Install the Cursor extension

The extension can be installed from the extensions view on Cursor version 1.1.6 or earlier. On later versions, it can be installed through a .vsix file.
 Fluid Attacks' Cursor plugin, along with our entire suite of local tools and extensions, is available free of charge.
Fluid Attacks' Cursor plugin, along with our entire suite of local tools and extensions, is available free of charge.Streamline your secure development workflow with the Fluid Attacks extension for Cursor. This powerful tool helps you identify and address vulnerabilities without leaving this AI-powered IDE.
These are the key features of this plugin:
- View the specific files and lines of code with reported vulnerabilities.
- Access detailed documentation on your code's vulnerabilities.
- Accept vulnerabilities temporarily.
- Leverage Claude Sonnet's AI model to generate custom guides for fixing vulnerabilities or fix vulnerabilities automatically.
- Request reattacks.
To learn about these features, read Identify and address vulnerabilities from Cursor.
Download the extension
To download the extension in Cursor versions up to 1.1.6, follow these steps:
- Open Cursor.
- Access the extensions view.
- Type Fluid Attacks in the search bar.
- Locate the extension and click on Install.

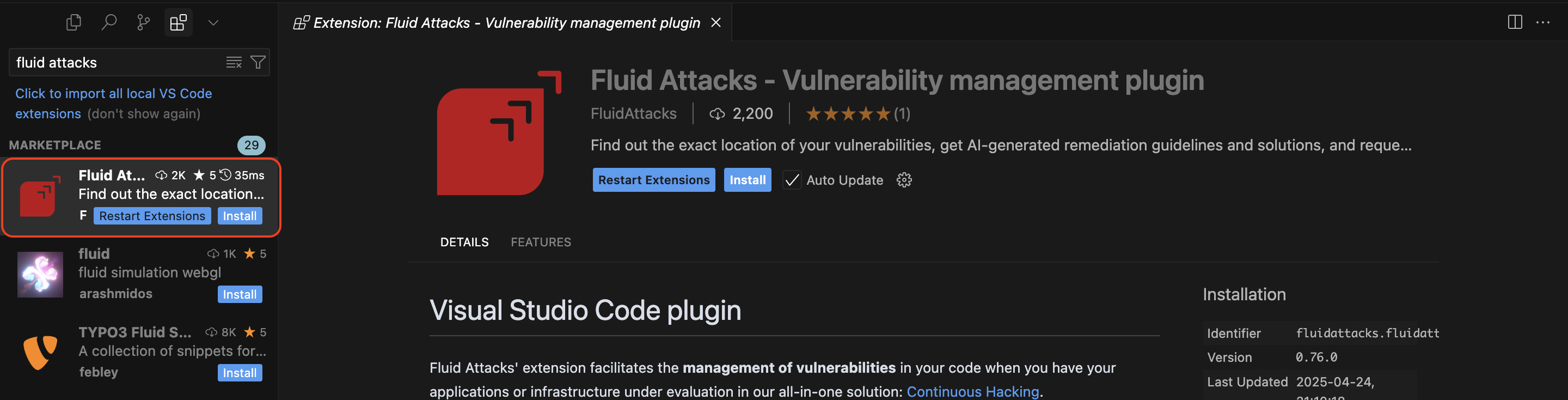
To download the extension in Cursor versions later than 1.1.6, follow these steps:
- Download the .vsix file containing the Fluid Attacks extension by visiting marketplace.visualstudio.com/_apis/public/gallery/publishers/fluidattacks/vsextensions/fluidattacks/latest/vspackage.
- Open Cursor.
- Open the command palette (Cmd/Ctrl + Shift + P). and type "Extensions: Install from VSIX".
- Select the previously downloaded .vsix file.
Connect Cursor with the Fluid Attacks platform

Configuring the extension requires a valid API token. Generate one before proceeding with the steps below.
After downloading the extension, you need to configure it to connect the Fluid Attacks platform with Cursor. Follow these steps:
- Type the following into the input bar: >Fluid Attacks: set Fluid Attacks token.
- Paste your API token into the input bar and press Enter.
- Use Ctrl/Cmd + R to refresh the IDE.
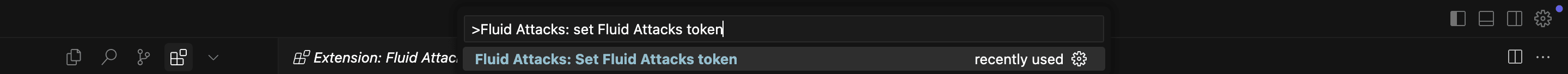
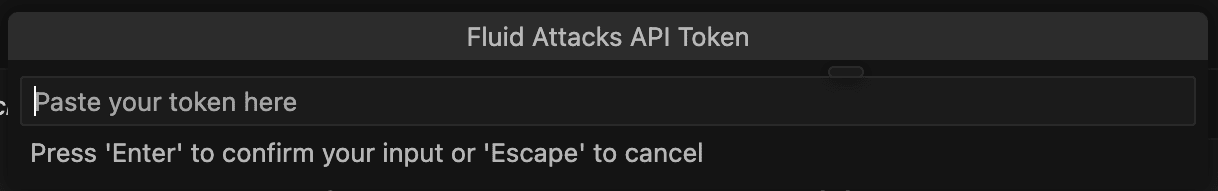
Verify successful installation

The extension analyzes the files you provide as input, so ensure you include all relevant files for comprehensive vulnerability management.
Once you have the Cursor extension set up, verify that it functions correctly:
- Open the base folder of your Git repository in Cursor.
- You should see the Fluid Attacks extension icon in the IDE's activity bar and red dots on files with identified vulnerabilities. This confirms successful configuration.
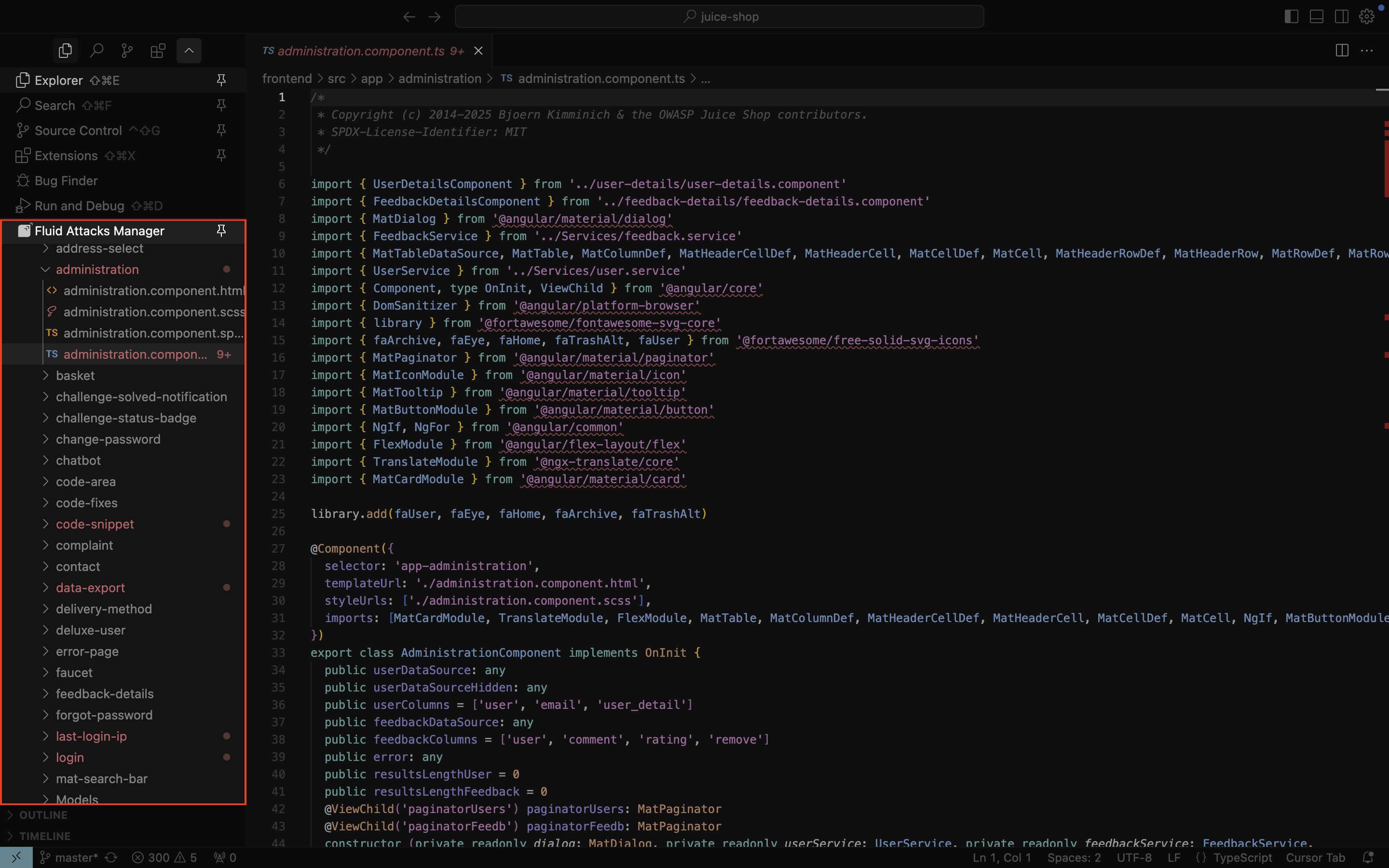
 Note: Some extension features require Git history. Ensure your project is a Git repository cloned using Git.
Note: Some extension features require Git history. Ensure your project is a Git repository cloned using Git.