CVSS score adjustment
Software composition analysis (SCA) detects when open-source components and dependencies in your software project have associated CVE entries. Fluid Attacks understands that particular circumstances need to be present for these vulnerabilities to be exploited, and that these circumstances are not necessarily met in the context of your application. To accurately reflect their potential impact, Fluid Attacks adjusts the CVSS score of vulnerabilities found with SCA scans. This involves retrieving the original CVSS score (v3.1 and 4.0) and specifying that the scan cannot prove that the vulnerability is exploitable, as well as specifying the Remediation Level and Report Confidence values (only in v3.1), which is something the CVE-reporting source might not do. The added specificity is as follows:
- Exploit Code Maturity/Exploit Maturity (E) as 'Unproven' (U)
- Remediation Level (RL) as 'Official Fix' (O) (only in v3.1)
- Report Confidence (RC) as 'Confirmed' (C) (only in v3.1)
The above factors accounted for, CVSS scores reported by Fluid Attacks' SCA are lower than those calculated by the CVE-reporting sources.
To illustrate this, consider the following example of a vulnerability reported by Fluid Attacks' SCA (only a comparison between CVSS v3.1 scores is shown, as v4.0 score calculations by CVE-reporting sources are often pending):
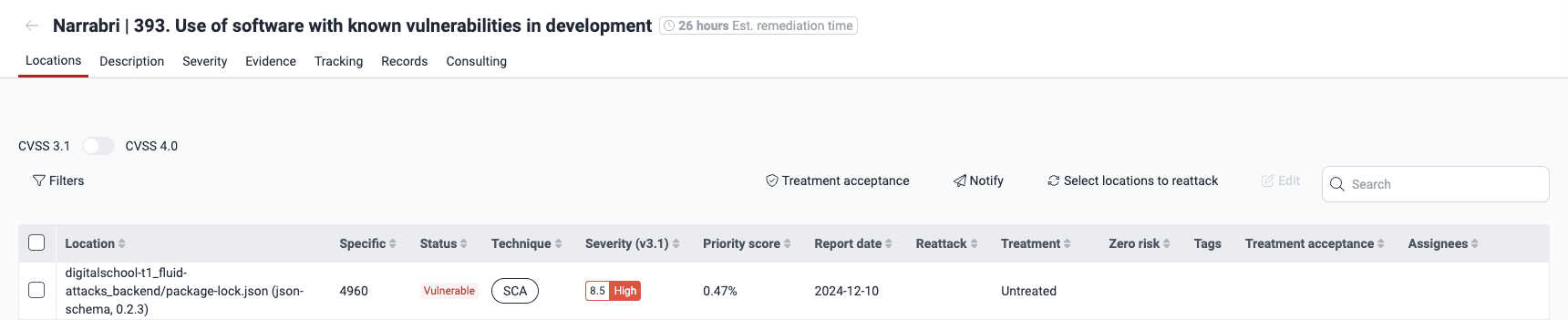
- By clicking on its location, you can identify the CVE in question in the Details tab.
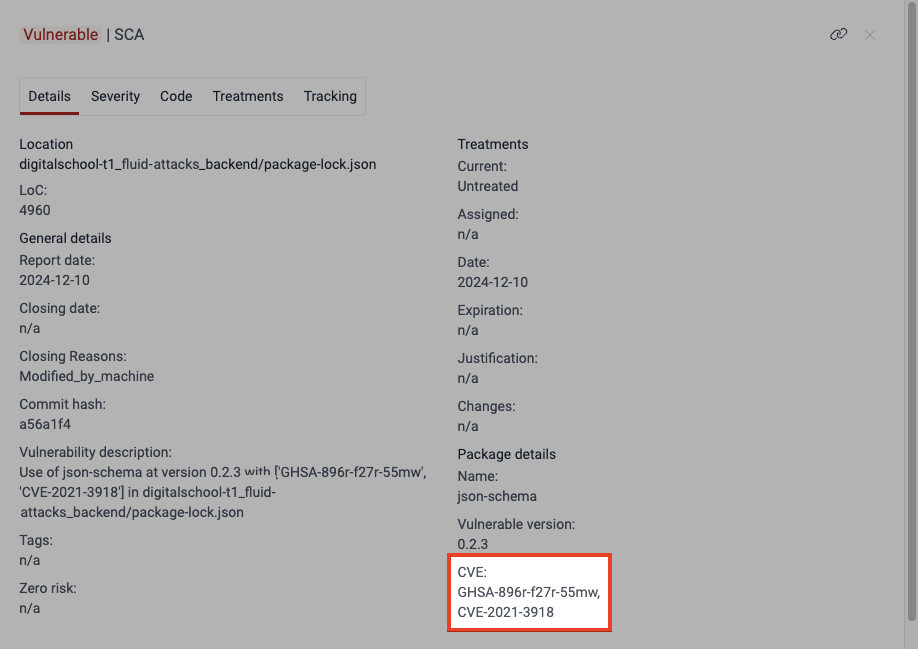
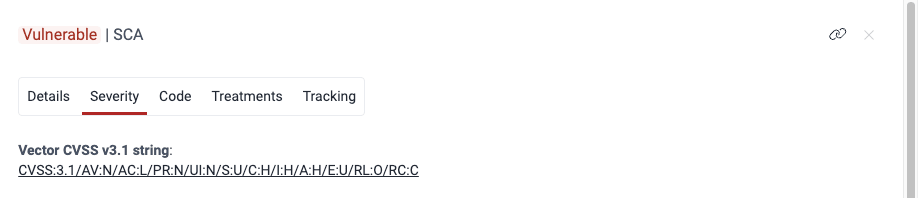
- Switching to the Severity tab, you can learn the CVSS vector string assigned by Fluid Attacks (CVSS v3.1 score: 8.5).
- Checking the advisory by NIST and the responsible CNA, you can learn the CVSS vector string assigned by them (CVSS v3.1 score: 9.8).
- Comparing both vector strings available (v3.1), you can notice that Fluid Attacks specified E, RL and RC, bringing more accuracy to the CVSS score calculation.
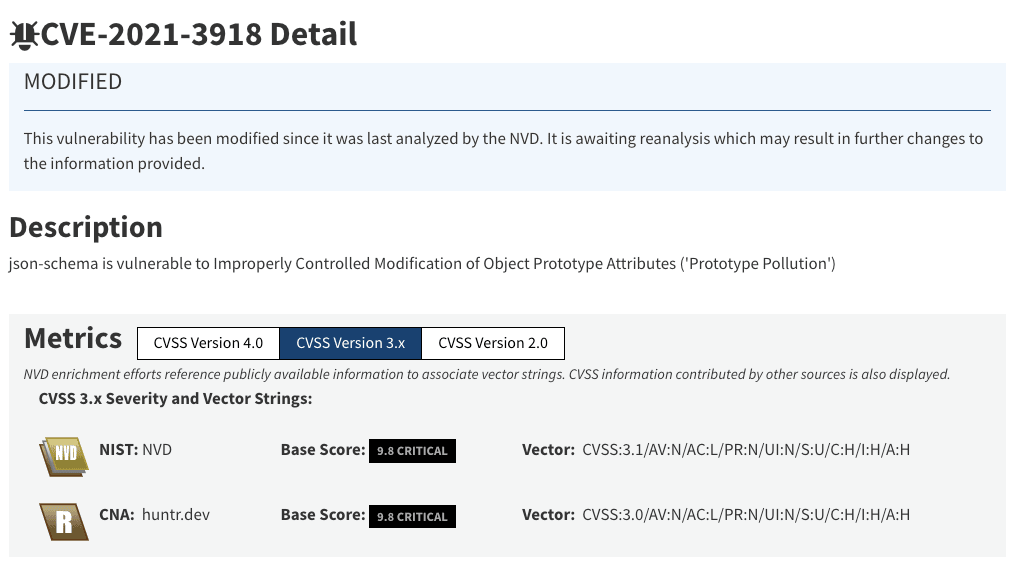
- Source: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
- Fluid Attacks: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C
- The result is a significant difference of 1.3 units or, in terms of the qualitative severity rating, one level.

In this case, the CVSS v4.0 vector string calculated by Fluid Attacks, specifying E as noted, is the following and equals a score of 8.1, lower than that obtained with v3.1: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N/E:U

If Fluid Attacks' hacking team performs a review of a vulnerability reported by SCA scans and can prove that the vulnerability is exploitable, the CVSS score is adjusted to reflect this.