Virtual Private Network (VPN)
The VPN is a common component that is responsible for establishing secure connections between Fluid Attacks’ VPC and the private network of some of Fluid Attacks’ clients.
Its main purpose is to provide a method to reach resources that are not accessible via the Internet and are essential for Fluid Attacks’ service.
These resources are typically source code repositories and pre-production application environments.
Public Oath
- Fluid Attacks will look for private-connection solutions that balance security, usability, and standardization in order to provide a service that is as seamless and scalable as possible.
- An authentication architecture that uses role-based access control, strong passwords, and multiple factors will be used for controlling who accesses client networks.
- When possible, detailed logs of network activity will be provided to clients via Integrates.
Architecture
- The
vpncomponent is managed as code using Terraform. - Sensitive information for establishing secure connections with client networks is stored in encrypted YAML files using Mozilla SOPS.
- It implements two different architectures, Cloudflare and AWS.
Cloudflare
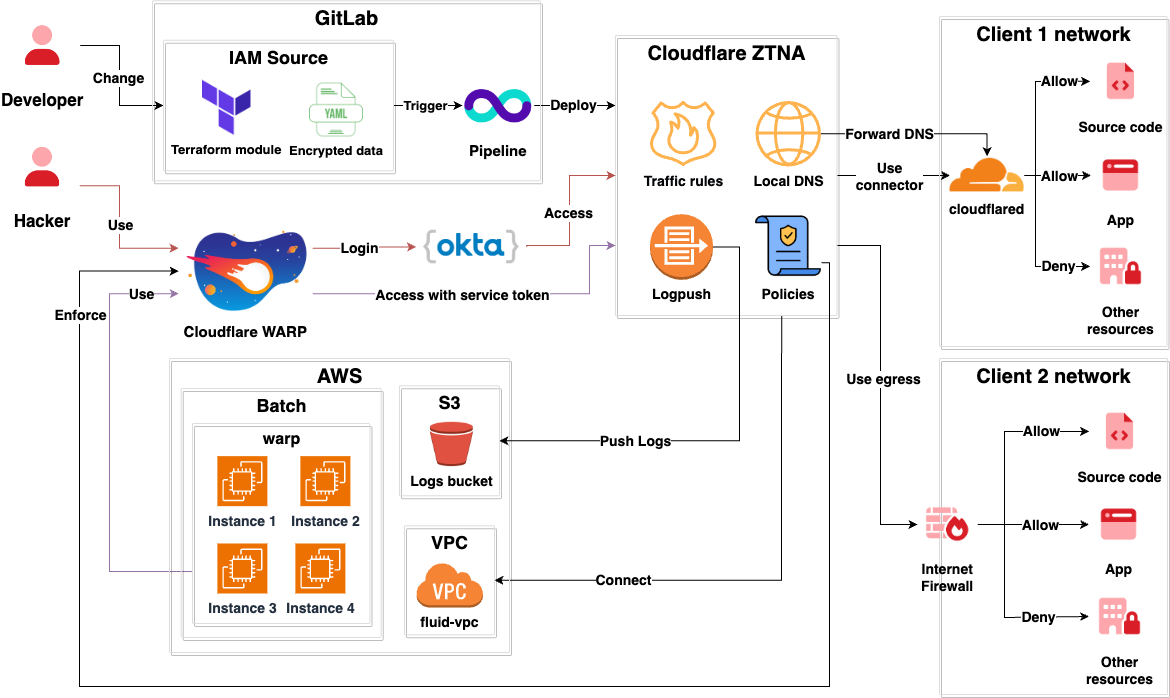
- This architecture uses Fluid Attacks’ Cloudflare network in order to connect Fluid Attacks and its clients.
- Fluid Attacks Hackers use Cloudflare WARP to connect to the Cloudflare network.
- Authentication to Cloudflare WARP for hackers is done via Okta.
- An AWS Batch compute environment called
warpInitialize machines with Cloudflare WARP installed so they can reach the networks of clients. - Authentication to Cloudflare WARP for AWS Batch is done using a service token.
- Posture policies like having the latest OS version, firewall turned on, and an encrypted hard drive are enforced over all devices connected to WARP.
- The AWS VPC is accessible via WARP for developers to perform debugging.
- Navigation logs for traffic between Fluid Attacks and the networks of clients are pushed to an S3 bucket using Cloudflare Logpush.
- Minimum privilege traffic rules exist so that only users with permissions have access to the clients networks.
Networks of clients can be reached in two different ways.
Connector
- The client installs
cloudflareon a machine belonging to the network that they want to share with Fluid Attacks. cloudflarecommunicates with Fluid Attacks’ Cloudflare network.- The
cloudflareinstance becomes a pivot machine that allows Fluid Attacks to reach the client network. - As the client is the owner of the
cloudflareinstance running in their network, they can set up minimum-privilege rules for it to only reach those resources that should be accessible. - Internal DNS requests are forwarded to the client’s DNS servers.
Egress
- Fluid Attacks provides a pair of reserved IPv4 public addresses that are used exclusively for reaching the client’s network. These are called
egress ips. - The client exposes the resources that need to be accessed to the Internet and only allows traffic from Fluid Attacks
egress ips.
AWS
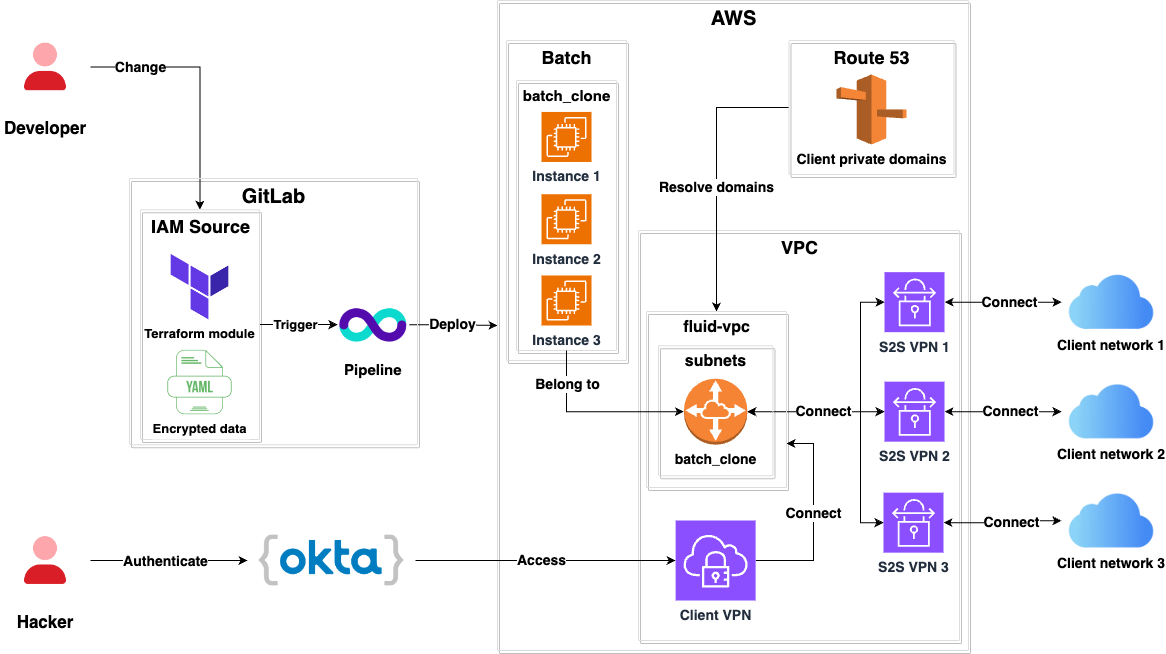
- This architecture is deprecated and will be removed in the future.
- It uses AWS Site-to-Site VPN Connections.
- A subnet called
batch_cloneis routed through all the Site-to-Site VPNs so it can reach the networks of clients. - It uses Route53 to resolve domains within the networks of clients.
- Fluid Attacks Hackers can access hosts in the networks of clients by using the AWS Client VPN.
- Authentication to the AWS Client VPN Endpoint is done via Okta.
Contributing
Please read the contributing page first.
General
- Any changes to vpn infrastructure must be done via merge requests.
- Find the infrastructure source code in the Git repository.
- Find all vpn client configurations in the Git repository. You can use SOPS to decrypt such values.
Accessing the VPN
You can connect to the vpn and gain access to our AWS VPC and client private networks. To do so, you need to:
- Go to the VPN Self-Service portal:
- Log in with your Okta Credentials.
- If you do not have enough permissions, please contact help@fluidattacks.com.
- From the portal:
- Download the vpn client configuration.
- Download and install the AWS Client VPN for your Operating System.
- Open the AWS Client VPN and import the downloaded configuration.
- Connect to the VPN.
More about Common

Tip
Have an idea to simplify our architecture or noticed docs that could use some love? Don't hesitate to open an issue or submit improvements.