Correlate your threat model to vulnerabilities
The Design Map section provides you with a correlation between your threat model and the vulnerabilities Fluid Attacks has detected in your system. These threat matches are shown to you irrespective of whether such vulnerabilities have a 'Vulnerable' or 'Safe' status. Thanks to the information in this section, you can prioritize vulnerability remediation strategically, focusing on those flaws that pose the greatest risk to your business as defined by your threat model.
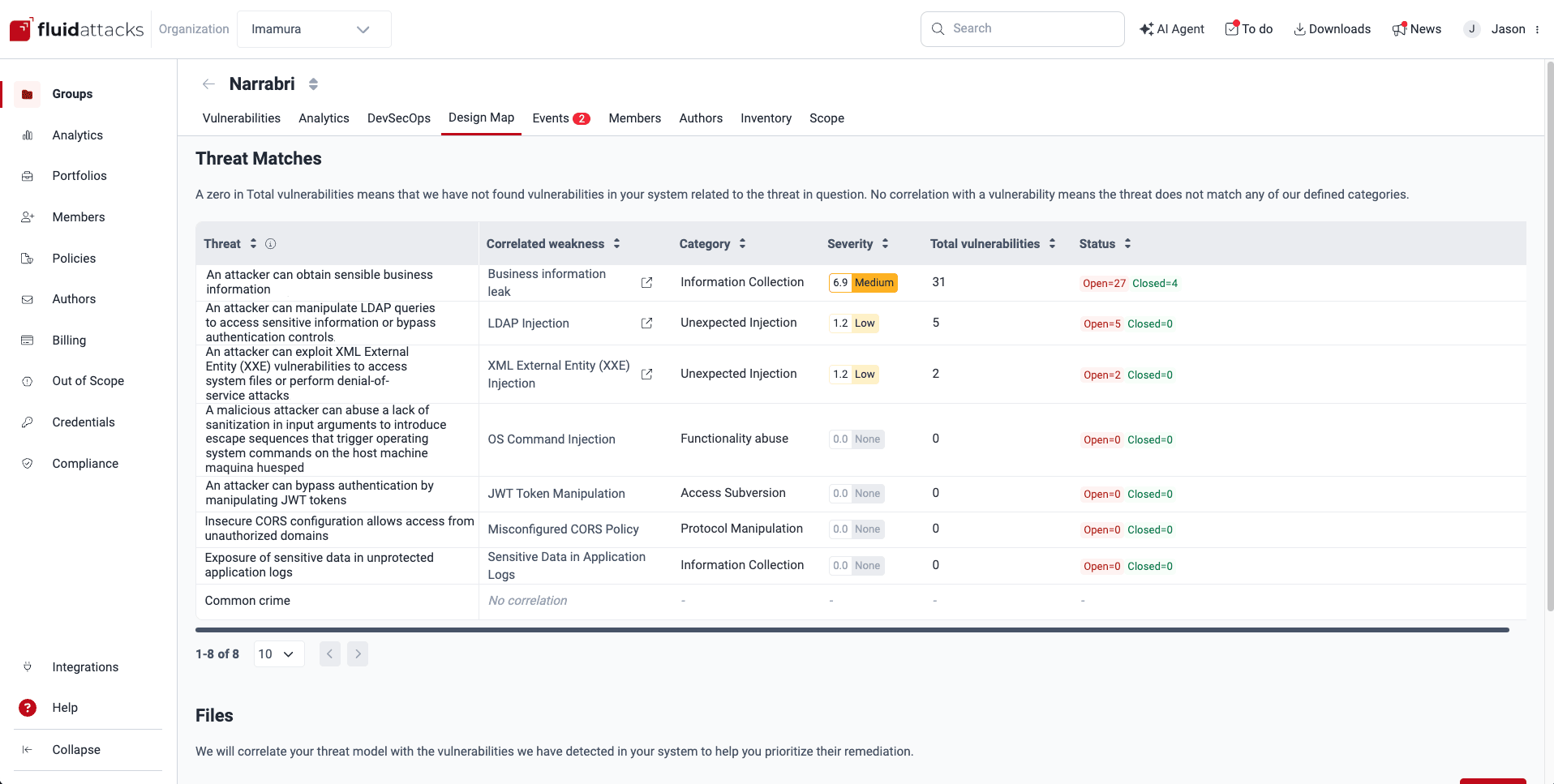
See the threat matches
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerOnce Fluid Attacks has analyzed the appropriately formatted file(s) you have provided detailing your threat model, the table in Threat Matches shows you the following information:
- Threat: The detailed descriptions of threats to your business as provided in your model
- Correlated weakness: The vulnerabilities from Fluid Attacks' categorization whose descriptions match those of the threats in your model
- Category: The names of the categories where Fluid Attacks has included the weaknesses
- Severity: The default CVSS scores Fluid Attacks has assigned to the related vulnerabilities
- Total vulnerabilities: The total paths in your system where the weaknesses have been present
- Status: Total vulnerabilities by their Status:
- Closed: Vulnerabilities that are no longer present
- Open: Vulnerabilities that are present

The value 'No correlation' means that the threat does not match any of Fluid Attacks' defined categories.

A zero in Total vulnerabilities means that Fluid Attacks has not found vulnerabilities in your system related to the threat in question.

Fluid Attacks applies your threat model to the entire group, not to specific components.
Manage threat model files
 Role required: User, Vulnerability Manager or Group Manager
Role required: User, Vulnerability Manager or Group ManagerYou need to upload at least one correctly formatted spreadsheet detailing your threat model so that Fluid Attacks can do the correlation with the reported vulnerabilities. The name(s), description(s) and upload date(s) of those resources are shown in the table under Files.
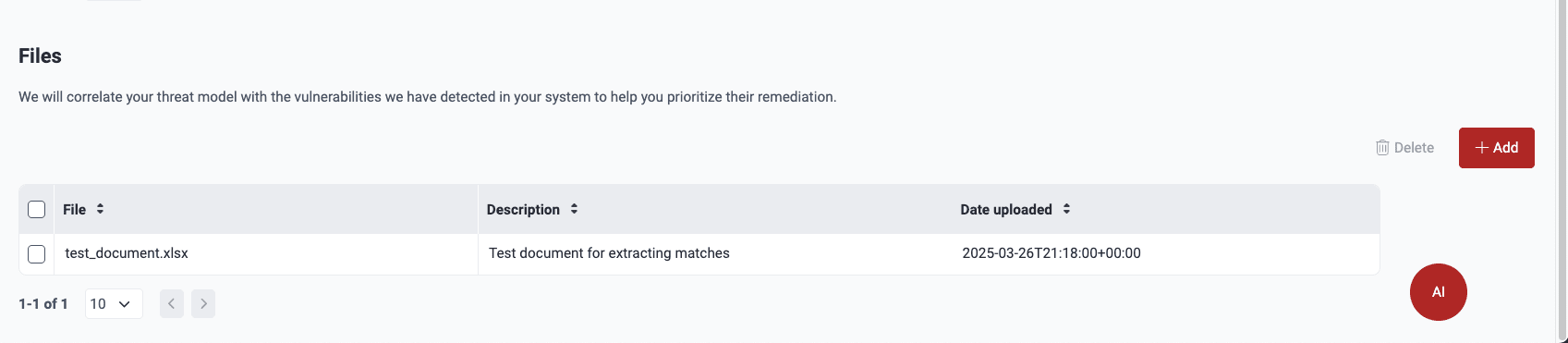
- File: The spreadsheet's name
- Description: Your team's concise account of the file's content
- Date uploaded: When the spreadsheet was added to the platform
Upload threat model files

File requirements:
- The file you upload must be a spreadsheet with the .xlsx or .xls extension. No other kind of file is supported.
- Threat descriptions in the spreadsheet must be organized vertically, in the same column(s). Fluid Attacks' analysis takes into account each column with relevant threat descriptions across the sheets in your file.
- The file must indeed have threat descriptions. If you, for example, add a spreadsheet that only lists security requirements, the analysis is not performed.

Make sure your files meet the above requirements. Otherwise, you are shown the 'processing' message endlessly.

Give the threat-related column an obvious name, such as one including the word "threat."
When you have a spreadsheet with your threat model that is appropriately formatted, you can add it by following these steps:
-
Navigate to Design Map.
- Click on the Add/Add file button.
- Upload a spreadsheet with the .xlsx or .xls extension and write a brief description of the file's contents (maximum 200 characters).
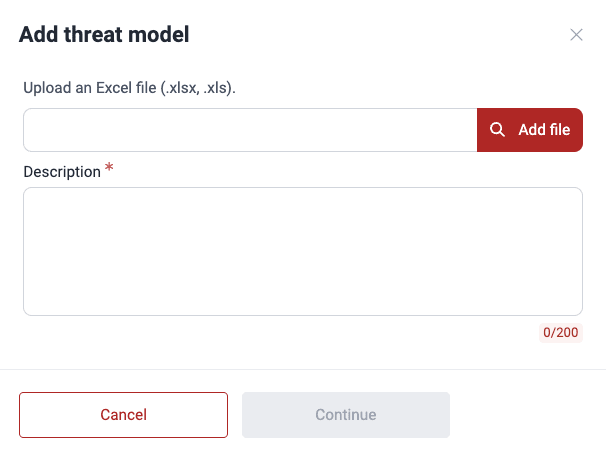
- Click on Continue.
When the analysis is done, you can see the results under Threat Matches.
Delete threat model files

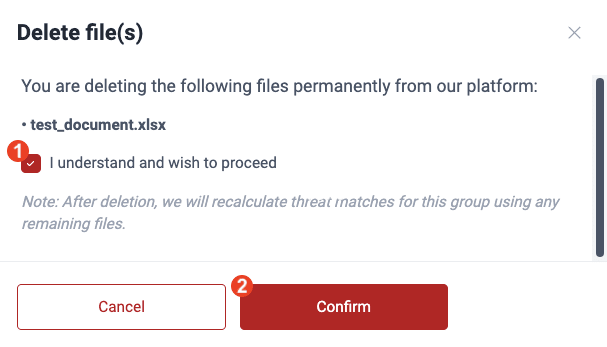
When you delete a threat model file, threat matches are recalculated using any remaining file.
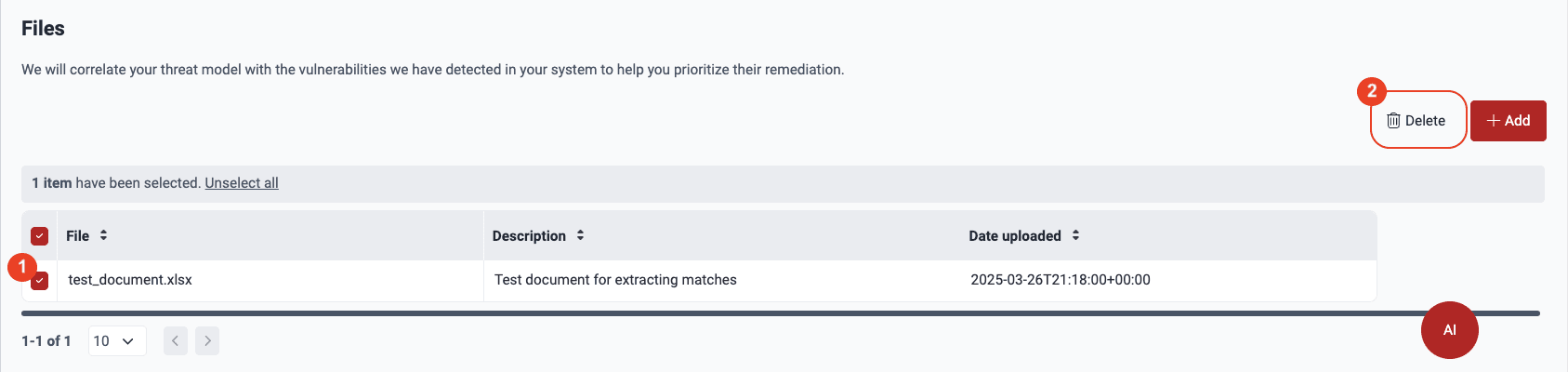
Follow these steps to delete threat model files:
-
Navigate to Design Map.
- Under Files, select the file(s) using the checkbox(es) and click on the Delete button.
- Acknowledge that you understand that once the file is removed, threat matches are recalculated with any files left. Click on the checkbox and then Confirm.

Have questions about the security of your data? Get some answers in this Data security and privacy section.

Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.