Install and use MCP for AI tool integration
Fluid Attacks' Model Context Protocol (MCP) server is a helpful software component that allows AI systems to connect and work with the Fluid Attacks platform over the Internet.
Thanks to this integration, you can query the platform using natural language without leaving your preferred AI tool. This guide explains how to
- install the local MCP server in Claude;
- use the remote MCP server in Cursor and VS Code,
and provides a couple of examples.

Tips:
- Start chats with a mention of Fluid Attacks' API (e.g., "Using Fluid Attacks' API,").
- Always specify whether your requests are at the group or the organization level.
- For requests at the group level, specify the name of the organization as well.
Capabilities
Fluid Attacks' MCP server has only read capabilities. You cannot modify or create anything in Fluid Attacks' platform. These are its capabilities:
- Retrieve analytics information for an organization or group
- Retrieve detailed vulnerability information
- Access to the documentation in the Help Center
- Configure and execute Fluid Attacks' SAST and SCA scanners (Docker required)
Requirement
The MCP server requires you use a valid API token.
MCP server in Claude

See the requirements of the MCP server on Claude.
Install the runtime environment
Follow these steps to install Node.js, which is required for using Fluid Attacks' MCP server. If you already have Node.js v22 installed, simply skip to the next section according to your need.
- It is recommended that you install Node Version Manager (nvm), as it allows you to have different versions of Node.js and switch between them according to your current need. To install nvm, open your terminal and run the following:
- Install the Node.js version 22 with the following command (v18 or higher is required):
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.40.2/install.sh | bashClose and reopen your terminal or run the following command to load nvm into your current session:
\. "$HOME/.nvm/nvm.sh"nvm install 22Setup in Claude
Set up Fluid Attacks' MCP server in Claude following these instructions:
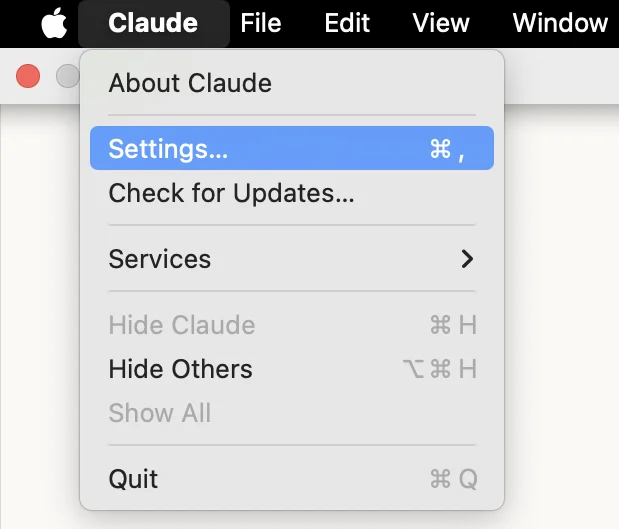
- On Claude, go to the menu bar, click on Claude and then Settings.
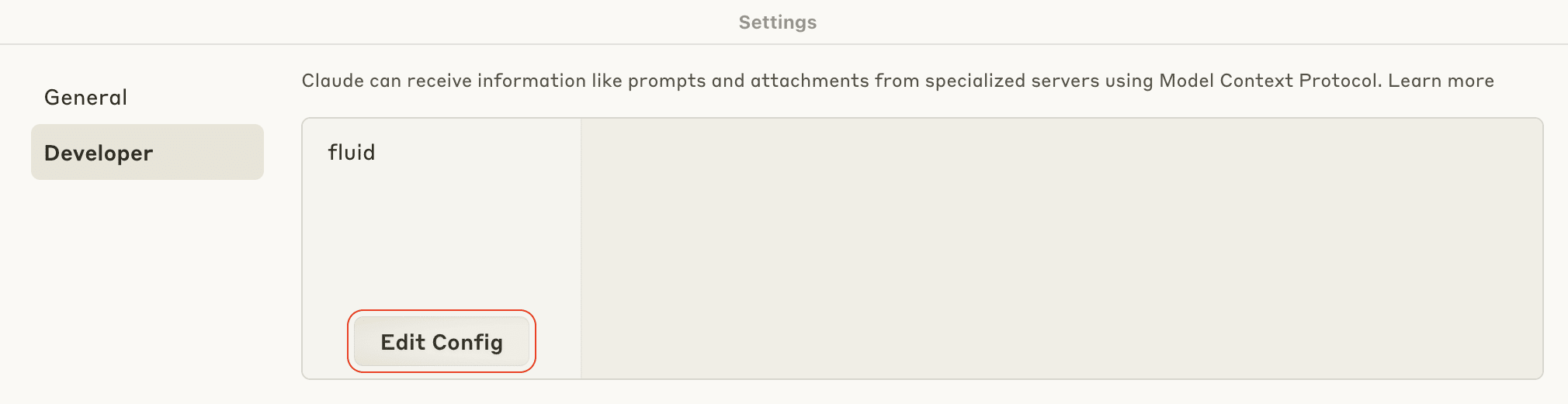
- Switch to the Developer tab and click the Edit Config button.
- You are presented with a folder that contains the file claude_desktop_config.json. Open this file with a text editor.
- Paste the following into the configuration file, replacing
<your_api_token_here>with the previously generated Fluid Attacks API token. - Save the file and close both it and Claude.
{
"mcpServers": {
"fluidattacks-mcp": {
"command": "npx",
"args": [
"--cache",
"/tmp/fluidattacks-mcp",
"-y",
"@fluidattacks/mcp"
],
"env": {
"API_TOKEN": "<your_api_token_here>"
}
}
}
}To interact with the platform, reopen Claude and start chatting! See an example below.
Example in Claude
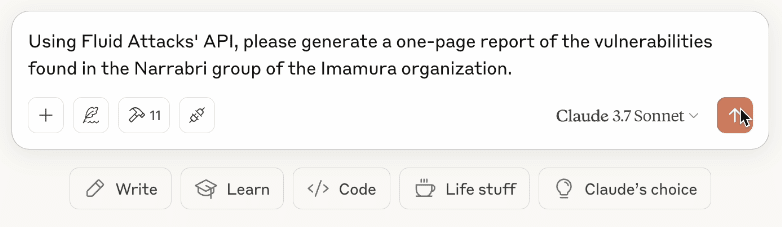
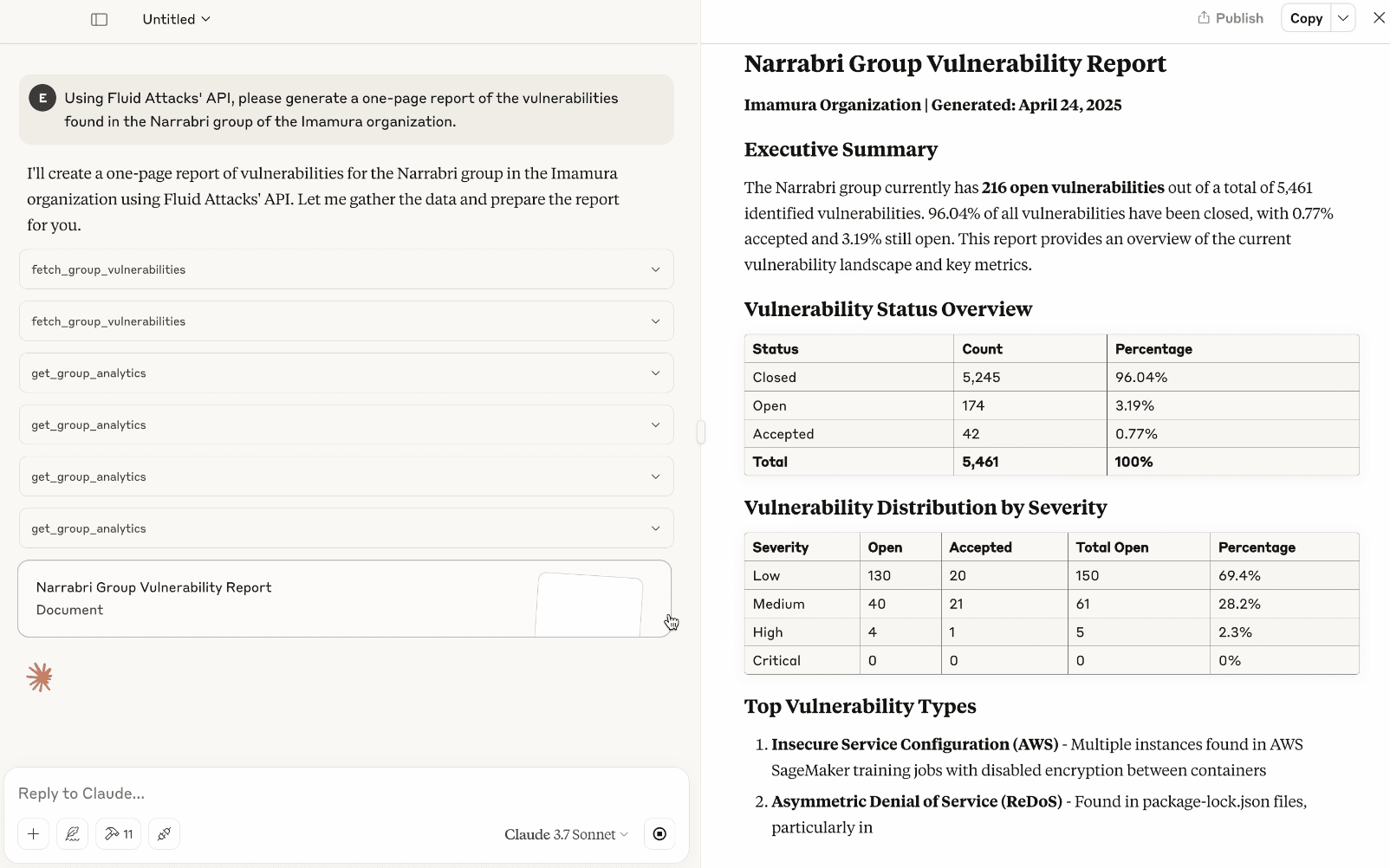
The following example shows the generation of a vulnerability report for a specific group in a specific organization.
The prompt is the following:
"Using Fluid Attacks' APl, please generate a one-page report of the vulnerabilities found in the Narrabri group of the Imamura organization."
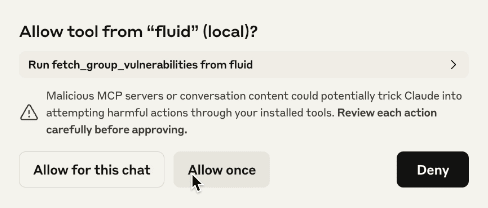
Claude asks for permission before using a tool by the MCP server. The following screenshot references the fetch_group_vulnerabilities tool, which accesses the group's vulnerability information (like vulnerability status and severity).

Check out the description of each tool.
Claude then mentions the tools run and provides an outline of the report while generating the one-page document.
Remote MCP server in Cursor and VS Code

Do not forget to generate an API token for the setup.
Setup in Cursor and VS Code
Use Fluid Attacks' remote MCP server in Cursor or VS Code following these instructions:
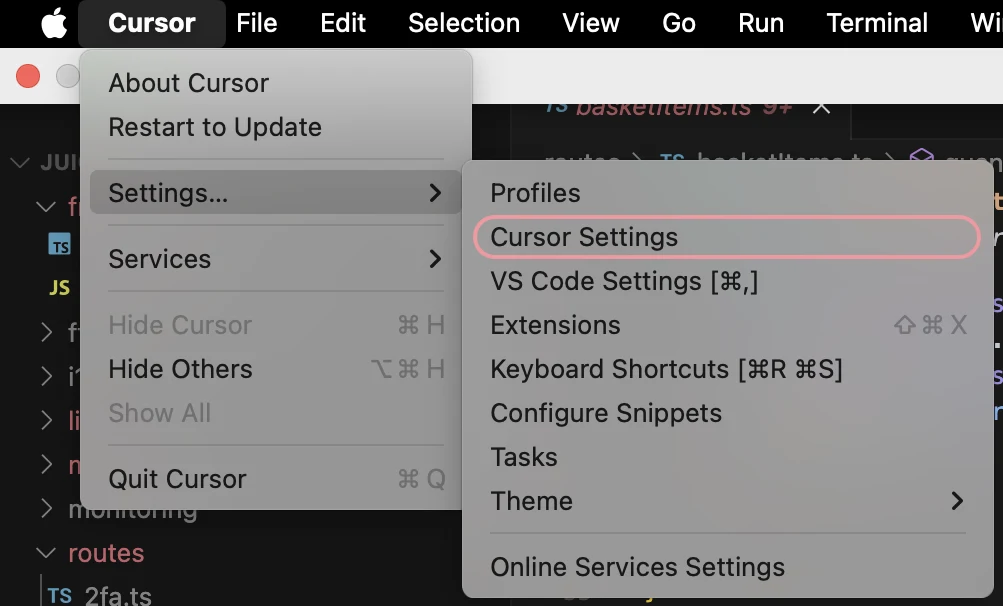
- Go to the menu bar, click on Cursor/VS Code and then go to Settings... > Cursor Settings/VS Code Settings.
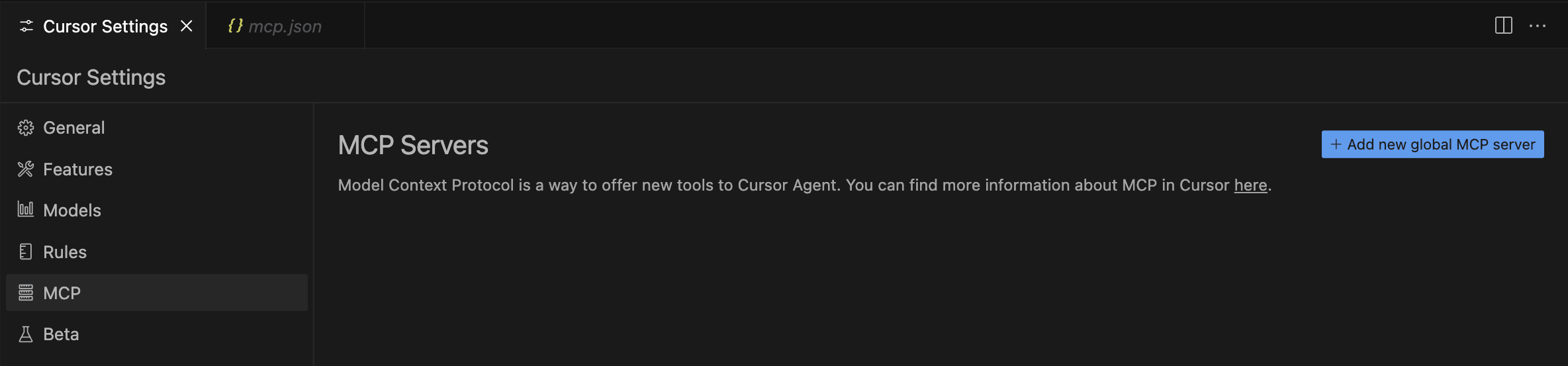
- Navigate to MCP and click on Add new global MCP server.
- Paste the following into the configuration file, replacing
<your_api_token_here>with the previously generated Fluid Attacks API token. Bear in mind that the field"type": "http"is obligatory only in VS Code. - Save the file and close it.
{
"mcpServers": {
"fluidattacks-mcp": {
"type": "http",
"url": "https://app.fluidattacks.com/mcp/messages/",
"headers": {
"Authorization": "Bearer <your_api_token_here>"
}
}
}
}Open a chat to start interacting with the platform. For example, in Cursor, just type the following into the input bar: >Cursor: New Chat. See an example of a chat in below.
Example in Cursor
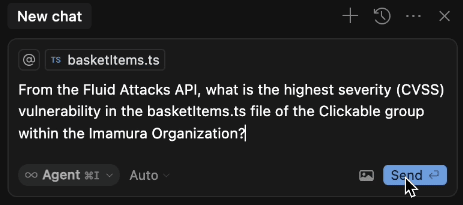
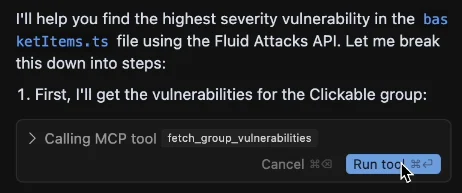
The following example shows the request for the vulnerability with the highest CVSS score in a specific file within a specific group in a specific organization.
The prompt used is the following:
"From the Fluid Attacks API, what is the highest severity (CVSS) vulnerability in the basketitems.ts file of the Clickable group within the Imamura Organization?"
Cursor asks for confirmation before running a tool by the MCP server. The following screenshot references the fetch_group_vulnerabilities tool, which retrieves vulnerability information (like vulnerability status and severity) from a specific file.

Read the description of each tool.
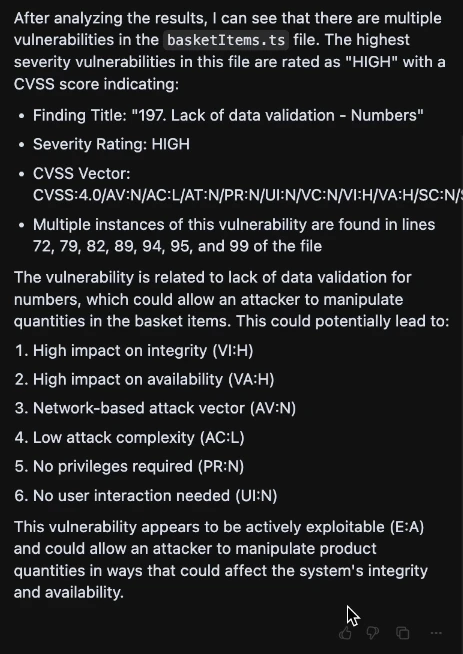
Cursor then responds with the type of vulnerability's name, as well as breaks down its CVSS score and informs of the lines of code where the vulnerability is present.
Share the server configuration with your team

Requirements:
- Have Node.js installed
- Create the environment variable called
FLUID_ATTACKS_API_TOKEN
You can keep the Fluid Attacks MCP server configuration in your code repository for your entire team to use. Simply add the following to your IDE configuration folder within your repository and have your team meet the above requirements.
{
"mcpServers": {
"fluidattacks-mcp": {
"command": "npx",
"args": [
"--cache",
"/tmp/fluidattacks-mcp",
"-y",
"@fluidattacks/mcp",
"https://app.fluidattacks.com/mcp/messages/"
],
}
}
}With this option, the API token is not hardcoded, as it stays an environment variable, and the MCP server configuration can be versioned with no issues.
Security considerations
- API token security: Store tokens securely, never commit to version control
- Data sensitivity: Be cautious when sharing vulnerability data
 Development: Dive deep into the MCP server.
Development: Dive deep into the MCP server.