Identify and address vulnerabilities from IntelliJ
Fluid Attacks' IntelliJ IDEA plugin offers the following functions:
To access the above functions, click on the Fluid Attacks extension in the IDE's left-side menu.

See vulnerable file and code line
You can view vulnerabilities reported in the Fluid Attacks platform from the IntelliJ IDEA:
Click on the Fluid Attacks icon in the left-side menu. You are then presented with a comprehensive list of weaknesses detected in your code.

Click on the weakness of your interest to view the names and vulnerable lines of all affected files.
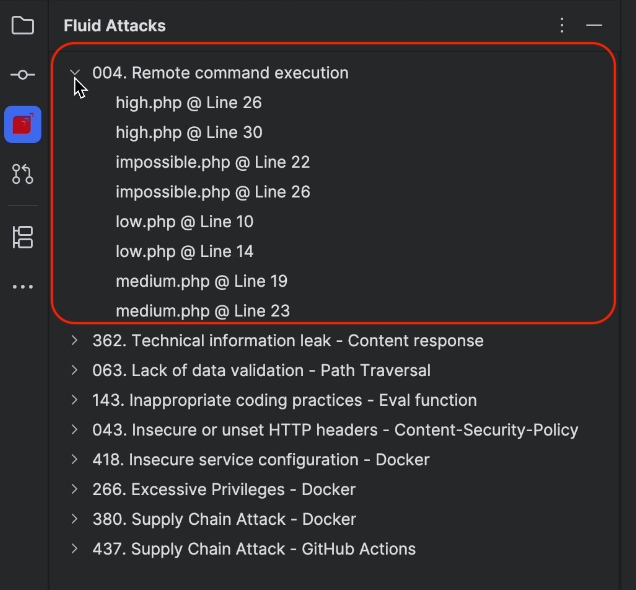
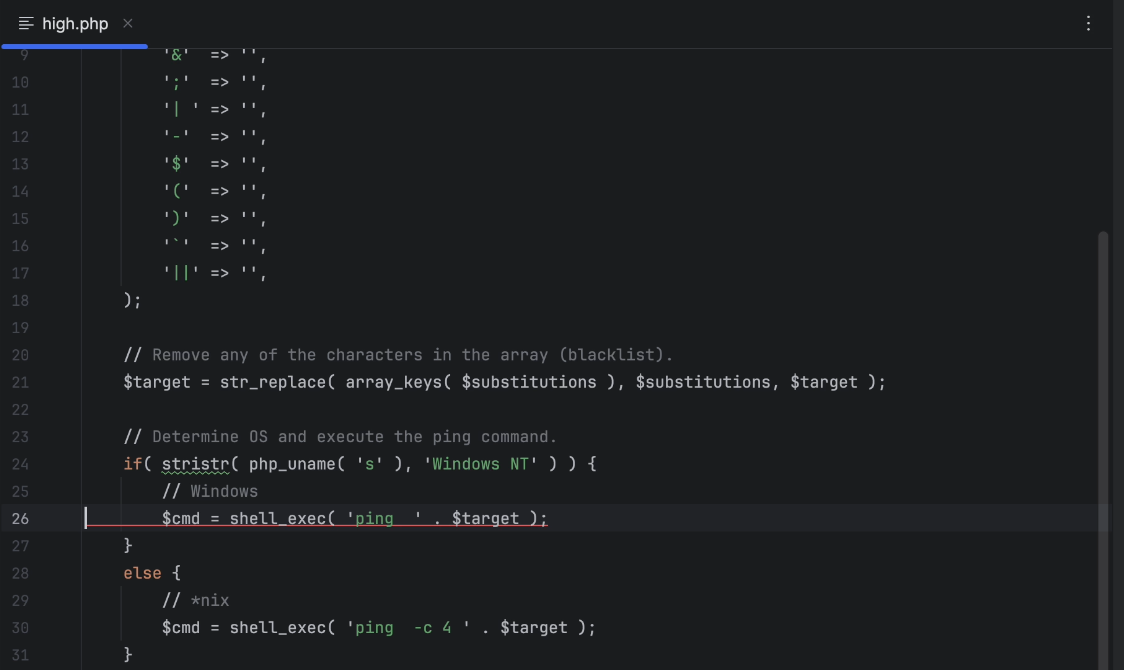
Select a file of your interest to identify the line of code where the vulnerability is present, which is underlined with red.
Get AI generated remediation guides

-
Click on the Fluid Attacks icon in the IDE's left-side menu.
-
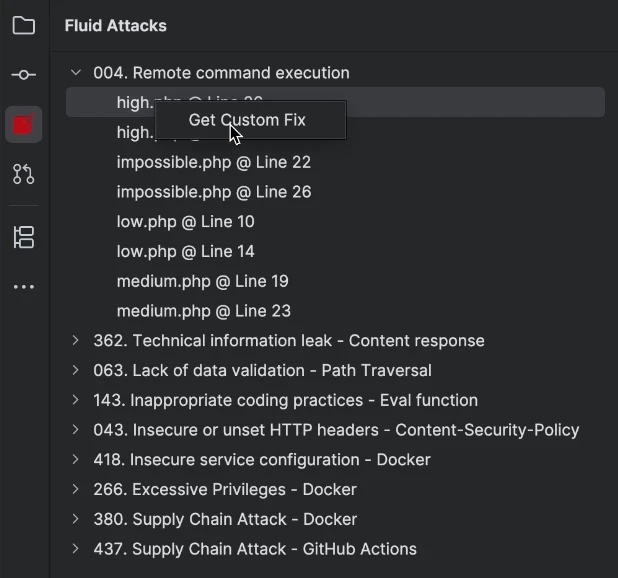
Expand the weakness you wish to explore by clicking on its name.
Right-click on a vulnerable file and choose the Get Custom Fix option.
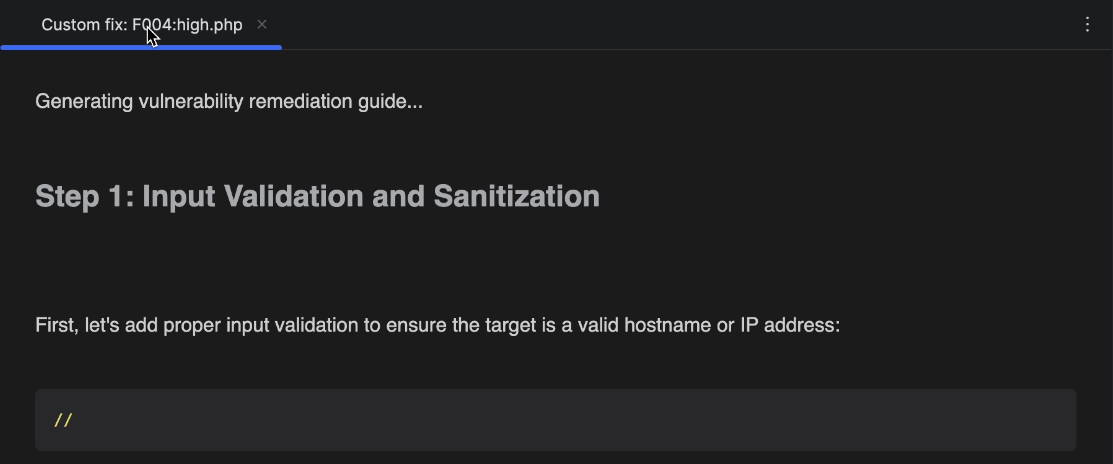
The corresponding editor tab appears and starts displaying the remediation guide.
 Free trial
Free trial