Install the IntelliJ plugin

Plugin support information:
- Android Studio: Meerkat (2024.3.1) and later
- AppCode: Build 243.0 and later
- Aqua: 2024.3 and later
- IntelliJ IDEA Community: 2024.3 and later
- IntelliJ IDEA Ultimate: 2024.3 and later

See more specs of the IntelliJ plugin.
 Fluid Attacks' IntelliJ plugin, along with our entire suite of local tools and extensions, is available free of charge.
Fluid Attacks' IntelliJ plugin, along with our entire suite of local tools and extensions, is available free of charge.Fluid Attacks' IntelliJ plugin enables you to view the following directly on IntelliJ IDEA and other supported IDEs:
- A list of the types of vulnerabilities and their specific cases that Fluid Attacks has identified so far in the source code of your products.
- The specific lines of code in which a vulnerability detected by Fluid Attacks' tools or hacking team is present.
To install the plugin please follow these steps:
- Go to JetBrains Marketplace and use the search bar to look for 'Fluid Attacks'.
- Click on the search result to be directed to the Fluid Attacks plugin page. There, click the Get button.
- Log in to Fluid Attacks' platform.
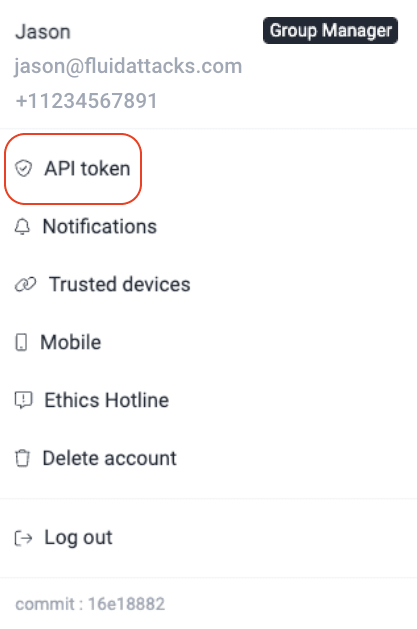
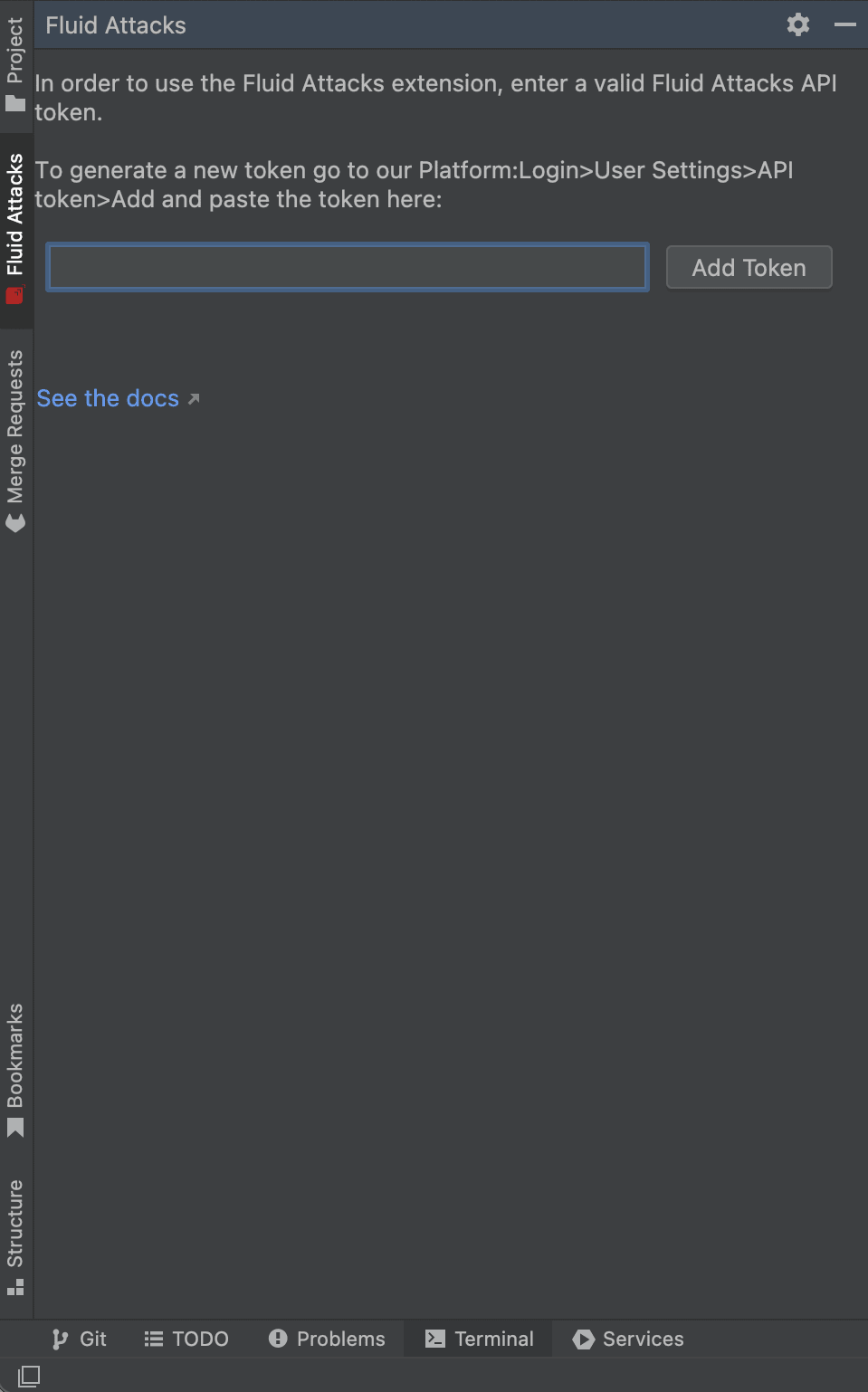
- Generate and copy an API token from the platform (for detailed instructions, see Generate or revoke the API Token).
- Go to the IDE and click on the Fluid Attacks tab on the left side, then paste the API token in the provided field and click on Add Token.

Alternatively, in the IDE, such as IntelliJ IDEA, open your settings and click on Plugins, then search for 'Fluid Attacks' in the Marketplace tab.

If installing the plugin from the IDE, click the Install button next to the search result. When it is done, restart IntelliJ IDEA.
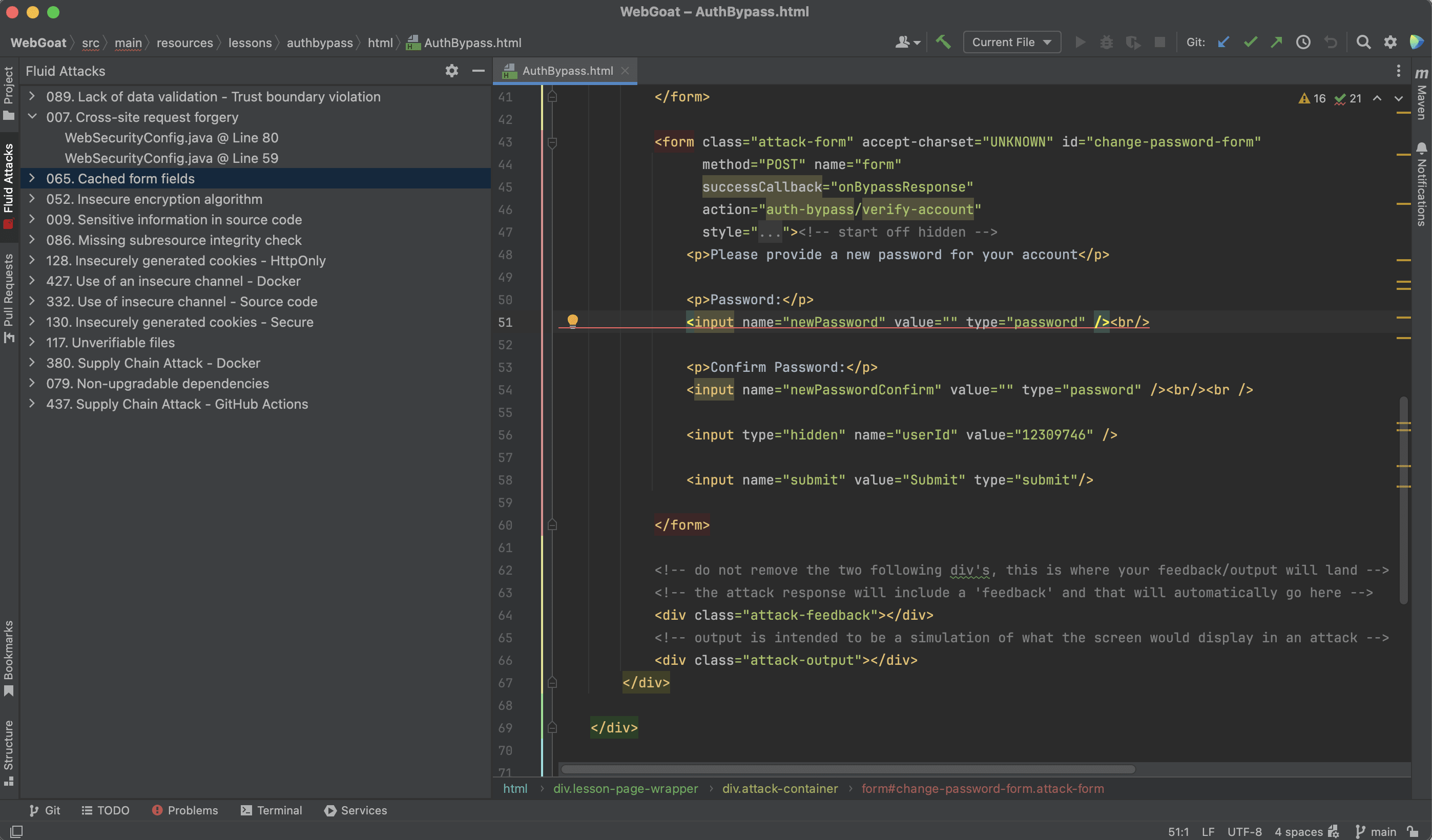
Upon providing the token, the tab reloads and shows you a tree view with the vulnerable locations in your repository, categorized by type of vulnerability. Clicking on a location takes you to the relevant line(s) in the respective file.

Free trial
Search for vulnerabilities in your apps for free with Fluid Attacks' automated security testing! Start your 21-day free trial and discover the benefits of the Continuous Hacking Essential plan. If you prefer the Advanced plan, which includes the expertise of Fluid Attacks' hacking team, fill out this contact form.