Manage security gates
Manage your organization's security gates
 Role required: Organization Manager
Role required: Organization Manager
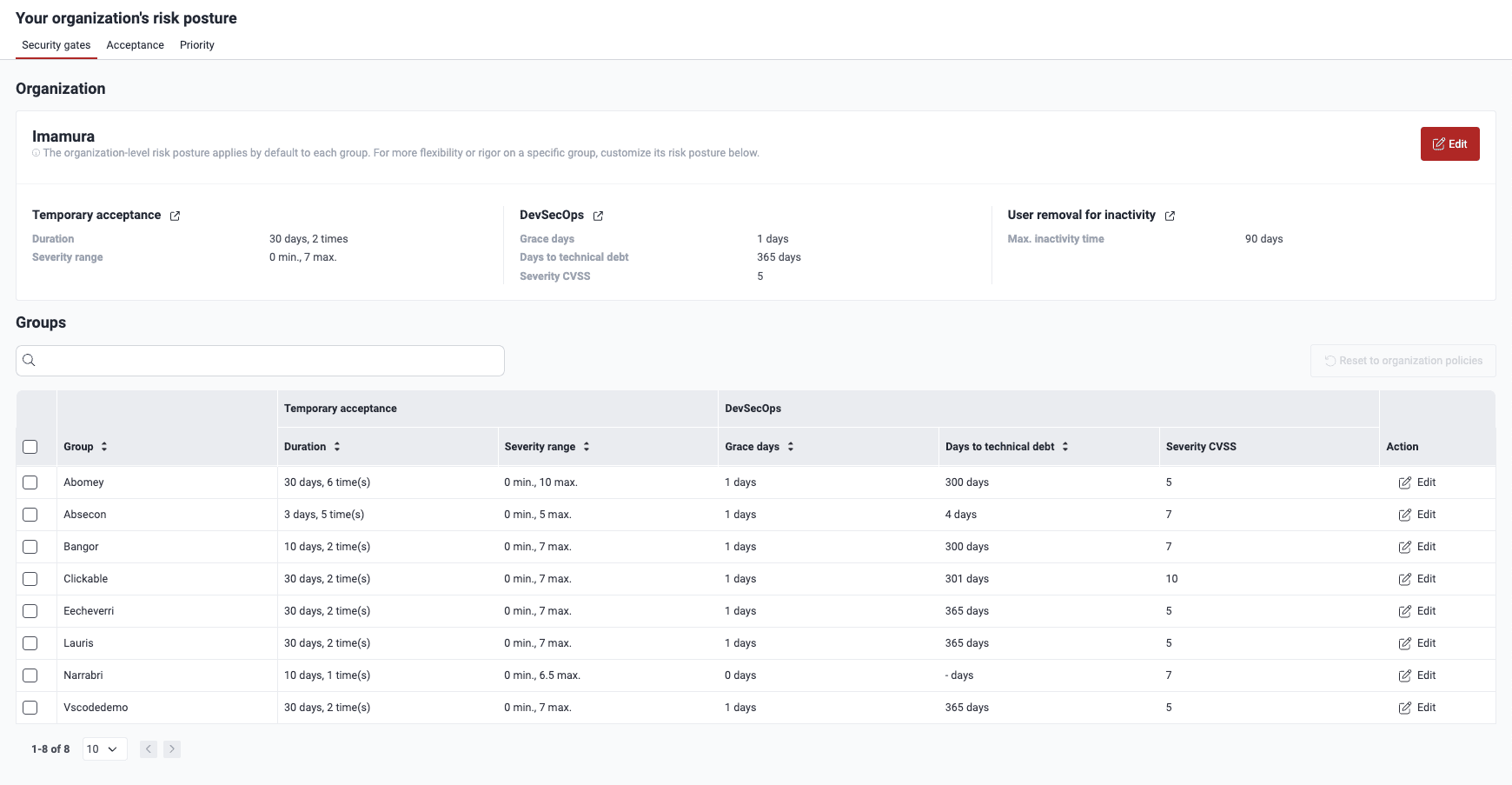
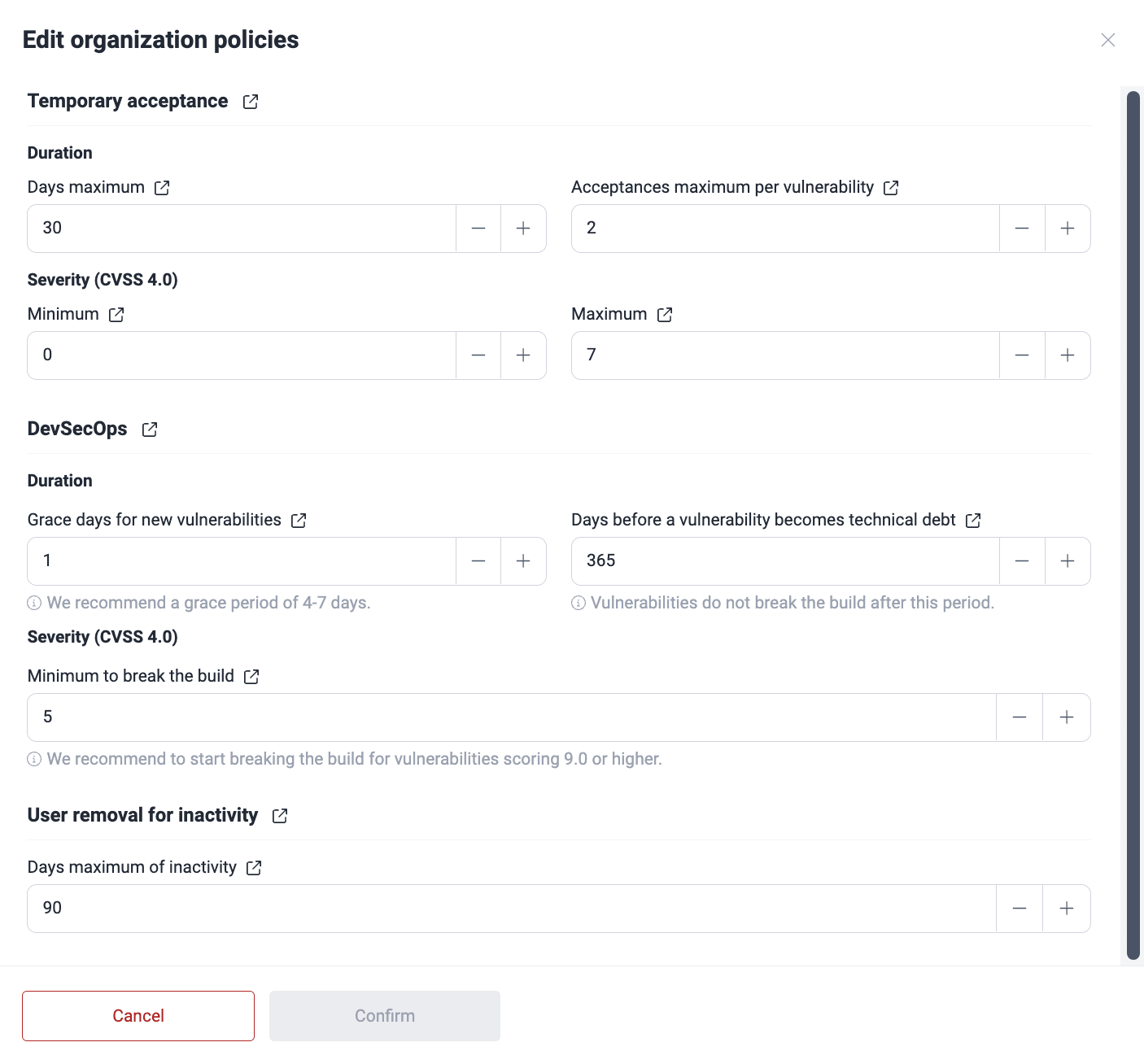
Under Organization, you find the security gates configuration that your organization applies by default for each of its new groups. To modify it, click on Edit. A pop-up window appears, displaying the eight policies available to you, which are explained further below on this page. To save any changes, click on Confirm.
Temporary acceptance
Maximum number of calendar days a finding can be temporarily accepted
Indicates for how many days a vulnerability can be temporarily accepted. The platform allows it to be at most 999 calendar days. This policy affects the executions of CI Gate, as temporarily accepted vulnerabilities do not break the build. Set this cautiously to avoid leaving vulnerabilities unaddressed for extended periods, causing risks to your applications.
Maximum number of times a finding can be accepted
Indicates the maximum number of times a vulnerability can be temporarily accepted. Once this limit is reached, the vulnerability cannot be temporarily accepted again, even if it goes through other treatments or is present again after having been remediated once.
Minimum CVSS score allowed for temporary acceptance
Indicates the minimum Common Vulnerability Scoring System (CVSS) score (0.0 to 10.0) required for a vulnerability to be temporarily accepted.
Maximum CVSS score allowed for temporary acceptance
DevSecOps
Grace period where newly reported vulnerabilities will not break the build
Indicates the amount of days during which newly discovered vulnerabilities do not trigger CI Gate to break the build. Exercise caution when setting this value to minimize the risk of unaddressed vulnerabilities impacting your applications.

Number of days until vulnerabilities are considered technical debt and do not break the build
Indicates the period (in days) before a vulnerability is considered "technical debt" and does not break the build. That is, during that amount of days, the vulnerability breaks the build once reported and unmanaged. But after this period, the vulnerability does not break the build.
Minimum CVSS score of an open vulnerability to break the build
Indicates the minimum CVSS score required for an unmanaged vulnerability to break the build when using CI Gate in strict mode.

Number of days after which a member is removed due to inactivity
Indicates the allowed inactivity period (in days) before a member is automatically removed from the platform. Its default value is 90 days. The removed member loses all access and must request a new invitation to rejoin. The latter has to be issued by an Organization Manager.

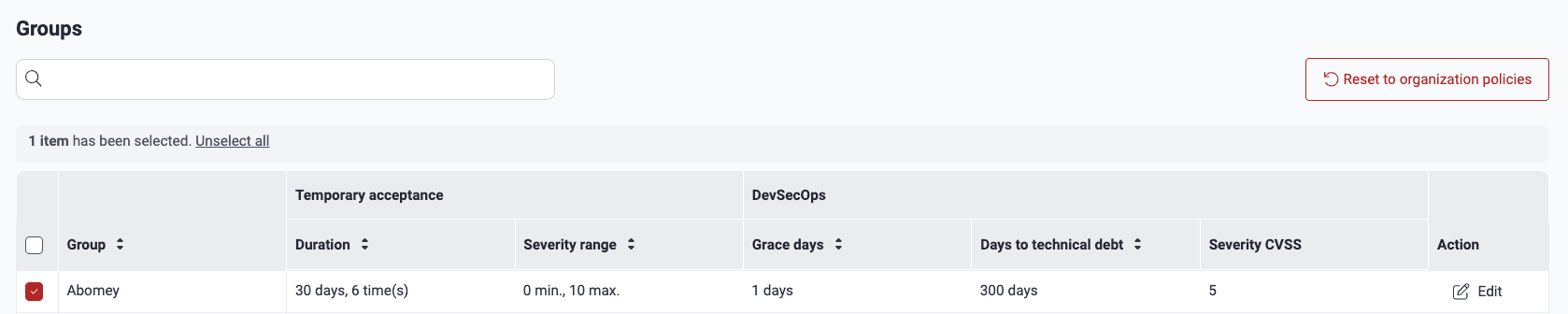
Manage your security gates at a group level
 Role required: Organization Manager
Role required: Organization Manager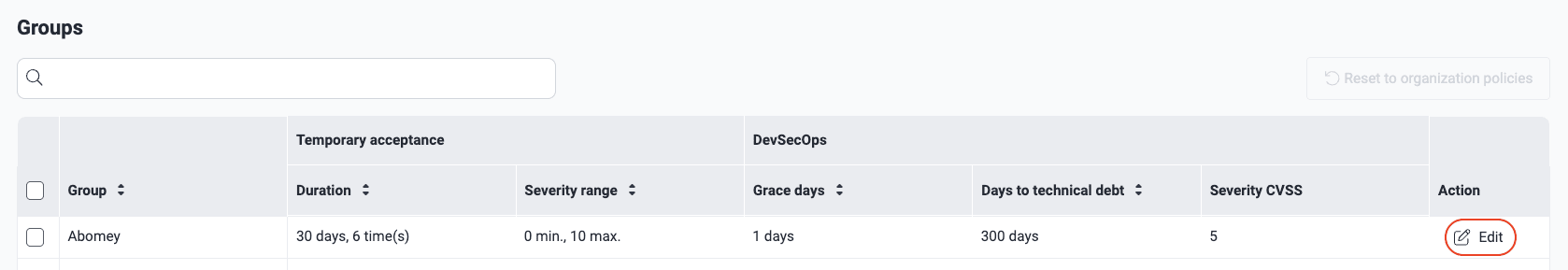
In the pop-up window, define your group's specific policies (see the definitions above) and click the Confirm button when you are done.
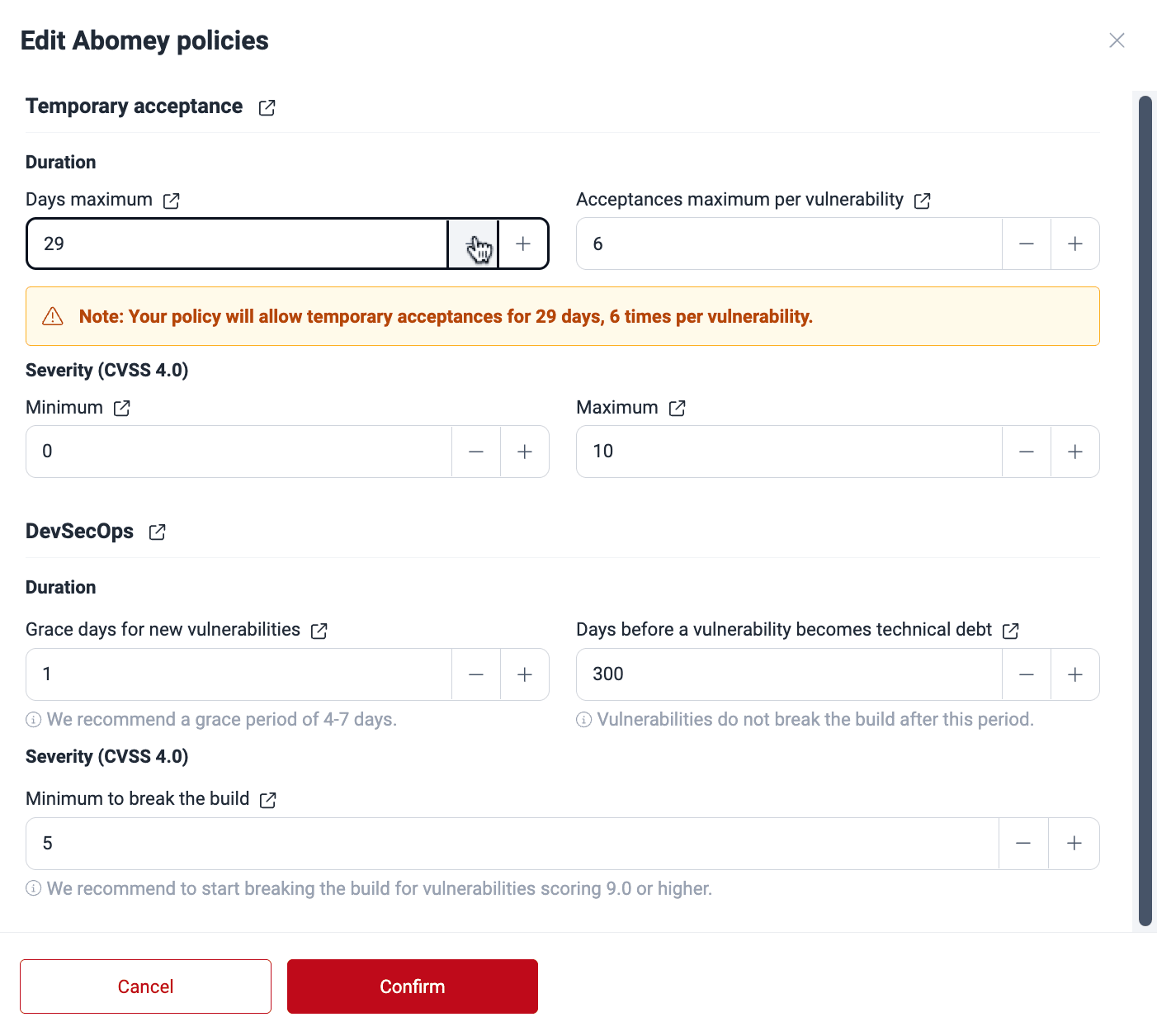
Upon confirming, you get an email notification announcing the policy change.
On the platform, it is also possible to change the security gates configuration of one or more groups to that currently used at the organization level. To do this, select the group(s) and click on Reset to organization policies.