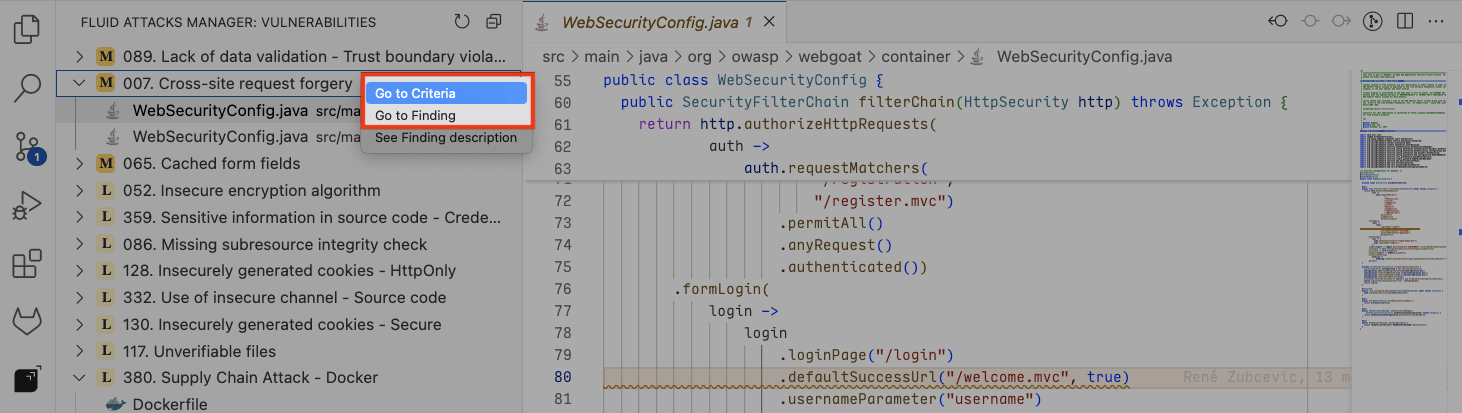
If starting from VS Code's explorer, follow these steps to access the link to the DB:
-
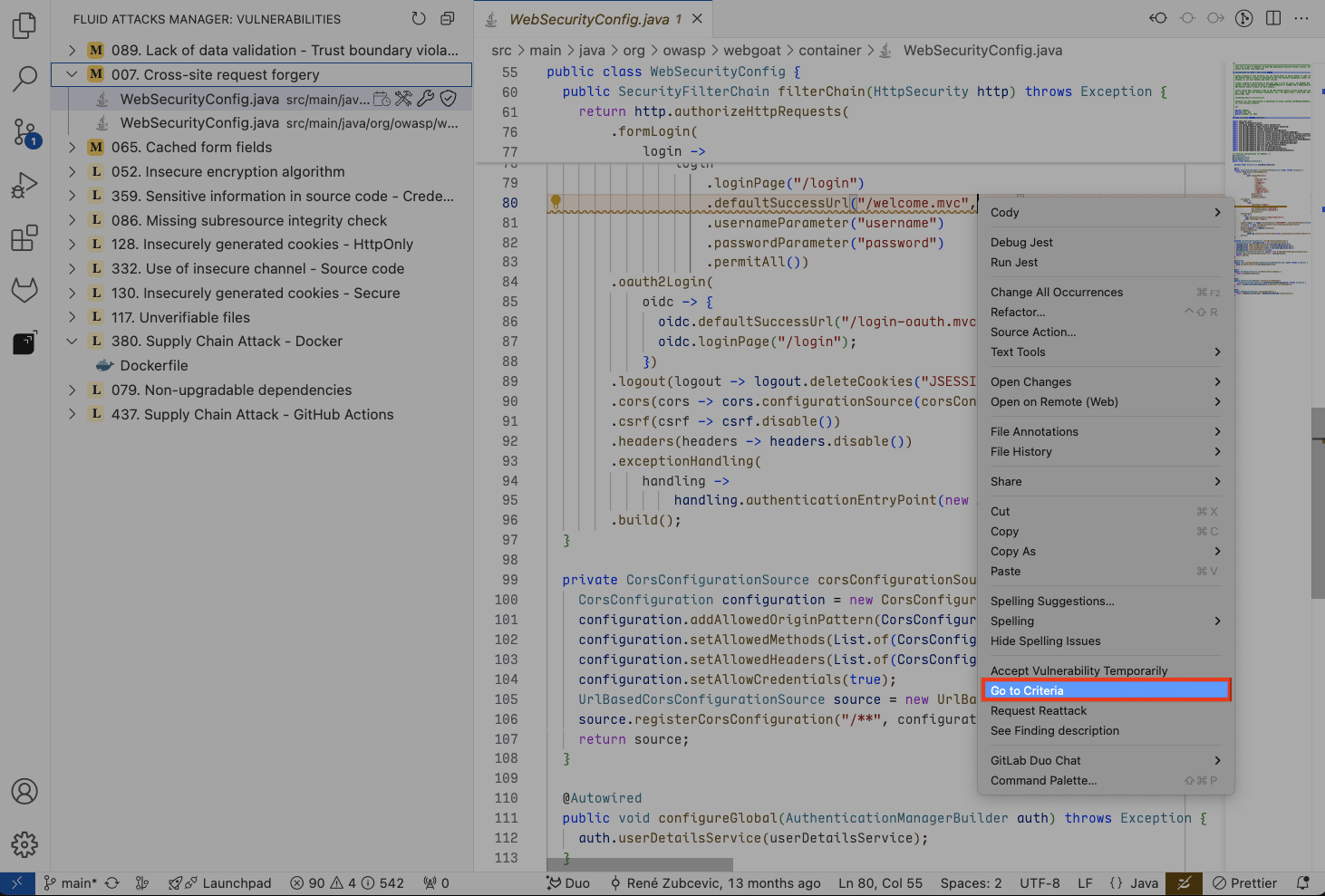
Click on the file to open it.
Right-click on the vulnerable line and select Go to criteria.
To access the link to the vulnerability on the platform, starting from VS Code's explorer, do the following:
-
Click on the file to open it.
Locate the vulnerable line and hover your mouse cursor over it. A pop-up window appears, showing the definition and the external link.
-
Click on the link to the vulnerability URL on the platform.
View vulnerability description
Fluid Attacks offers comprehensive documentation on their classification of vulnerabilities.
-
Click on the Fluid Attacks extension in VS Code's activity bar.
-
Right-click on the type of vulnerability of your interest.
-
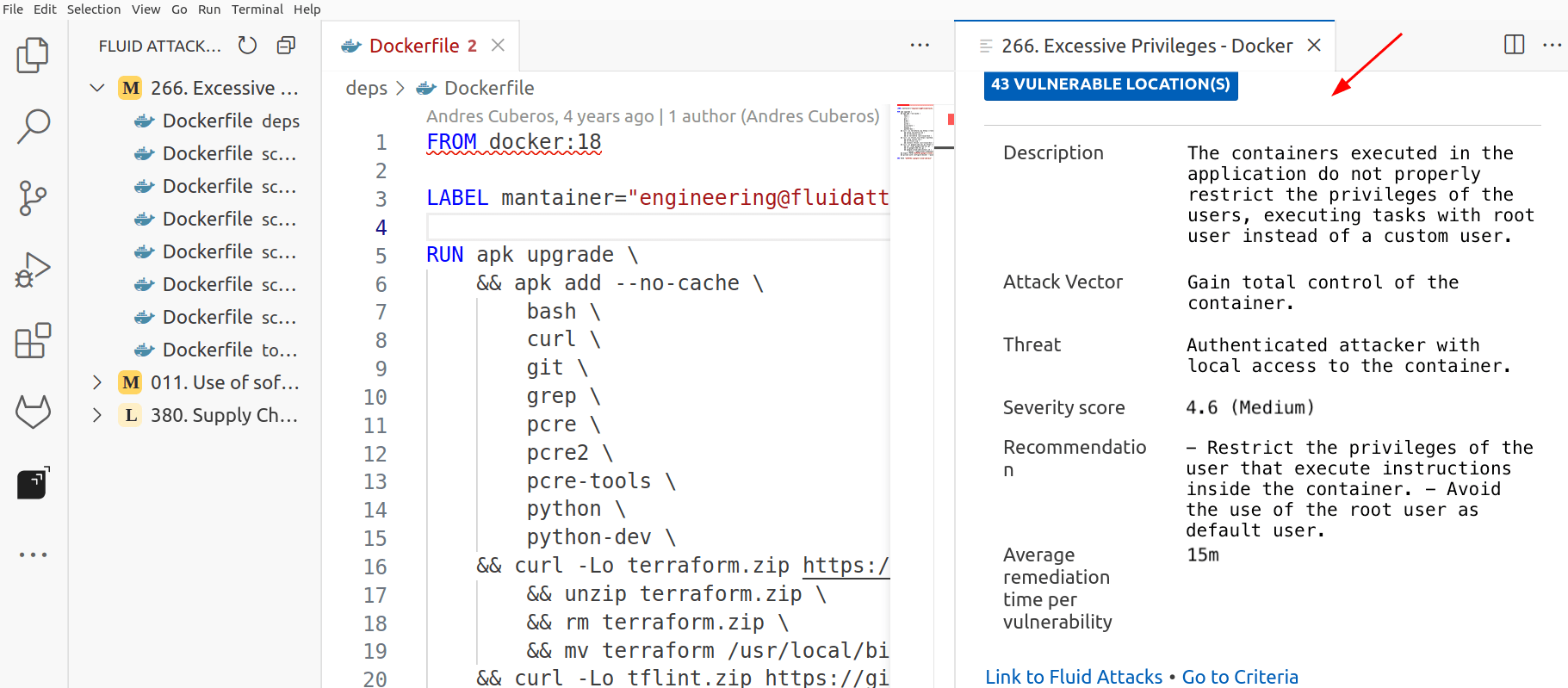
Select See Finding description. This causes the current editor view to split to show you selected information from Fluid Attacks' documentation without leaving VS Code. This includes attack vector, threat, severity score and average remediation time information.
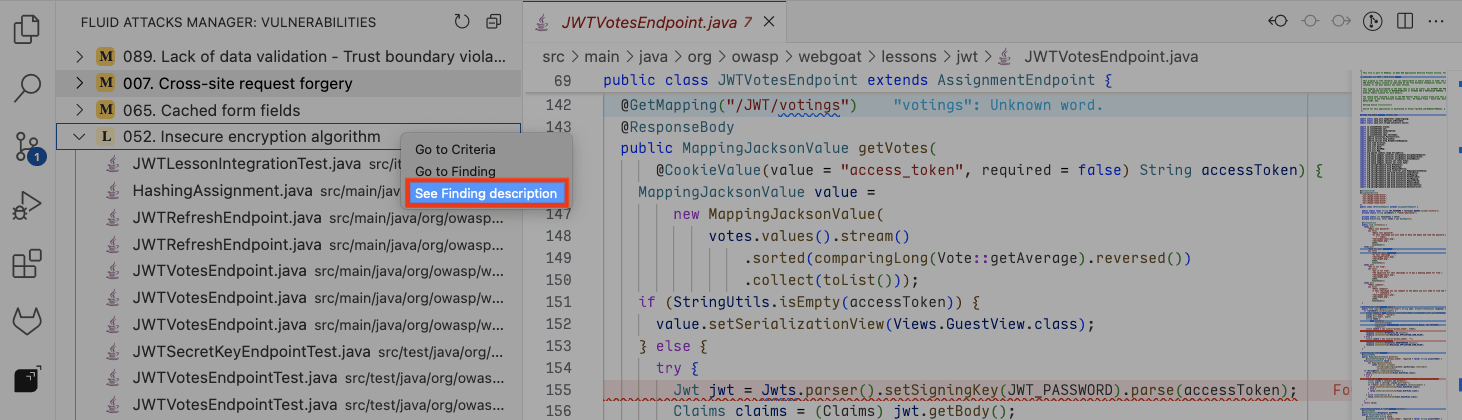
If starting from VS Code's explorer, follow these steps to view the vulnerability description:
-
Click on the file to open it.
-
Right-click on the vulnerable line and select See Finding description.
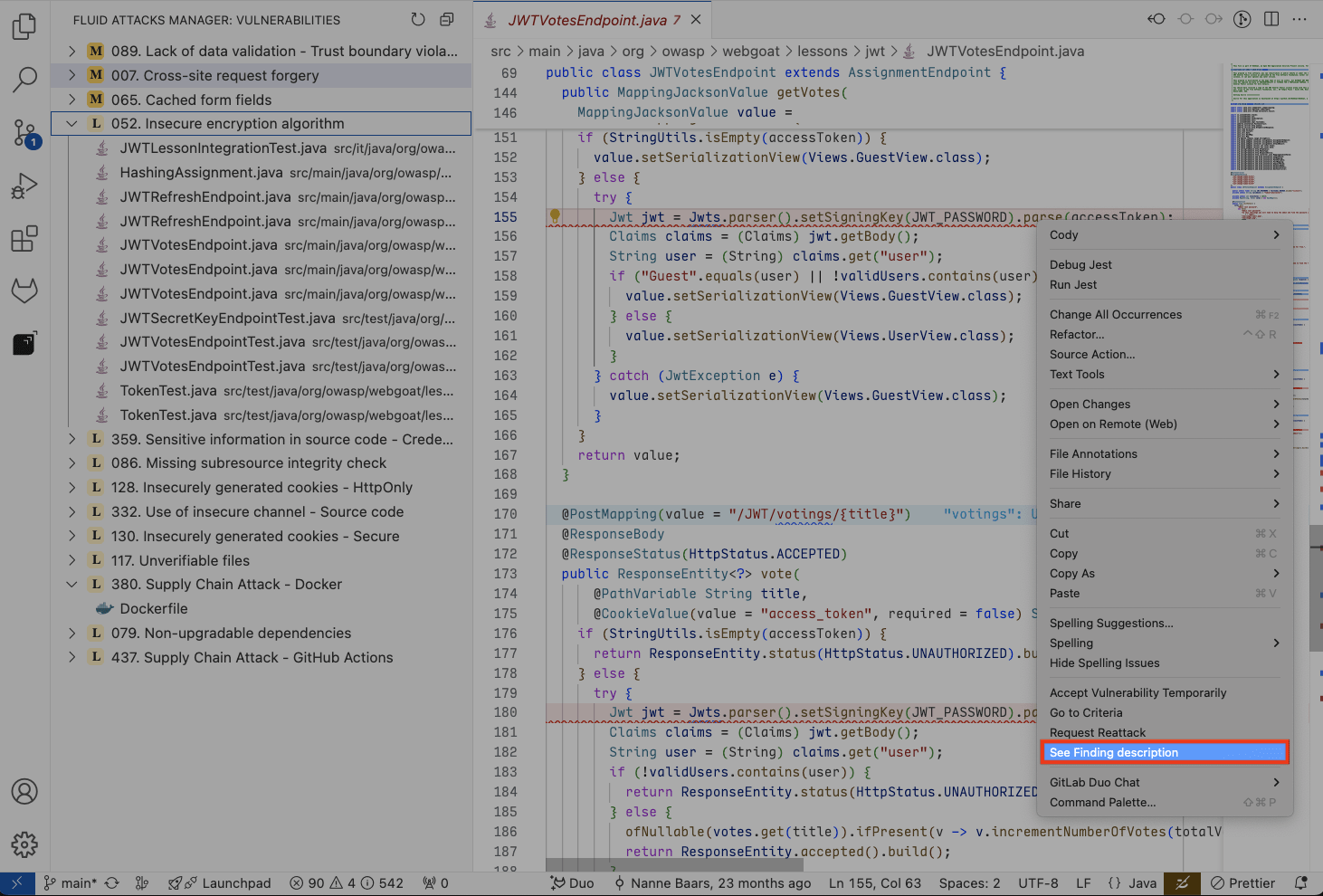
See the vulnerability description and other details at the right side of the editor.
Use fix options

-
Custom fix: Generate step-by-step guides telling you how to fix your code
-
Autofix: Automatically generate a suggested pull request fixing the code (special caution is advised when using this function, as it intends to make changes directly to your codebase)

Refresh button
To ensure actions such as reattack requests and treatment assignment are reflected in the extension, click the refresh button.
Upon refreshing, vulnerability underlines update to reflect their status:
-
Blue: Reattack requested
-
Yellow: 'Temporarily accepted' treatment applied