Install the MCP for AI tool integration
This guide explains how to install the local MCP server in Claude and use the remote MCP server in Cursor and VS Code. Besides, you can learn how to integrate Fluid Attacks security scanners into your software development lifecycle (SDLC) using AI agents.
Prerequisites
- To use the Fluid Attacks MCP Server, you need an AI assistant that supports MCP, such as Claude (via Cursor, Claude Desktop, VS Code, etc.).
- Do you want to access information about vulnerabilities? If so, you need a Fluid Attacks API token. This is optional for public tools.
- Do you want to run security scans? If so, you need to have Docker installed. Also, it is recommended to configure an AGENTS.md file in the project root directory.
MCP server in Claude

See the requirements of the MCP server on Claude.
Install the runtime environment
Follow these steps to install Node.js, which is required for using Fluid Attacks' MCP server. If you already have Node.js v22 installed, simply skip to the next section according to your needs.
- It is recommended that you install Node Version Manager (nvm), as it allows you to have different versions of Node.js and switch between them according to your current needs. To install nvm, open your terminal and run the following:
- Install the Node.js version 22 with the following command (v18 or higher is required):
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.40.2/install.sh | bashClose and reopen your terminal or run the following command to load nvm into your current session:
\. "$HOME/.nvm/nvm.sh"nvm install 22Setup in Claude
Set up Fluid Attacks' MCP server in Claude following these instructions:
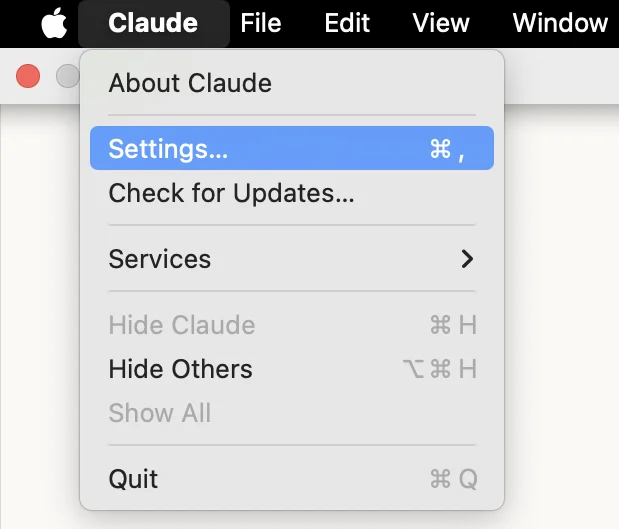
- On Claude, go to the menu bar, click on Claude and then Settings.
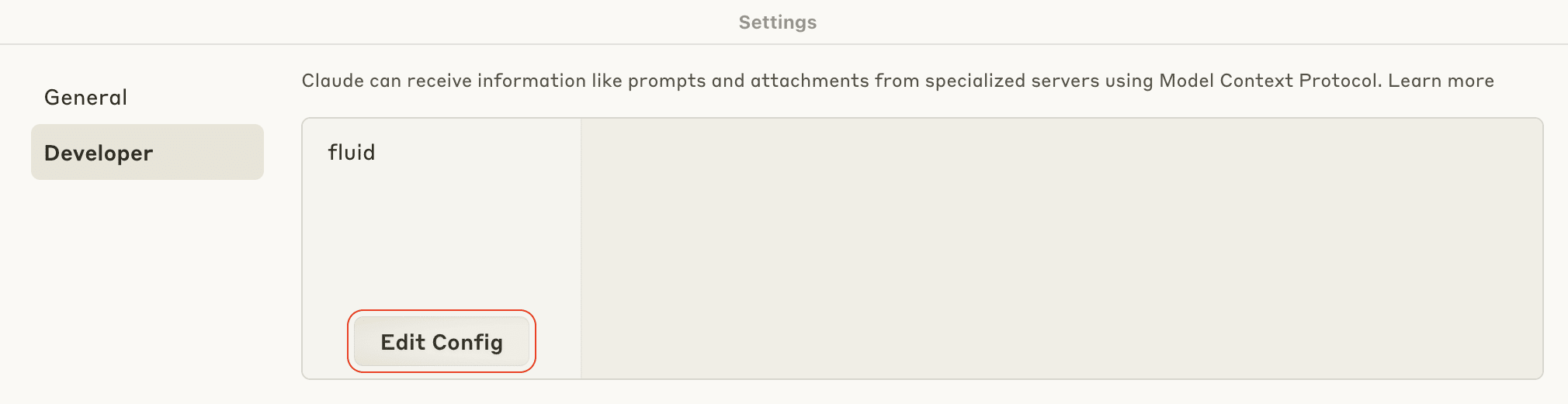
- Switch to the Developer tab and click the Edit Config button.
- You are presented with a folder that contains the file claude_desktop_config.json. Open this file with a text editor.
- Paste the following into the configuration file, replacing
<your_api_token_here>with the previously generated Fluid Attacks API token. - Save the file and close both it and Claude.
{
"mcpServers": {
"fluidattacks-mcp": {
"command": "npx",
"args": [
"--cache",
"/tmp/fluidattacks-mcp",
"-y",
"@fluidattacks/mcp"
],
"env": {
"API_TOKEN": "<your_api_token_here>"
}
}
}
}To interact with the platform, reopen Claude and start chatting! See an example below.
Example in Claude
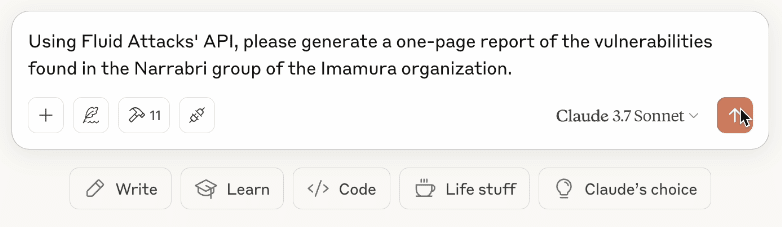
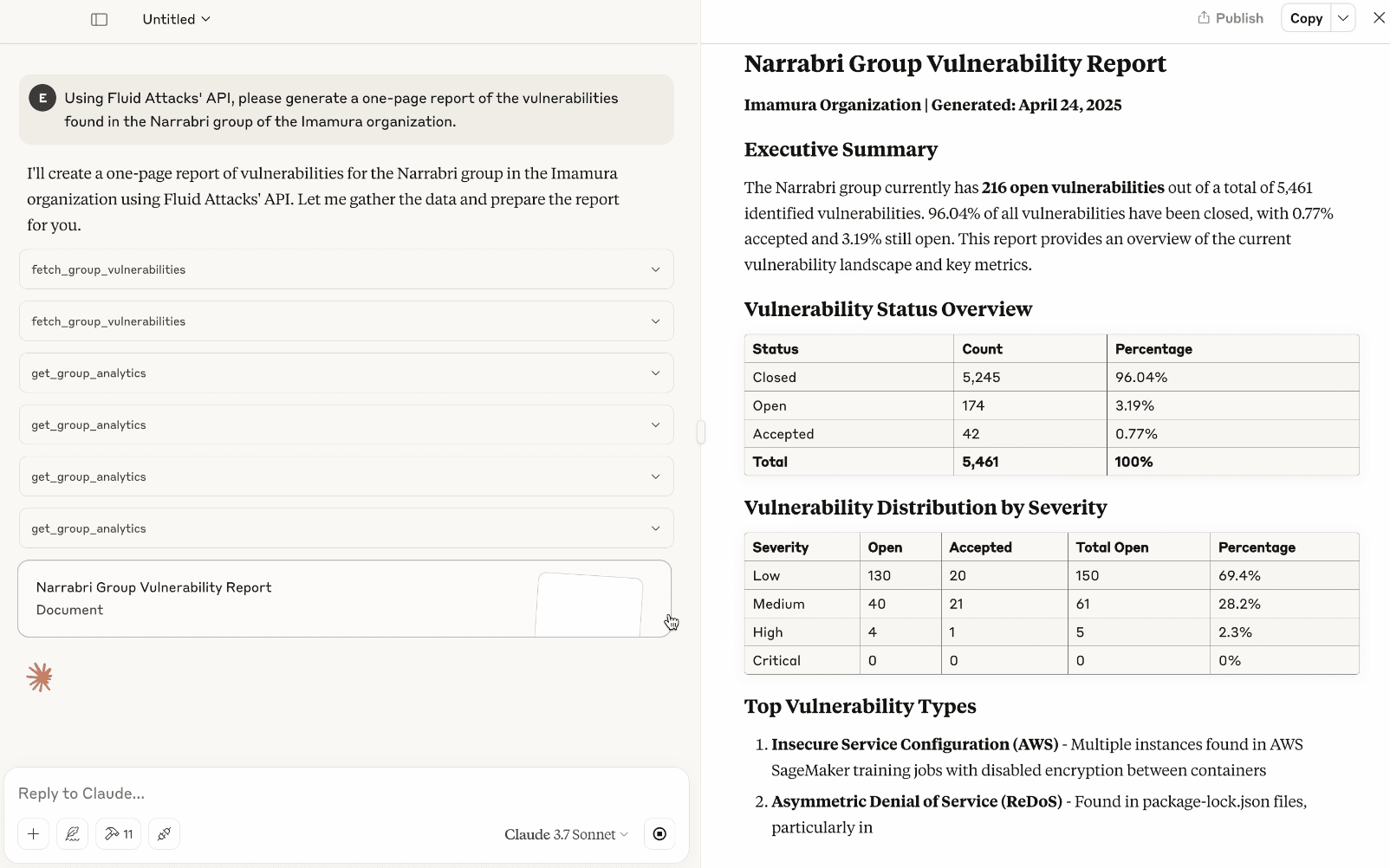
The following example shows the generation of a vulnerability report for a specific group in a specific organization.
The prompt is the following:
"Using Fluid Attacks' APl, please generate a one-page report of the vulnerabilities found in the Narrabri group of the Imamura organization."
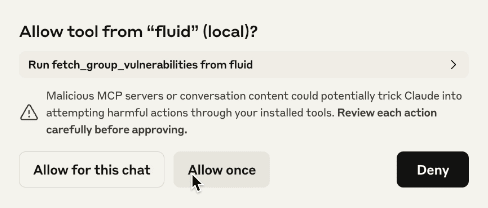
Claude asks for permission before using a tool by the MCP server. The following screenshot references the fetch_group_vulnerabilities tool, which accesses the group's vulnerability information (like vulnerability status and severity).

Check out a description of each tool and capability.
Claude then mentions the tools run and provides an outline of the report while generating the one-page document.
Remote MCP server in Cursor

Do not forget to generate an API token for the setup.
Configuration
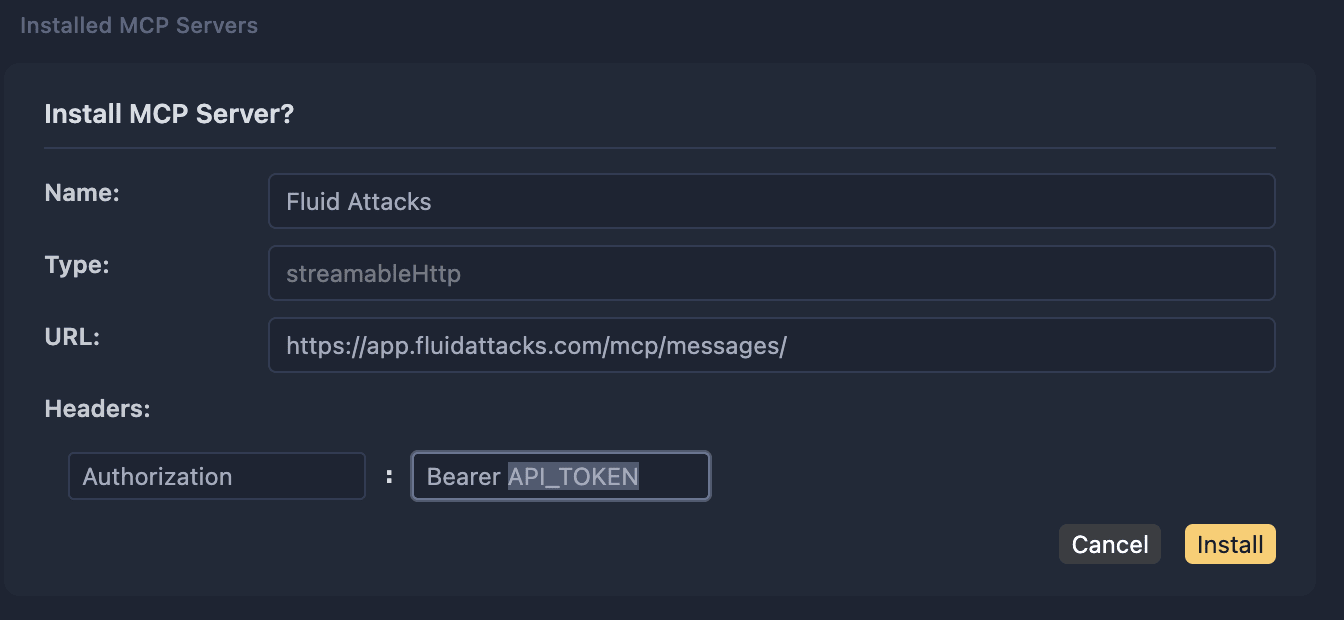
Use Fluid Attacks' remote MCP server in Cursor, following these instructions:
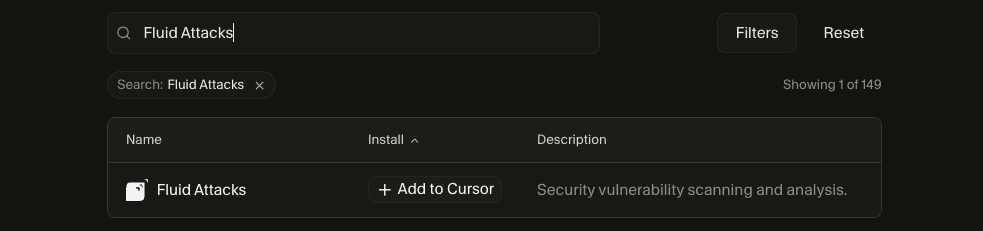
- Go to Cursor's MCP Directory and search for the Fluid Attacks server.
- Click on the Add to Cursor button.
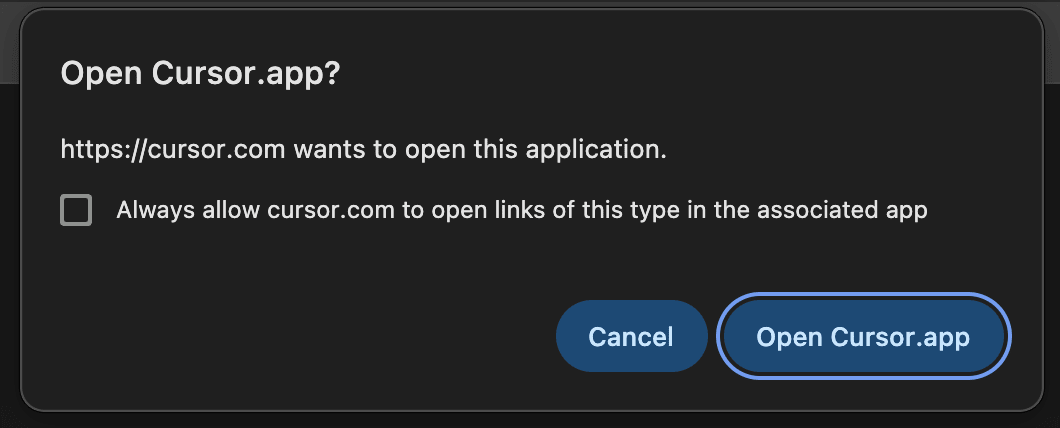
- Once you see this warning message in your browser, click the Open Link or Open Cursor.app button.
- Optional: Add the token generated from the Fluid Attacks platform. If you do not have a token, you can leave the default setting. Please note that the token is required to access information about your groups on the platform.
- Click on the Install button.
- Verify that the server is active before using it to request vulnerability scans or reports containing information about your groups.
- You can now use the Fluid Attacks MCP server in Cursor.
Example in Cursor
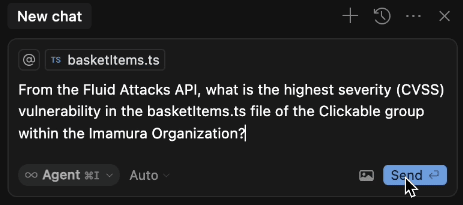
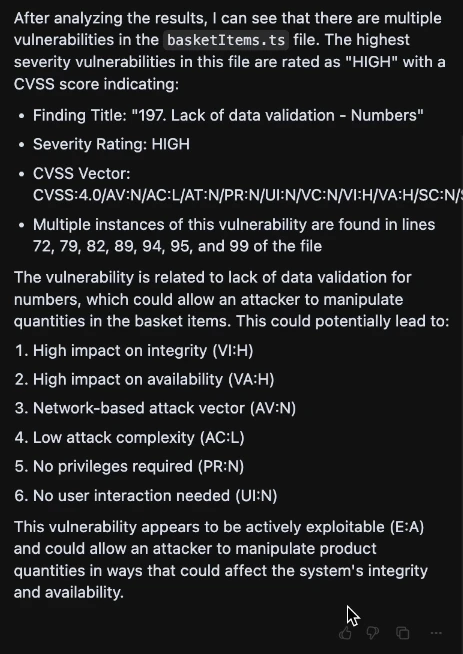
The following example shows the request for the vulnerability with the highest CVSS score in a specific file within a specific group in a specific organization.
The prompt used is the following:
"From the Fluid Attacks API, what is the highest severity (CVSS) vulnerability in the basketitems.ts file of the Clickable group within the Imamura Organization?"
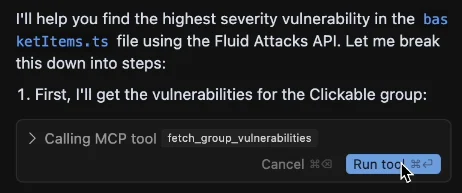
Cursor asks for confirmation before running a tool by the MCP server. The following screenshot references the fetch_group_vulnerabilities tool, which retrieves vulnerability information (like vulnerability status and severity) from a specific file.

Read a description of each tool and capability.
Cursor then responds with the type of vulnerability's name, as well as breaks down its CVSS score and informs of the lines of code where the vulnerability is present.
Remote MCP server in VS Code

Do not forget to generate an API token for the setup.
Configuration
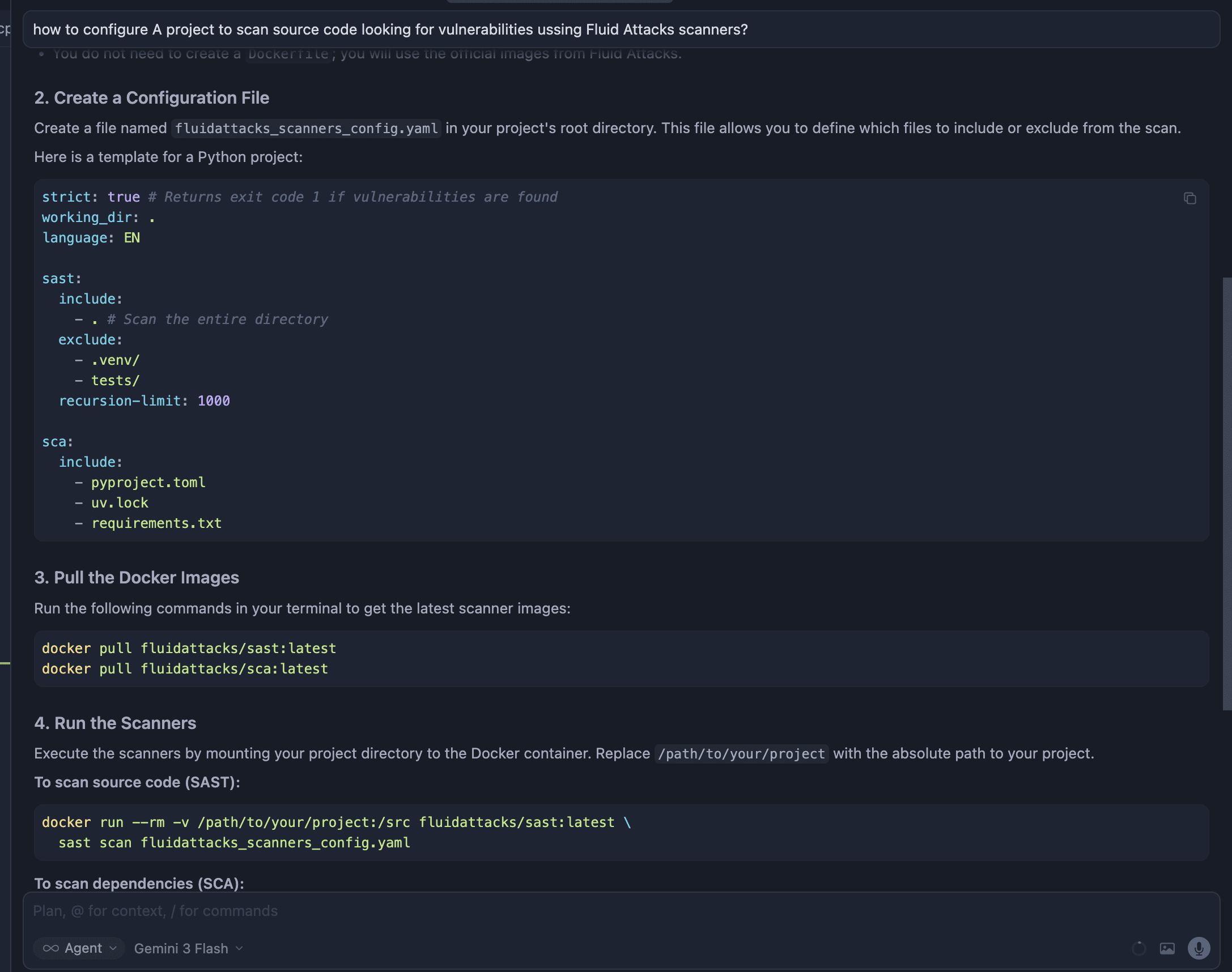
Use Fluid Attacks' remote MCP server in VS Code, following these instructions:
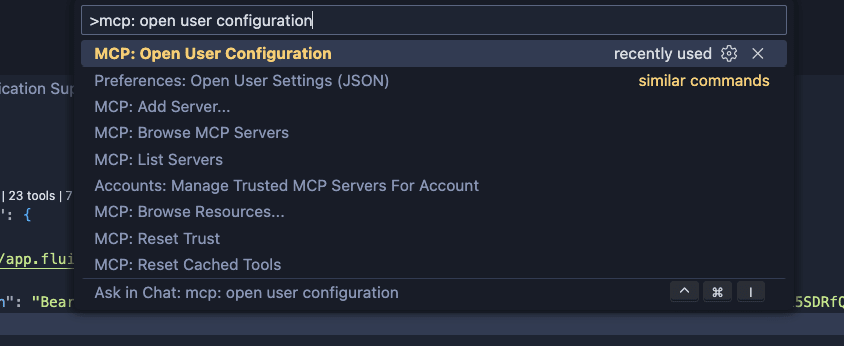
- Open VS Code's search bar (CMD + P) and type > MCP: Open User Configuration
- Select the option shown in the image below:
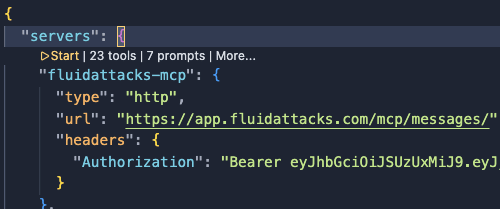
- Fluid Attacks the MCP Server in the servers section of the file:
{
"servers": {
"fluidattacks-mcp": {
"type": "http",
"url": "https://app.fluidattacks.com/mcp/messages/",
"headers": {
"Authorization": "Bearer <paste_your_api_token_here>"
}
}
}
} - Optional: Replace
<paste_your_api_token_here>with your Fluid Attacks API token. - Save the file.
- As shown in the image below, click on Start.
-
The number of tools and prompts should be shown.
-
To enable the AI Agent to use our MCP tools, click on the Configure Tools option.
-
On the opened window, search for
fluidattacks-mcpand enable the tools you want to use, and click the OK button. See the following image: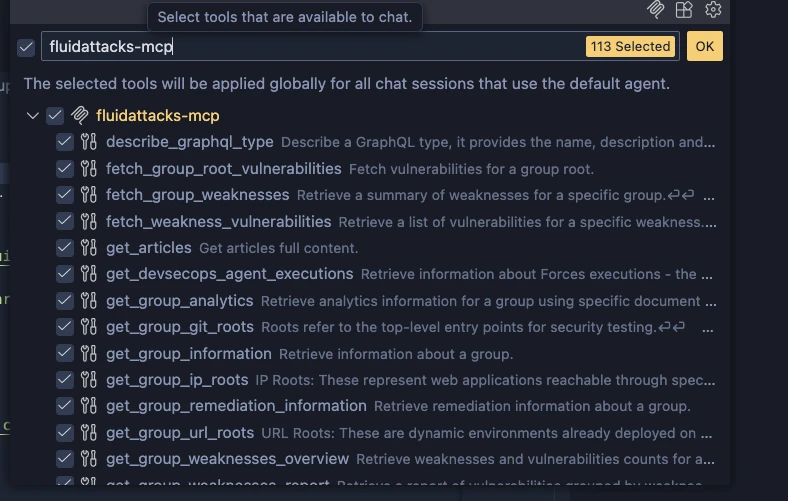
- You can now use the Fluid Attacks MCP server in VS Code.
Share the server configuration with your team

Requirements:
- Have Node.js installed
- Create the environment variable called
FLUID_ATTACKS_API_TOKEN
You can keep the Fluid Attacks MCP server configuration in your code repository for your entire team to use. Simply add the following to your IDE configuration folder within your repository and have your team meet the above requirements.
{
"mcpServers": {
"fluidattacks-mcp": {
"command": "npx",
"args": [
"--cache",
"/tmp/fluidattacks-mcp",
"-y",
"@fluidattacks/mcp",
"https://app.fluidattacks.com/mcp/messages/"
],
}
}
}With this option, the API token is not hardcoded, as it stays an environment variable, and the MCP server configuration can be versioned with no issues.
Security considerations
- API token security: Store tokens securely, never commit to version control
- Data sensitivity: Be cautious when sharing vulnerability data
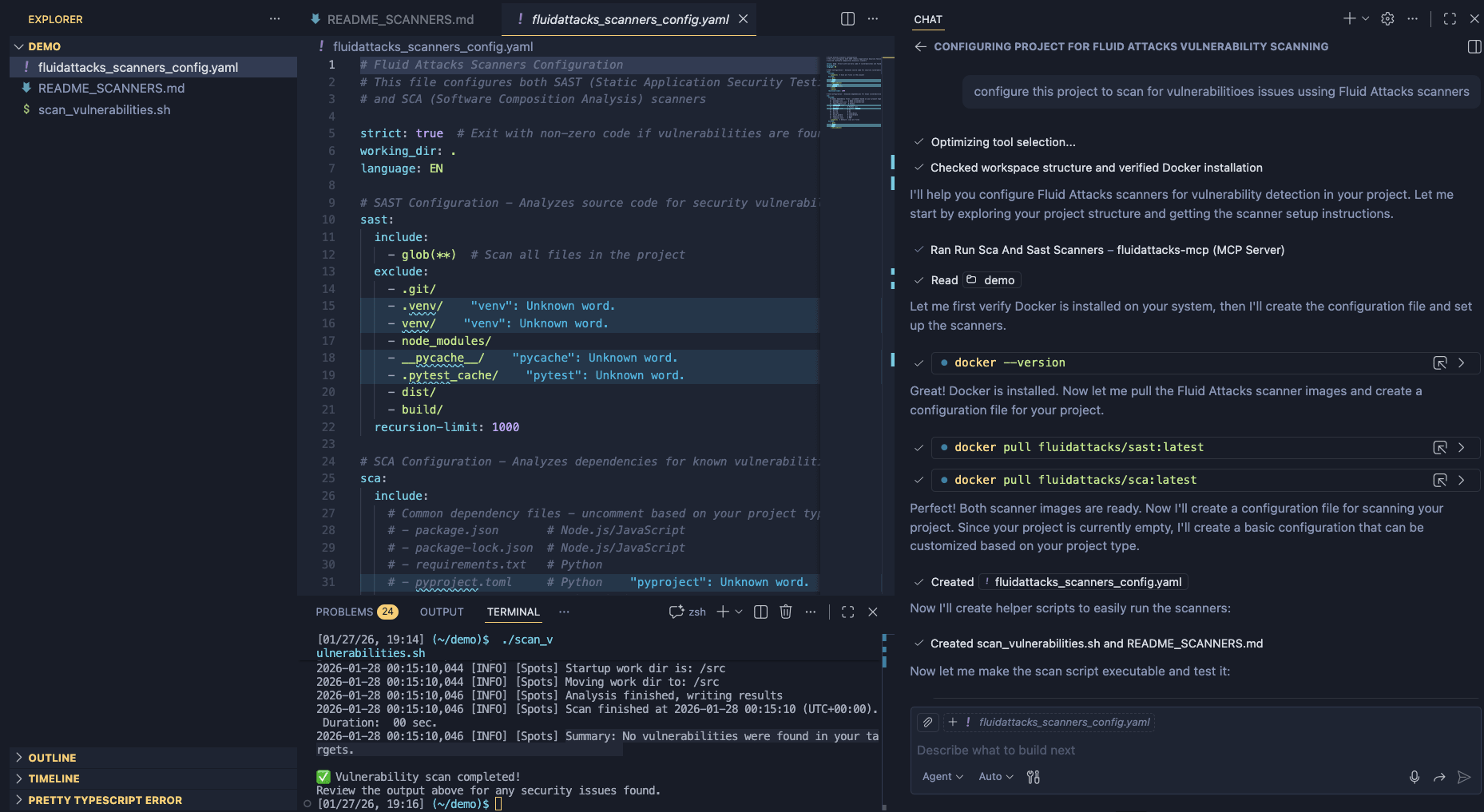
Integrate our scanners into your SDLC using AI
When using AI-powered development tools, such as Cursor, GitHub Copilot, or similar AI coding assistants, you can configure them to automatically execute Fluid Attacks security scanners at appropriate points in your SDLC. This integration helps you ensure that security vulnerabilities are detected and addressed early.
Before integrating our security scanners with AI agents, ensure that you have Docker installed on your system, that Fluid Attacks' MCP server is configured in your AI development environment, and that you have write access to your project directory for configuration files and scan results.
Add AGENTS.md to your project using Fluid Attacks' MCP server
On the chat of your AI agent, start by typing
/fluidattacks-mcp/ and then select the following command:/fluidattacks-mcp/config_agents_mdAdd AGENTS.md to your project manually
1. Create the AGENTS.md file
Add an AGENTS.md file to your project root directory. This file contains instructions that AI agents will follow to determine when and how to execute security scanners.
The AGENTS.md file should be placed at the root of your project:
your-project/
├── AGENTS.md # Add this file
├── src/
├── package.json
└── ...2. Add the AGENTS.md content
# Project Instructions
## Execute Security Scanners
### Execute SCA Scanner When:
- New dependencies are added to the project
- Dependencies are updated to new versions
- Lock files are modified (e.g.,`package-lock.json`, `uv.lock`)
- User explicitly requests a dependency security scan
- Setting up a new project for the first time
- Before deploying to production- Before pushing to the repository
### Execute SAST Scanner When:
- Source code changes are made to application files
- New features or modules are added
- Security-sensitive code is modified (authentication, authorization)
- User explicitly requests a code security scan
- Before committing significant code changes
- During code reviews
- Before deploying to production
- Before pushing to the repository
### Execute Both Scanners When:
- A complete security audit is needed
- Major project updates involving both code and dependencies- Pre-deployment security check
- User requests a full security scan
## Prerequisites
- Docker installed on the system
- No Dockerfile creation needed - only download the Docker images
- Write access to the project directory for configuration files and results
## Fluid Attacks Scanner
### Purpose
Scan the project for vulnerabilities using the Fluid Attacks MCP tools.
### Step-by-Step Instructions
#### 1. Use Fluid Attack MCP tools to configure and run the scanner
#### 2. Add the output file to .gitignore
#### 3. Remediate vulnerabilities
- Review the output file
- If there are vulnerabilities, remediate them
## Best Practices for Agents
### 1. Configuration File Management- Always verify the correct paths for include/exclude before running
- Adjust configuration based on project structure
- Use `.gitignore` as a reference for exclude patterns
- Store configuration files in the project root and add them to .gitignore
- Add the output file (Fluid-Attacks-Results.csv) to .gitignore
## When to Run What
| Scenario | Scanner | Priority |
| ----------------------------- | ------- | -------- |
| New dependency added | SCA | High |
| Code changes in auth/security | SAST | Critical |
| Weekly security audit | Both | Medium |
| Pre-deployment check | Both | Critical |
| Dependency version update | SCA | High |
| New feature development | SAST | Medium |
| Third-party library added | SCA | High |
| API endpoint changes | SAST | High |
## Integration with Development Workflow
- On Code Changes: Run SAST if source files modified
- On Dependency Changes: Run SCA if dependency files modified
- On User Request: Run appropriate scanner(s)
- Help with remediation: Always create/update security reports
- Re-scan: After fixes to verify remediationTroubleshooting
If the scanners are not being executed automatically:
- Verify that AGENTS.md exists in your project root
- Ensure the Fluid Attacks MCP server is properly configured
- Check that Docker is installed and running
- Verify that the AI agent has read access to AGENTS.md
- You can ask the AI agent to execute the scanners: "Run fluid attacks scanners."
- You can use Fluid Attacks prompts
If the scanners report false positives:
- Review the specific vulnerability details
- Adjust scanner configuration if needed
- Document acceptable exceptions in your project documentation
- Consider reaching out to Fluid Attacks support for clarification
 Development: Dive deep into the MCP server.
Development: Dive deep into the MCP server.